Paloalto Networks PCNSA Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0) Exam Practice Test
Palo Alto Networks Certified Network Security Administrator (PAN-OS 10.0) Questions and Answers
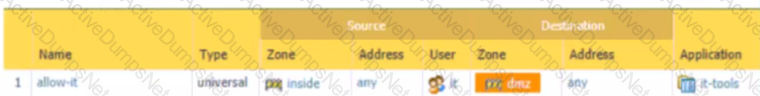
Based on the screenshot what is the purpose of the group in User labelled ''it"?
What are three valid source or D=destination conditions available as Security policy qualifiers? (Choose three.)
Which System log severity level would be displayed as a result of a user password change?
What is used to monitor Security policy applications and usage?
The PowerBall Lottery has reached an unusually high value this week. Your company has decided to raise morale by allowing employees to access the PowerBall Lottery website (www.powerball.com) for just this week. However, the company does not want employees to access any other websites also listed in the URL filtering “gambling” category.
Which method allows the employees to access the PowerBall Lottery website but without unblocking access to the “gambling” URL category?
What is considered best practice with regards to committing configuration changes?
Which security profile will provide the best protection against ICMP floods, based on individual combinations of a packet`s source and destination IP address?
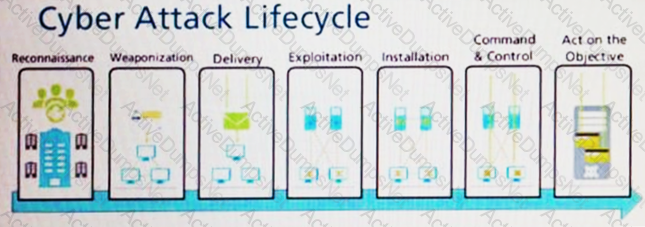
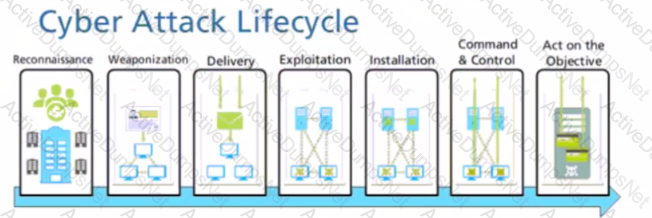
Which stage of the cyber-attack lifecycle makes it important to provide ongoing education to users on spear phishing links, unknown emails, and risky websites?
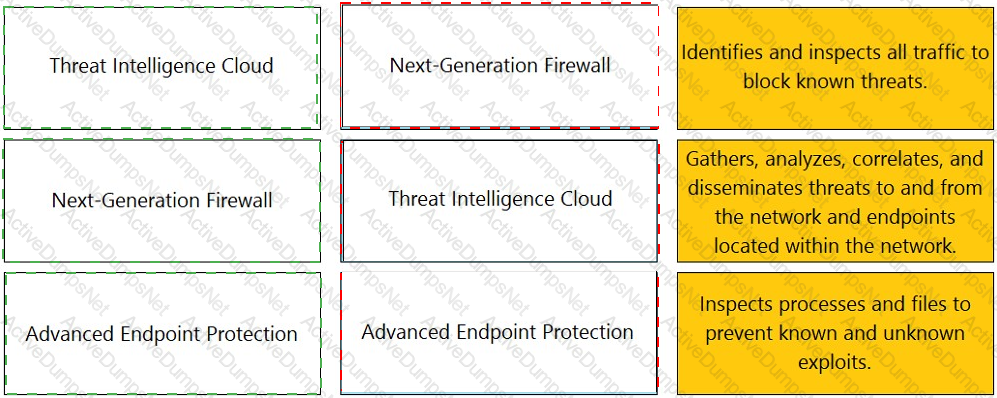
Which service protects cloud-based applications such as Dropbox and Salesforce by administering permissions and scanning files for sensitive information?
What must be considered with regards to content updates deployed from Panorama?
