Riverbed 299-01 Riverbed Certified Solutions Professional - Network Performance Management Exam Practice Test
Riverbed Certified Solutions Professional - Network Performance Management Questions and Answers
In this scenario, you have created a host group called My_Computers on Cascade Profiler. In that group you have included the subnet 192.168.1.0/25.
You have 10 devices in that group 192.168.1.1-10. The rest of the addresses are unused. While running reports on this segment of the network you notice that when a report is run using the entire subnet you see traffic destined for 192.168.1.120. When you run the same report specifying the host group the traffic does not appear. Why is this happening?
What does Cascade use as the flow key to identify a unique flow?
What is a benefit that Cascade Profiler might provide to Security Operations? (Select 3)
When links in a network are using WAN optimization, it is best if the Cascade Profiler or Express receives data from a _________or _________ monitoring traffic on the LAN side of the Steelhead that is located on the server side of the optimized connection. This is necessary in order to determine server delay.
(Select 2)
If a VLAN SPAN (VLAN101) is configured and monitored by Cascade Shark, which of the following is true? (Select 2)
For DNS reverse lookup, Cascade Profiler caches as follows:
If there is a Layer 7 fingerprint and a Layer 4 mapping for a particular application, which of the following is truE. (Select 5)
Which of the following statements is true regarding SNMP polling and NTP syncing among Cascade components?
When editing a previously configured service policy, what options become available if you click the 'show advanced settings' checkbox? (Select 3)
Which of the following configuration changes can be used to reduce the number of alerts generated overall for a Service?
Which of the following capabilities are supported by the Cascade Sensor appliance but are not supported by the Cascade Sensor-VE RSP packagE. (Select 2)
Within Cascade Pilot a Watch can: (Select 3)
When analyzing a large (100GB, for example) trace file within Cascade Pilot, you should:
How does Cascade Profiler obtain switch port discovery and population information?
Cascade Profiler provides identity information collected from Active Directory 2008 by installing and correctly configuring the 'Cascade Connector' agent software on:
Within Cascade Profiler you can set the recipient for policy notifications under Advanced configuration to:
A system administrator needs to update their Cascade Profiler host group settings to remove references to a decommissioned office on the 10.63.32.0/24 subnet.
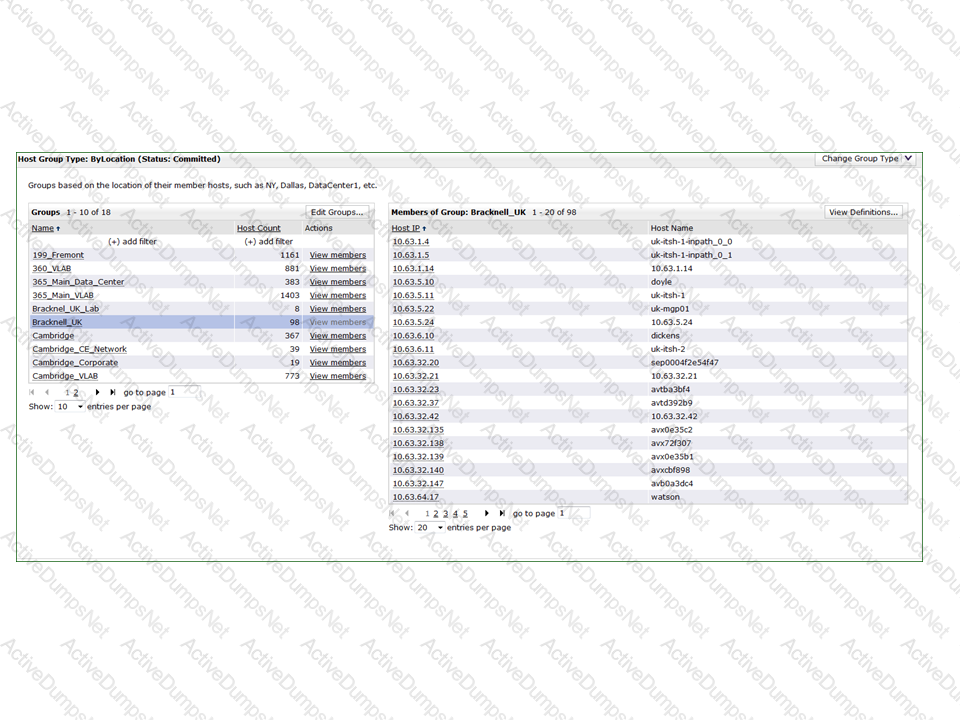
What is the best way to do this?
When defining a service which of the following are supported ways of aggregating the results? (Select 2)
What is the maximum number of Cascade Profilers that can be configured in the Cascade Shark appliance as receivers of flows?
Within Cascade Profiler, what can be done to prevent a data resolution from being available for selection on the Report Criteria section of traffic reports?
Which of the listed versions of NetFlow are supported by Cascade?
What is the maximum number of custom applications that can be defined on a Cascade Profiler?
For switch port Discovery on Cascade Profiler what device provides the MAC to IP address mapping?
Where is one place Cascade Profiler can obtain Identity (user) information for use in reporting user activity on a network?
For an analytic policy that monitors TCP retransmission bandwidth, which of the following best describes what is minimally required before a baseline can be established?
Which of the following is valid syntax for defining host groups? (Select 3)
What is one way Cascade obtains information about retransmissions in the network?
What is the typical retention time of packets of a CSK-01100 Cascade Shark appliance with 1 capture job?
When drilling down from a Cascade Profiler traffic report to analyze the underlying packets in Cascade Pilot, which of the following is NOT required?
What is the Active Timeout requirement on flow sources sending NetFlow to Cascade?
Refer to the Exhibit.

For a user defined host policy on Cascade Profiler, what would trigger this policy to generate an alert?
Which of the following are default user-defined policies on Cascade Profiler? (Select 3)
WAN optimization reports on Cascade Profiler require that the WAN interfaces for all Steelheads performing optimization are included in a WAN Interface group and are marked as Steelhead interfaces. Which of the following is true?
Once the Cascade Shark appliance has an initial configuration with an IP Address set to 10.1.1.1 you can connect to it from a web browser using the URL:
Which of the following does the Cascade Sensor device provide that the Cascade Sensor-VE does not? (Select 2)
Which of the following is false in regards to Cascade Profiler reporting and alerting? (Select 2)
