Fortinet FCSS_SDW_AR-7.6 FCSS - SD-WAN 7.6 Architect Exam Practice Test
FCSS - SD-WAN 7.6 Architect Questions and Answers
Which two statements correctly describe what happens when traffic matches the implicit SD-WAN rule? (Choose two.)
(In the context of SD-WAN, the terms underlay and overlay are commonly used to categorize links.
Which two statements about underlay and overlay links are correct? Choose two answers.)
Refer to the exhibits, which show the configuration of an SD-WAN rule and the corresponding rule status and routing table.

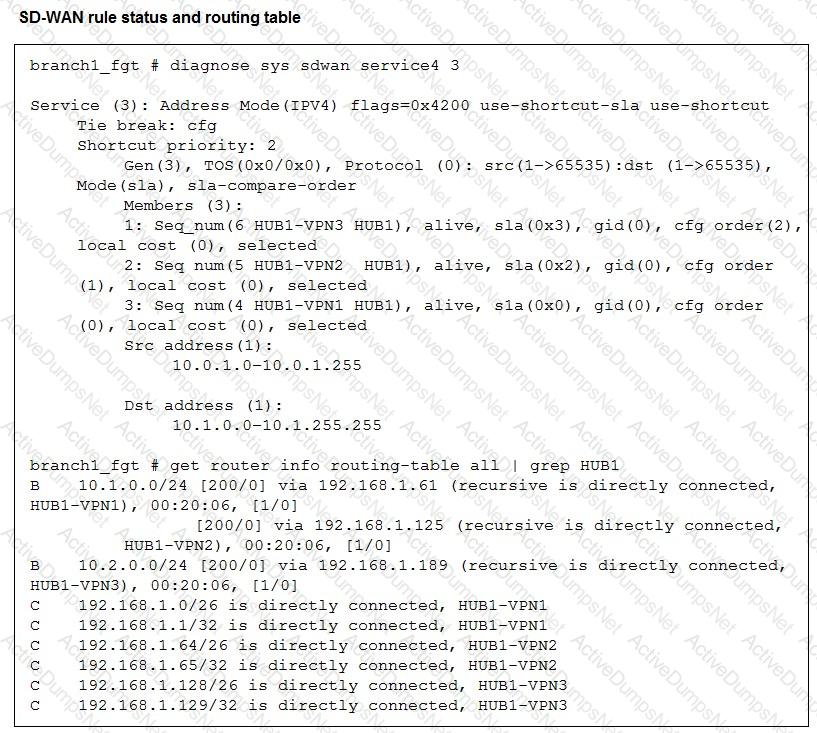
The administrator wants to understand the expected behavior for traffic matching the SD-WAN rule.
Based on the exhibits, what can the administrator expect for traffic matching the SD-WAN rule?
(Refer to the exhibit.
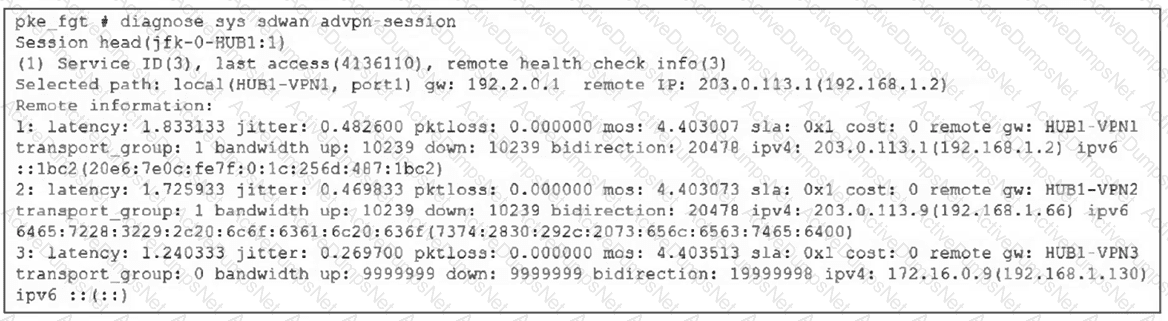
Based on the output shown in the exhibit, what can you conclude about the device role and how it handles health checks? Choose one answer.)