Which Palo Alto Networks firewall security platform provides network security for mobile endpoints by inspecting traffic deployed as internet gateways?
An address object of type IP Wildcard Mask can be referenced in which part of the configuration?
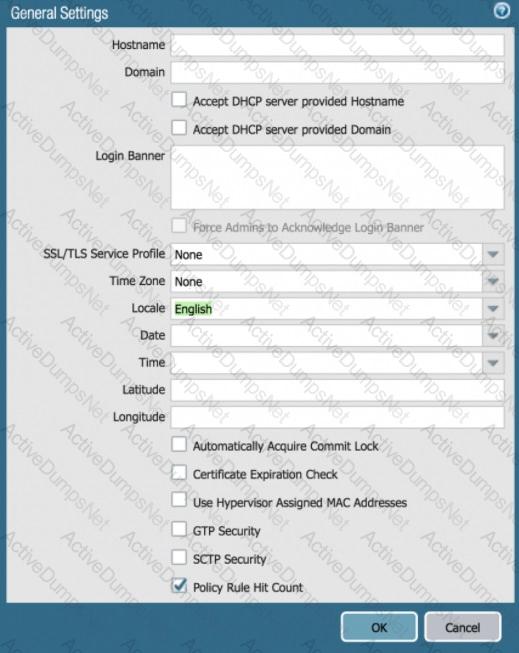
