- Home
- Paloalto Networks
- Security Operations
- XDR-Engineer
- XDR-Engineer - Palo Alto Networks XDR Engineer
Paloalto Networks XDR-Engineer Palo Alto Networks XDR Engineer Exam Practice Test
Palo Alto Networks XDR Engineer Questions and Answers
What is a benefit of ingesting and forwarding Palo Alto Networks NGFW logs to Cortex XDR?
Options:
Sending endpoint logs to the NGFW for analysis
Blocking network traffic based on Cortex XDR detections
Enabling additional analysis through enhanced application logging
Automated downloading of malware signatures from the NGFW
Answer:
CExplanation:
IntegratingPalo Alto Networks Next-Generation Firewalls (NGFWs)with Cortex XDR by ingesting and forwarding NGFW logs allows for enhanced visibility and correlation across network and endpoint data. NGFW logs contain detailed information about network traffic, applications, and threats, which Cortex XDR can use to improve its detection and analysis capabilities.
Correct Answer Analysis (C):Enabling additional analysis through enhanced application loggingis a key benefit. NGFW logs include application-layer data (e.g., App-ID, user activity, URL filtering), which Cortex XDR can ingest to perform deeper analysis, such as correlating network events with endpoint activities. This enhanced logging enables better incident investigation, threat detection, and behavioral analytics by providing a more comprehensive view of the environment.
Why not the other options?
A. Sending endpoint logs to the NGFW for analysis: The integration is about forwarding NGFW logs to Cortex XDR, not the other way around. Endpoint logs are not sent to the NGFW for analysis in this context.
B. Blocking network traffic based on Cortex XDR detections: While Cortex XDR can share threat intelligence with NGFWs to block traffic (via mechanisms like External Dynamic Lists), this is not the primary benefit of ingesting NGFW logs into Cortex XDR. The focus here is on analysis, not blocking.
D. Automated downloading of malware signatures from the NGFW: NGFWs do not provide malware signatures to Cortex XDR. Malware signatures are typically sourced from WildFire (Palo Alto Networks’ cloud-based threat analysis service), not directly from NGFW logs.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains NGFW integration: “Ingesting Palo Alto Networks NGFW logs into Cortex XDR enables additional analysis through enhanced application logging, improving visibility and correlation across network and endpoint data” (paraphrased from the Data Ingestion section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers NGFW log integration, stating that “forwarding NGFW logs to Cortex XDR enhancesapplication-layer analysis for better threat detection” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration” as a key exam topic, encompassing NGFW log integration.
A multinational company with over 300,000 employees has recently deployed Cortex XDR in North America. The solution includes the Identity Threat Detection and Response (ITDR) add-on, and the Cortex team has onboarded the Cloud Identity Engine to the North American tenant. After waiting the required soak period and deploying enough agents to receive Identity and threat analytics detections, the team does not see user, group, or computer details for individuals from the European offices. What may be the reason for the issue?
Options:
The XDR tenant is not in the same region as the Cloud Identity Engine
The Cloud Identity Engine plug-in has not been installed and configured
The Cloud Identity Engine needs to be activated in all global regions
The ITDR add-on is not compatible with the Cloud Identity Engine
Answer:
AExplanation:
TheIdentity Threat Detection and Response (ITDR)add-on in Cortex XDR enhances identity-based threat detection by integrating with theCloud Identity Engine, which synchronizes user,group, and computer details from identity providers (e.g., Active Directory, Okta). For the Cloud Identity Engine to provide comprehensive identity data across regions, it must be properly configured and aligned with the Cortex XDR tenant’s region.
Correct Answer Analysis (A):The issue is likely thatthe XDR tenant is not in the same region as the Cloud Identity Engine. Cortex XDR tenants are region-specific (e.g., North America, Europe), and the Cloud Identity Engine must be configured to synchronize data with the tenant in the same region. If the North American tenant is used but the European offices’ identity data is managed by a Cloud Identity Engine in a different region (e.g., Europe), the tenant may not receive user, group, or computer details for European users, causing the observed issue.
Why not the other options?
B. The Cloud Identity Engine plug-in has not been installed and configured: The question states that the Cloud Identity Engine has been onboarded, implying it is installed and configured. The issue is specific to European office data, not a complete lack of integration.
C. The Cloud Identity Engine needs to be activated in all global regions: The Cloud Identity Engine does not need to be activated in all regions. It needs to be configured to synchronize with the tenant in the correct region, and regional misalignment is the more likely issue.
D. The ITDR add-on is not compatible with the Cloud Identity Engine: The ITDR add-on is designed to work with the Cloud Identity Engine, so compatibility is not the issue.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains Cloud Identity Engine integration: “The Cloud Identity Engine must be configured in the same region as the Cortex XDR tenant to ensure proper synchronization of user, group, and computer details” (paraphrased from the Cloud Identity Engine section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers ITDR and identity integration, stating that “regional alignment between the tenant and Cloud Identity Engine is critical for accurate identity data” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration” as a key exam topic, encompassing Cloud Identity Engine configuration.
Using the Cortex XDR console, how can additional network access be allowed from a set of IP addresses to an isolated endpoint?
