Paloalto Networks CloudSec-Pro Palo Alto Networks Cloud Security Professional Exam Practice Test
Palo Alto Networks Cloud Security Professional Questions and Answers
What are two ways to scan container images in Jenkins pipelines? (Choose two.)
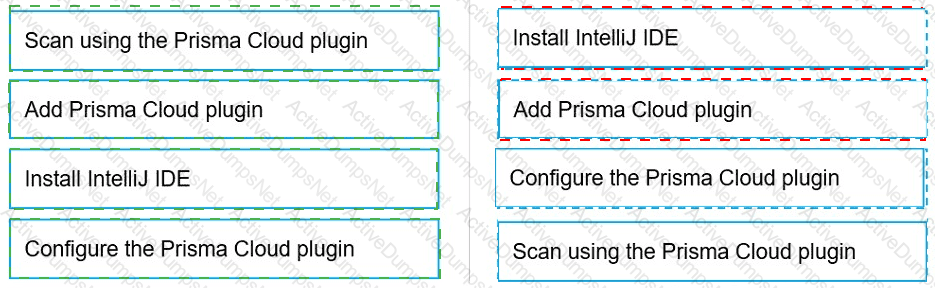
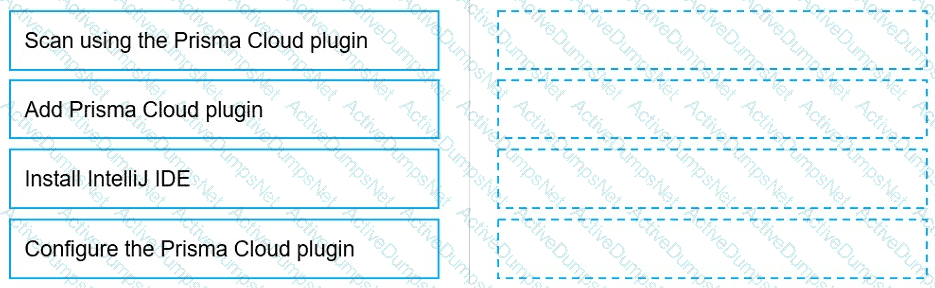
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
In Azure, what permissions need to be added to Management Groups to allow Prisma Cloud to calculate net effective permissions?
A Prisma Cloud administrator is onboarding a single GCP project to Prisma Cloud. Which two steps can be performed by the Terraform script? (Choose two.)
Which data security default policy is able to scan for vulnerabilities?
The exclamation mark on the resource explorer page would represent?
Who can access saved searches in a cloud account?
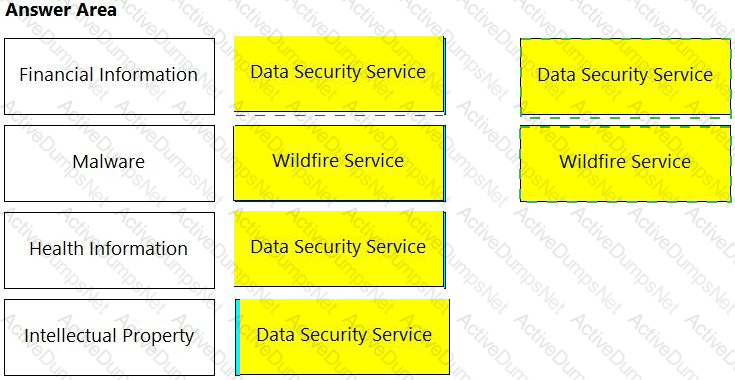
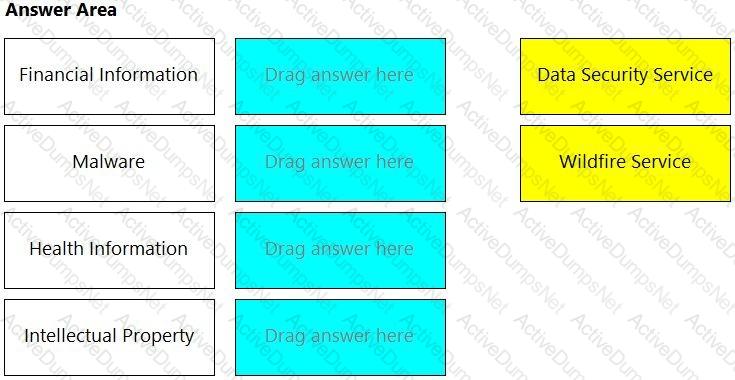
Match the service on the right that evaluates each exposure type on the left.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud? (Choose two.)
