Paloalto Networks PCNSE Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0 Exam Practice Test
Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 11.0 Questions and Answers
A security engineer is informed that the vulnerability protection profile of their on-premises Palo Alto Networks firewall is triggering on a common Threat ID, and which has been determined to be a false positive. The engineer is asked to resolve the issue as soon as possible because it is causing an outage for a critical service The engineer opens the vulnerability protection profile to add the exception, but the Threat ID is missing.
Which action is the most operationally efficient for the security engineer to find and implement the exception?
Which protocol is supported by Global Protect clientless VPN
Which protocol is supported by GlobalProtect Clientless VPN?
How is Perfect Forward Secrecy (PFS) enabled when troubleshooting a VPN Phase 2 mismatch?
Which operation will impact the performance of the management plane?
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed.
Which set of actions should the engineer take to achieve this goal?
Which translated port number should be used when configuring a NAT rule for a transparent proxy?
Users have reported an issue when they are trying to access a server on your network. The requests aren’t taking the expected route. You discover that there are two different static routes on the firewall for the server. What is used to determine which route has priority?
An administrator notices that an interface configuration has been overridden locally on a firewall. They require all configuration to be managed from Panorama and overrides are not allowed.
What is one way the administrator can meet this requirement?
When backing up and saving configuration files, what is achieved using only the firewall and is not available in Panorama?
How can a firewall engineer bypass App-ID and content inspection features on a Palo Alto Networks firewall when troubleshooting?
An engineer is reviewing policies after a PAN-OS upgrade What are the two differences between Highlight Unused Rules and the Rule Usage Hit counters immediately after a reboot?
Which two policy components are required to block traffic in real time using a dynamic user group (DUG)? (Choose two.)
An enterprise network security team is deploying VM-Series firewalls in a multi-cloud environment. Some firewalls are deployed in VMware NSX-V, while others are in AWS, and all are centrally managed using Panorama with the appropriate plugins installed. The team wants to streamline policy management by organizing the firewalls into device groups in which the AWS-based firewalls act as a parent device group, while the NSX-V firewalls are configured as a child device group to inherit Security policies. However, after configuring the device group hierarchy and attempting to push configurations, the team receives errors, and policy inheritance is not functioning as expected. What is the most likely cause of this issue?
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
Which two methods can be configured to validate the revocation status of a certificate? (Choose two.)
Phase two of a VPN will not establish a connection. The peer is using a policy-based VPN configuration.
What part of the configuration should the engineer verify?
A threat intelligence team has requested more than a dozen Short signatures to be deployed on all perimeter Palo Alto Networks firewalls. How does the firewall engineer fulfill this request with the least time to implement?
A firewall administrator has confirm reports of a website is not displaying as expected, and wants to ensure that decryption is not causing the issue. Which three methods can the administrator use to determine if decryption is causing the website to fail? (Choose three.)
Exhibit.
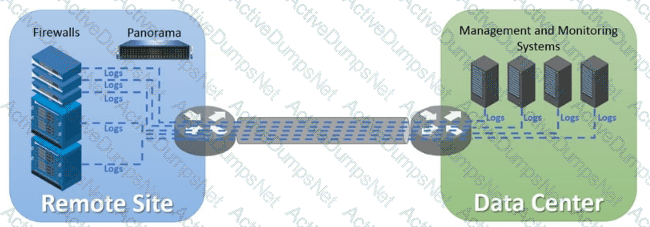
An organization has Palo Alto Networks NGFWs that send logs to remote monitoring and security management platforms The network team has reported excessive traffic on the corporate WAN How could the Palo Alto Networks NGFW administrator reduce WAN traffic while maintaining support for all the existing monitoring/security platforms?
When using certificate authentication for firewall administration, which method is used for authorization?