Based on the graphic, what is the purpose of the SSL/TLS Service profile configuration option?
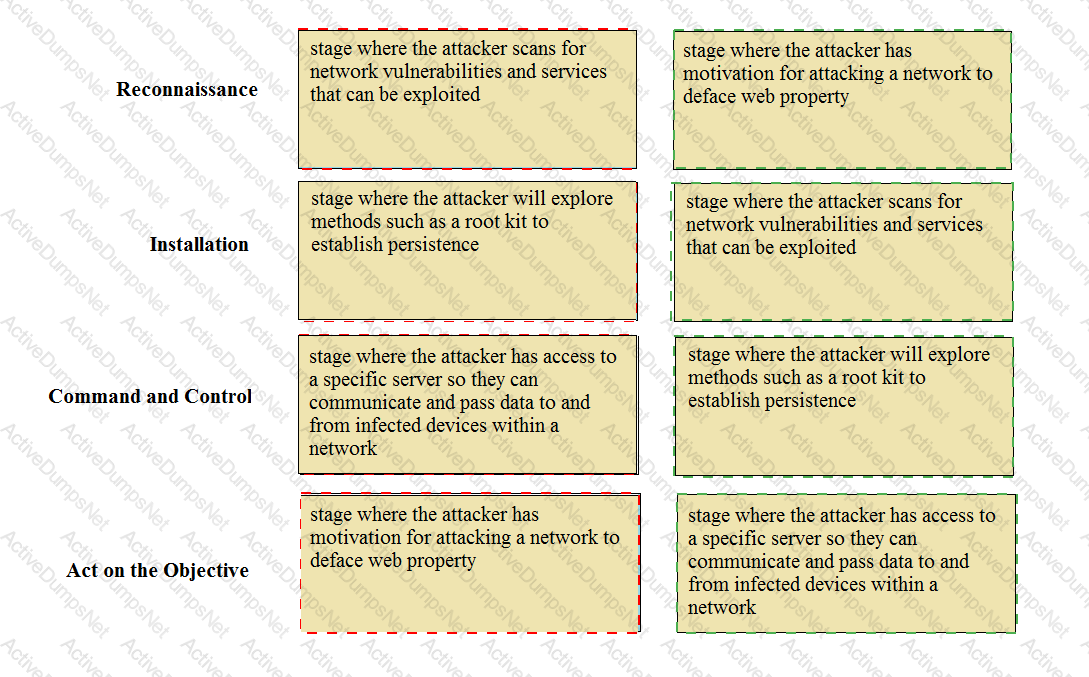
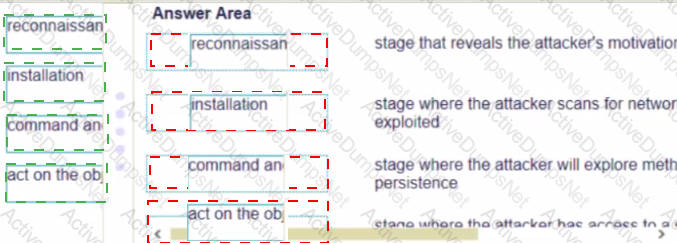
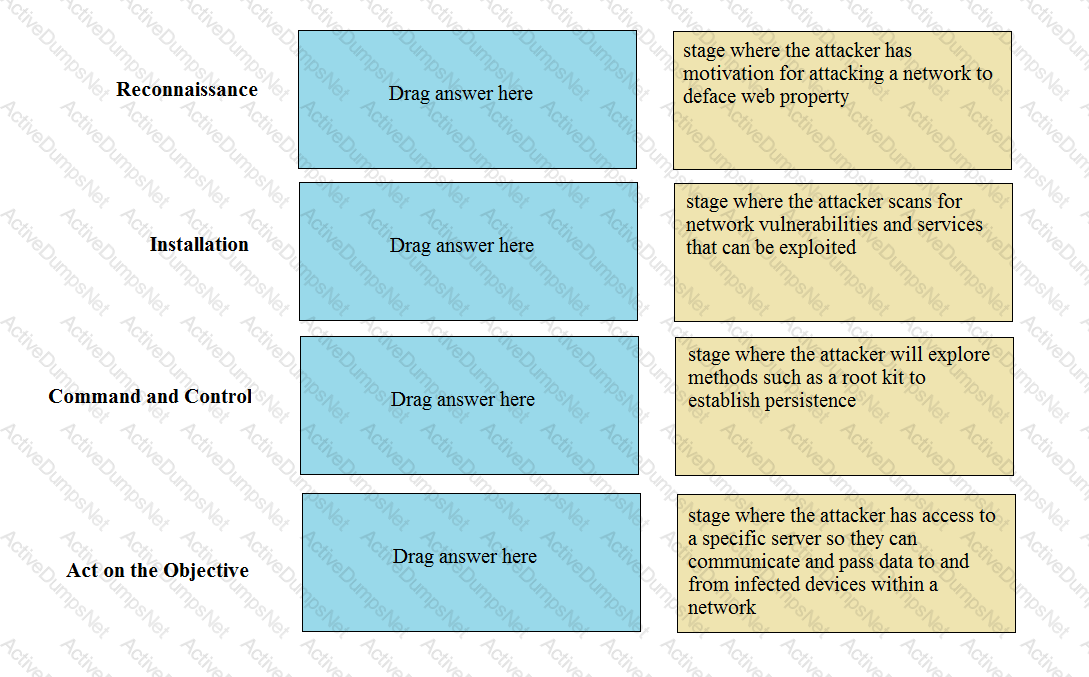
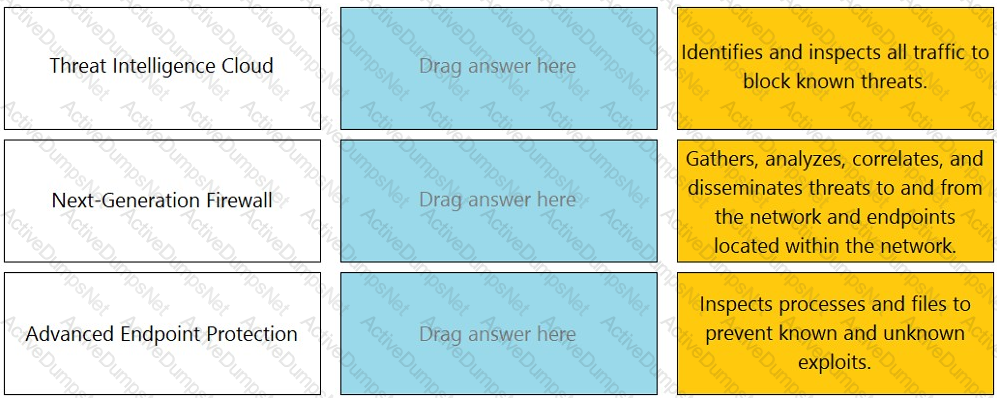
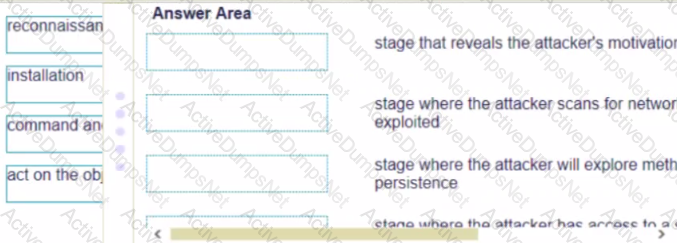
Match the Cyber-Attack Lifecycle stage to its correct description.