Refer to the exhibit.
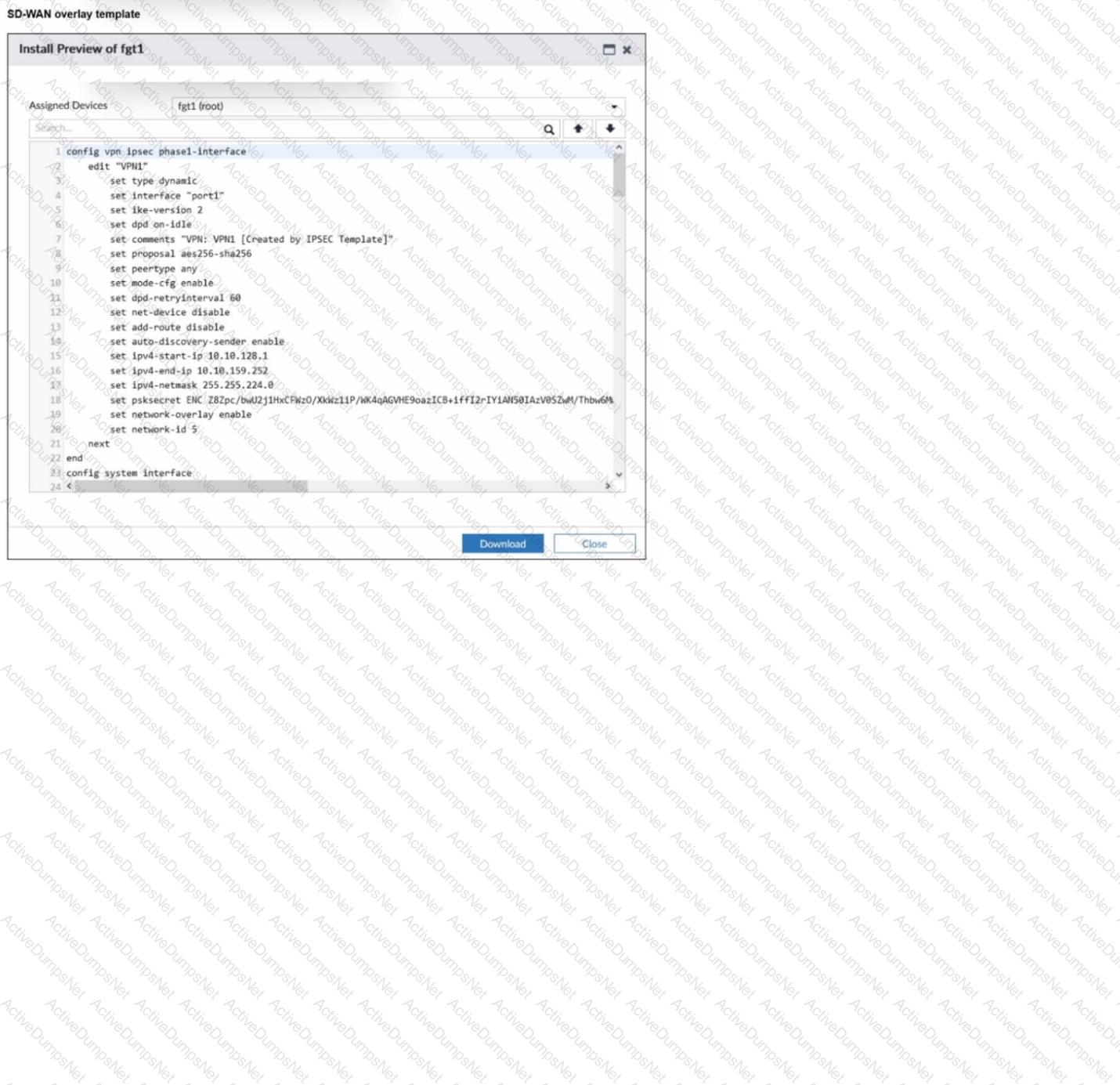
The administrator used the SD-WAN overlay template to prepare an IPsec tunnels configuration for a hub-and-spoke SD-WAN topology. The exhibit shows the FortiManager installation preview for one FortiGate device.