Options:
Add entries in Configuration section of Security Settings
Add entries in the Allowed Domains section of Security Settings for the tenant
Add entries in Exceptions Configuration section of Isolation Exceptions
Add entries in Response Actions section of Agent Settings profile
Answer:
CExplanation:
In Cortex XDR,endpoint isolationis a response action that restricts network communication to and from an endpoint, allowing only communication with the Cortex XDR management server to maintain agent functionality. To allow additional network access (e.g., from a set of IP addresses) to an isolated endpoint, administrators can configureisolation exceptionsto permit specific traffic while the endpoint remains isolated.
Correct Answer Analysis (C):TheExceptions Configuration section of Isolation Exceptionsin the Cortex XDR console allows administrators to define exceptions for isolated endpoints, such as permitting network access from specific IP addresses. This ensures that the isolated endpoint can communicate with designated IPs (e.g., for IT support or backup servers) while maintaining isolation from other network traffic.
Why not the other options?
A. Add entries in Configuration section of Security Settings: The Security Settings section in the Cortex XDR console is used for general tenant-wide configurations (e.g., password policies), not for managing isolation exceptions.
B. Add entries in the Allowed Domains section of Security Settings for the tenant: The Allowed Domains section is used to whitelist domains for specific purposes (e.g., agent communication), not for defining IP-based exceptions for isolated endpoints.
D. Add entries in Response Actions section of Agent Settings profile: The Response Actions section in Agent Settings defines automated response actions (e.g., isolate on specific conditions), but it does not configure exceptions for already isolated endpoints.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains isolation exceptions: “To allow specific network access to an isolated endpoint, add IP addresses or domains in the Exceptions Configuration section of Isolation Exceptions in the Cortex XDR console” (paraphrased from the Endpoint Isolation section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers isolation management, stating that “Isolation Exceptions allow administrators to permit network access from specific IPs to isolated endpoints” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “post-deployment management and configuration” as a key exam topic, encompassing isolation exception configuration.
A query is created that will run weekly via API. After it is tested and ready, it is reviewed in the Query Center. Which available column should be checked to determine how many compute units will be used when the query is run?
Options:
Query Status
Compute Unit Usage
Simulated Compute Units
Compute Unit Quota
Answer:
BExplanation:
In Cortex XDR, theQuery Centerallows administrators to manage and reviewXQL (XDR Query Language)queries, including those scheduled to run via API. Each query consumescompute units, a measure of the computational resources required to execute the query. To determine how many compute units a query will use, theCompute Unit Usagecolumn in the Query Center provides the actual or estimated resource consumption based on the query’s execution history or configuration.
Correct Answer Analysis (B):TheCompute Unit Usagecolumn in the Query Center displays the number of compute units consumed by a query when it runs. For a tested and ready query, this column provides the most accurate information on resource usage, helping administrators plan for API-based executions.
Why not the other options?
A. Query Status: The Query Status column indicates whether the query ran successfully, failed, or is pending, but it does not provide information on compute unit consumption.
C. Simulated Compute Units: While some systems may offer simulated estimates, Cortex XDR’s Query Center does not have a “Simulated Compute Units” column. The actual usage is tracked in Compute Unit Usage.
D. Compute Unit Quota: The Compute Unit Quota refers to the total available compute units for the tenant, not the specific usage of an individual query.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains Query Center functionality: “The Compute Unit Usage column in the Query Center shows the compute units consumed by a query, enabling administrators to assess resource usage for scheduled or API-based queries” (paraphrased from the Query Center section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers query management, stating that “Compute Unit Usage provides details on the resources used by each query in the Query Center” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “maintenance and troubleshooting” as a key exam topic, encompassing query resource management.
Which method will drop undesired logs and reduce the amount of data being ingested?
Options:
[COLLECT:vendor="vendor", product="product", target_brokers="", no_hit=drop] * drop _raw_log contains "undesired logs";
[INGEST:vendor="vendor", product="product", target_dataset="vendor_product_raw",no_hit=drop] * filter _raw_log not contains "undesired logs";
[COLLECT:vendor="vendor", product="product", target_dataset="", no_hit=drop] * drop _raw_log contains "undesired logs";
[INGEST:vendor="vendor", product="product", target_brokers="vendor_product_raw", no_hit=keep] * filter _raw_log not contains "undesired logs";
Answer:
CExplanation:
In Cortex XDR, managing data ingestion involves defining rules to collect, filter, or drop logs to optimize storage and processing. The goal is todrop undesired logsto reduce the amount of data ingested. The syntax used in the options appears to be a combination of ingestion rule metadata (e.g., [COLLECT] or [INGEST]) and filtering logic, likely written in a simplified query language for log processing. Thedropaction explicitly discards logs matching a condition, whilefilterwithnot containscan achieve similar results by keeping only logs that do not match the condition.
Correct Answer Analysis (C):The method in option C,[COLLECT:vendor="vendor", product="product", target_dataset="", no_hit=drop] * drop _raw_log contains "undesired logs";, explicitlydropslogs where the raw log content contains "undesired logs". The [COLLECT] directive defines the log collection scope (vendor, product, and dataset), and the no_hit=drop parameter indicates that unmatched logs are dropped. The drop _raw_log contains "undesired logs" statement ensures that logs matching the "undesired logs" pattern are discarded, effectively reducing the amount of data ingested.
Why not the other options?
