Fortinet FCSS_SASE_AD-25 FCSS - FortiSASE 25 Administrator Exam Practice Test
FCSS - FortiSASE 25 Administrator Questions and Answers
Which statement best describes the Digital Experience Monitor (DEM) feature on FortiSASE?
A customer wants to upgrade their legacy on-premises proxy to a cloud-based proxy for a hybrid network.
Which two FortiSASE features would help the customer achieve this outcome? (Choose two.)
Refer to the exhibits.
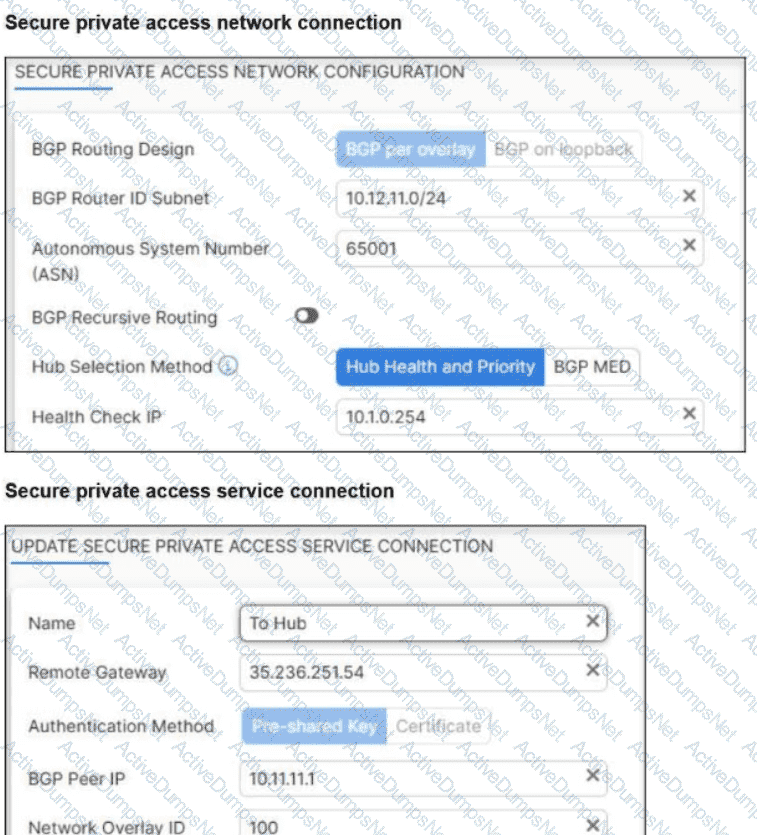
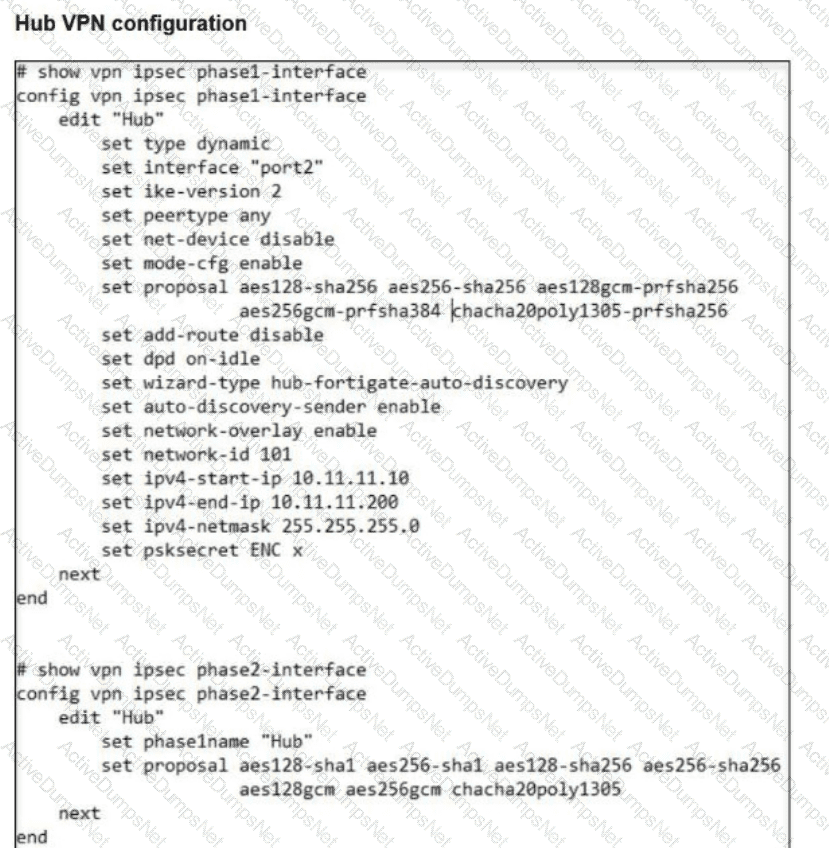
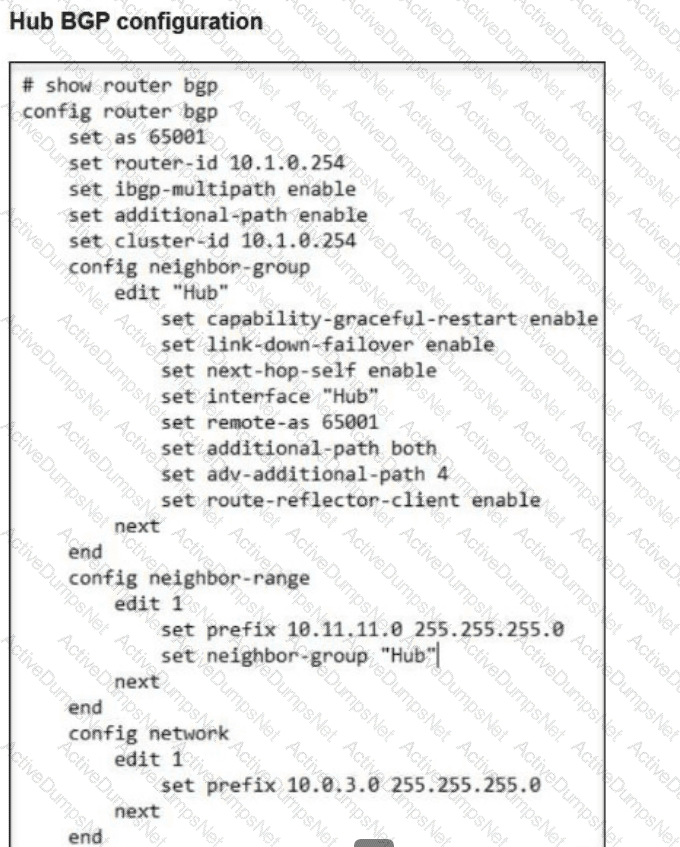

A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub.
The VPN tunnel does not establish.
Which configuration needs to be modified to bring the tunnel up?
Which two are required to enable central management on FortiSASE? (Choose two.)
Which FortiSASE feature ensures least-privileged user access to corporate applications that are protected by an on-premises FortiGate device?
Which description of the FortiSASE inline-CASB component is true?
What are two advantages of using zero-trust tags? (Choose two.)
