Fortinet NSE7_OTS-7.2 Fortinet NSE 7 - OT Security 7.2 Exam Practice Test
Fortinet NSE 7 - OT Security 7.2 Questions and Answers
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
Refer to the exhibit.
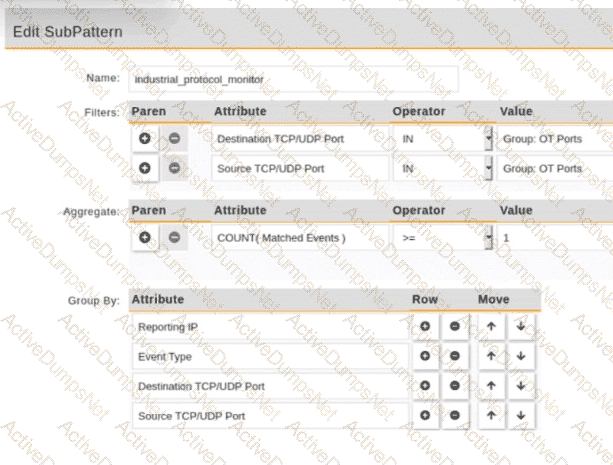
An operational technology rule is created and successfully activated to monitor the Modbus protocol on FortiSIEM. However, the rule does not trigger incidents despite Modbus traffic and application logs being received correctly by FortiSIEM.
Which statement correctly describes the issue on the rule configuration?
Refer to the exhibit.
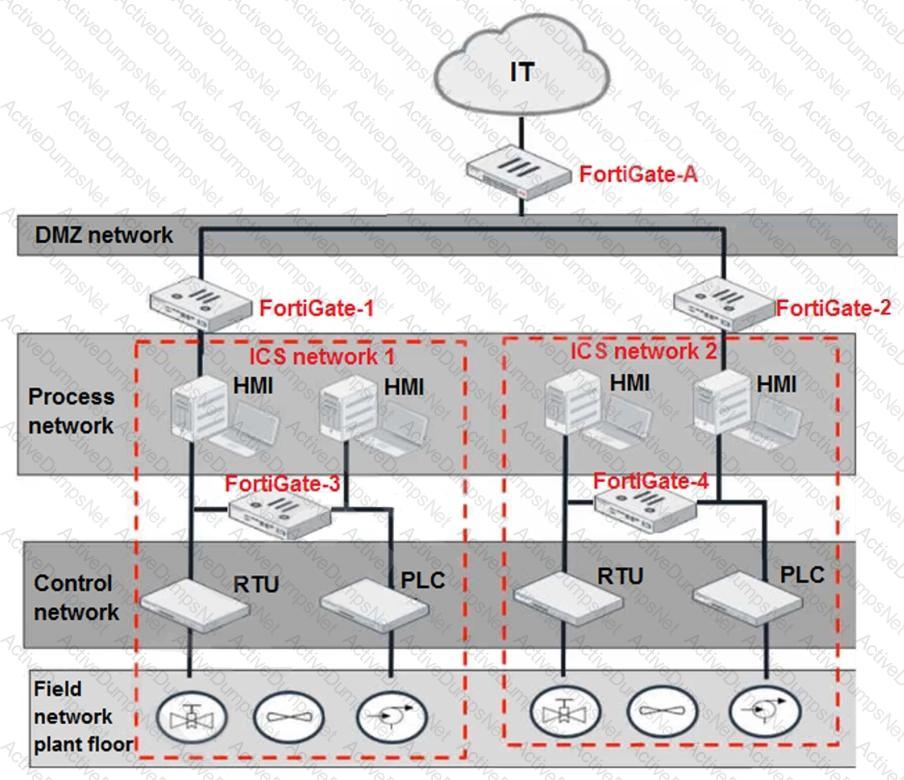
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
Which three methods of communication are used by FortiNAC to gather visibility information? (Choose three.)
Refer to the exhibit.
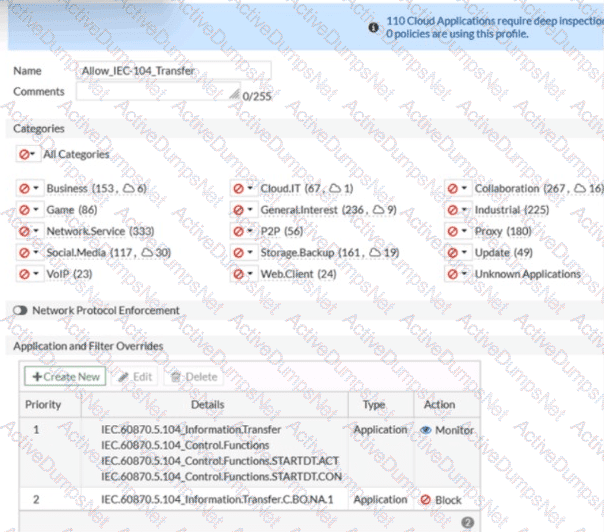
An OT network security audit concluded that the application sensor requires changes to ensure the correct security action is committed against the overrides filters.
