Fortinet NSE7_LED-7.0 Fortinet NSE 7 - LAN Edge 7.0 Exam Practice Test
Fortinet NSE 7 - LAN Edge 7.0 Questions and Answers
Which CLI command should an administrator use on FortiGate to view the RSSO authentication process in real time?
Refer to the exhibits.
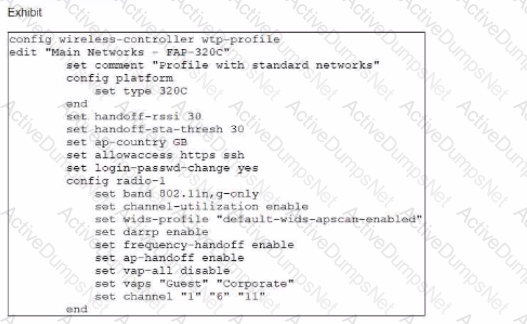
In the WTP profile configuration shown in the exhibit, the AP profile is assigned to two FAP-320 APs that are installed in an open plan office.
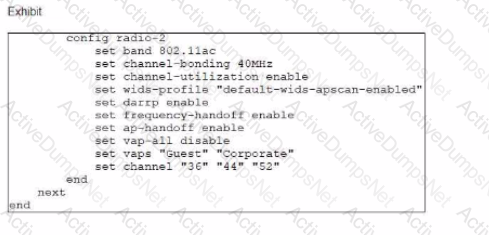
The first AP has 32 clients associated with the 5 GHz radios and 22 clients associated with the 2.4 GHz radio. The second AP has 12 clients associated with the 5 GHz radios and 20 clients associated with the 2.4 GHz radio.
A dual-band-capable client enters the office near the first AP and the first AP measures the new client at -33 dBm signal strength. The second AP measures the new client at 2 -43 dBm signal strength.
If the new client attempts to connect to the corporate wireless network, with which AP radio will the client be associated?
A wireless network in a school provides guest access using a captive portal to allow unregistered users to self-register and access the network The administrator is requested to update the existing configuration to provide captive portal authentication through a secure connection (HTTPS)
Which two changes must the administrator make to enforce HTTPS authentication"? (Choose two >
Refer to the exhibits showing AP monitoring information.
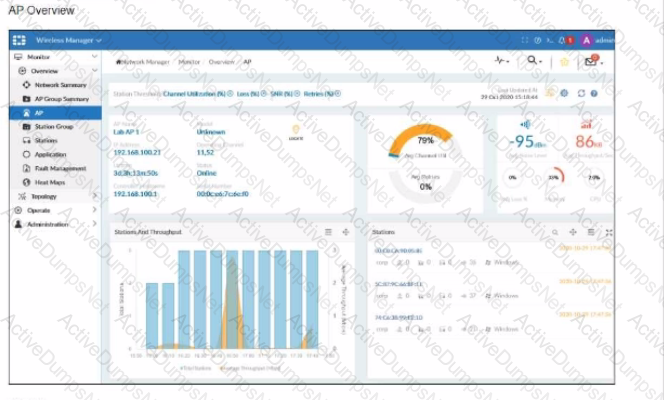
The exhibits show the status of an AP in a small office building. The building is located at the edge of a campus, and users are reporting issues with wireless network performance.
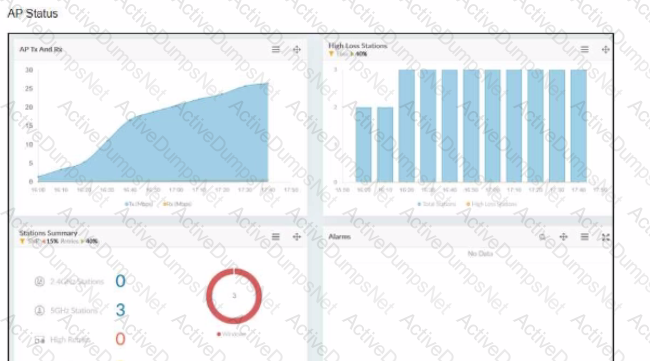
Which configuration change would best improve the wireless network performance?