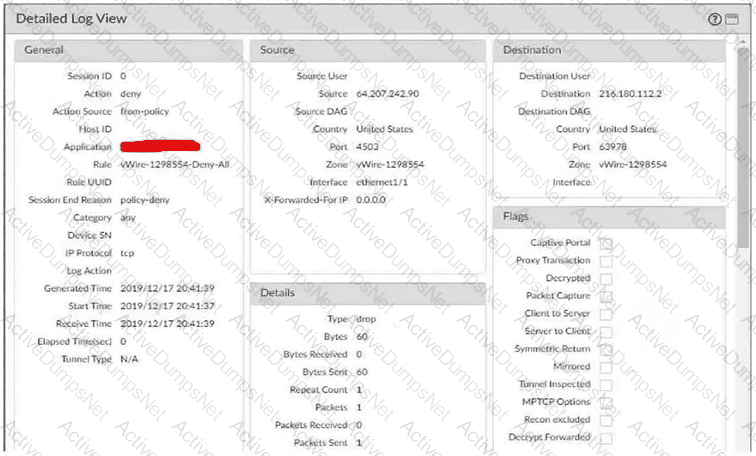
Exhibit.
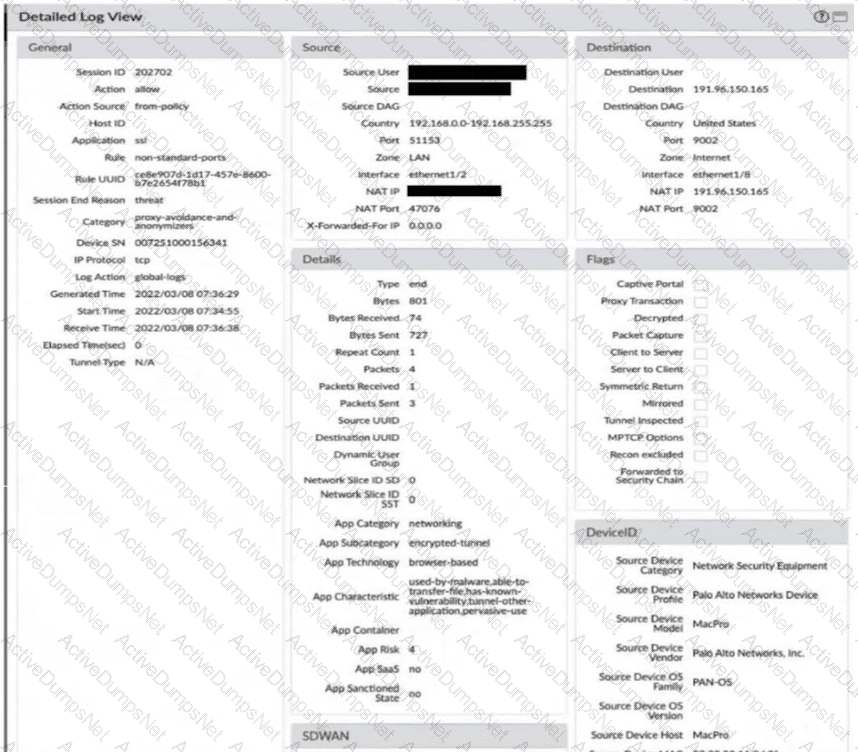
Given the screenshot, how did the firewall handle the traffic?
Which statement explains the difference between using the PAN-OS integrated User-ID agent and the standalone User-ID agent when using Active Directory for user-to-IP mapping?