Which change must the OT network administrator make?
Which statement is correct about processing matched rogue devices by FortiNAC?
As an OT network administrator, you are managing three FortiGate devices that each protect different levels on the Purdue model. To increase traffic visibility, you are required to implement additional security measures to detect exploits that affect PLCs.
Which security sensor must implement to detect these types of industrial exploits?
An OT network consists of multiple FortiGate devices. The edge FortiGate device is deployed as the secure gateway and is only allowing remote operators to access the ICS networks on site.
Management hires a third-party company to conduct health and safety on site. The third-party company must have outbound access to external resources.
As the OT network administrator, what is the best scenario to provide external access to the third-party company while continuing to secure the ICS networks?
Refer to the exhibit.
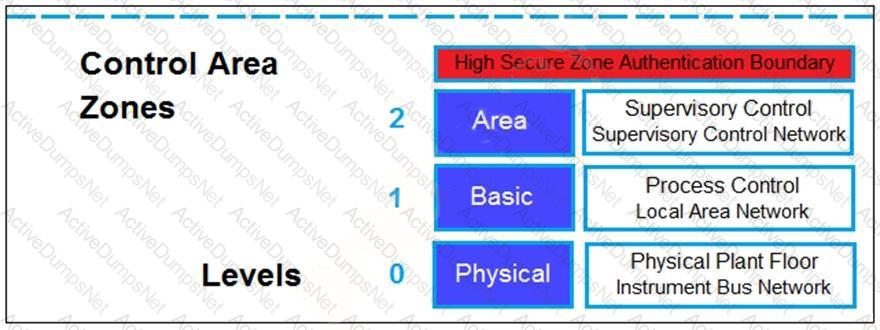
Based on the Purdue model, which three measures can be implemented in the control area zone using the Fortinet Security Fabric? (Choose three.)
The OT network analyst run different level of reports to quickly explore failures that could put the network at risk. Such reports can be about device performance. Which FortiSIEM reporting method helps to identify device failures?
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
Refer to the exhibit.
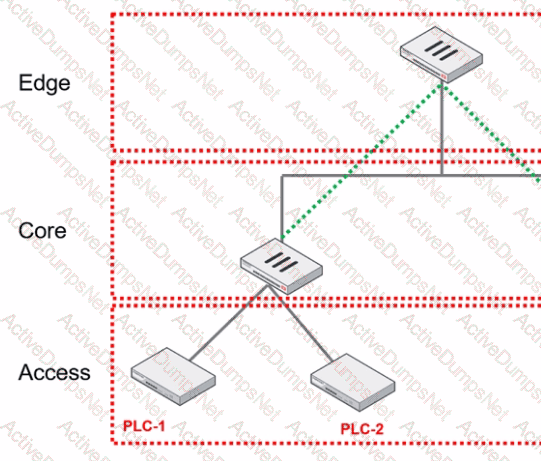
You are assigned to implement a remote authentication server in the OT network.
Which part of the hierarchy should the authentication server be part of?
As an OT network administrator you are required to generate reports that primarily use the same type of data sent to FortiSlEM These reports are based on the preloaded analytic searches
Which two actions can you take on FortiSlEM to enhance running reports for future use? (Choose two.)
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
When you create a user or host profile, which three criteria can you use? (Choose three.)
An OT administrator has configured FSSO and local firewall authentication. A user who is part of a user group is not prompted from credentials during authentication.
What is a possible reason?
The OT network analyst runs different level of reports to quickly explore threats that exploit the network. Such reports can be run on all routers, switches, and firewalls. Which FortiSIEM reporting method helps to identify these type of exploits of image firmware files?
Refer to the exhibit and analyze the output.
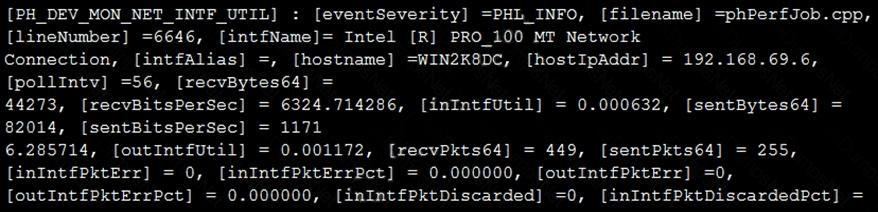
Which statement about the output is true?
What are two critical tasks the OT network auditors must perform during OT network risk assessment and management? (Choose two.)
An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