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
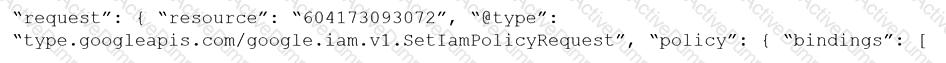
B)
C)
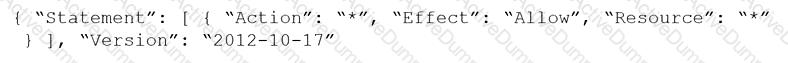
D)

The security auditors need to ensure that given compliance checks are being run on the host. Which option is a valid host compliance policy?
Which three incident types will be reflected in the Incident Explorer section of Runtime Defense? (Choose three.)
An administrator sees that a runtime audit has been generated for a Container. The audit message is “DNS resolution of suspicious name wikipedia.com. type A”.
Why would this message appear as an audit?
A customer's Security Operations Center (SOC) team wants to receive alerts from Prisma Cloud via email once a day about all policies that have a violation, rather than receiving an alert every time a new violation occurs.
Which alert rule configuration meets this requirement?
Which two filters are available in the SecOps dashboard? (Choose two.)
Which report includes an executive summary and a list of policy violations, including a page with details for each policy?
A customer wants to harden its environment from misconfiguration.
Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
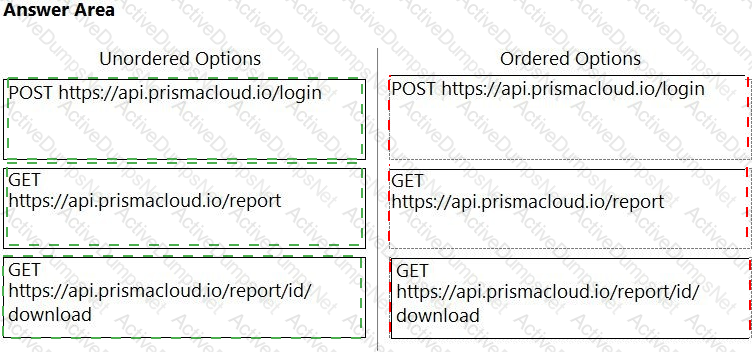
An administrator has been tasked with creating a custom service that will download any existing compliance report from a Prisma Cloud Enterprise tenant.
In which order will the APIs be executed for this service?
(Drag the steps into the correct order of occurrence, from the first step to the last.)

One of the resources on the network has triggered an alert for a Default Config policy.
Given the following resource JSON snippet:
Which RQL detected the vulnerability?
A)

B)
C)
D)
Which of the following is a reason for alert dismissal?
What happens when a role is deleted in Prisma Cloud?
Console is running in a Kubernetes cluster, and you need to deploy Defenders on nodes within this cluster.
Which option shows the steps to deploy the Defenders in Kubernetes using the default Console service name?
What are the subtypes of configuration policies in Prisma Cloud?
Which command correctly outputs scan results to stdout in tabular format and writes scan results to a JSON file while still sending the results to Console?
A customer has a requirement to scan serverless functions for vulnerabilities.
What is the correct option to configure scanning?
On which cloud service providers can new API release information for Prisma Cloud be received?
In which two ways can Prisma Cloud images be retrieved in Prisma Cloud Compute Self-Hosted Edition? (Choose two.)
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
When would a policy apply if the policy is set under Defend > Vulnerability > Images > Deployed?
Per security requirements, an administrator needs to provide a list of people who are receiving e-mails for Prisma Cloud alerts.