Which three protocols are used for controlling FortiSwitch devices on FortiGate? (Choose three.)
Exhibit.
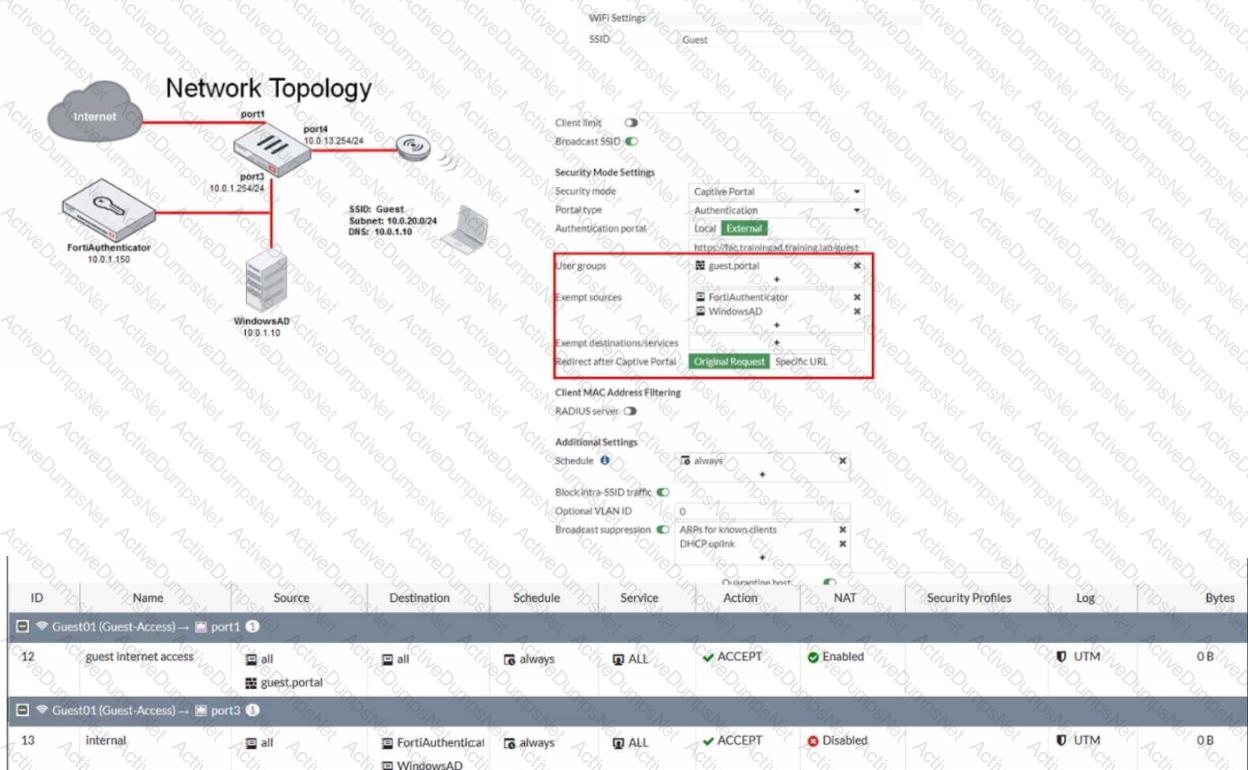
Refer to the exhibit showing a network topology and SSID settings.
FortiGate is configured to use an external captive portal However wireless users are not able to see the captive portal login page
Which configuration change should the administrator make to fix the problem?
Refer to the exhibits.
