Fortinet FCSS_NST_SE-7.4 FCSS - Network Security 7.4 Support Engineer Exam Practice Test
FCSS - Network Security 7.4 Support Engineer Questions and Answers
Exhibit.
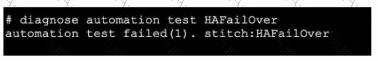
Refer to the exhibit, which shows the output of diagnose automation test.
What can you observe from the output? (Choose two.)
Refer to the exhibit, which shows a session entry.
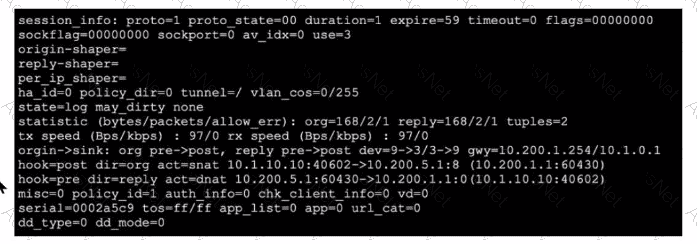
Which statement about this session is true?
Which exchange lakes care of DoS protection in IKEv2?
Exhibit.
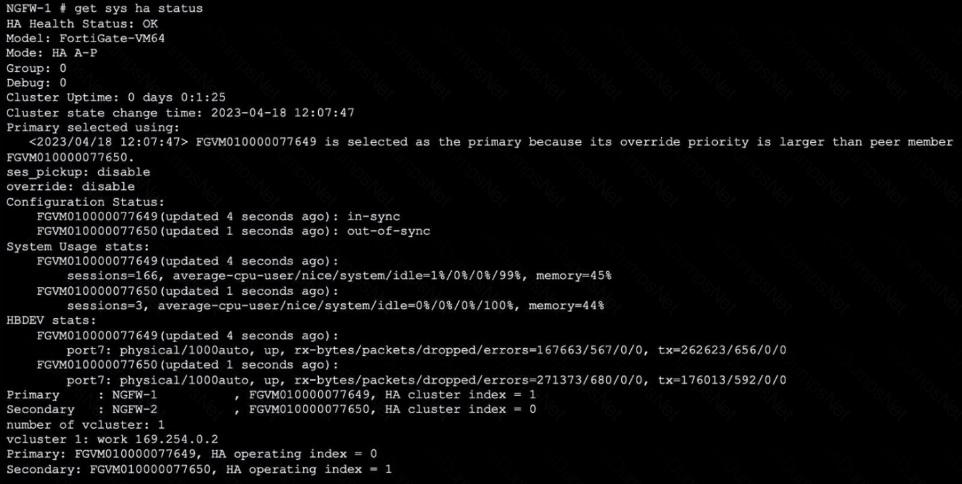
Refer to the exhibit, which shows the output of get system ha status.
NGFW-1 and NGFW-2 have been up for a week.
Which two statements about the output are true? (Choose two.)
Refer to the exhibit, which shows one way communication of the downstream FortiGate with the upstream FortiGate within a Security Fabric.
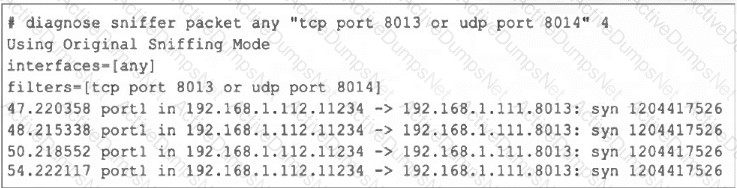
What three actions must you take to ensure successful communication? (Choose three.)
Refer to the exhibit, which shows the output of the command get router info bgp neighbors 100.64.2.254 advertised-routes.

What can you conclude from the output?
Refer to the exhibit, which shows the omitted output of a session table entry.