Refer to Exhibit:
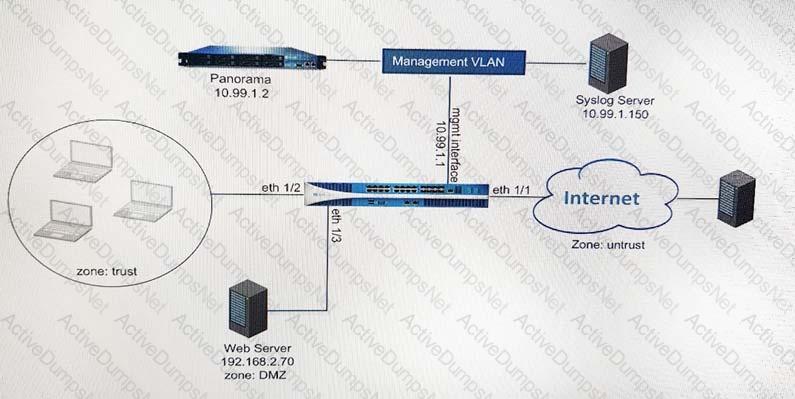
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
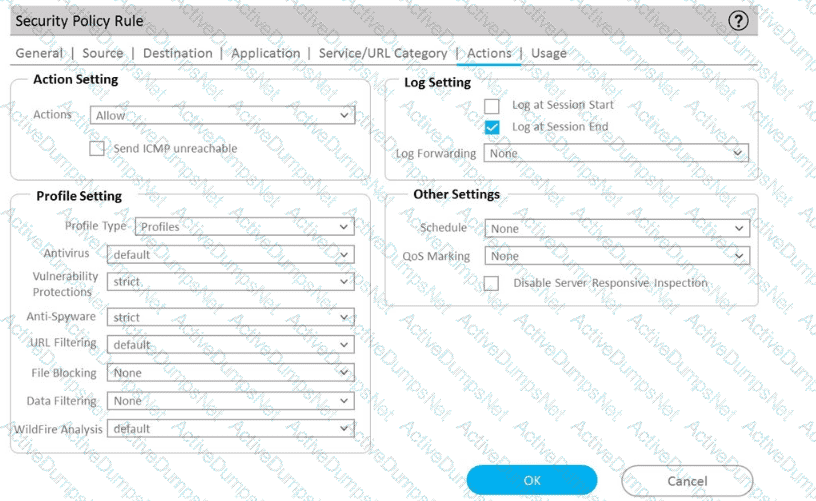
B)
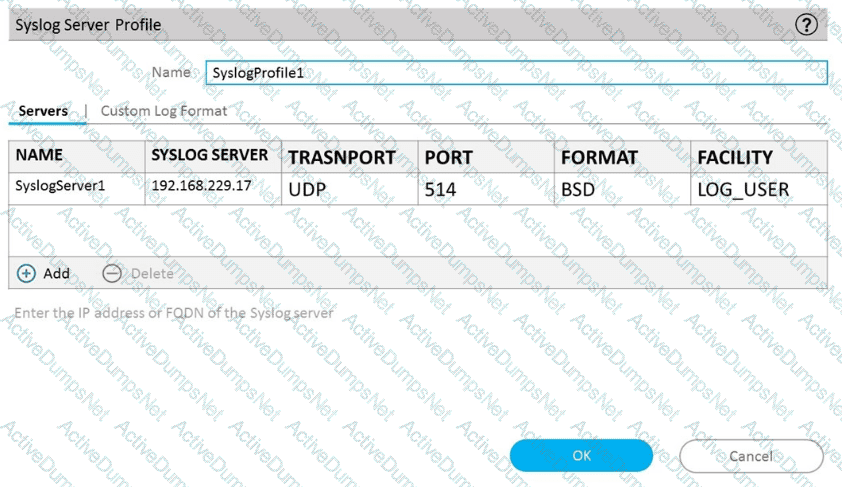
C)
D)
A system administrator runs a port scan using the company tool as part of vulnerability check. The administrator finds that the scan is identified as a threat and is dropped by the firewall. After further investigating the logs, the administrator finds that the scan is dropped in the Threat Logs.
An engineer needs to permit XML API access to a firewall for automation on a network segment that is routed through a Layer 3 sub-interface on a Palo Alto Networks firewall. However, this network segment cannot access the dedicated management interface due to the Security policy.
Without changing the existing access to the management interface, how can the engineer fulfill this request?
What is the best description of the Cluster Synchronization Timeout (min)?
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?
Which action can be taken to immediately remediate the issue of application traffic with a valid use case triggering the decryption log message, "Received fatal alert UnknownCA from client"?
An administrator connects a new fiber cable and transceiver Ethernet1/1 on a Palo Alto Networks firewall. However, the link does not come up. How can the administrator troubleshoot to confirm the transceiver type, tx-power, rxpower, vendor name, and part number by using the CLI?
An administrator Just enabled HA Heartbeat Backup on two devices However, the status on tie firewall's dashboard is showing as down High Availability.
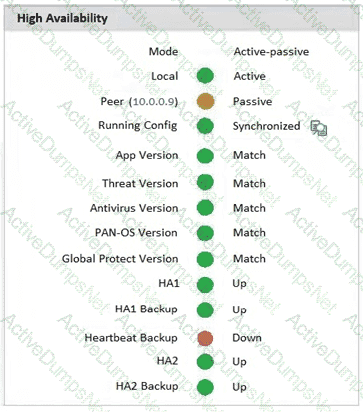
What could an administrator do to troubleshoot the issue?