Which user mapping method could be used to discover user IDs in an environment with multiple Windows domain controllers?
Which type of security rule will match traffic between the Inside zone and Outside zone, within the Inside zone, and within the Outside zone?
Based on the show security policy rule would match all FTP traffic from the inside zone to the outside zone?
What are three characteristics of the Palo Alto Networks DNS Security service? (Choose three.)
Palo Alto Networks firewall architecture accelerates content map minimizing latency using which two components'? (Choose two )
A systems administrator momentarily loses track of which is the test environment firewall and which is the production firewall. The administrator makes changes to the candidate configuration of the production firewall, but does not commit the changes. In addition, the configuration was not saved prior to
making the changes.
Which action will allow the administrator to undo the changes?
Access to which feature requires the PAN-OS Filtering license?
How do you reset the hit count on a security policy rule?
During the packet flow process, which two processes are performed in application identification? (Choose two.)
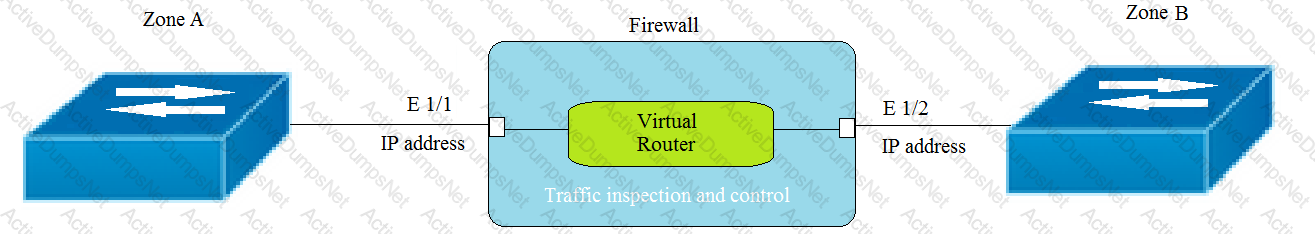
Given the topology, which zone type should zone A and zone B to be configured with?
Which Security profile can you apply to protect against malware such as worms and Trojans?
An administrator would like to silently drop traffic from the internet to a ftp server.
Which Security policy action should the administrator select?
Prior to a maintenance-window activity, the administrator would like to make a backup of only the running configuration to an external location.
What command in Device > Setup > Operations would provide the most operationally efficient way to achieve this outcome?
Which three statement describe the operation of Security Policy rules or Security Profiles? (Choose three)
What two authentication methods on the Palo Alto Networks firewalls support authentication and authorization for role-based access control? (Choose two.)
Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.
What is the quickest way to reset the hit counter to zero in all the security policy rules?
Which Security profile must be added to Security policies to enable DNS Signatures to be checked?