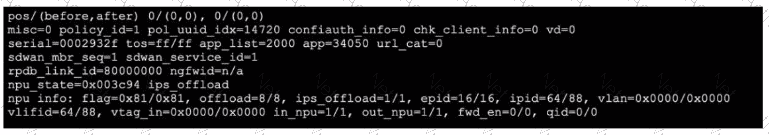
Which two statements are true? (Choose two.)
Exhibit.

Refer to the exhibit, which shows two entries that were generated in the FSSO collector agent logs.
What three conclusions can you draw from these log entries? {Choose three.)
Refer to the exhibit, which shows a partial output of the fssod daemon real-time debug command.
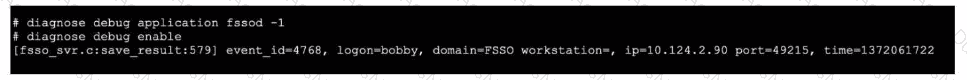
What two conclusions can you draw Itom the output? (Choose two.)
Which statement about IKEv2 is true?
What are two reasons you might see iprope_in_check() check failed, drop when using the debug flow? (Choose two.)
Refer to the exhibit, which shows the output of get router info bgp summary.
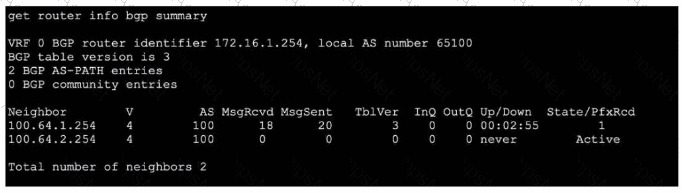
Which two statements are true? (Choose two.)
Refer to the exhibit, which shows the output of a policy route table entry.
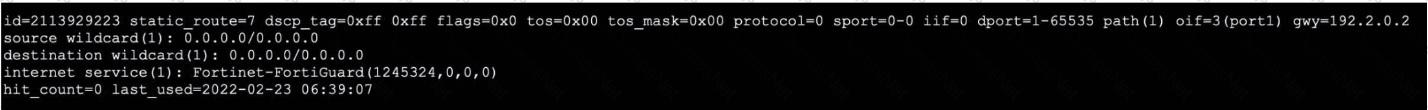
Which type of policy route does the output show?
Which two statements about an auxiliary session ate true? (Choose two.)
Which authentication option can you not configure under config user radius on FortiOS?
Refer to the exhibit, which shows partial outputs from two routing debug commands.
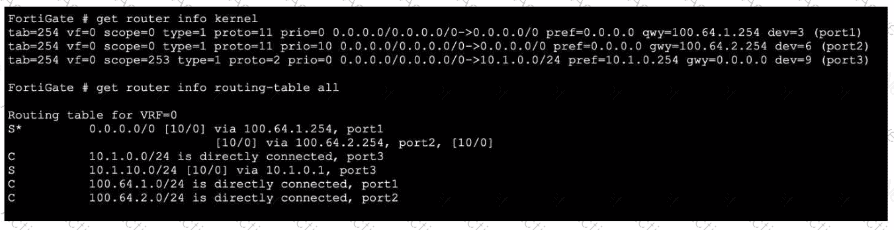
Which change must an administrator make on FortiGate to route web traffic from internal users to the internet, using ECMP?
Which statement about protocol options is true?
What are two functions of automation stitches? (Choose two.)
Refer to the exhibits.
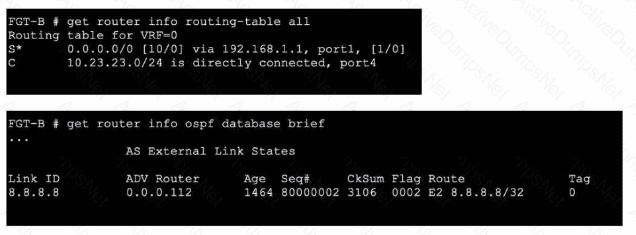
An administrator Is expecting to receive advertised route 8.8.8.8/32 from FGT-A. On FGT-B, they confirm that the route is being advertised and received, however, the route is not being injected into the routing table. What is the most likely cause of this issue?