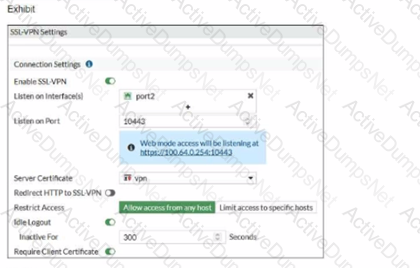
Examine the debug output and the SSL VPN configuration shown in the exhibits.
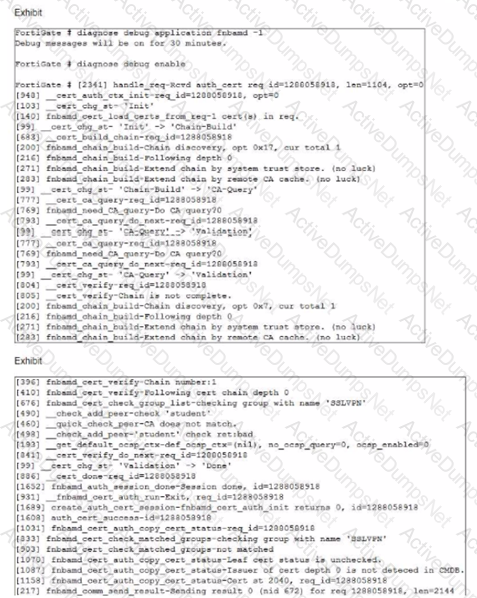
An administrator has configured SSL VPN on FortiGate. To improve security, the administrator enabled Required Client Certificate on the SSL VPN configuration page. However, a user is unable to successfully authenticate to SSL VPN.
Which configuration change should the administrator make to fix the problem?
Refer to the exhibit.
Examine the partial debug output shown in the exhibit.

Which two statements about the debug output are true? (Choose1 two.)
Refer to the exhibit
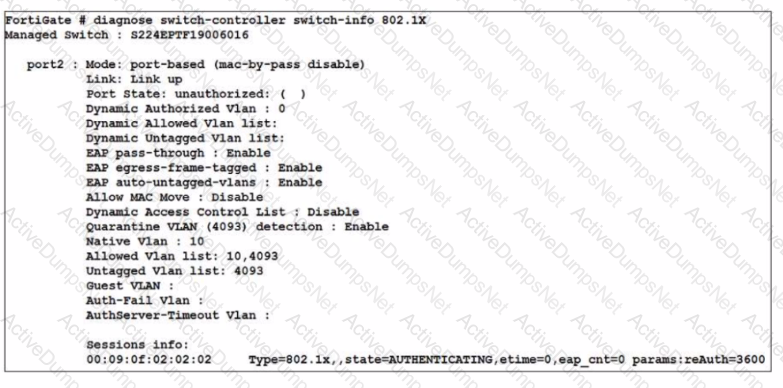
A device connected to port2 on FortiSwitch cannot access the network The port is assigned a security policy to enforce 802 1X authentication While troubleshooting the issue, the administrator obtains the debug output shown in the exhibit
Which two scenarios are likely to cause this issue? (Choose two.)
Which two statements about the MAC-based 802 1X security mode available on FortiSwitch are true? (Choose two.)
An administrator is testing the connectivity for a new VLAN The devices in the VLAN are connected to a FortiSwitch device that is managed by FortiGate Quarantine is disabled on FortiGate
While testing the administrator noticed that devices can ping FortiGate and FortiGate can ping the devices The administrator also noticed that inter-VLAN communication works However intra-VLAN communication does not work
Which scenario is likely to cause this issue?
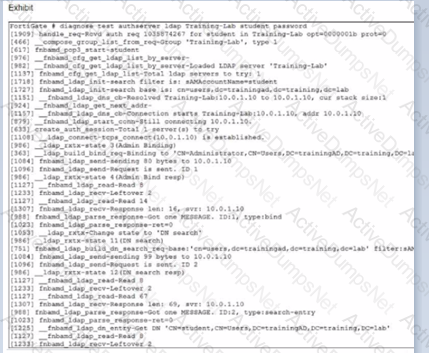
Refer to the exhibits.