Which three multi-factor authentication methods can be used to authenticate access to the firewall? (Choose three.)
The firewall team has been asked to deploy a new Panorama server and to forward all firewall logs to this server By default, which component of the Palo Alto Networks firewall architect is responsible for log forwarding and should be checked for early signs of overutilization?
Which three statements accurately describe Decryption Mirror? (Choose three.)
An administrator plans to install the Windows-Based User-ID Agent to prevent credential phishing.
Which installer package file should the administrator download from the support site?
An administrator is troubleshooting application traffic that has a valid business use case, and observes the following decryption log message: "Received fatal alert UnknownCA from client."
How should the administrator remediate this issue?
A firewall engineer creates a NAT rule to translate IP address 1.1.1.10 to 192.168.1.10. The engineer also plans to enable DNS rewrite so that the firewall rewrites the IPv4 address in a DNS response based on the original destination IP address and translated destination IP address configured for the rule. The engineer wants the firewall to rewrite a DNS response of 1.1.1.10 to 192.168.1.10.
What should the engineer do to complete the configuration?
An organization uses the User-ID agent to control access to sensitive internal resources. A firewall engineer adds Security policies to ensure only User A has access to a specific resource. User A was able to access the resource without issue before the updated policies, but now is having intermittent connectivity issues. What is the most likely resolution to this issue?
Which two virtualization platforms officially support the deployment of Palo Alto Networks VM-Series firewalls? (Choose two.)
If an administrator wants to apply QoS to traffic based on source, what must be specified in a QoS policy rule?
A firewall administrator wants to be able at to see all NAT sessions that are going ‘through a firewall with source NAT. Which CLI command can the administrator use?
An administrator has configured OSPF with Advanced Routing enabled on a Palo Alto Networks firewall running PAN-OS 10.2. After OSPF was configured, the administrator noticed that OSPF routes were not being learned.
Which two actions could an administrator take to troubleshoot this issue? (Choose two.)
A network security administrator has an environment with multiple forms of authentication. There is a network access control system in place that authenticates and restricts access for wireless users, multiple Windows domain controllers, and an MDM solution for company-provided smartphones. All of these devices have their authentication events logged.
Given the information, what is the best choice for deploying User-ID to ensure maximum coverage?
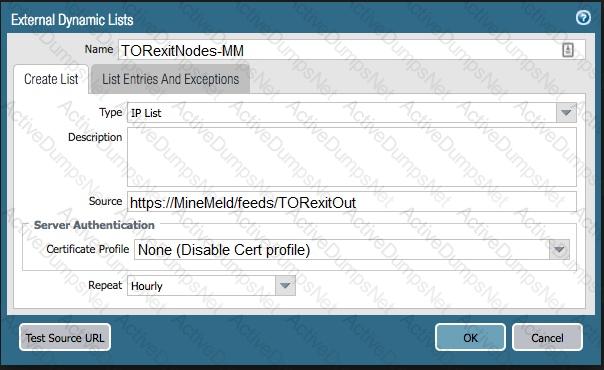
The firewall is not downloading IP addresses from MineMeld. Based, on the image, what most likely is wrong?
An engineer creates a set of rules in a Device Group (Panorama) to permit traffic to various services for a specific LDAP user group.
What needs to be configured to ensure Panorama can retrieve user and group information for use in these rules?
Why are external zones required to be configured on a Palo Alto Networks NGFW in an environment with multiple virtual systems?
An administrator encountered problems with inbound decryption. Which option should the administrator investigate as part of triage?
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an interal syslog server. Where can the firewall engineer define the data to be added into each forwarded log?
What can be used as an Action when creating a Policy-Based Forwarding (PBF) policy?
Which Panorama feature protects logs against data loss if a Panorama server fails?
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
Which three items must be configured to implement application override? (Choose three )
Which log type is supported in the Log Forwarding profile?
Where is Palo Alto Networks Device Telemetry data stored on a firewall with a device certificate installed?
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
Refer to the exhibit.