Based on the exhibit, which statement best describes the configuration applied to the FortiGate device?
Refer to the exhibits.
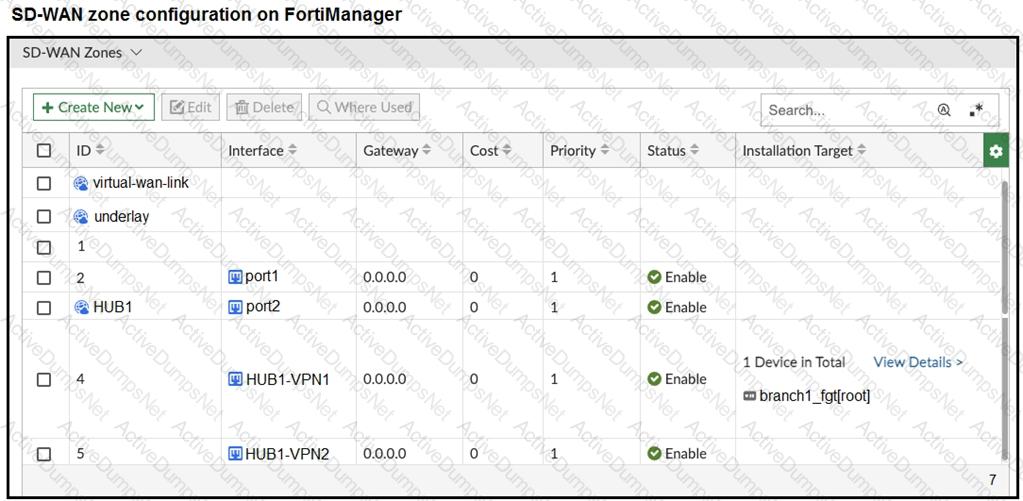
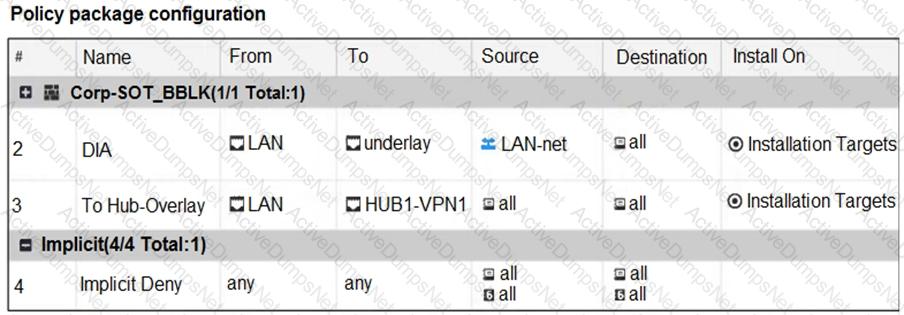
The exhibits show the SD-WAN zone configuration of an SD-WAN template prepared on FortiManager and the policy package configuration.
When the administrator tries to install the configuration changes, FortiManager fails to commit.
What should the administrator do to fix the issue?
Refer to the exhibit.
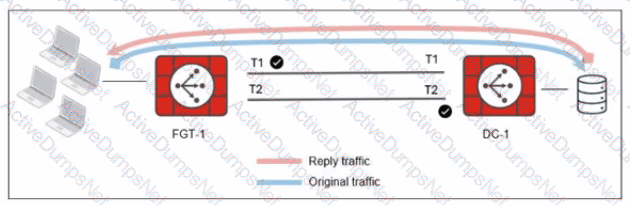
The administrator analyzed the traffic between a branch FortiGate and the server located in the data center, and noticed the behavior shown in the diagram.
When the LAN clients located behind FGT1 establish a session to a server behind DC-1, the administrator observes that, on DC-1, the reply traffic is routed overT2. even though T1 is the preferred member in
the matching SD-WAN rule.
What can the administrator do to instruct DC-1 to route the reply traffic through the member with the best performance?
The administrator uses the FortiManager SD-WAN overlay template to prepare an SD-WAN deployment. Using information provided through the SD-WAN overlay template wizard, FortiManager creates templates ready to install on the spoke and hub devices.