A. [COLLECT:vendor="vendor", product="product", target_brokers="", no_hit=drop] * drop _raw_log contains "undesired logs";: This is similar to option C but uses target_brokers="", which is typically used for Broker VM configurations rather than direct dataset ingestion. While it could work, option C is more straightforward with target_dataset="".
B. [INGEST:vendor="vendor", product="product", target_dataset="vendor_product_raw", no_hit=drop] * filter _raw_log not contains "undesired logs";: This method uses filter _raw_log not contains "undesired logs" to keep logs that do not match the condition, which indirectly drops undesired logs. However, the drop action in option C is more explicit and efficient for reducing ingestion.
D. [INGEST:vendor="vendor", product="product", target_brokers="vendor_product_raw", no_hit=keep] * filter _raw_log not contains "undesired logs";: The no_hit=keep parameter means unmatched logs are kept, which does not align with the goal of reducing data. The filter statement reduces data, but no_hit=keep may counteract this by retaining unmatched logs, making this less effective than option C.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains log ingestion rules: “To reduce data ingestion, use the drop action to discard logs matching specific patterns, such as _raw_log contains 'pattern'” (paraphrased from the Data Ingestion section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers data ingestion optimization, stating that “dropping logs with specific content using drop _raw_log contains is an effective way to reduce ingested data volume” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration” as a key exam topic, encompassing log filtering and dropping.
An engineer wants to automate the handling of alerts in Cortex XDR and defines several automation rules with different actions to be triggered based on specific alert conditions. Some alerts do not trigger the automation rules as expected. Which statement explains why the automation rules might not apply to certain alerts?
Options:
They are executed in sequential order, so alerts may not trigger the correct actions if the rules are not configured properly
They only apply to new alerts grouped into incidents by the system and only alerts that generateincidents trigger automation actions
They can only be triggered by alerts with high severity; alerts with low or informational severity will not trigger the automation rules
They can be applied to any alert, but they only work if the alert is manually grouped into an incident by the analyst
Answer:
AExplanation:
In Cortex XDR,automation rules(also known as response actions or playbooks) are used to automate alert handling based on specific conditions, such as alert type, severity, or source. These rules are executed in a defined order, and the first rule that matches an alert’s conditions triggers its associated actions. If automation rules are not triggering as expected, the issue often lies in their configuration or execution order.
Correct Answer Analysis (A):Automation rules areexecuted in sequential order, and each alert is evaluated against the rules in the order they are defined. If the rules are not configured properly (e.g., overly broad conditions in an earlier rule or incorrect prioritization), an alert may match an earlier rule and trigger its actions instead of the intended rule, or it may not match any rule due to misconfigured conditions. This explains why some alerts do not trigger the expected automation rules.
Why not the other options?
B. They only apply to new alerts grouped into incidents by the system and only alerts that generate incidents trigger automation actions: Automation rules can apply to both standalone alerts and those grouped into incidents. They are not limited to incident-related alerts.
C. They can only be triggered by alerts with high severity; alerts with low or informational severity will not trigger the automation rules: Automation rules can be configured to trigger based on any severity level (high, medium, low, or informational), so this is not a restriction.
D. They can be applied to any alert, but they only work if the alert is manually grouped into an incident by the analyst: Automation rules do not require manual incident grouping; they can apply to any alert based on defined conditions, regardless of incident status.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains automation rules: “Automation rules are executed in sequential order, and the first rule matching an alert’s conditions triggers its actions. Misconfigured rules or incorrect ordering can prevent expected actions from being applied” (paraphrased from the Automation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers automation, stating that “sequential execution of automation rules requires careful configuration to ensure the correct actions are triggered” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “playbook creation and automation” as a key exam topic, encompassing automation rule configuration.
Which statement describes the functionality of fixed filters and dashboard drilldowns in enhancing a dashboard’s interactivity and data insights?
Options:
Fixed filters allow users to select predefined data values, while dashboard drilldowns enable users to alter the scope of the data displayed by selecting filter values from the dashboard header
Fixed filters limit the data visible in widgets, while dashboard drilldowns allow users to download data from the dashboard in various formats
Fixed filters let users select predefined or dynamic values to adjust the scope, while dashboard drilldowns provide interactive insights or trigger contextual changes, like linking to XQL searches
Fixed filters allow users to adjust the layout, while dashboard drilldowns provide links to external reports and/or dashboards
Answer:
CExplanation:
In Cortex XDR,fixed filtersanddashboard drilldownsare key features that enhance the interactivity and usability of dashboards. Fixed filters allow users to refine the data displayed in dashboard widgets by selecting predefined or dynamic values (e.g., time ranges, severities, or alertsources), adjusting the scope of the data presented. Dashboard drilldowns, on the other hand, enable users to interact with widget elements (e.g., clicking on a chart bar) to gain deeper insights, such as navigating to detailed views, other dashboards, or executingXQL (XDR Query Language)searches for granular data analysis.
Correct Answer Analysis (C):The statement in option C accurately describes the functionality:Fixed filters let users select predefined or dynamic values to adjust the scope, ensuring users can focus on specific subsets of data (e.g., alerts from a particular source).Dashboard drilldowns provide interactive insights or trigger contextual changes, like linking to XQL searches, allowing users to explore related data or perform detailed investigations directly from the dashboard.
Why not the other options?