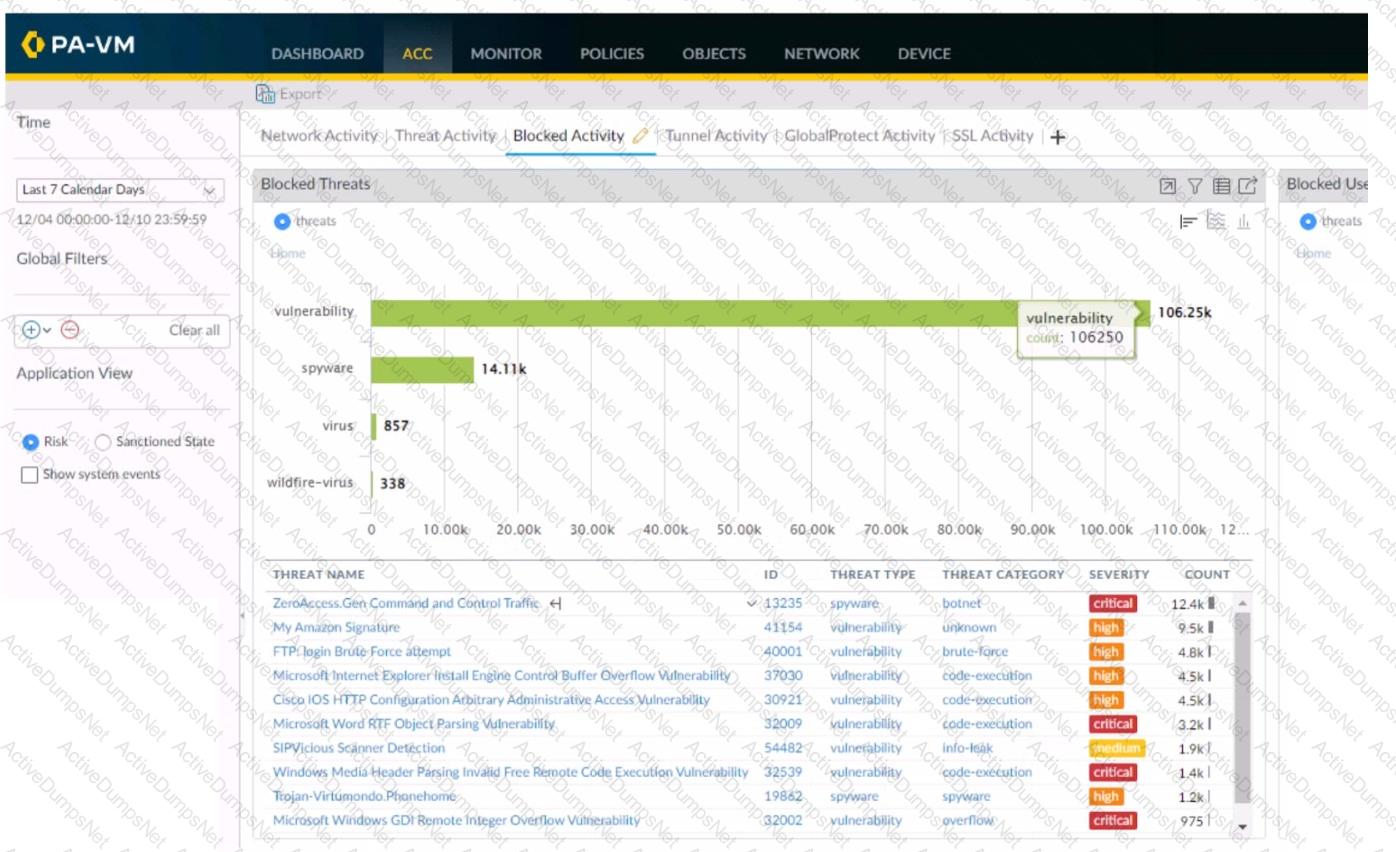
Using the above screenshot of the ACC, what is the best method to set a global filter, narrow down Blocked User Activity, and locate the user(s) that could be compromised by a botnet?
Four configuration choices are listed, and each could be used to block access to a specific URL.
If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
A firewall engineer is managing a Palo Alto Networks NGFW that does not have the DHCP server on DHCP agent configuration. Which interface mode can the broadcast DHCP traffic?