What are the three templates created by the SD-WAN overlay template for a spoke device? (Choose three.)
When you use the command diagnose sys session list, how do you identify the sessions that correspond to traffic steered according to SD-WAN rules?
(Refer to the exhibits.
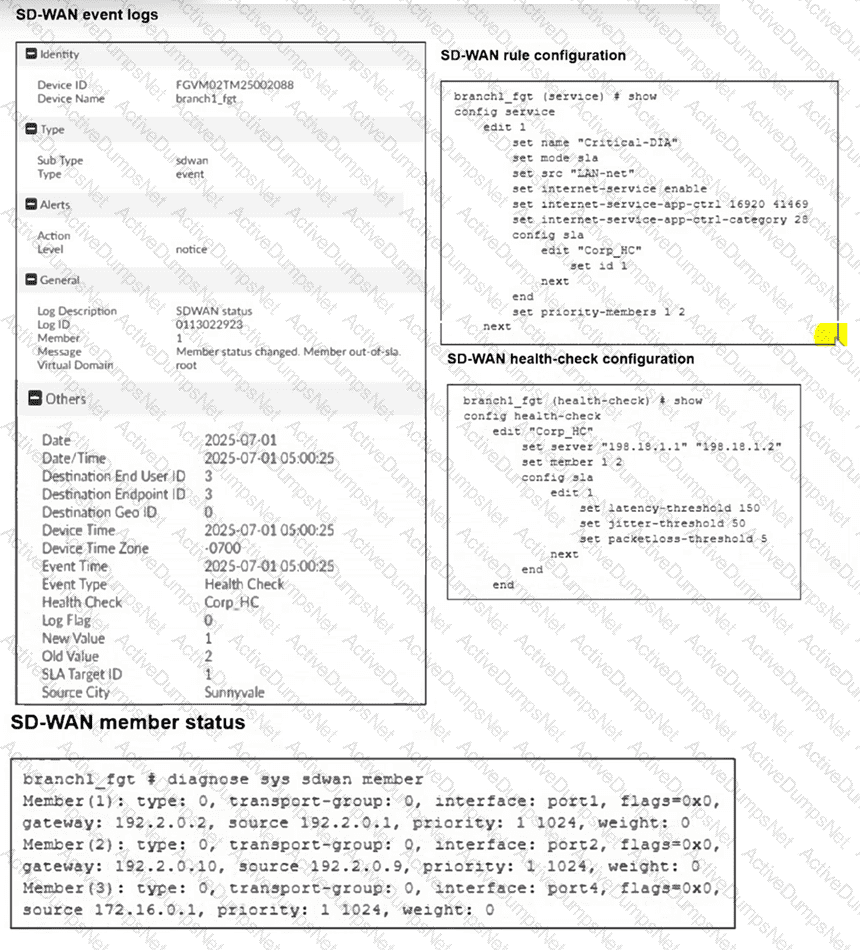
Two SD-WAN event logs, the member status, the SD-WAN rule configuration, and the health-check configuration for a FortiGate device are shown.
Immediately after the log messages are displayed, how will the FortiGate steer the traffic based on the information shown in the exhibits? Choose one answer.)
Refer to the exhibits.
