Paloalto Networks XSIAM-Analyst Palo Alto Networks XSIAM Analyst Exam Practice Test
Palo Alto Networks XSIAM Analyst Questions and Answers
Which Cytool command will re-enable protection on an endpoint that has Cortex XDR agent protection paused?
Which feature terminates a process during an investigation?
Which two methods can be used to create and share queries into the Query Library? (Choose two.)
What is the expected behavior when querying a data model with no specific fields specified in the query?
Which type of task can be used to create a decision tree in a playbook?
A threat hunter discovers a true negative event from a zero-day exploit that is using privilege escalation to launch "Malware pdf.exe". Which XQL query will always show the correct user context used to launch "Malware pdf.exe"?
In the Endpoint Data context menu of the Cortex XSIAM endpoints table, where will an analyst be able to determine which users accessed an endpoint via Live Terminal?
While investigating an incident on the Incident Overview page, an analyst notices that the playbook encountered an error. Upon playbook work plan review, it is determined that the error was caused by a timeout. However, the analyst does not have the necessary permissions to fix or create a new playbook.
Given the critical nature of the incident, what can the analyst do to ensure the playbook continues executing the remaining steps?
What information is provided in the timeline view of Cortex XSIAM?
Based on the artifact details in the image below, what can an analyst infer from the hexagon-shaped object with the exclamation mark (!) at the center?

Two security analysts are collaborating on complex but similar incidents. The first analyst merges the two incidents into one for easier management. The other analyst immediately discovers that the custom incident field values relevant to the investigation are missing.
How can the team retrieve the missing details?
An analyst conducting a threat hunt needs to collect multiple files from various endpoints. The analyst begins the file retrieval process by using the Action Center, but upon review of the retrieved files, notices that the list is incomplete and missing files, including kernel files.
What could be the reason for the issue?
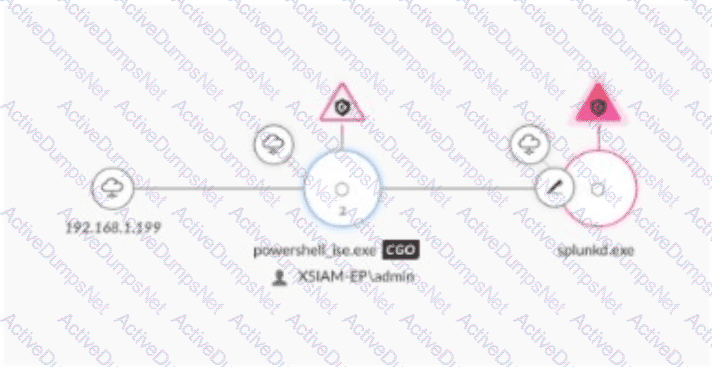
Based on the image below, which two additional steps should a SOC analyst take to secure the endpoint? (Choose two.)
In addition to defining the Rule Name and Severity Level, which step or set of steps accurately reflects how an analyst should configure an indicator prevention rule before reviewing and saving it?
Which attribution evidence will have the lowest confidence level when evaluating assets to determine if they belong to an organization’s attack surface?