Examine the LDAP server configuration and output shown in the exhibits.
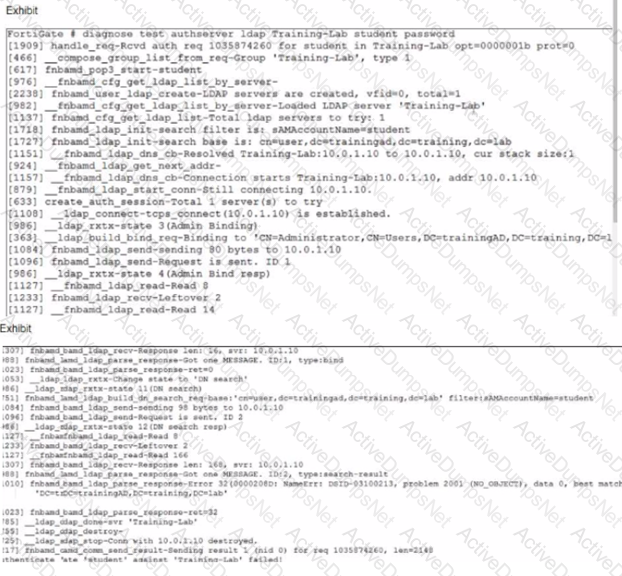
Note that the Distinguished Name and Username settings on the LDAP server configuration have been expanded to display their full contents.
An LDAP user named student cannot authenticate. While testing the student account, the administrator gets the CLI output shown in the exhibit.
According to the output, which FortiGate LDAP server settings must the administrator check?
Which statement correctly describes the guest portal behavior on FortiAuthenticator?
Refer to the exhibit.
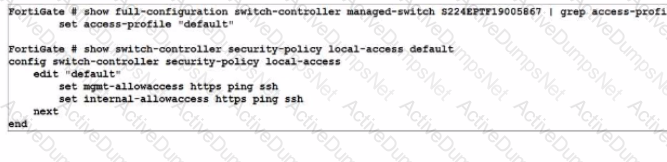
An administrator wants to telnet into the S224EPTF19005867 switch over the FortiGate FortiLink interface.
Which configuration change should the administrator make?
Which EAP method requires the use of a digital certificate on both the server end and the client end?
Refer to the exhibit.
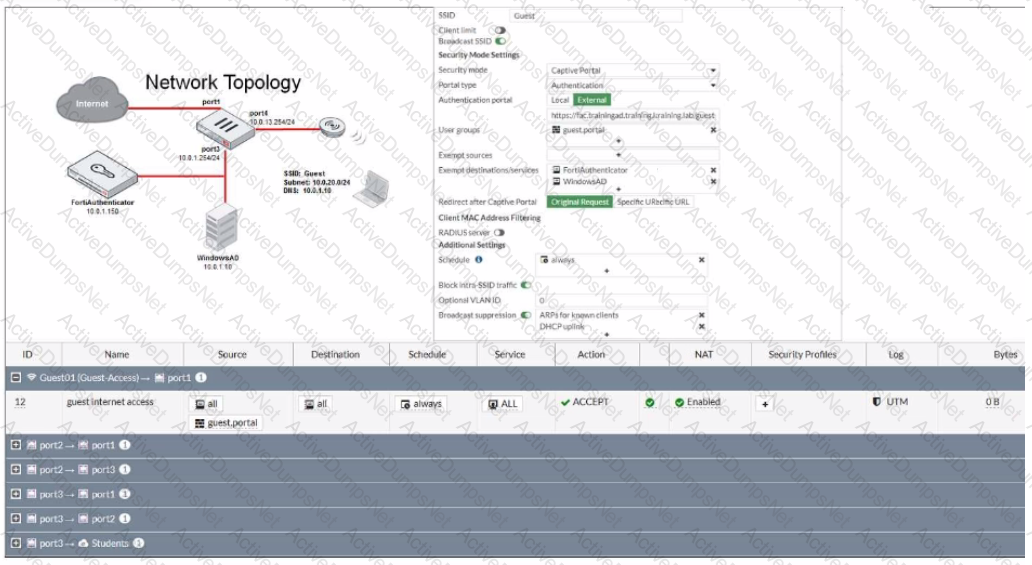
The exhibit shows a network topology and SSID settings. FortiGate is configured to use an external captive portal.