A. Fixed filters allow users to select predefined data values, while dashboard drilldowns enable users to alter the scope of the data displayed by selecting filter values from the dashboard header: This is incorrect because drilldowns do not alter the scope via dashboard header filters; they provide navigational or query-based insights (e.g., linking to XQL searches). Additionally, fixed filters support both predefined and dynamic values, not just predefined ones.
B. Fixed filters limit the data visible in widgets, while dashboard drilldowns allow users to download data from the dashboard in various formats: While fixed filters limit data in widgets, drilldowns do not primarily facilitate data downloads. Downloads are handled via export functions, not drilldowns.
D. Fixed filters allow users to adjust the layout, while dashboard drilldowns provide links to external reports and/or dashboards: Fixed filters do not adjust the dashboard layout; they filter data. Drilldowns can link to other dashboards but not typically to external reports, and their primary role is interactive data exploration, not just linking.
Exact Extract or Reference:
TheCortex XDR Documentation Portaldescribes dashboard features: “Fixed filters allow users to select predefined or dynamic values to adjust the scope of data in widgets. Drilldowns enable interactive exploration by linking to XQL searches or other dashboards for contextual insights” (paraphrased from the Dashboards and Widgets section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers dashboard configuration, stating that “fixed filters refine data scope, and drilldowns provide interactive links to XQL queries or related dashboards” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “dashboards and reporting” as a key exam topic, encompassing fixed filters and drilldowns.
What will enable a custom prevention rule to block specific behavior?
Options:
A correlation rule added to an Agent Blocking profile
A custom behavioral indicator of compromise (BIOC) added to an Exploit profile
A custom behavioral indicator of compromise (BIOC) added to a Restriction profile
A correlation rule added to a Malware profile
Answer:
CExplanation:
In Cortex XDR,custom prevention rulesare used to block specific behaviors or activities on endpoints by leveragingBehavioral Indicators of Compromise (BIOCs). BIOCs define patterns of behavior (e.g., specific process executions, file modifications, or network activities) that, when detected, can trigger preventive actions, such as blocking a process or isolating an endpoint. These BIOCs are typically associated with aRestriction profile, which enforces blocking actions for matched behaviors.
Correct Answer Analysis (C):Acustom behavioral indicator of compromise (BIOC)added to aRestriction profileenables a custom prevention rule to block specific behavior. The BIOC defines the behavior to detect (e.g., a process accessing a sensitive file), and the Restriction profile specifies the preventive action (e.g., block the process). This configuration ensures that the identified behavior is blocked on endpoints where the profile is applied.
Why not the other options?
A. A correlation rule added to an Agent Blocking profile: Correlation rules are used to generate alerts by correlating events across datasets, not to block behaviors directly. There is no “Agent Blocking profile” in Cortex XDR; this is a misnomer.
B. A custom behavioral indicator of compromise (BIOC) added to an Exploit profile: Exploit profiles are used to detect and prevent exploit-based attacks (e.g., memory corruption), not general behavioral patterns defined by BIOCs. BIOCs are associated with Restriction profiles for blocking behaviors.
D. A correlation rule added to a Malware profile: Correlation rules do not directly block behaviors; they generate alerts. Malware profiles focus on file-based threats (e.g., executables analyzed by WildFire), not behavioral blocking via BIOCs.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains BIOC and Restriction profiles: “Custom BIOCs can be added to Restriction profiles to block specific behaviors on endpoints, enabling tailored prevention rules” (paraphrased from the BIOC and Restriction Profile sections). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers prevention rules, stating that “BIOCs in Restriction profiles enable blocking of specific endpoint behaviors” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing BIOC and prevention rule configuration.
Multiple remote desktop users complain of in-house applications no longer working. The team uses macOS with Cortex XDR agents version 8.7.0, and the applications were previously allowed by disable prevention rules attached to the Exceptions Profile "Engineer-Mac." Based on the images below, what is a reason for this behavior?
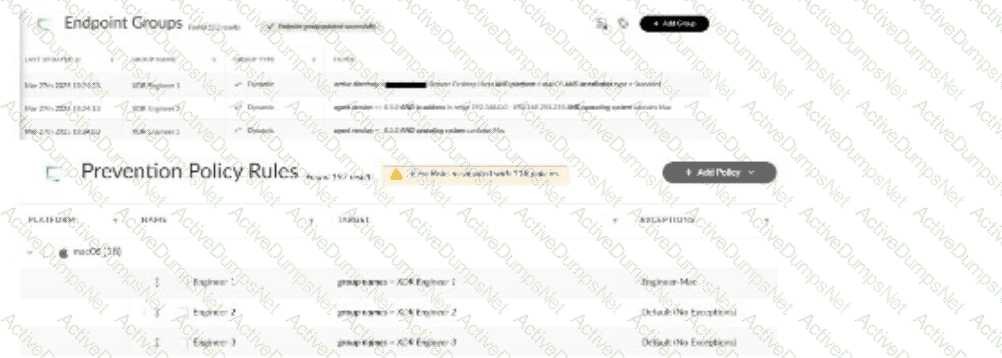
Options:
Endpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range
The Cloud Identity Engine is disconnected or removed
XDR agent version was downgraded from 8.7.0 to 8.4.0
Installation type changed from VDI to Kubernetes
Answer:
AExplanation:
The scenario involves macOS users with Cortex XDR agents (version 8.7.0) who can no longer run in-house applications that were previously allowed via disable prevention rules in the"Engineer-Mac" Exceptions Profile. This profile is applied to an endpoint group (e.g., "Mac-Engineers"). Theissue likely stems from a change in the endpoint group’s configuration or the endpoints’ attributes, affecting policy application.
