Paloalto Networks XSIAM-Engineer Palo Alto Networks XSIAM Engineer Exam Practice Test
Palo Alto Networks XSIAM Engineer Questions and Answers
In the Incident War Room, which command is used to update incident fields identified in the incident layout?
When Cortex XDR agents are on servers in a zone with no internet access, which configuration will keep them communicating with the platform?
Which two requirements must be met for a Cortex XDR agent to successfully use the Broker VM as a download source for content updates? (Choose two.)
Which action will prevent the automatic extraction of indicators such as IP addresses and URLs from a script's output?
A Cortex XSIAM engineer is implementing role-based access control (RBAC) and scope-based access control (SBAC) for users accessing the Cortex XSIAM tenant with the following requirements:
Users managing machines in Europe should be able to manage and control all endpoints and installations, create profiles and policies, view alerts, and initiate Live Terminal, but only for endpoints in the Europe region.
Users managing machines in Europe should not be able to create, modify, or delete new or existing user roles.
The Europe region endpoints are identified by both of the following:
Endpoint Tag = "Europe-Servers" and Endpoint Group = "Europe" for servers in Europe
Endpoint Group = "Europe" and Endpoint Tag = "Europe-Workstation" for workstations in Europe
Which two sets of implementation actions should the engineer take? (Choose two.)
While using the playbook debugger, an engineer attaches the context of an alert as test data.
What happens with respect to the interactions with the list objects via tasks in this scenario?
Which two alert notification options can be configured without creating a playbook? (Choose two.)
Which two alert notification options can be configured without creating a playbook? (Choose two.)
Which installer type should be used when upgrading a non-Linux Kubernetes cluster?
Administrators from Building 3 have been added to Cortex XSIAM to perform limited functions on a subset of endpoints. Custom roles have been created and applied to the administrators to limit their permissions, but their access should also be constrained through the principle of least privilege according to the endpoints they are allowed to manage. All endpoints are part of an endpoint group named "Building3," and some endpoints may also be members of other endpoint groups.
Which technical control will restrict the ability of the administrators to manage endpoints outside of their area of responsibility, while maintaining visibility to Building 3's endpoints?
A Cortex XSIAM engineer adds a disable injection and prevention rule for a specific running process. After an hour, the engineer disables the rule to reinstate the security capabilities, but the capabilities are not applied.
What is the explanation for this behavior?
Which step must be taken to enable Cloud Identity Engine on Cortex XSIAM?
A security engineer notices that in the past week ingestion has spiked significantly. Upon investigating the anomaly, it is determined that a custom application developed in-house caused the spike. The custom application is sending syslog to the Broker VM Syslog Collector applet. The engineer consults with the SOC analyst, who determines that 90% of the logs from the custom application are not used.
What can the engineer configure to reduce the ingestion?
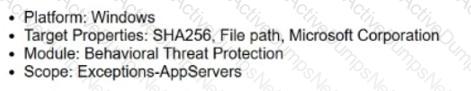
A Behavioral Threat Protection (BTP) alert is triggered with an action of "Prevented (Blocked)" on one of several application servers running Windows Server 2022. The investigation determines the involved processes to be legitimate core OS binaries, and the description from the triggered BTP rule is an acceptable risk for the company to allow the same activity in the future.
This type of activity is only expected on the endpoints that are members of the endpoint group "AppServers," which already has a separate prevention policy rule with an exceptions profile named "Exceptions-AppServers" and a malware profile named "Malware-AppServers."
The CGO that was terminated has the following properties:
SHA256: eb71ea69dd19f728ab9240565e8c7efb59821e19e3788e289301e1e74940c208
File path: C:\Windows\System32\cmd.exe
Digital Signer: Microsoft Corporation
How should the exception be created so that it is scoped as narrowly as possible to minimize the security gap?
A Cortex XSIAM engineer at a SOC downgrades a critical threat intelligence content pack from the Cortex Marketplace while performing routine maintenance. As a result, the SOC team loses access to the latest threat intelligence data.
Which action will restore the functionality of the content pack to its previously installed version?
How does Cortex XSIAM manage licensing for Kubernetes environments?
How can a Cortex XSIAM engineer resolve the issue when a SOC analyst escalates missing details after merging two similar incidents?
An engineer wants to onboard data from a third-party vendor’s firewall. There is no content pack available for it, so the engineer creates custom data source integration and parsing rules to generate a dataset with the firewall data.
How can the analytics capabilities of Cortex XSIAM be used on the data?