VMware 2V0-21.23 VMware vSphere 8.x Professional Exam Practice Test
VMware vSphere 8.x Professional Questions and Answers
An administrator is tasked with moving an application and guest operating system (OS) running on top of a physical server to a software-defined data center (SDDC) in a remote secure location.
The following constraints apply:
• The remote secure location has no network connectivity to the outside world.
• The business owner is not concerned if all changes in the application make it to the SDDC in the secure location.
• The application's data is hosted in a database with a high number of transactions.
What could the administrator do to create an image of the guest OS and application that can be moved to this remote data center?
An administrator is tasked with looking into the disaster recovery options for protecting a database server using VMware vSphere Replication.
The following requirements must be met:
• The virtual machine must remain online during the protection.
• The virtual machine's snapshots must be used as part of the replication process.
Which step must the administrator complete to accomplish this task?
An administrator needs to provide encryption for workloads within an existing vSphere cluster. The following requirements must be met:
• Workloads should be encrypted at rest.
• Encrypted workloads must automatically be encrypted during transit.
• Encryption should not require any specific hardware.
What should the administrator configure to meet these requirements?
Refer to the exhibit.
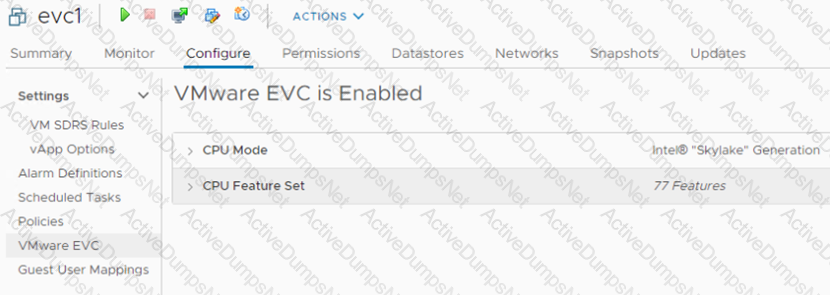
An administrator is tasked with adding new capacity to an existing software-defined data center (SDDC).
• The SDDC currently hosts two vSphere clusters (ClusterA and ClusterB) with different CPU compatibilities.
• vSphere vMotion and vSphere Distributed Resource Scheduler (DRS) are currently in use in the SDDC.
• The new capacity will be implemented by provisioning four ESXi hosts running a new generation of Intel Skylake CPUs.
• All workload virtual machines (VMs) must support live migration to any cluster in the SDDC.
The administrator noticed the running critical "ever virtual machine (VM) shown in the exhibit is not migrating using vSphere vMotion to the original Clusters A or B.
Which three steps must the administrator take to support this functionality? (Choose three.)
An administrator is responsible for the management of a VMware vCenter instance that is currently experiencing performance issues. The administrator quickly identifies that the CPU and memory utilization of vCenter is consistently over 80%. Upon further analysis, it seems that the vpxd process is contributing significantly to the performance issue.
A combination of which four steps should the administrator take to resolve the performance issues and ensure that a similar issue can be rectified without requiring downtime to vCenter moving forward? (Choose four.)
An administrator is preparing to perform an update to vSphere clusters that are running vSAN. The administrator wants to ensure that the following requirements are met as part of the update:
•All hosts in the cluster are updated with the same software.
•The firmware versions on the hosts are updated
•The new software versions are checked for compliance against the vSAN Hardware Compatibility List.
Which three steps should the administrator take to meet these requirements? (Choose three.)
An administrator is asked to configure a security policy at the port group level of a standard switch.
The following requirements must be met:
• The security policy must apply to all virtual machines on portgroup-1.
• All traffic must be forwarded, regardless of the destination.
An administrator is tasked with allowing a single user the ability to take snapshots on a virtual machine. When looking in vCenter, the administrator can see that there are already users and groups assigned permissions on the virtual machine as follows:
•The group VMJJsers has the Virtual Machine Power User role.
•The group VM_Viewers has the Read Only role.
The administrator confirms that the user requesting the additional access is currently one of five members of the VM_Viewers group
Which two steps should the administrator take to grant this user the additional access required without impacting the user access of others? (Choose two.)
An administrator is adding a new ESXi host to an existing vSphere cluster. When selecting the cluster, the administrator Is unable to use the Cluster Quickstart workflow to add and configure the additional host.
What could be the root cause of this issue?
A vSphere cluster hosts a three-tier application. The cluster has 50% resources available. If a host in the cluster fails, the database server must be online before the application server, and the application server must be online before the Web server.
Which feature can be used to meet these requirements?
An administrator is investigating reports of users experiencing difficulties logging into a VMware vCenter instance using LDAP accounts.
Which service should the administrator check as part of troubleshooting?
Refer to the exhibit.