Correct Answer Analysis (A):The reason for the behavior is that theendpoint IP address changed from 192.168.0.0 range to 192.168.100.0 range. In Cortex XDR, endpoint groups can be defined using dynamic criteria, such as IP address ranges, to apply specific policies like the "Engineer-Mac" Exceptions Profile. If the group "Mac-Engineers" was defined to include endpoints in the 192.168.0.0 range, and the remote desktop users’ IP addresses changed to the 192.168.100.0 range (e.g., due to a network change or VPN reconfiguration), these endpoints would no longer belong to the "Mac-Engineers" group. As a result, the "Engineer-Mac" Exceptions Profile, which allowed the in-house applications, would no longer apply, causing the applications to be blocked by default prevention rules.
Why not the other options?
B. The Cloud Identity Engine is disconnected or removed: The Cloud Identity Engine provides user and group data for identity-based policies, but it is not directly related to Exceptions Profiles or application execution rules. Its disconnection would not affect the application of the "Engineer-Mac" profile.
C. XDR agent version was downgraded from 8.7.0 to 8.4.0: The question states the users are using version 8.7.0, and there’s no indication of a downgrade. Even if a downgrade occurred, it’s unlikely to affect the application of an Exceptions Profile unless specific features were removed, which is not indicated.
D. Installation type changed from VDI to Kubernetes: The installation type (e.g., VDI for virtual desktops or Kubernetes for containerized environments) is unrelated to macOS endpoints running remote desktop sessions. This change would not impact the application of the Exceptions Profile.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains endpoint group policies: “Dynamic endpoint groups based on IP address ranges apply policies like Exceptions Profiles; if an endpoint’s IP changes to a different range, it may no longer belong to the group, affecting policy enforcement” (paraphrased from the Endpoint Management section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers policy application, stating that “changes in IP address ranges can cause endpoints to fall out of a group, leading to unexpected policy behavior like blocking previously allowed applications” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “Cortex XDR agent configuration” as a key exam topic, encompassing endpoint group and policy management.
In addition to using valid authentication credentials, what is required to enable the setup of the Database Collector applet on the Broker VM to ingest database activity?
Options:
Valid SQL query targeting the desired data
Access to the database audit log
Database schema exported in the correct format
Access to the database transaction log
Answer:
AExplanation:
TheDatabase Collector appleton the Broker VM in Cortex XDR is used to ingest database activity logs by querying the database directly. To set up the applet, valid authentication credentials (e.g., username and password) are required to connect to the database. Additionally, avalid SQL querymust be provided to specify the data to be collected, such as specific tables, columns, or events (e.g., login activity or data modifications).
Correct Answer Analysis (A):Avalid SQL query targeting the desired datais required to configure the Database Collector applet. The query defines which database records or events are retrieved and sent to Cortex XDR for analysis. This ensures the applet collects only the relevant data, optimizing ingestion and analysis.
Why not the other options?
B. Access to the database audit log: While audit logs may contain relevant activity, the Database Collector applet queries the database directly using SQL, not by accessing audit logs. Audit logs are typically ingested via other methods, such as Filebeat or syslog.
C. Database schema exported in the correct format: The Database Collector does not require an exported schema. The SQL query defines the data structure implicitly, and Cortex XDR maps the queried data to its schema during ingestion.
D. Access to the database transaction log: Transaction logs are used for database recovery or replication, not for direct data collection by the Database Collector applet, which relies on SQL queries.
Exact Extract or Reference:
TheCortex XDR Documentation Portaldescribes the Database Collector applet: “To configure the Database Collector, provide valid authentication credentials and a valid SQL query to retrieve the desired database activity” (paraphrased from the Broker VM Applets section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers data ingestion, stating that “the Database Collector applet requires a SQL query to specify the data to ingest from the database” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “data ingestion and integration” as a key exam topic, encompassing Database Collector configuration.
A correlation rule is created to detect potential insider threats by correlating user login events from one dataset with file access events from another dataset. The rule must retain all user login events, even if there are no matching file access events, to ensure no login activity is missed.
text
Copy
dataset = x
| join (dataset = y)
Which type of join is required to maintain all records from dataset x, even if there are no matching events from dataset y?
Options:
Inner
Left
Right
Outer
Answer:
BExplanation:
In Cortex XDR, correlation rules useXQL (XDR Query Language)to combine data from multiple datasets to detect patterns, such as insider threats. Thejoinoperation in XQL is used to correlate events from two datasets based on a common field (e.g., user ID). The type of join determines how records are matched and retained when there are no corresponding events in one of the datasets.
The question specifies that the correlation rule must retainall user login eventsfrom dataset x (the primary dataset containing login events), even if there are no matching file access events in dataset y (the secondary dataset). This requirement aligns with aLeft Join(also called Left Outer Join), which includes all records from the left dataset (dataset x) and any matching records from the right dataset (dataset y). If there is no match in dataset y, the result includes null values for dataset y’s fields, ensuring no login events are excluded.