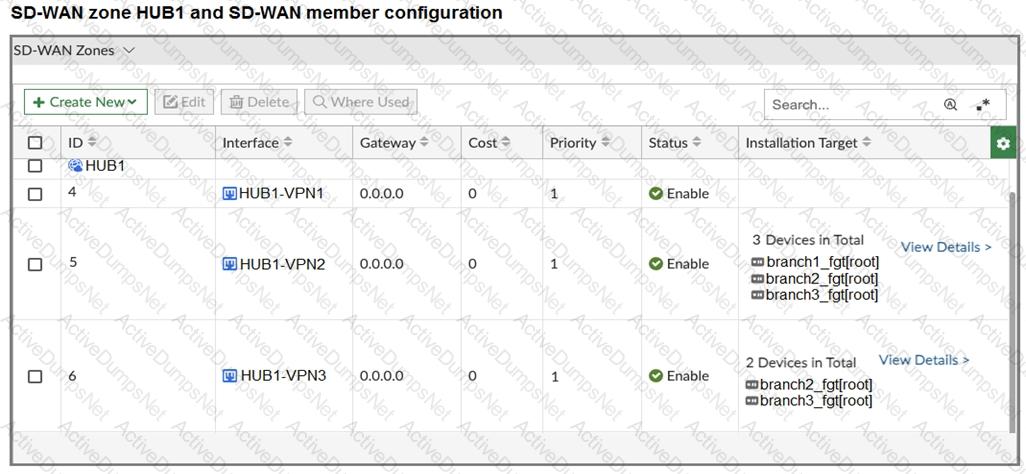
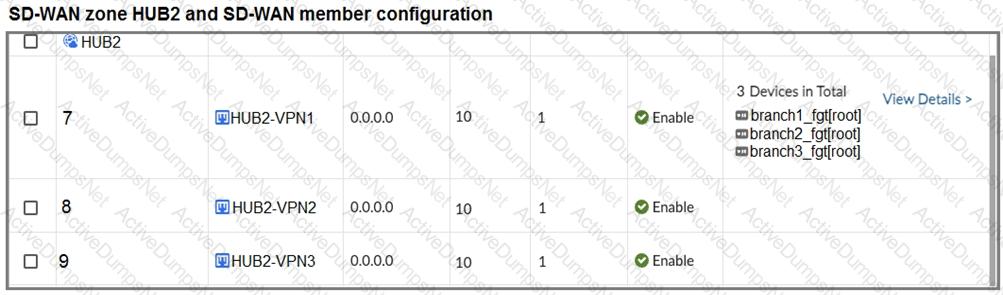
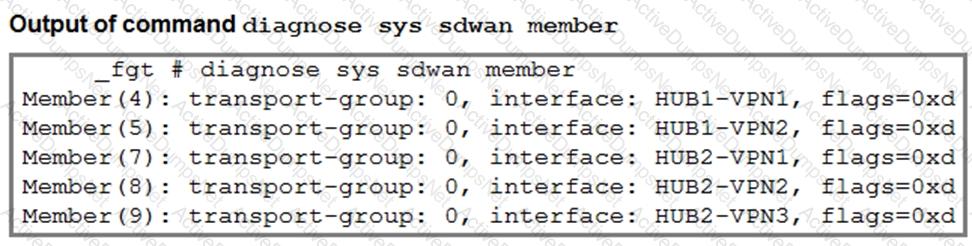
The first exhibit shows the SD-WAN zone HUB1 and SD-WAN member configuration from an SD-WAN template, and the second exhibit shows the output of command diagnose sys sdwan member collected on a FortiGate device.
Which statement best describes what the diagnose output shows?
(Refer to the exhibits.
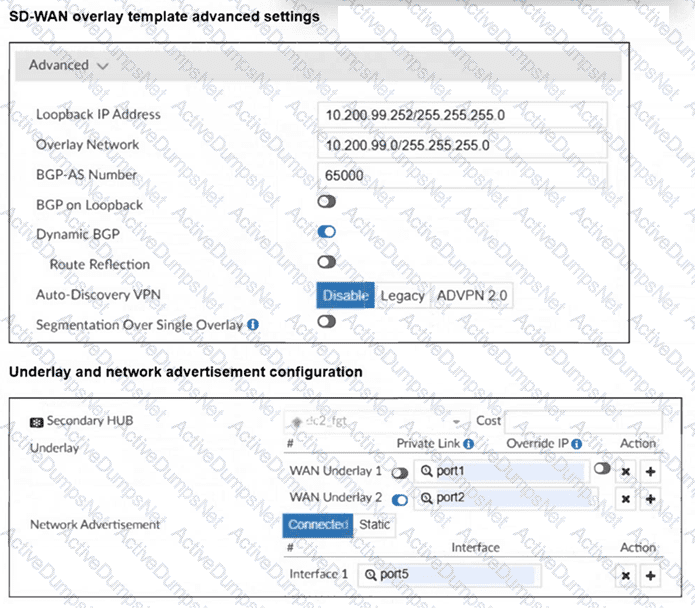
The SD-WAN overlay template advanced settings and the underlay and network advertisement settings are shown. These are the configurations for the secondary hub of a dual-hub SD-WAN topology created with the FortiManager SD-WAN overlay orchestrator.