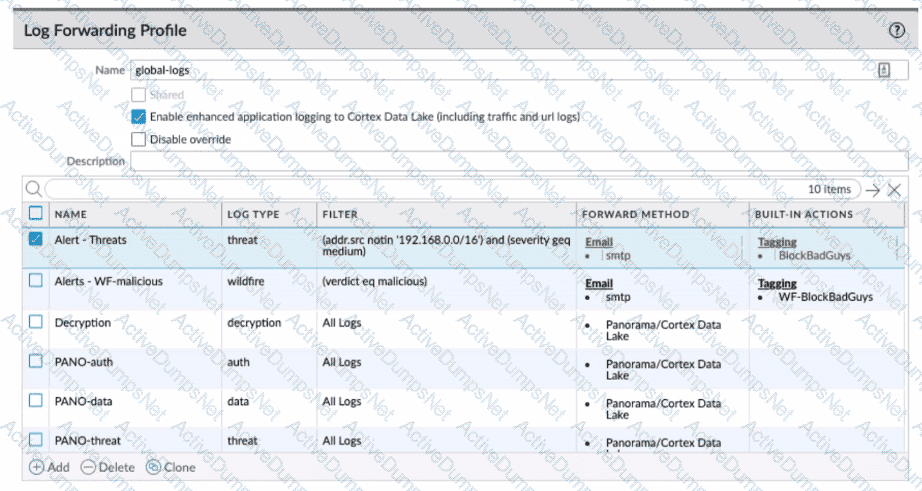
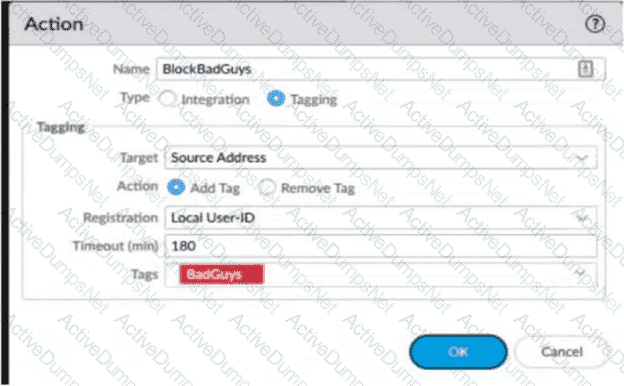
Review the images. A firewall policy that permits web traffic includes the global-logs policy is depicted
What is the result of traffic that matches the "Alert - Threats" Profile Match List?
Which statement about High Availability timer settings is true?
An administrator pushes a new configuration from Panorama to a pair of firewalls that are configured as an active/passive HA pair. Which NGFW receives the configuration from Panorama?
For company compliance purposes, three new contractors will be working with different device groups in their hierarchy to deploy policies and objects. Which type of role-based access is most appropriate for this project?
An administrator is troubleshooting intermittent connectivity problems with a user's GlobalProtect connection. Packet captures at the firewall reveal missing UDP packets, suggesting potential packet loss on the connection. The administrator aims to resolve the issue by enforcing an SSL tunnel over TCP specifically for this user.
What configuration change is necessary to implement this troubleshooting solution for the user?
An engineer decides to use Panorama to upgrade devices to PAN-OS 10.2.
Which three platforms support PAN-OS 10.2? (Choose three.)
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
A security engineer wants to upgrade the company's deployed firewalls from PAN-OS 10.1 to 11.0.x to take advantage of the new TLSvl.3 support for management access.
What is the recommended upgrade path procedure from PAN-OS 10.1 to 11.0.x?
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
An engineer is deploying multiple firewalls with common configuration in Panorama.
What are two benefits of using nested device groups? (Choose two.)
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow. Upon opening the newly created packet capture, the administrator still sees traffic for the previous filter.
What can the administrator do to limit the captured traffic to the newly configured filter?
If a template stack is assigned to a device and the stack includes three templates with overlapping settings, which settings are published to the device when the template stack is pushed?
An administrator has been asked to configure active/active HA for a pair of Palo Alto Networks NGFWs. The firewall use Layer 3 interfaces to send traffic to a single gateway IP for the pair.
Which configuration will enable this HA scenario?
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What should the enterprise do to use PAN-OS MFA?
A firewall administrator needs to check which egress interface the firewall will use to route the IP 10.2.5.3.
