Paloalto Networks Practitioner Palo Alto Networks Cybersecurity Practitioner (PCCP) Exam Practice Test
Palo Alto Networks Cybersecurity Practitioner (PCCP) Questions and Answers
What type of DNS record maps an IPV6 address to a domain or subdomain to another hostname?
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
What are two limitations of signature-based anti-malware software? (Choose two.)
What would allow a security team to inspect TLS encapsulated traffic?
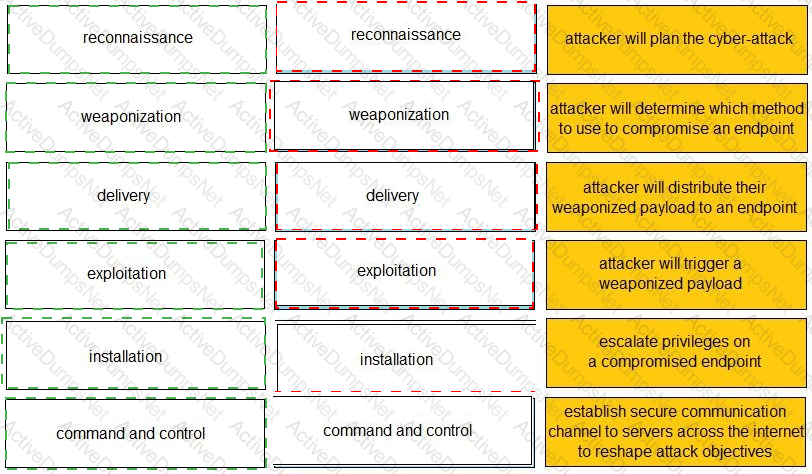
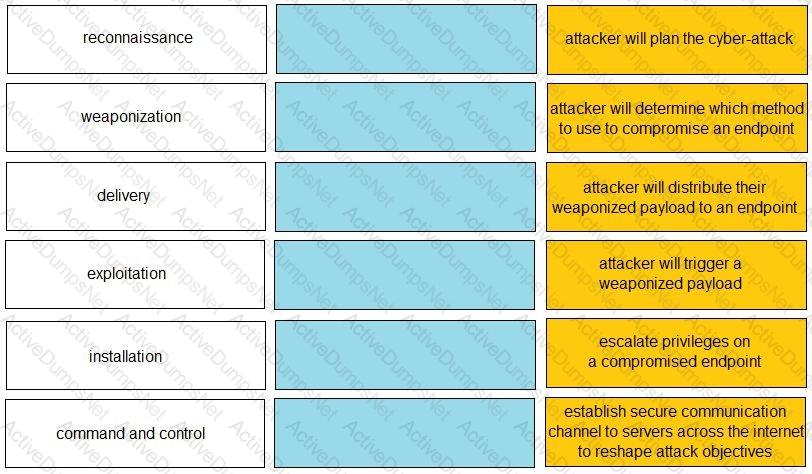
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

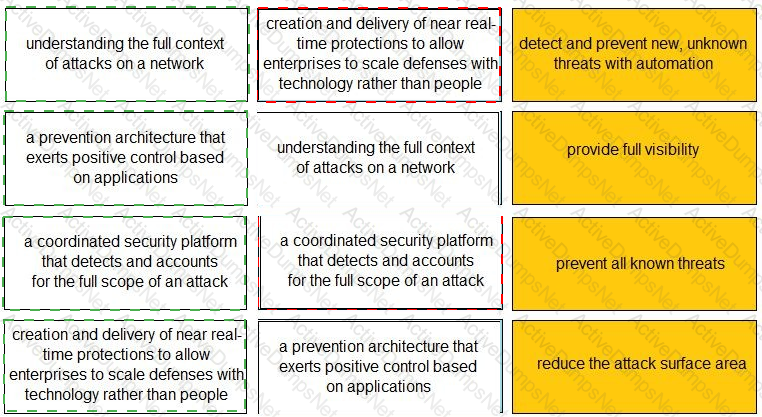
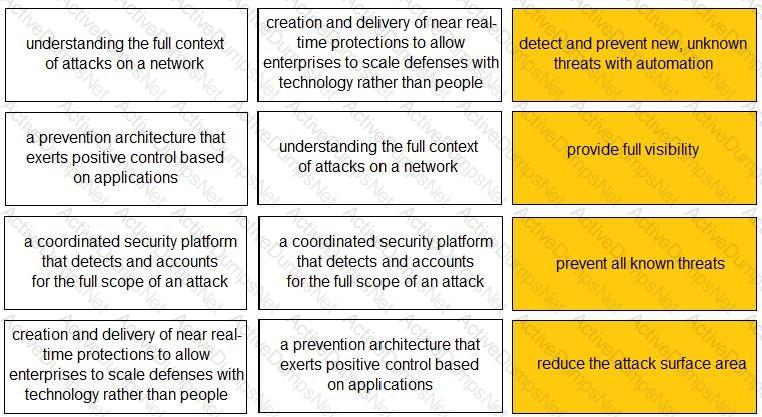
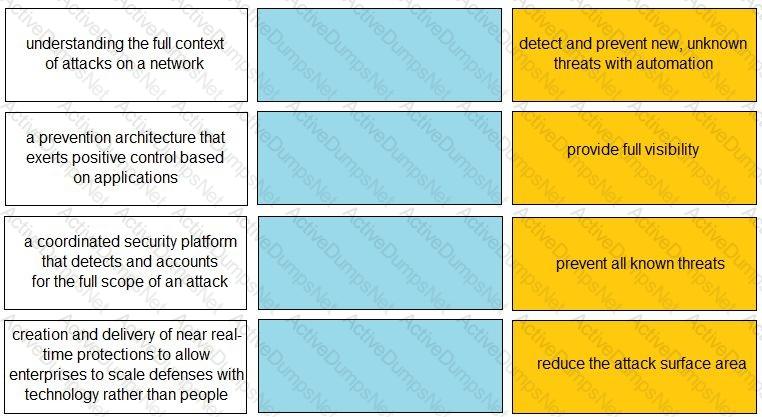
Match each description to a Security Operating Platform key capability.
Which two services does a managed detection and response (MDR) solution provide? (Choose two.)
Which characteristic of serverless computing enables developers to quickly deploy application code?
Which tool's analysis data gives security operations teams insight into their environment's risks from exposed services?
What differentiates Docker from a bare metal hypervisor?
Which endpoint tool or agent can enact behavior-based protection?
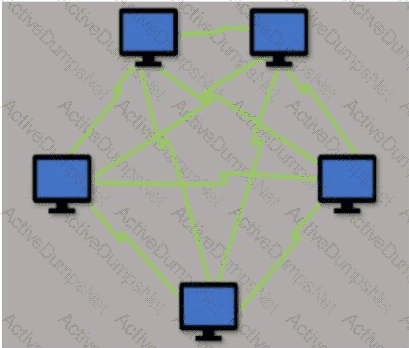
Which type of LAN technology is being displayed in the diagram?
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
Which model would a customer choose if they want full control over the operating system(s) running on their cloud computing platform?
Which statement is true about advanced persistent threats?
Which security function enables a firewall to validate the operating system version of a device before granting it network access?
Which type of Wi-Fi attack depends on the victim initiating the connection?
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
Which type of malware takes advantage of a vulnerability on an endpoint or server?
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
Why is it important to protect East-West traffic within a private cloud?
Which MITRE ATT&CK tactic grants increased permissions to a user account for internal servers of a corporate network?
Web 2.0 applications provide which type of service?
On which security principle does virtualization have positive effects?