Which two conclusions can you draw from the information shown in the exhibits? Choose two answers.)
Refer to the exhibit.
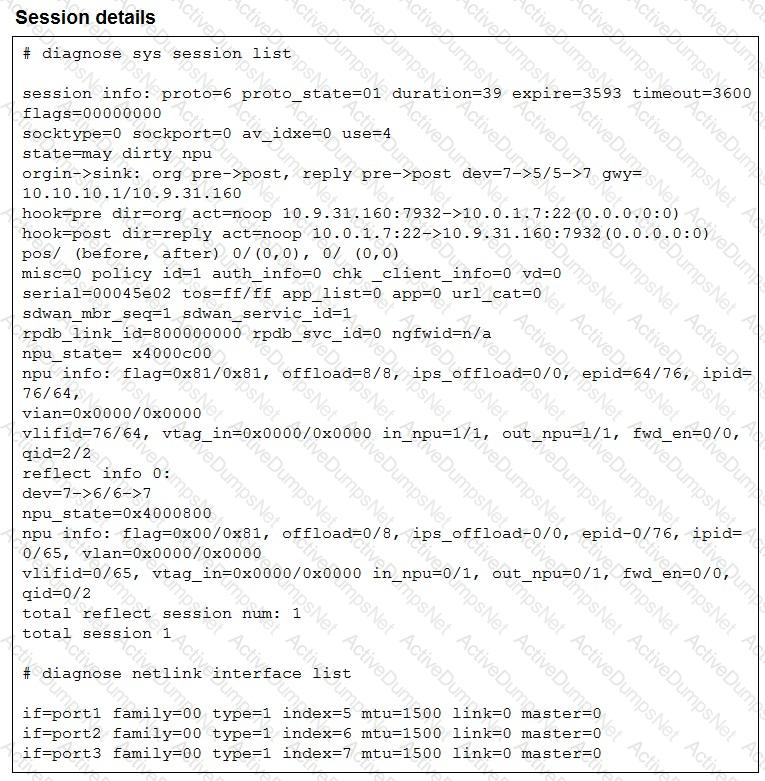
The exhibit shows the details of a session and the index numbers of some relevant interfaces on a FortiGate device that supports hardware offloading.
Based on the information shown in the exhibits, which two conclusions can you draw? (Choose two.)
Refer to the exhibit.

How does FortiGate handle the traffic with the source IP 10.0.1.130 and the destination IP 128.66.0 125?
(When you deploy SD-WAN, you can choose from several common designs. Each design best applies to specific contexts.
Which two statements correctly associate a common SD-WAN design with its main indication or constraint? Choose two answers.)
(Refer to the exhibit.
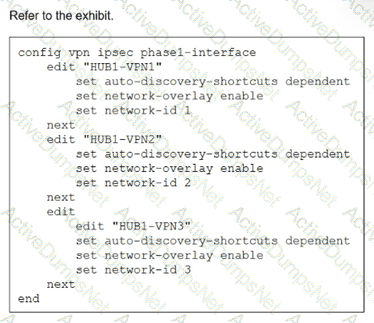
You update the spokes configuration of an existing auto-discovery VPN (ADVPN) topology by adding the parameters shown in the exhibit.
Which is a valid objective of those settings? Choose one answer.)
Refer to the exhibits.
