RedHat RH033 Red Hat Linux Essentials Exam Practice Test
Red Hat Linux Essentials Questions and Answers
Which of the following network diagnostic tools is NOT used in the Linux operating system?
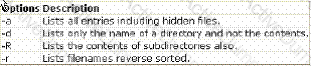
Which of the following commands can be used by a user to display the list of contents existing in his current user account?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Net Perfect Inc. The company has a Linux-based network.
By using the VI utility, you have created a document that has 100 lines. You want to replace all the occurrences of "net" with "Net" in the first 50 lines of the document. Which of the following commands will you use?
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. Rick, a Sales Manager, has a permission issue on a file. You want to know the names of groups of which Rick is a member. You want to store the information in a text file named
RickGroup.txt. Which of the following commands will you use to accomplish the task?
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. Rick, a Sales Manager, wants to combine the contents of the Sale1.txt and Sale2.txt files to
a new file named FinSale.txt. Which of the following commands will he use to accomplish the task?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. You want to run two programs, foo and bar. You also want to ensure that bar is executed if and only if foo has executed successfully. Which of the following command sequences will John use to accomplish the task?
You work as the Network Administrator for McNeil Inc. The company has a Linux-based network.
You are working a root user on the Red Hat operating system. You want to search for files named snow.html, Snow.html, SNOW.html in the current directory. Which of the following commands should you use to accomplish the task?
You are working with the vi editor and writing a textfile. Which of the following commands will you use if you want to move the cursor 3 characters to the right?
You work as the Network Technician for Tech Perfect Inc. The company has a Linux-based network.
You are working as a root user on the Linux operating system. You want to create an alias such that when you type c, the system should run the clear command to clear the screen. Which of the following tools should you use to accomplish the task?
You work as a Technician for Net World Inc. The company has a Linux-based network. You have configured a file server on the company's etwork. You want to summarize disk usage of each file in a particular directory on the file server. Which of the following commands will you use?
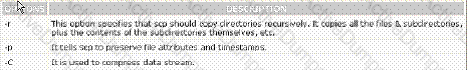
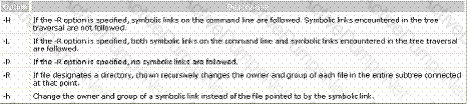
Which of the following commands is used to securely copy files from one host to another over the network?
You want to temporarily change your primary group to another group of which you are a member. In this process, a new shell will be created, and when you exit the shell, your previous group will be reinstated. Which of the following commands will you use to accomplish this task?
You work as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. You want to modify a configuration file in a Linux server. Which of the following utilities will you use to accomplish the task?
Which of the following key-combinations is used to redo a change undone by a u command in vim?
John works as a Network Administrator for Perfect Solutions Inc. The company has a Debian Linuxbased network. He is working on the bash shell in which he creates a variable VAR1. After some calculations, he opens a new ksh shell. Now, he wants to set VAR1 as an environmental variable so that he can retrieve VAR1 into the ksh shell. Which of the following commands will John run to accomplish the task?
Fill in the blank with the appropriate permission to complete the statement below.
The___________command is used to start xsession using the xinit utility.
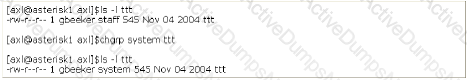
You work as the Network technician for McNeil Inc. The company has a Linux-based Network. You are working on the Red Hat operating system. You want to remove some write protected files and directories. Which of the following commands should you use to accomplish this task?
You work as the Network Technician for Tech Perfect Inc. The company has a Linux-based network.
You are currently working on vim. You opened a file in four windows in a single vim screen. You want to jump from one window to another. Which of the following key-combinations should you use to accomplish the task?
Which of the following commands is used to append the list of files in the /tmp directory to an existing file named deletelater.txt?
Which of the following is a multi-platform instant messaging client, based on a library named libpurple?
Which of the following is NOT true about the inode table in the Linux operating system?
You work as a Network Administrator for Net Perfect Inc. The company has a Linux-based network.
You have created a folder named Report.
You have made David the owner of the folder. The members of a group named JAdmin can access the folder and have Read, Write, and
Execute permissions. No other user can access the folder. You want to ensure that the members of
the JAdmin group do not have Write permission on the folder. Also, you want other users to have Read permission on the Report folder.
Whizh of the following commands will you use to accomplish the task?