You receive notification about a new malware that infects hosts An infection results in the infected host attempting to contact a command-and-control server Which Security Profile when applied to outbound Security policy rules detects and prevents this threat from establishing a command-and-control connection?
An administrator is implementing an exception to an external dynamic list by adding an entry to the list manually. The administrator wants to save the changes, but the OK button is grayed out.
What are two possible reasons the OK button is grayed out? (Choose two.)
What is a default setting for NAT Translated Packets when the destination NAT translation is selected as Dynamic IP (with session distribution)?
Which Palo Alto network security operating platform component provides consolidated policy creation and centralized management?
A Security Profile can block or allow traffic at which point?
What is the minimum timeframe that can be set on the firewall to check for new WildFire signatures?
The PowerBall Lottery has reached a high payout amount and a company has decided to help employee morale by allowing employees to check the number, but doesn’t want to unblock the gambling URL category.
Which two methods will allow the employees to get to the PowerBall Lottery site without the company unlocking the gambling URL category? (Choose two.)
An administrator wishes to follow best practices for logging traffic that traverses the firewall
Which log setting is correct?
Which URL Filtering Profile action does not generate a log entry when a user attempts to access a URL?
How can a complete overview of the logs be displayed to an administrator who has permission in the system to view them?
Choose the option that correctly completes this statement. A Security Profile can block or allow traffic ____________.
Which two matching criteria are used when creating a Security policy involving NAT? (Choose two.)
What is a recommended consideration when deploying content updates to the firewall from Panorama?
How are service routes used in PAN-OS?
How is the hit count reset on a rule?
Given the screenshot what two types of route is the administrator configuring? (Choose two )
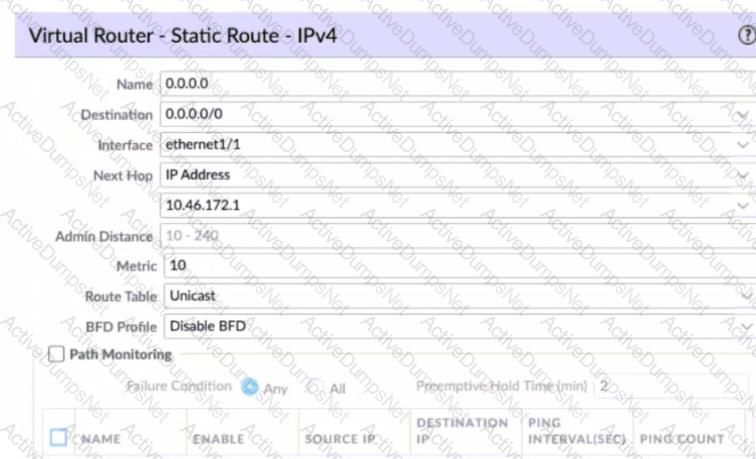
An administrator would like to determine the default deny action for the application dns-over-https
Which action would yield the information?
Which two features can be used to tag a username so that it is included in a dynamic user group? (Choose two.)
Which type firewall configuration contains in-progress configuration changes?
Which feature enables an administrator to review the Security policy rule base for unused rules?
Which two types of profiles are needed to create an authentication sequence? (Choose two.)