Correct Answer Analysis (B):ALeft Joinensures that all records from dataset x (user login events) are retained, regardless of whether there are matching file access events in dataset y. This meets the requirement to ensure no login activity is missed.
Why not the other options?
A. Inner: An Inner Join only includes records where there is a match in both datasets (x and y). This would exclude login events from dataset x that have no corresponding file access events in dataset y, which violates the requirement.
C. Right: A Right Join includes all records from dataset y (file access events) and only matching records from dataset x. This would prioritize file access events, potentially excluding login events with no matches, which is not desired.
D. Outer: A Full Outer Join includes all records from both datasets, with nulls in places where there is no match. While this retains all login events, it also includes unmatched file access events from dataset y, which is unnecessary for the stated requirement of focusing on login events.
Exact Extract or Reference:
TheCortex XDR Documentation Portalin theXQL Reference Guideexplains join operations: “A Left Join returns all records from the left dataset and matching records from the right dataset. If there is no match, null values are returned for the right dataset’s fields” (paraphrased from the XQL Join section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers correlation rules and XQL, noting that “Left Joins are used in correlation rules to ensure all events from the primary dataset are retained, even without matches in the secondary dataset” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetlists “detection engineering” as a key exam topic, including creating correlation rules with XQL.
During the deployment of a Broker VM in a high availability (HA) environment, after configuring the Broker VM FQDN, an XDR engineer must ensure agent installer availability and efficient content caching to maintain performance consistency across failovers. Which additionalconfiguration steps should the engineer take?
Options:
Use shared SSL certificates and keys for all Broker VMs and configure a single IP address for failover
Upload the-signed SSL server certificate and key and deploy a load balancer
Deploy a load balancer and configure SSL termination at the load balancer
Enable synchronized session persistence across Broker VMs and use a self-signed certificate and key
Answer:
BExplanation:
In a high availability (HA) environment, theBroker VMin Cortex XDR acts as a local proxy to facilitate agent communications, content caching, and installer distribution, reducing dependency on direct cloud connections. To ensureagent installer availabilityandefficient content cachingacross failovers, the Broker VM must be configured to handle agent requests consistently, even if one VM fails. This requires proper SSL certificate management and load balancing to distribute traffic across multiple Broker VMs.
Correct Answer Analysis (B):The engineer shouldupload the signed SSL server certificate and keyto each Broker VM to secure communications and ensure trust between agents and the Broker VMs. Additionally, deploying aload balancerin front of the Broker VMs allows traffic to be distributed across multiple VMs, ensuring availability and performance consistency during failovers. The load balancer uses the configured Broker VM FQDN to route agent requests, and the signed SSL certificate ensures secure, uninterrupted communication. This setup supports content caching and installer distribution by maintaining a stable connection point for agents.
Why not the other options?
A. Use shared SSL certificates and keys for all Broker VMs and configure a single IP address for failover: While shared SSL certificates can be used, configuring a single IP address for failover (e.g., via VRRP or a floating IP) is less flexible than a load balancer and may not efficiently handle content caching or installer distribution across multiple VMs. Load balancers are preferred for HA setups in Cortex XDR.
C. Deploy a load balancer and configure SSL termination at the load balancer: SSL termination at the load balancer means the load balancer decrypts traffic before forwarding it to the Broker VMs, requiring unencrypted communication between the load balancer and VMs. This is not recommended for Cortex XDR, as Broker VMs require end-to-end SSL encryption for security, and SSL termination complicates certificate management.
D. Enable synchronized session persistence across Broker VMs and use a self-signed certificate and key: Self-signed certificates are not recommended for production HA environments, as they can cause trust issues with agents and require manual configuration. Synchronized session persistence is not a standard feature for Broker VMs and is unnecessary for content caching or installer availability.
Exact Extract or Reference:
TheCortex XDR Documentation Portaldescribes Broker VM HA configuration: “For high availability, deploy multiple Broker VMs behind a load balancer and upload a signed SSL server certificate and key to each VM to secure agent communications” (paraphrased from the Broker VM Deployment section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers Broker VM setup, stating that “a load balancer with signed SSL certificates ensures agent installer availability and content caching in HA environments” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “planning and installation” as a key exam topic, encompassing Broker VM deployment for HA.
Based on the image of a validated false positive alert below, which action is recommended for resolution?

Options:
Create an alert exclusion for OUTLOOK.EXE
Disable an action to the CGO Process DWWIN.EXE
Create an exception for the CGO DWWIN.EXE for ROP Mitigation Module
Create an exception for OUTLOOK.EXE for ROP Mitigation Module
Answer:
DExplanation:
In Cortex XDR, a false positive alert involvingOUTLOOK.EXEtriggering aCGO (Codegen Operation)alert related toDWWIN.EXEsuggests that theROP (Return-Oriented Programming) Mitigation Module(part of Cortex XDR’s exploit prevention) has flagged legitimate behavior as suspicious. ROP mitigation detects attempts to manipulate program control flow, often used in exploits, but can generate false positives for trusted applications like OUTLOOK.EXE. To resolve this, the recommended action is to create an exception for the specific process and module causing the false positive, allowing the legitimate behavior to proceed without triggering alerts.