Which information does FortiSASE use to bring network lockdown into effect on an endpoint?
What is required to enable the MSSP feature on FortiSASE?
Which two components are part of onboarding a secure web gateway (SWG) endpoint for secure internet access (SIA)? (Choose two.)
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page?
A company must provide access to a web server through FortiSASE secure private access for contractors.
What is the recommended method to provide access?
Which authentication method overrides any other previously configured user authentication on FortiSASE?
In a FortiSASE SD-WAN deployment with dual hubs, what are two benefits of assigning hubs with different priorities? (Choose two.)
Refer to the exhibit.
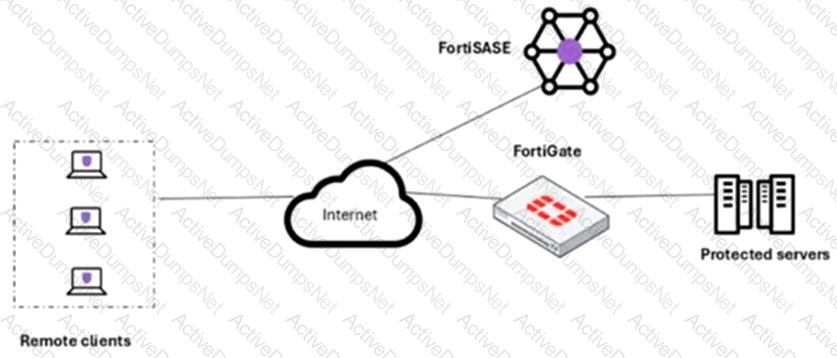
A customer needs to implement device posture checks for their remote endpoints while accessing the protected server. They also want the TCP traffic between the remote endpoints and the protected servers to be processed by FortiGate.
In this scenario, which two setups will achieve these requirements? (Choose two.)