Which command should they use?
While troubleshooting an issue, a firewall administrator performs a packet capture with a specific filter. The administrator sees drops for packets with a source IP address of 10.1.1.1.
How can the administrator further investigate these packet drops by looking at the global counters for this packet capture filter?
Which feature can provide NGFWs with User-ID mapping information?
An administrator configures a site-to-site IPsec VPN tunnel between a PA-850 and an external customer on their policy-based VPN devices.
What should an administrator configure to route interesting traffic through the VPN tunnel?
A root cause analysis investigation into a recent security incident reveals that several decryption rules have been disabled. The security team wants to generate email alerts when decryption rules are changed.
How should email log forwarding be configured to achieve this goal?
Which administrative authentication method supports authorization by an external service?
A company wants to add threat prevention to the network without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel The administrator determines that the lifetime needs to be changed to match the peer. Where should this change be made?
An engineer is configuring a Protection profile to defend specific endpoints and resources against malicious activity.
The profile is configured to provide granular defense against targeted flood attacks for specific critical systems that are accessed by users from the internet.
Which profile is the engineer configuring?
Which GloDalProtecI gateway setting is required to enable split-tunneting by access route, destination domain and application?
An engineer configures SSL decryption in order to have more visibility to the internal users' traffic when it is regressing the firewall.
Which three types of interfaces support SSL Forward Proxy? (Choose three.)
An administrator has configured a pair of firewalls using high availability in Active/Passive mode. Link and Path Monitoring is enabled with the Failure Condition set to "any." There is one link group configured containing member interfaces ethernet1/1 and ethernet1/2 with a Group Failure Condition set to "all."
Which HA state will the Active firewall go into if ethernet1/1 link goes down due to a failure?'
An administrator is receiving complaints about application performance degradation. After checking the ACC, the administrator observes that there is an excessive amount of VoIP traffic.
Which three elements should the administrator configure to address this issue? (Choose three.)
Which link is responsible for synchronizing sessions between high availability (HA) peers?
An engineer configures a new template stack for a firewall that needs to be deployed. The template stack should consist of four templates arranged according to the diagram

Which template values will be configured on the firewall If each template has an SSL/TLS Service profile configured named Management?
An administrator wants to add User-ID information for their Citrix MetaFrame Presentation Server (MPS) users.
Which option should the administrator use?
How does Panorama prompt VMWare NSX to quarantine an infected VM?
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
An auditor is evaluating the configuration of Panorama and notices a discrepancy between the Panorama template and the local firewall configuration. When overriding the firewall configuration pushed from Panorama, what should you consider?
Which two components are required to configure certificate-based authentication to the web UI when firewall access is needed on a trusted interface? (Choose two.)
An administrator is using Panorama to manage multiple firewalls. After upgrading all devices to the latest PAN-OS software, the administrator enables log forwarding from the firewalls to Panorama.
However, pre-existing logs from the firewalls are not appearing in Panorama.
Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
A consultant advises a client on designing an explicit Web Proxy deployment on PAN-OS 11 0 The client currently uses RADIUS authentication in their environment
Which two pieces of information should the consultant provide regarding Web Proxy authentication? (Choose two.)
Which two actions would be part of an automatic solution that would block sites with untrusted certificates without enabling SSL Forward Proxy? (Choose two.)
To connect the Palo Alto Networks firewall to AutoFocus, which setting must be enabled?
‘SSL Forward Proxy decryption is configured, but the firewall uses Untrusted-CA to sign the website https://www important-website com certificate, End-users are receiving the "security certificate is no: trusted” warning, Without SSL decryption, the web browser shows chat the website certificate is trusted and signet by well-known certificate chain Well-Known-intermediate and Wako Hebe CA Security administrator who represents the customer requires the following two behaviors when SSL Forward Proxy is enabled:
1. End-users must not get the warning for the https:///www.very-import-website.com/ website.
2. End-users should get the warning for any other untrusted website.
Which approach meets the two customer requirements?
What are three prerequisites to enable Credential Phishing Prevention over SSL? (Choose three
A network engineer has discovered that asymmetric routing is causing a Palo Alto Networks firewall to drop traffic. The network architecture cannot be changed to correct this.
