Examine this command:
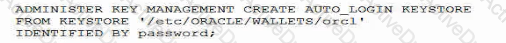
Which two statements are true?
As the SYSKM user you must create the password-based keystore, which will be used for TDE. Examine this list:

Identify the sequence that Oracle uses to search for the keystore and its location.
When creating labels using Oracle Label Security, which is required?
Examine this command:

What masking definitions does it list?
Which statement is true about Network ACLs?
You are the Service Consumer In the Cloud Shared Responsibility Model.
Which three are your responsibility when using the Infrastructure as a Service (IaaS)?
Which CVSS Version 3.1 metric indicates how close an attacker needs to be to the vulnerable component?
Which two represent the set of users that are never affected by connect command rules?
Examine these commands and responses:
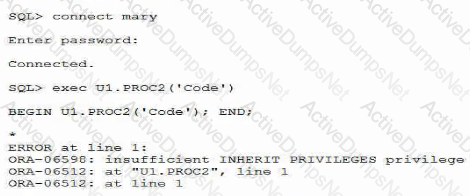
Which object privilege must be granted to allow execution of the stored procedure?
A database link must be created to connect a source Autonomous Database to target on premises database.
Examine this command:
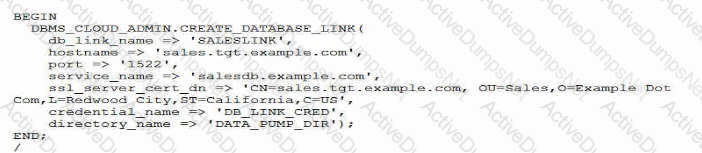
Which two options are true?
Which two statements are true about running the Oracle Database Security Assessment Tool (DBSAT) Collector?
Examine this statement and its result:
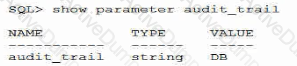
You issue this statement and then restart the database instance:
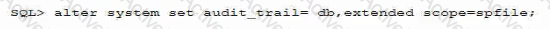
Which Is true about generated audit records?
Examine this parameter In sqinet.ora:
SQLNET.ADTHENTICATION_SEBVICES=(NONE)
For which two cases do you need a password file?