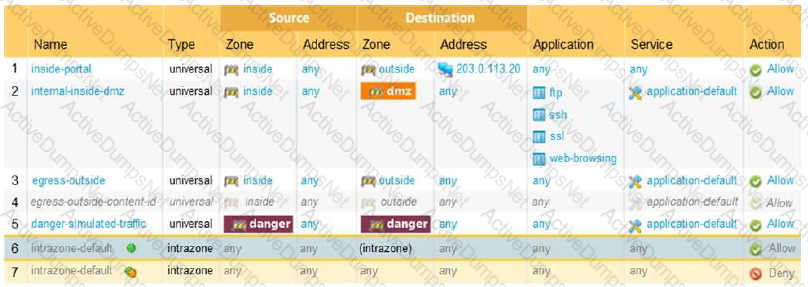
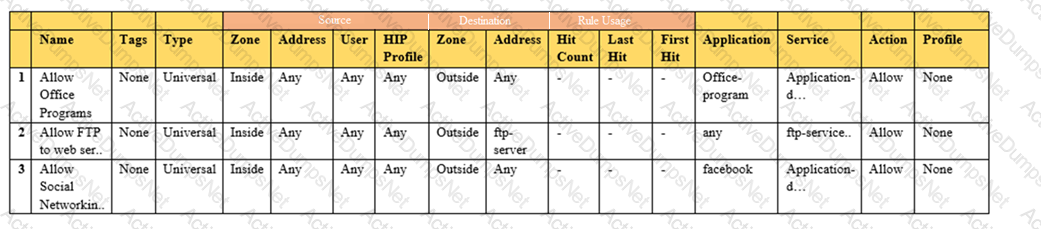
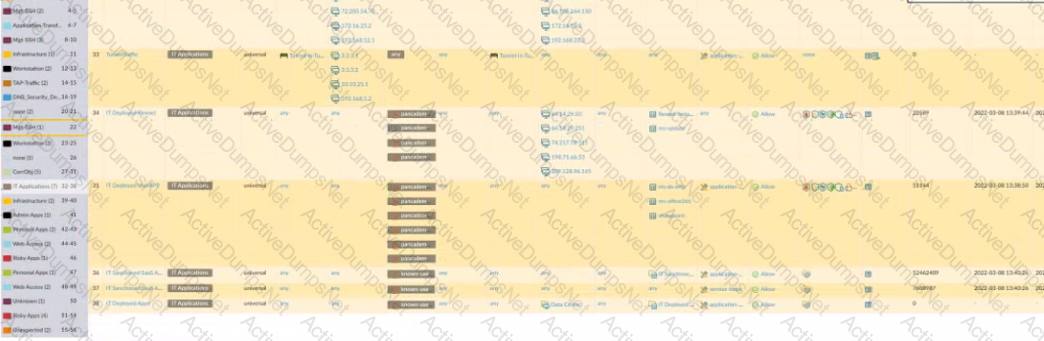
Given the image, which two options are true about the Security policy rules. (Choose two.)
Selecting the option to revert firewall changes will replace what settings?
Given the Cyber-Attack Lifecycle diagram, identify the stage in which the attacker can initiate malicious code against a targeted machine.
In which section of the PAN-OS GUI does an administrator configure URL Filtering profiles?
A security administrator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified by App-ID as SuperApp_base.
On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days.
Based on the information, how is the SuperApp traffic affected after the 30 days have passed?
A website is unexpectedly allowed due to miscategorization.
What are two way-s to resolve this issue for a proper response? (Choose two.)
An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment?
How frequently can wildfire updates be made available to firewalls?
In which stage of the Cyber-Attack Lifecycle would the attacker inject a PDF file within an email?
What must be configured before setting up Credential Phishing Prevention?
What are three valid information sources that can be used when tagging users to dynamic user groups? (Choose three.)
Match each feature to the DoS Protection Policy or the DoS Protection Profile.
Which two features can be used to tag a user name so that it is included in a dynamic user group? (Choose two)
By default, which action is assigned to the interzone-default rule?
An administrator is reviewing the Security policy rules shown in the screenshot below.
Which statement is correct about the information displayed?
An administrator configured a Security policy rule where the matching condition includes a single application and the action is set to deny. What deny action will the firewall perform?
Which component is a building block in a Security policy rule?
Which URL Filtering profile action would you set to allow users the option to access a site only if they provide a URL admin password?
What Policy Optimizer policy view differ from the Security policy do?
Given the cyber-attack lifecycle diagram identify the stage in which the attacker can run malicious code against a vulnerability in a targeted machine.
Which license is required to use the Palo Alto Networks built-in IP address EDLs?