Which two actions can be taken on the firewall to allow the dropped traffic permanently? (Choose two.)
An administrator wants to use LDAP, TACACS+, and Kerberos as external authentication services for authenticating users. What should the administrator be aware of regarding the authentication sequence, based on the Authentication profile in the order Kerberos LDAP, and TACACS+?
After switching to a different WAN connection, users have reported that various websites will not load, and timeouts are occurring. The web servers work fine from other locations.
The firewall engineer discovers that some return traffic from these web servers is not reaching the users behind the firewall. The engineer later concludes that the maximum transmission unit (MTU) on an upstream router interface is set to 1400 bytes.
The engineer reviews the following CLI output for ethernet1/1.
Which setting should be modified on ethernet1/1 to remedy this problem?
What does SSL decryption require to establish a firewall as a trusted third party and to establish trust between a client and server to secure an SSL/TLS connection'?
An administrator has two pairs of firewalls within the same subnet. Both pairs of firewalls have been configured to use High Availability mode with Active/Passive. The ARP tables for upstream routes display the same MAC address being shared for some of these firewalls.
What can be configured on one pair of firewalls to modify the MAC addresses so they are no longer in conflict?
A firewall engineer is configuring quality of service (OoS) policy for the IP address of a specific server in an effort to limit the bandwidth consumed by frequent downloads of large files from the internet.
Which combination of pre-NAT and / or post-NAT information should be used in the QoS rule?
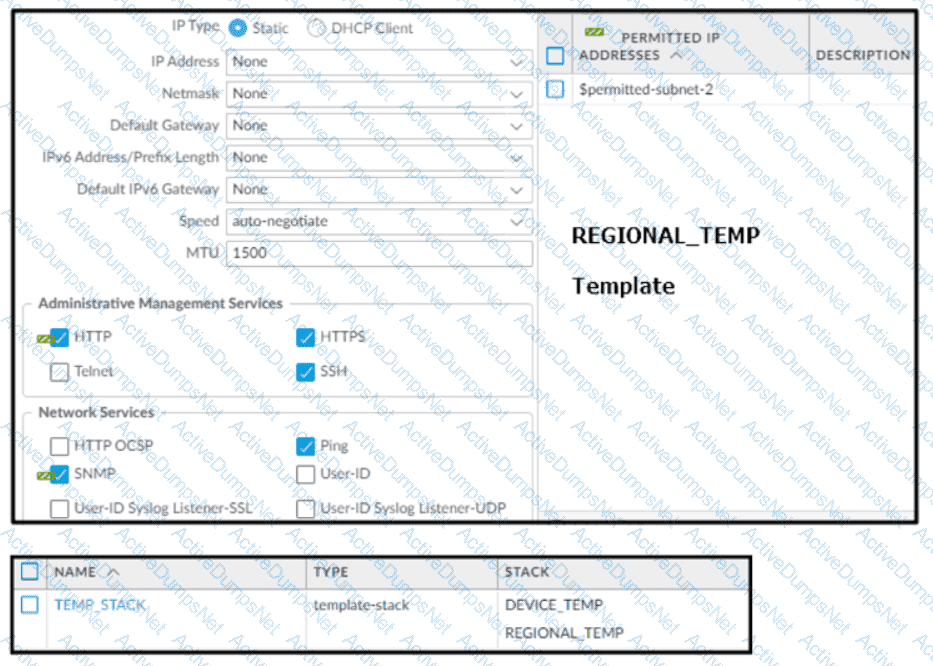
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
What is the purpose of the firewall decryption broker?
An engineer has been asked to limit which routes are shared by running two different areas within an OSPF implementation. However, the devices share a common link for communication. Which virtual router configuration supports running multiple instances of the OSPF protocol over a single link?
An administrator configures HA on a customer's Palo Alto Networks firewalls with path monitoring by using the default configuration values.
What are the default values for ping interval and ping count before a failover is triggered?
An internal audit team has requested additional information to be included inside traffic logs forwarded from Palo Alto Networks firewalls to an internal syslog server.
Where can the firewall engineer define the data to be added into each forwarded log?
A firewall engineer reviews the PAN-OS GlobalProtect application and sees that it implicitly uses web-browsing and depends on SSL.
When creating a new rule, what is needed to allow the application to resolve dependencies?
