ECCouncil EC0-479 EC-Council Certified Security Analyst (ECSA) Exam Practice Test
EC-Council Certified Security Analyst (ECSA) Questions and Answers
Lance wants to place a honeypot on his network. Which of the following would be your recommendations?
You are working for a large clothing manufacturer as a computer forensics investigator and are called in to investigate an unusual case of an employee possibly stealing clothing designs from the company and selling them under a different brand name for a different company. What you discover during the course of the investigation is that the clothing designs are actually original products of the employee and the company has no policy against an employee selling his own designs on his own time. The only thing that you can find that the employee is doing wrong is that his clothing design incorporates the same graphic symbol as that of the company with only the wording in the graphic being different. What area of the law is the employee violating?
When examining the log files from a Windows IIS Web Server, how often is a new log file created?
The offset in a hexadecimal code is:
A (n) ____________ is one that‟s performed by a computer program rather than the attacker manually performing the steps in the attack sequence.
If a suspect computer is located in an area that may have toxic chemicals, you must:
While working for a prosecutor, What do you think you should do if the evidence you found appears to be exculpatory and is not being released to the defense ?
The ____________________ refers to handing over the results of private investigations to the authorities because of indications of criminal activity.
The use of warning banners helps a company avoid litigation by overcoming an employees assumed
____________ When connecting to the company‟s intranet, network or Virtual Private Network(VPN) and will allow the company‟s investigators to monitor, search and retrieve information stored within the network.
This organization maintains a database of hash signatures for known software:
Office Documents (Word, Excel and PowerPoint) contain a code that allows tracking the MAC or unique identifier of the machine that created the document. What is that code called?
You are working as a Computer forensics investigator for a corporation on a computer abuse case. You discover evidence that shows the subject of your investigation is also embezzling money from the company. The company CEO and the corporate legal counsel advise you to contact law enforcement and provide them with the evidence that you have founD. The law enforcement officer that responds requests that you put a network sniffer on your network and monitor all traffic to the subjects computer. You inform the officer that you will not be able to comply with that request because doing so would:
When investigating a Windows System, it is important to view the contents of the page or swap file because:
One way to identify the presence of hidden partitions on a suspect‟s hard drive is to:
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to sensitive information about the company clients. You have rummaged through their trash and found very little information. You do not want to set off any alarms on their network, so you plan on performing passive footprinting against their Web servers. What tool should you use?
What is the following command trying to accomplish?
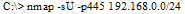
Why are Linux/Unix based computers better to use than Windows computers for idle scanning?
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
You work as a penetration tester for Hammond Security Consultants. You are currently working on a contract for the state government of California. Your next step is to initiate a DoS attack on their network. Why would you want to initiate a DoS attack on a system you are testing?
An "idle" system is also referred to as what?
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years. You navigate to archive.org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code. While searching through the code, you come across something abnormal:
What have you found?
How many possible sequence number combinations are there in TCP/IP protocol?
Click on the Exhibit Button
Paulette works for an IT security consulting company that is currently performing an audit for the firm ACE Unlimited. Paulette's duties include logging on to all the company's network equipment to ensure IOS versions are up-to-date and all the other security settings are as stringent as possible. Paulette presents the following screenshot to her boss so he can inform the client about necessary changes need to be made. From the screenshot, what changes should the client company make?
Exhibit:

Kyle is performing the final testing of an application he developed for the accounting department. His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
#include
#include
int main(int argc, char *argv[])
{
char buffer[10];
if (argc < 2)
{
fprintf(stderr, "USAGE: %s string\n", argv[0]);
return 1;
}
strcpy(buffer, argv[1]);
return 0;
}
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
Software firewalls work at which layer of the OSI model?
You have compromised a lower-level administrator account on an Active Directory network of a small company in Dallas, Texas. You discover Domain Controllers through enumeration. You connect to one of the Domain Controllers on port 389 using ldp.exe. What are you trying to accomplish here?
Software firewalls work at which layer of the OSI model?
Which of the following should a computer forensics lab used for investigations have?
During the course of an investigation, you locate evidence that may prove the innocence of the suspect of the investigation. You must maintain an unbiased opinion and be objective in your entire fact finding process. Therefore you report this evidence. This type of evidence is known as:
Law enforcement officers are conducting a legal search for which a valid warrant was obtaineD. While conducting the search, officers observe an item of evidence for an unrelated crime that was not included in the warrant. The item was clearly visible to the officers and immediately identified as evidence. What is the term used to describe how this evidence is admissible?
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
Windows identifies which application to open a file with by examining which of the following?
You are assisting in the investigation of a possible Web Server Hack. The company who called you stated that customers reported to them that whenever they entered the web address of the company in their browser, what they received was a porno graphic web site. The company checked the web server and nothing appears wrong. When you type in the IP address of the web site in your browser everything appears normal. What is the name of the attack that affects the DNS cache of the name resolution servers, resulting in those servers directing users to the wrong web site?