However, wireless users are not able to see the captive portal login page.
Which configuration change should the administrator make to fix the problem?
Refer to the exhibit.
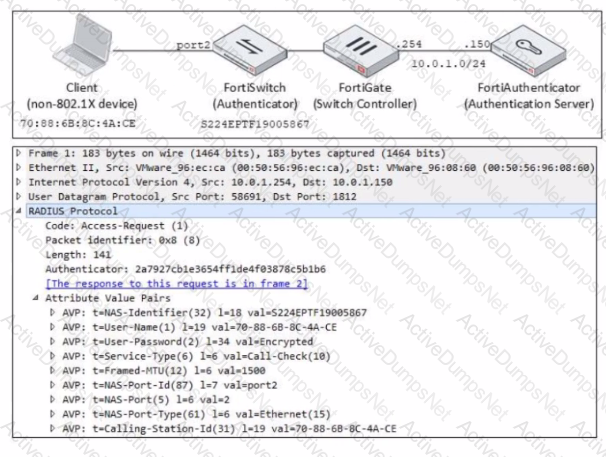
Examine the network diagram and packet capture shown in the exhibit
The packet capture was taken between FortiGate and FortiAuthenticator and shows a RADIUS Access-Request packet sent by FortiSwitch to FortiAuthenticator through FortiGate
Why does the User-Name attribute in the RADIUS Access-Request packet contain the client MAC address?
Refer to the exhibits.
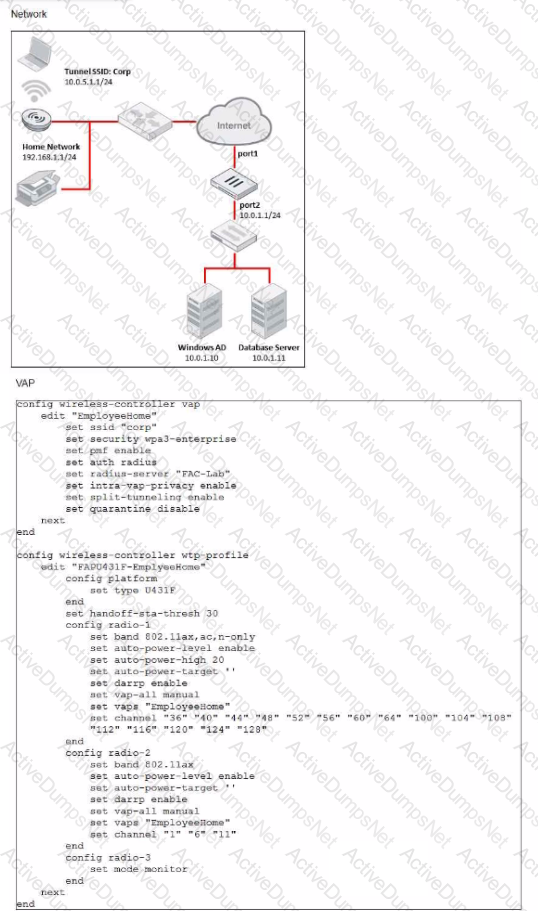
The CLI output shows a FortiGate configuration supporting a remote AP in an employee's home. The employee requires access to resources located on the company network, including the database server and AD server. The employee is trying to print to a printer connected in their home, but is not able to.
Which two solutions would resolve the issue? (Choose two.)