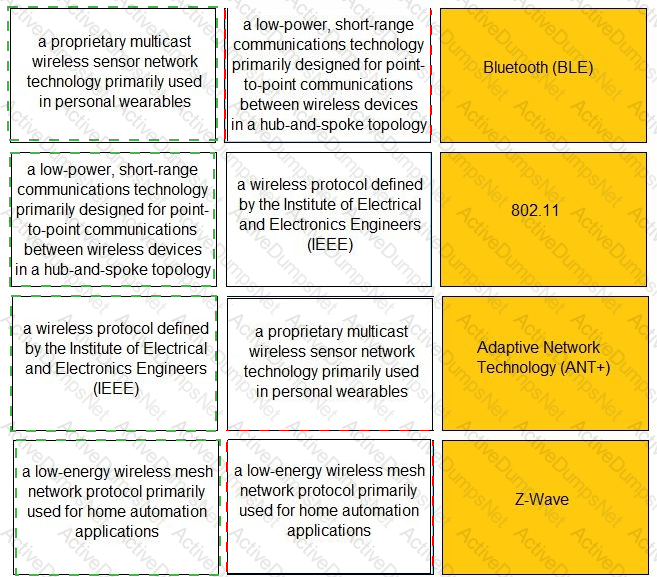
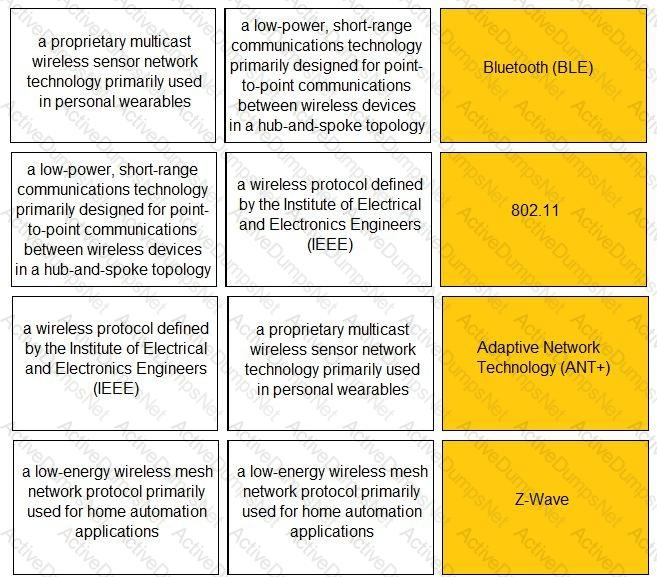
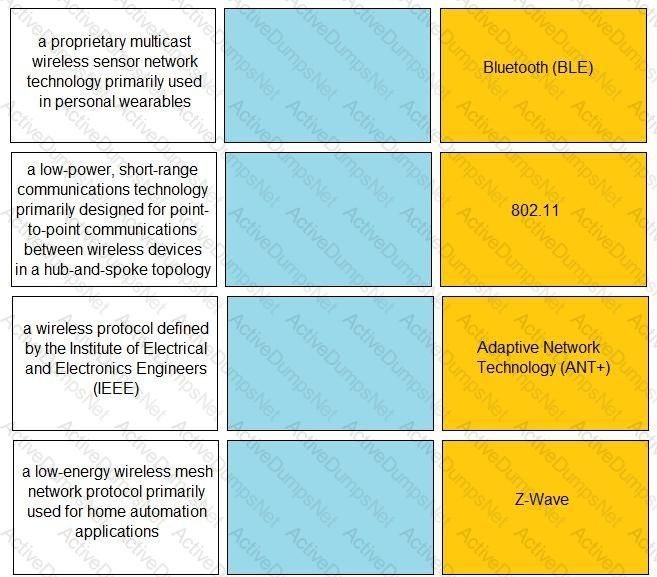
Match the IoT connectivity description with the technology.
Which method is used to exploit vulnerabilities, services, and applications?
What is an advantage of virtual firewalls over physical firewalls for internal segmentation when placed in a data center?
If an endpoint does not know how to reach its destination, what path will it take to get there?
An Administrator wants to maximize the use of a network address. The network is 192.168.6.0/24 and there are three subnets that need to be created that can not overlap. Which subnet would you use for the network with 120 hosts?
Requirements for the three subnets: Subnet 1: 3 host addresses
Subnet 2: 25 host addresses
Subnet 3: 120 host addresses
The customer is responsible only for which type of security when using a SaaS application?
What does SIEM stand for?
Which statement describes advanced malware?
What type of area network connects end-user devices?
Which activities do local organization security policies cover for a SaaS application?
Which two statements apply to the SSL/TLS protocol? (Choose two.)
What are three benefits of the cloud native security platform? (Choose three.)
What are two examples of an attacker using social engineering? (Choose two.)