Where in the PAN-OS GUI can an administrator monitor the rule usage for a specified period of time?
Which administrator type provides more granular options to determine what the administrator can view and modify when creating an administrator account?
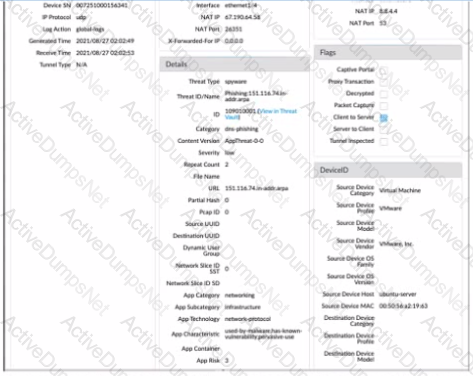
Given the detailed log information above, what was the result of the firewall traffic inspection?
The NetSec Manager asked to create a new firewall Local Administrator profile with customized privileges named NewAdmin. This new administrator has to authenticate without inserting any username or password to access the WebUI.
What steps should the administrator follow to create the New_Admin Administrator profile?
An administrator would like to protect against inbound threats such as buffer overflows and illegal code execution.
Which Security profile should be used?
What can be achieved by selecting a policy target prior to pushing policy rules from Panorama?
What is the purpose of the automated commit recovery feature?
Which type of address object is "10 5 1 1/0 127 248 2"?
Where in Panorama Would Zone Protection profiles be configured?
A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall?
Why should a company have a File Blocking profile that is attached to a Security policy?
An administrator would like to block access to a web server, while also preserving resources and minimizing half-open sockets. What are two security policy actions the administrator can select? (Choose two.)
Which administrator type utilizes predefined roles for a local administrator account?
If users from the Trusted zone need to allow traffic to an SFTP server in the DMZ zone, how should a Security policy with App-ID be configured?
A)

B)

C)

D)

Which type of administrator account cannot be used to authenticate user traffic flowing through the firewall’s
data plane?
Where within the URL Filtering security profile must a user configure the action to prevent credential submissions?
An administrator wants to prevent access to media content websites that are risky
Which two URL categories should be combined in a custom URL category to accomplish this goal? (Choose two)
Match the cyber-attack lifecycle stage to its correct description.
According to the best practices for mission critical devices, what is the recommended interval for antivirus updates?
Which firewall feature do you need to configure to query Palo Alto Networks service updates over a data-plane interface instead of the management interface?
Which two firewall components enable you to configure SYN flood protection thresholds? (Choose two.)
Which URL profiling action does not generate a log entry when a user attempts to access that URL?
What are the requirements for using Palo Alto Networks EDL Hosting Sen/ice?
Which dynamic update type includes updated anti-spyware signatures?
An administrator wants to enable access to www.paloaltonetworks.com while denying access to all other sites in the same category.
Which object should the administrator create to use as a match condition for the security policy rule that allows access to www.paloaltonetworks.com?
An administrator has an IP address range in the external dynamic list and wants to create an exception for one specific IP address in this address range.
Which steps should the administrator take?
Which two statements are correct about App-ID content updates? (Choose two.)
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
Which path in PAN-OS 10.0 displays the list of port-based security policy rules?
After making multiple changes to the candidate configuration of a firewall, the administrator would like to start over with a candidate configuration that matches the running configuration.
Which command in Device > Setup > Operations would provide the most operationally efficient way to accomplish this?
Which solution is a viable option to capture user identification when Active Directory is not in use?
Which CLI command will help confirm if FQDN objects are resolved in the event there is a shadow rule?
What is an advantage for using application tags?
Identify the correct order to configure the PAN-OS integrated USER-ID agent.
3. add the service account to monitor the server(s)
2. define the address of the servers to be monitored on the firewall
4. commit the configuration, and verify agent connection status
1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent
Which action would an administrator take to ensure that a service object will be available only to the selected device group?