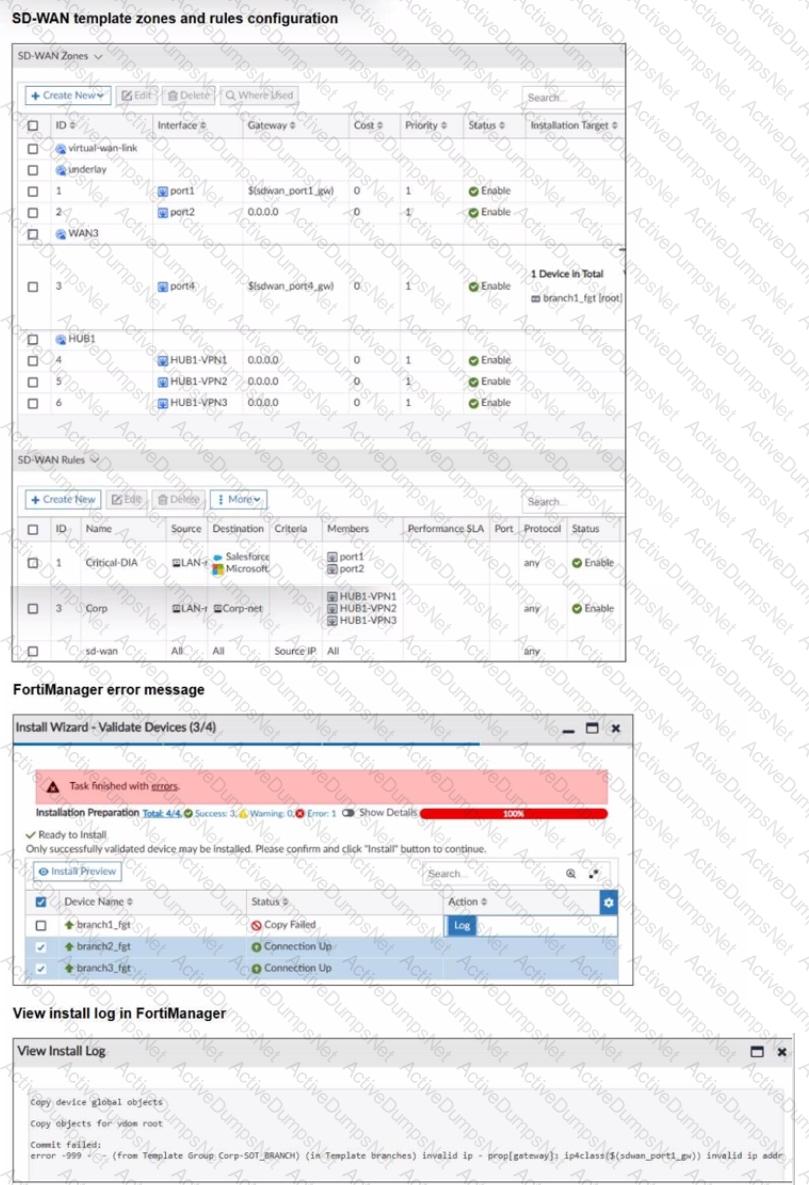
You use FortiManager to configure SD-WAN on three branch devices.
When you install the device settings. FortiManager prompts you with the error "Copy Failed" for the device branch1_fat When you click the log button. FortiManager displays the message shown in the exhibit.
You are planning a large SD-WAN deployment with approximately 1000 spokes and want to allow ADVPN between the spokes. Some remote sites use FortiSASE to connect to the company's SD-WAN hub. Which overlay routing configuration should you use?
Which three characteristics apply to provisioning templates available on FortiManager? (Choose three.)
Refer to the exhibit.
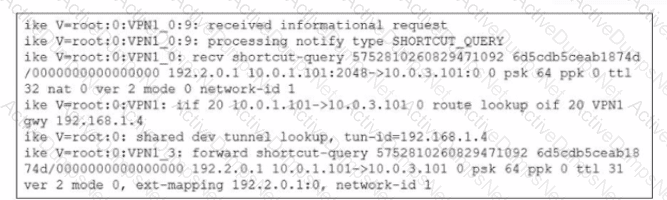
Which statement best describe the role of the ADVPN device in handling traffic?
SD-WAN interacts with many other FortiGate features. Some of them are required to allow SD-WAN to steer the traffic.
Which three configuration elements that you must configure before FortiGate can steer traffic according to SD-WAN rules? (Choose three.)
Refer to the exhibit.