Correct Answer Analysis (D):Create an exception for OUTLOOK.EXE for ROP Mitigation Moduleis the recommended action. Since OUTLOOK.EXE is the process triggering the alert, creating an exception for OUTLOOK.EXE in the ROP Mitigation Module allows this legitimate behavior to occur without being flagged. This is done by adding OUTLOOK.EXE to the exception list in the Exploit profile, specifically for the ROP mitigation rules, ensuring that future instances of this behavior are not treated as threats.
Why not the other options?
A. Create an alert exclusion for OUTLOOK.EXE: While an alert exclusion can suppress alerts for OUTLOOK.EXE, it is a broader action that applies to all alert types, not just those from the ROP Mitigation Module. This could suppress other legitimate alerts for OUTLOOK.EXE, reducing visibility into potential threats. An exception in the ROP Mitigation Module is more targeted.
B. Disable an action to the CGO Process DWWIN.EXE: Disabling actions for DWWIN.EXE in the context of CGO is not a valid or recommended approach in Cortex XDR. DWWIN.EXE (Dr. Watson, a Windows error reporting tool) may be involved, but the primary process triggering the alert is OUTLOOK.EXE, and there is no “disable action” specifically for CGO processes in this context.
C. Create an exception for the CGO DWWIN.EXE for ROP Mitigation Module: While DWWIN.EXE is mentioned in the alert, the primary process causing the false positive is OUTLOOK.EXE, as it’s the application initiating the behavior. Creating an exception for DWWIN.EXE would not address the root cause, as OUTLOOK.EXE needs the exception to prevent the ROP Mitigation Module from flagging its legitimate operations.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains false positive resolution: “To resolve false positives in the ROP Mitigation Module, create an exception for the specific process (e.g., OUTLOOK.EXE) in the Exploit profile to allow legitimate behavior without triggering alerts” (paraphrased from the Exploit Protection section). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers exploit prevention tuning, stating that “exceptions for processes like OUTLOOK.EXE in the ROP Mitigation Module prevent false positives while maintaining protection” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing false positive resolution.
What is the earliest time frame an alert could be automatically generated once the conditions of a new correlation rule are met?
Options:
Between 30 and 45 minutes
Immediately
5 minutes or less
Between 10 and 20 minutes
Answer:
CExplanation:
In Cortex XDR,correlation rulesare used to detect specific patterns or behaviors by analyzing ingested data and generating alerts when conditions are met. The time frame for alert generation depends on the data ingestion pipeline, the processing latency of the Cortex XDR backend, and the rule’s evaluation frequency. For a new correlation rule, once the conditions are met (i.e., the relevant events are ingested and processed), Cortex XDR typically generates alerts within a short time frame, often5 minutes or less, due to its near-real-time processing capabilities.
Correct Answer Analysis (C):Theearliest time framefor an alert to be generated is5 minutes or less, as Cortex XDR’s architecture is designed to process and correlate events quickly. This accounts for the time to ingest data, evaluate the correlation rule, and generate the alert in the system.
Why not the other options?
A. Between 30 and 45 minutes: This time frame is too long for Cortex XDR’s near-real-time detection capabilities. Such delays might occur in systems with significant processing backlogs, but not in a properly configured Cortex XDR environment.
B. Immediately: While Cortex XDR is fast, “immediately” implies zero latency, which is not realistic due to data ingestion, processing, and rule evaluation steps. A small delay (within 5 minutes) is expected.
D. Between 10 and 20 minutes: This is also too long for the earliest possible alert generation in Cortex XDR, as the system is optimized for rapid detection and alerting.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains correlation rule processing: “Alerts are generated within 5 minutes or less after the conditions of a correlation rule are met, assuming data is ingested and processed in near real-time” (paraphrased from the Correlation Rules section). TheEDU-262: Cortex XDR Investigation and Responsecourse covers detection engineering, stating that “Cortex XDR’s correlation engine processes rules and generates alerts typically within a few minutes of event ingestion” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing correlation rule alert generation.
Which XQL query can be saved as a behavioral indicator of compromise (BIOC) rule, then converted to a custom prevention rule?
Options:
dataset = xdr_data
| filter event_type = ENUM.DEVICE and action_process_image_name = "**"
and action_process_image_command_line = "-e cmd*"
and action_process_image_command_line != "*cmd.exe -a /c*"
dataset = xdr_data
| filter event_type = ENUM.PROCESS and event_type = ENUM.DEVICE and action_process_image_name = "**"
and action_process_image_command_line = "-e cmd*"
and action_process_image_command_line != "*cmd.exe -a /c*"
dataset = xdr_data
| filter event_type = FILE and (event_sub_type = FILE_CREATE_NEW or event_sub_type = FILE_WRITE or event_sub_type = FILE_REMOVE or event_sub_type = FILE_RENAME) and agent_hostname = "hostname"
| filter lowercase(action_file_path) in ("/etc/*", "/usr/local/share/*", "/usr/share/*") and action_file_extension in ("conf", "txt")
| fields action_file_name, action_file_path, action_file_type, agent_ip_a
dataset = xdr_data
| filter event_type = ENUM.PROCESS and action_process_image_name = "**"
and action_process_image_command_line = "-e cmd*"
and action_process_image_command_line != "*cmd.exe -a /c*"
Answer:
DExplanation:
In Cortex XDR, aBehavioral Indicator of Compromise (BIOC)rule defines a specific pattern of endpoint behavior (e.g., process execution, file operations, or network activity) that can trigger an alert. BIOCs are often created usingXQL (XDR Query Language)queries, which are then saved as BIOC rules to monitor for the specified behavior. To convert a BIOC into acustom prevention rule, the BIOC must be associated with aRestriction profile, which allows the defined behavior to be blocked rather than just detected. For a query to be suitable as a BIOC and convertible to a prevention rule, it must meet the following criteria:
It must monitor a behavior that Cortex XDR can detect on an endpoint, such as process execution, file operations, or device events.