Where can the administrator locate this list of e-mail recipients?
The development team is building pods to host a web front end, and they want to protect these pods with an application firewall.
Which type of policy should be created to protect this pod from Layer7 attacks?
Which two CI/CD plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.).
What are two built-in RBAC permission groups for Prisma Cloud? (Choose two.)
In Prisma Cloud for Azure Net Effective Permissions Calculation, the following Azure permission levels are supported by which three permissions? (Choose three).
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
Which policy type should be used to detect and alert on cryptominer network activity?
Which two roles have access to view the Prisma Cloud policies? (Choose two.)
Which set of steps is the correct process for obtaining Console images for Prisma Cloud Compute Edition?
What are two alarm types that are registered after alarms are enabled? (Choose two.)
A customer wants to be notified about port scanning network activities in their environment. Which policy type detects this behavior?
What is the behavior of Defenders when the Console is unreachable during upgrades?
An administrator has been tasked with a requirement by your DevSecOps team to write a script to continuously query programmatically the existing users, and the user’s associated permission levels, in a Prisma Cloud Enterprise tenant.
Which public documentation location should be reviewed to help determine the required attributes to carry out this step?
What is the purpose of Incident Explorer in Prisma Cloud Compute under the "Monitor" section?
An administrator sees that a runtime audit has been generated for a container.
The audit message is:
“/bin/ls launched and is explicitly blocked in the runtime rule. Full command: ls -latr”
Which protection in the runtime rule would cause this audit?
The Compute Console has recently been upgraded, and the administrator plans to delay upgrading the Defenders and the Twistcli tool until some of the team’s resources have been rescaled. The Console is currently one major release ahead.
What will happen as a result of the Console upgrade?
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
Which field is required during the creation of a custom config query?
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
Given an existing ECS Cluster, which option shows the steps required to install the Console in Amazon ECS?
An administrator of Prisma Cloud wants to enable role-based access control for Docker engine.
Which configuration step is needed first to accomplish this task?
Which option shows the steps to install the Console in a Kubernetes Cluster?
Which port should a security team use to pull data from Console’s API?
A customer has a requirement to terminate any Container from image topSecret:latest when a process named ransomWare is executed.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
What is the correct method for ensuring key-sensitive data related to SSNs and credit card numbers cannot be viewed in Dashboard > Data view during investigations?
Which two attributes of policies can be fetched using API? (Choose two.)
Which component(s), if any, will Palo Alto Networks host and run when a customer purchases Prisma Cloud Enterprise Edition?
Which role does Prisma Cloud play when configuring SSO?
How many CLI remediation commands can be added in a custom policy sequence?
How often do Defenders share logs with Console?
Which two attributes are required for a custom config RQL? (Choose two.)
Prisma Cloud cannot integrate which of the following secrets managers?
A customer has a requirement to restrict any container from resolving the name www.evil-url.com.
How should the administrator configure Prisma Cloud Compute to satisfy this requirement?
The security team wants to enable the “block” option under compliance checks on the host.
What effect will this option have if it violates the compliance check?
Which of the following is displayed in the asset inventory?
What factor is not used in calculating the net effective permissions for a resource in AWS?
A user from an organization is unable to log in to Prisma Cloud Console after having logged in the previous day.
Which area on the Console will provide input on this issue?
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
A customer has Prisma Cloud Enterprise and host Defenders deployed.
What are two options that allow an administrator to upgrade Defenders? (Choose two.)
A customer is interested in PCI requirements and needs to ensure that no privilege containers can start in the environment.
Which action needs to be set for “do not use privileged containers”?
Which Defender type performs registry scanning?
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
Which two fields are required to configure SSO in Prisma Cloud? (Choose two.)
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
Which two integrations enable ingesting host findings to generate alerts? (Choose two.)
A customer is reviewing Container audits, and an audit has identified a cryptominer attack. Which three options could have generated this audit? (Choose three.)
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
Which three steps are involved in onboarding an account for Data Security? (Choose three.)