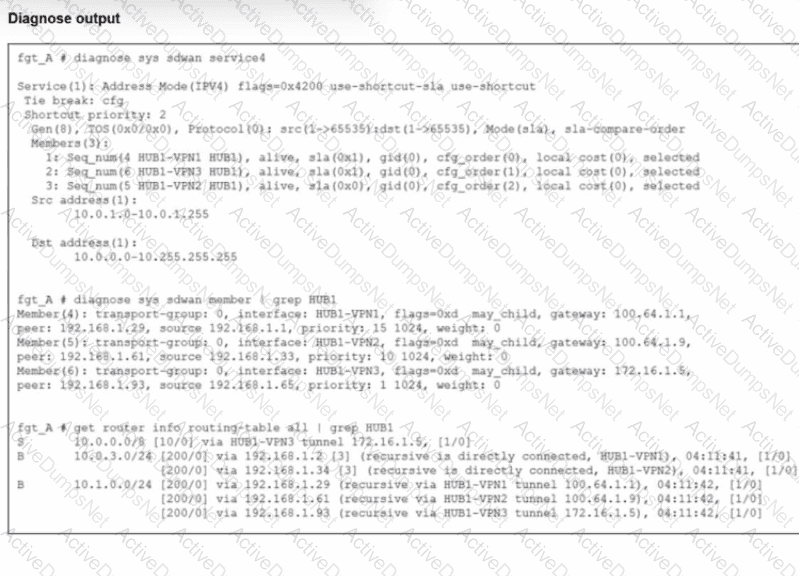
An administrator is troubleshooting SD-WAN on FortiGate. A device behind branch1_fgt generates traffic to the 10.0.0.0/8 network.
The administrator expects the traffic to match SD-WAN rule ID 1 and be routed over HUB1-VPN1. However, the traffic is routed over HUB1-VPN3.
Based on the output shown in the exhibit, which two reasons, individually or together, could explain the observed behavior? (Choose two.)
(In which order does FortiGate consider the following elements during the route lookup process? Choose one answer.)
You configured an SD-WAN rule with the best quality strategy and selected the predefined health check, Default_FortiGuard, to check the link performances against FortiGuard servers.
For the quality criteria, you selected Custom-profile-1.
Which factors does FortiGate use, and in which order. to determine the link that it should use to steer the traffic?
(Refer to the exhibit.
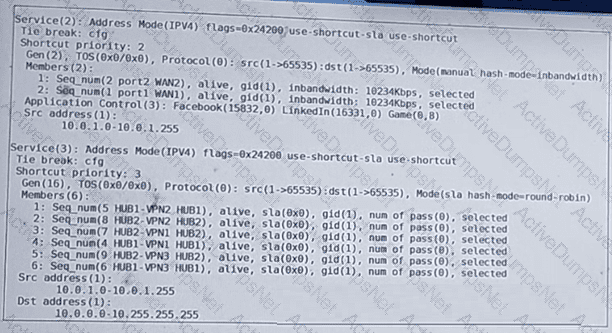
The administrator configured two SD-WAN rules to load balance traffic.
Which interfaces does FortiGate use to steer the traffic from 10.0.1.124 to 10.0.0.254? Choose one answer.)
Refer to the exhibit.
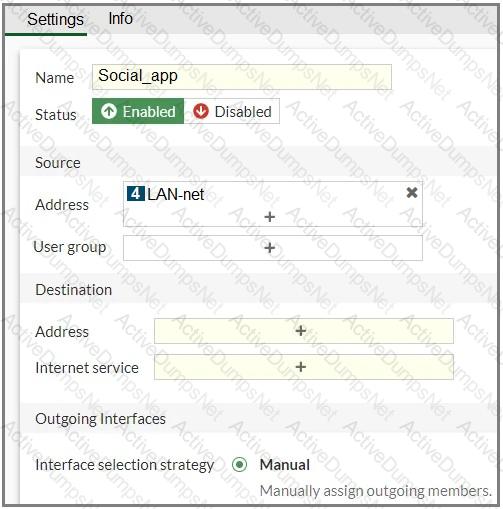
You configure SD-WAN on a standalone FortiGate device. You want to create an SD-WAN rule that steers Facebook and Linkedin traffic through the less costly internet link. The FortiGate GUI page appears as shown in the exhibit.
What should you do to set Facebook and LinkedIn as destinations?
An administrator is configuring SD-WAN to load balance their network traffic. Which two things should they consider when setting up SD-WAN? (Choose two.)
(Which two features must you configure before FortiGate can steer traffic according to SD-WAN rules? Choose two answers.)