The behavior must be actionable for prevention (e.g., blocking a process or file operation), typically involving events like process launches (ENUM.PROCESS) or file modifications (ENUM.FILE).
The query should not include overly complex logic (e.g., multiple event types with conflicting conditions) that cannot be translated into a BIOC rule.
Let’s analyze each query to determine which one meets these criteria:
Option A: dataset = xdr_data | filter event_type = ENUM.DEVICE ...This query filters for event_type = ENUM.DEVICE, which relates to device-related events (e.g., USB device connections). While device events can be monitored, the additional conditions (action_process_image_name = "**" and action_process_image_command_line) are process-related attributes, which are typically associated with ENUM.PROCESS events, not ENUM.DEVICE. This mismatch makes the query invalid for a BIOC, as it combines incompatible event types and attributes. Additionally, device events are not typically used for custom prevention rules, as prevention rules focus on blocking processes or fileoperations, not device activities.
Option B: dataset = xdr_data | filter event_type = ENUM.PROCESS and event_type = ENUM.DEVICE ...This query attempts to filter for events that are both ENUM.PROCESS and ENUM.DEVICE (event_type = ENUM.PROCESS and event_type = ENUM.DEVICE), which is logically incorrect because an event cannot have two different event types simultaneously. In XQL, the event_type field must match a single type (e.g., ENUM.PROCESS or ENUM.DEVICE), and combining them with an and operator results in no matches. This makes the query invalid for creating a BIOC rule, as it will not return any results and cannot be used for detection or prevention.
Option C: dataset = xdr_data | filter event_type = FILE ...This query monitors file-related events (event_type = FILE) with specific sub-types (FILE_CREATE_NEW, FILE_WRITE, FILE_REMOVE, FILE_RENAME) on a specific hostname, targeting file paths (/etc/*, /usr/local/share/*, /usr/share/*) and extensions (conf, txt). While this query can be saved as a BIOC to detect file operations, it is not ideal for conversion to a custom prevention rule. Cortex XDR prevention rules typically focus on blocking process executions (via Restriction profiles), not file operations. While file-based BIOCs can generate alerts, converting them to prevention rules is less common, as Cortex XDR’s prevention mechanisms are primarily process-oriented (e.g., terminating a process), not file-oriented (e.g., blocking a file write). Additionally, the query includes complex logic (e.g., multiple sub-types, lowercase() function, fields clause), which may not fully translate to a prevention rule.
Option D: dataset = xdr_data | filter event_type = ENUM.PROCESS ...This query monitors process execution events (event_type = ENUM.PROCESS) where the process image name matches a pattern (action_process_image_name = "**"), the command line includes -e cmd*, and excludes commands matching *cmd.exe -a /c*. This query is well-suited for a BIOC rule, as it defines a specific process behavior (e.g., a process executing with certain command-line arguments) that Cortex XDR can detect on an endpoint. Additionally, this type of BIOC can be converted to a custom prevention rule by associating it with aRestriction profile, which can block the process execution if the conditions are met. For example, the BIOC can be configured to detect processes with action_process_image_name = "**" and action_process_image_command_line = "-e cmd*", and a Restriction profile can terminate such processes to prevent the behavior.
Correct Answer Analysis (D):
Option D is the correct choice because it defines a process-based behavior (ENUM.PROCESS) that can be saved as a BIOC rule to detect the specified activity (processes with certain command-line arguments). It can then be converted to a custom prevention rule by adding it to a Restriction profile, which will block the process execution when the conditions are met. The query’s conditions are straightforward and compatible with Cortex XDR’s BIOC and prevention framework, making it the best fit for the requirement.
Exact Extract or Reference:
TheCortex XDR Documentation Portalexplains BIOC and prevention rules: “XQL queries monitoring process events (ENUM.PROCESS) can be saved as BIOC rules to detect specific behaviors, and these BIOCs can be added to a Restriction profile to create custom prevention rules that block the behavior” (paraphrased from the BIOC and Restriction Profile sections). TheEDU-260: Cortex XDR Prevention and Deploymentcourse covers BIOC creation, stating that “process-based XQL queries are ideal for BIOCs and can be converted to prevention rules via Restriction profiles to block executions” (paraphrased from course materials). ThePalo Alto Networks Certified XDR Engineer datasheetincludes “detection engineering” as a key exam topic, encompassing BIOC rule creation and conversion to prevention rules.
Unlock XDR-Engineer Features
- XDR-Engineer All Real Exam Questions
- XDR-Engineer Exam easy to use and print PDF format
- Download Free XDR-Engineer Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
Questions & Answers PDF Demo
- XDR-Engineer All Real Exam Questions
- XDR-Engineer Exam easy to use and print PDF format
- Download Free XDR-Engineer Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