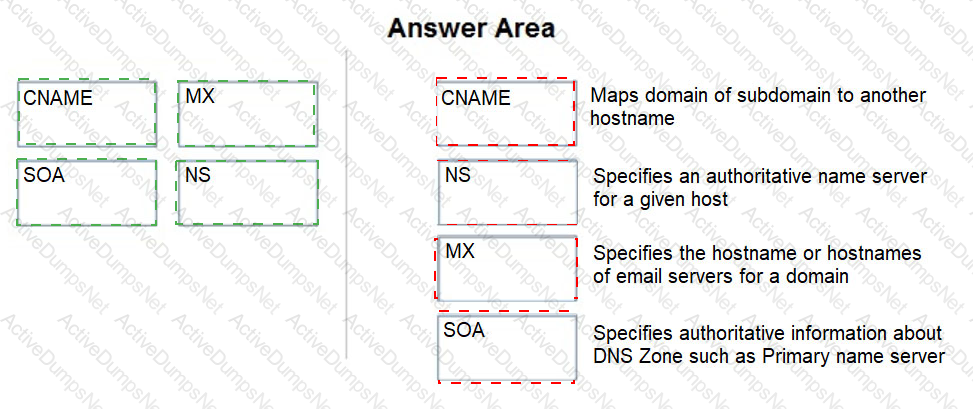
Match the DNS record type to its function within DNS.

Which statement describes DevOps?
Which architecture model uses virtual machines (VMs) in a public cloud environment?
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
Which term describes data packets that move in and out of the virtualized environment from the host network or a corresponding traditional data center?
Which capability does Cloud Security Posture Management (CSPM) provide for threat detection within Prisma Cloud?
Which statement describes a host-based intrusion prevention system (HIPS)?
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
At which layer of the OSI model are routing protocols defined?
What is the purpose of SIEM?
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
Which security tool provides policy enforcement for mobile users and remote networks?
Which technology grants enhanced visibility and threat prevention locally on a device?
Which two processes are critical to a security information and event management (SIEM) platform? (Choose two.)
What is the ptrpose of automation in SOAR?
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
How does Cortex XSOAR Threat Intelligence Management (TIM) provide relevant threat data to analysts?
Which IoT connectivity technology is provided by satellites?
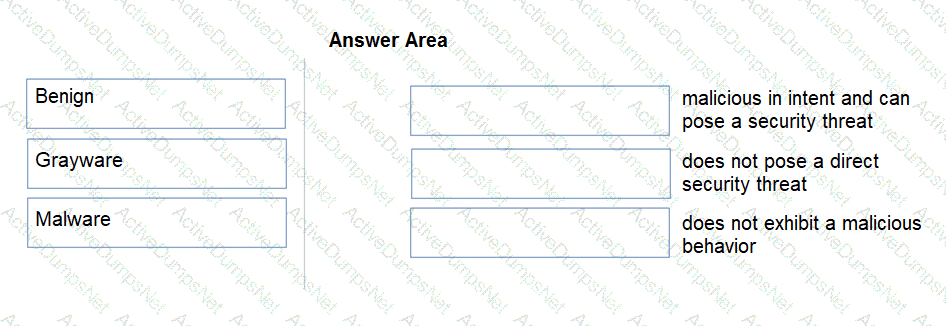
Match the Palo Alto Networks WildFire analysis verdict with its definition.
Which two statements apply to SaaS financial botnets? (Choose two.)
In which type of Wi-Fi attack does the attacker intercept and redirect the victim’s web traffic to serve content from a web server it controls?
You have been invited to a public cloud design and architecture session to help deliver secure east west flows and secure Kubernetes workloads.
What deployment options do you have available? (Choose two.)
Which two statements describe the Jasager attack? (Choose two.)
What role do containers play in cloud migration and application management strategies?
What is an event-driven snippet of code that runs on managed infrastructure?
Which methodology does Identity Threat Detection and Response (ITDR) use?
What is a key method used to secure sensitive data in Software-as-a-Service (SaaS) applications?
Which component of cloud security uses automated testing with static application security testing (SAST) to identify potential threats?
Which core component is used to implement a Zero Trust architecture?