Symantec 250-428 Administration of Symantec Endpoint Protection 14 Exam Practice Test
Administration of Symantec Endpoint Protection 14 Questions and Answers
A Symantec Endpoint Protection Manager (SEPM) administrator notices performance issues with the SEPM server. The Client tab becomes unresponsive in the SEPM console and .DAT files accumulate in the “agentinfo” folder.
Which tool should the administrator use to gather log files to submit to Symantec Technical Support?
Which action does the Shared Insight Cache (SIC) server take when the whitelist reaches maximum capacity?
A company needs to forward log data from Data Center A to Data Center B during off peak hours only.
How should the company architect its Symantec Endpoint Protection environment?
An administrator receives a browser certificate warning when accessing the Symantec Endpoint Protection Manager (SEPM) Web console.
Where can the administrator obtain the certificate?
Which two settings does an administrator enable to use the Risk Tracer Feature in the Virus and Spyware Protection policy? (Select two.)
Which ports on the company firewall must an administrator open to avoid problems when connecting to Symantec Public LiveUpdate servers?
Which client log shows that a client is downloading content from its designated source?
Which two Symantec Endpoint Protection components are used to distribute content updates? (Select two.)
A company has an application that requires network traffic in both directions to multiple systems at a specific external domain. A firewall rule was created to allow traffic to and from the external domain, but the rule is blocking incoming traffic.
What should an administrator enable in the firewall policy to allow this traffic?
Which Symantec Endpoint Protection Management (SEPM) database option is the default for deployments of fewer than 1,000 clients?
Which package type should an administrator use to reduce a SEP environment’s footprint when considering that new SEP 14 clients will be installed on point of sale terminals?
An administrator needs to increase the access speed for client files that are stored on a file server.
Which configuration should the administrator review to address the read speed from the server?
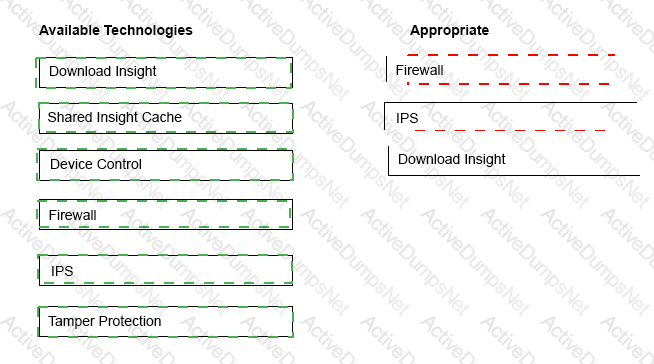
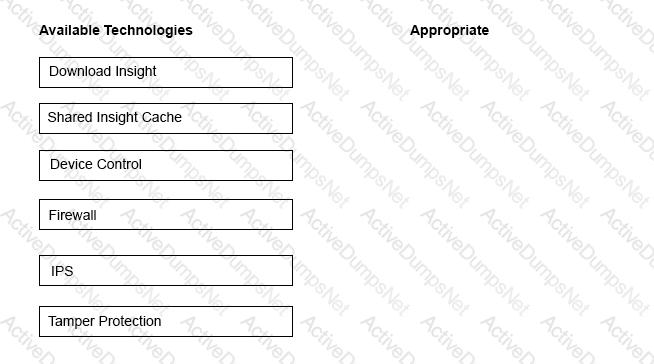
An administrator is unknowingly trying to connect to a malicious website and download a known threat within a .rar file. All Symantec Endpoint Protection technologies are installed on the client’s system.
Drag and drop the technologies to the right side of the screen in the sequence necessary to block or detect the malicious file.
Which action must a Symantec Endpoint Protection administrator take before creating custom Intrusion Prevention signatures?
Why does Power Eraser need Internet access?
A Symantec Endpoint Protection administrator must block traffic from an attacking computer for a specific time period.
Where should the administrator adjust the time to block the attacking computer?
When can an administrator add a new replication partner?
An administrator is recovering from a Symantec Endpoint Manager (SEPM) site failure.
Which file should the administrator use during an install of SEPM to recover the lost environment according to Symantec Disaster Recovery Best Practice documentation?
Which two options are available when configuring DNS change detections for SONAR? (Select two.)
Which action can an administrator take to improve the Symantec Endpoint Protection Manager (SEPM) dashboard performance and report accuracy?