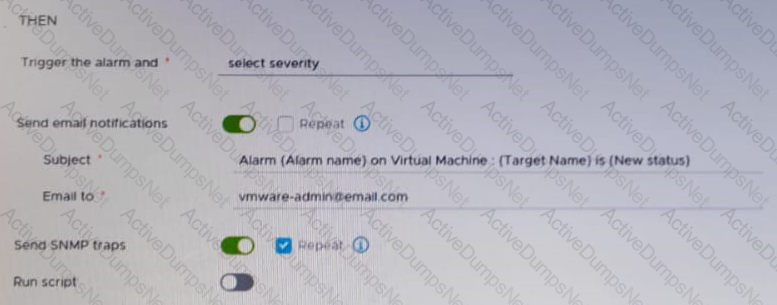
After updating a predefined alarm on VMware vCenter, an administrator enables email notifications as shown in the attached alarm; however, notifications are NOT being sent.
Where must the mail server settings be configured by the administrator to resolve this issue?
Following a merger with another company, an administrator is tasked with configuring an identity source for VMware vCenter so that all vSphere administrators can authenticate using their existing Active Directory accounts. Each company has user accounts in their own Active Directory forests.
The following additional information has been provided:
• The corporate policy states that only Windows-based machine accounts are allowed in Active Directory. Which action should the administrator take to configure vCenter Single Sign-On (SSO) to meet this requirement?
An administrator notices a performance issue in VMvvare vCenter To try and understand more about the performance issue, the administrator needs to gather more information about the vCenter database to eliminate a potential disk space issue.
Which two tools can the administrator use? (Choose two.)
An administrator is tasked with deploying a new on-premises software-defined data center (SDDC) that will contain a total of eight VMware vCenter instances.
The following requirements must be met:
• All vCenter instances should be visible in a single vSphere Client session.
• All vCenter inventory should be searchable from a single vSphere Client session.
• Any administrator must be able to complete operations on any vCenter instance using a single set of credentials.
What should the administrator configure to meet these requirements?
An administrator needs to consolidate a number of physical servers by migrating the workloads to a software-defined data center solution.
Which VMware solution should the administrator recommend?
An administrator must gracefully restart a virtual machine (VM) through the vSphere Client but the option is greyed out. The administrator has full administrative access on VMware vCenter and all the objects available in vCenter, but has no access to log onto the operating system.
Which action should the administrator take to meet the objective?
An administrator enables Secure Boot on an ESXi host. On booting the ESXi host, the following error message appears:
Fatal error: 39 (Secure Boot Failed)
An administrator manually configures a reference ESXi host that meets company security standards for vSphere environments. The administrator now needs to apply all of the security standards to every identically configured host across multiple vSphere clusters within a single VMware vCenter instance.
Which four steps would the administrator complete to meet this requirement? (Choose four.)
When configuring vCenter High Availability (HA), which two statements are true regarding the active, passive, and witness nodes? (Choose two.)
Which feature would allow for the non-disruptive migration of a virtual machine between two clusters in a single VMware vCenter instance?
After a number of outages within a production VMware software-defined data center, an administrator is tasked with identifying a solution to meet the following requirements:
• Reduce the risk of outages by proactively identifying issues with the environment and resolving them.
• Reduce the complexity of uploading log bundles when raising support tickets.
Which solution should the administrator recommend to meet these requirements?
An administrator wants to use tag-based placement rules on their virtual machine disks using VMware vCenter.
Which option would allow the administrator to achieve this?
An administrator is tasked with looking into the disaster recovery (DR) options for a software-defined data center (SDDC).
The following requirements must be met:
•All virtual machines (VMs) must be protected to a secondary site.
•The source VMs must remain online until the failover.
•When failing over to the secondary site, application downtime is allowed
•The DR failover must be managed from the vSphere Client.
•Costs must remain as low as possible.
How can the administrator accomplish this task?
An administrator is tasked with configuring remote direct memory access (RDMA) over Converged Ethernet v2 (RoCE v2).
Which two types of adapters must the administrator configure? (Choose two.)
An administrator is tasked with implementing a backup solution capable of backing up the Supervisor cluster, vSphere Pods, and persistent volumes.
Which two solutions must be used to meet this requirement? (Choose two.)
An administrator decides to restore VMware vCenter from a file-based backup following a failed upgrade. Which interface should the administrator use to complete the restore?
An administrator is planning to upgrade a VMware vCenter instance to version 8. It is currently integrated with the following solutions:
* VMware Aria Automation
* VMware Cloud Director
Which tool can the administrator use to run Interoperability reports before the upgrade process?
An administrator runs a two-node vSphere cluster, which contains two domain controller virtual machines (VMs). The administrator wants to ensure that VMs run on separate hosts without interfering with normal maintenance operations.
How should the administrator configure Distributed Resource Scheduler (DRS)?
An administrator is working with VMware Support and Is asked to provide log bundles for the ESXI hosts in an environment. Which three options Joes the administrator have? (Choose three.)
What are two uses cases for VMware Tools? (Choose two.)
A vSphere cluster has the following configuration:
• Virtual machines (VMs) are running Production and Test workloads
• vSphere Distributed Resource Scheduler (DRS) is enabled
• There are no resource pools in the cluster
Performance monitoring data shows that the Production workload VMs are not receiving their fully allocated memory when the vSphere cluster is fully utilized.
A combination of which two steps could the administrator perform to ensure that the Production VMs are always guaranteed the full allocation of memory? (Choose two.)
