Challenge 2 -Task 1
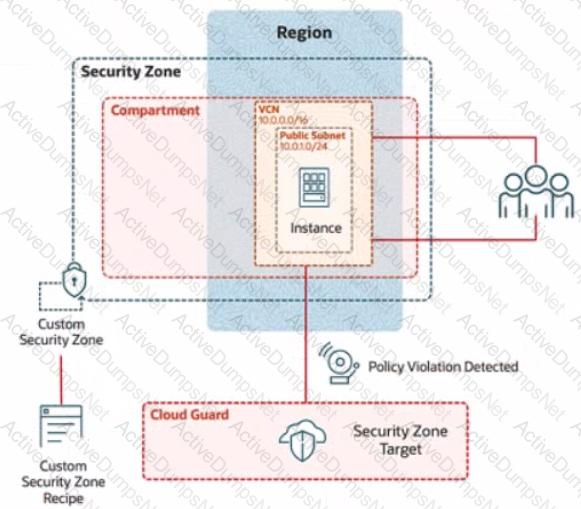
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 1: Create a Custom Security Zone Recipe
Create a Custom Security Zone Recipe named IAD-SP-PBT-CSP-01 that allows the provisioning of compute instances in the public subnet.
Enter the OCID of the created custom security zone recipe in the text box below.
Challenge 1 - Task 1
Integrate TLS Certificate Issued by the OCI Certificates Service with Load Balancer
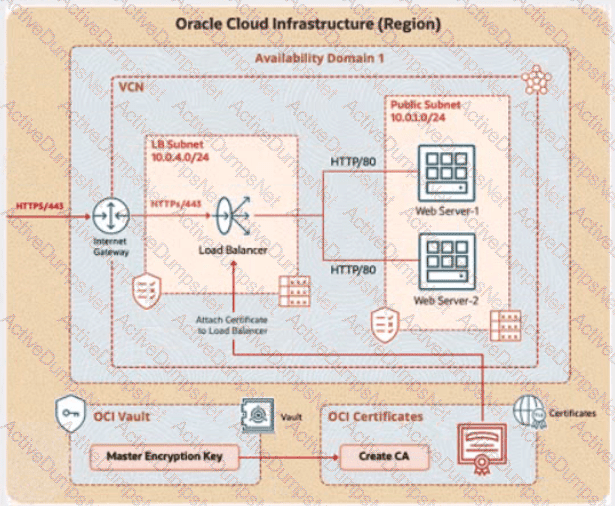
You are a cloud engineer at a tech company that is migrating its services to Oracle Cloud Infrastructure (OCI). You are required to set up secure communication for your web application using OCI's Certificate service. You need to create a Certificate Authority (CA), issue a TLS/SSL server certificate, and configure a load balancer to use this certificate to ensure encrypted traffic between clients and the backend servers.
Review the architecture diagram, which outlines the resources you'll need to address the requirement.
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
OCI Vault to store the secret required by the program, which is created in the root compartment as PBI_Vault_SP
Task 1: Create and Configure a Virtual Cloud Network (VCN)
Create a Virtual Cloud Network (VCN) namedPBT-CERT-VCN-01with the following specifications:
VCN with a CIDR block of 10.0.0.0/16
Subnet 1 (Compute Instance):
Name:Compute-Subnet-PBT-CERT
CIDR Block:10.0.1.0/24
Subnet 2 (Load Balancer):
Name:LB-Subnet-PBT-CERT-SNET-02
CIDR Block:10.0.2.0/24
Internet Gatewayfor external connectivity
Route table and security lists:
Security List namedPBT-CERT-CS-SL-01for Subnet 1 (Compute-Subnet-PBT-CERT) to allow SSH (port 22) traffic
Security List namedPBT-CERT-LB-SL-01for Subnet 2 (LB-Subnet-PBT-CERT) to allow HTTPS (port 443) traffic
"Enter the OCID of the created VCN in the text box below.
Challenge 2
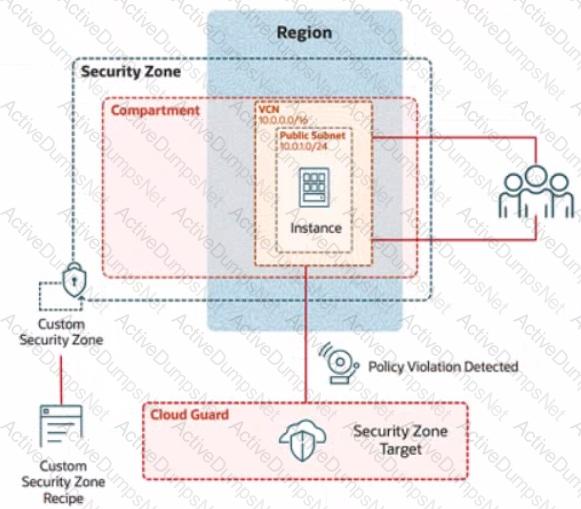
In deploying a new application, a cloud customer needs to reflect different security postures. If a security zone is enabled with the Maximum Security Zone recipe, the customer will be unable to create or update a resource in the security zone if the action violates the attached Maximum Security Zone policy.
As an application requirement, the customer requires a compute instance in the public subnet. You therefore, need to configure Custom Security Zones that allow the creation of compute instances in the public subnet.
Review the architecture diagram, which outlines the resoures you'll need to address the requirement:
Preconfigured
To complete this requirement, you are provided with the following:
Access to an OCI tenancy, an assigned compartment, and OCI credentials
Required IAM policies
Task 5: Provision a Compute Instance
Provision a compute instance in the IAD-SP-PBT-PUBSNET-01 public subnet, where:
Name IAD-SP-PBT-1-VM-01
image: Oracle Linux 8
Shape VM: Standard, A1, Flex
Enter the OCID of the created compute instance in the text box below.
Task 3: Create a Master Encryption Key
Note: OCI Vault to store the key required by this task is created in the root compartment as PBI_Vault_SP
Create an RSA Master Encryption Key (MEK), where:
Key name: PBT-CERT-MEK-01-
For example, if your username is 99008677-lab.user01, then the MEK name should be PBT-CERT-MEK-01990086771abuser01
Ensure you eliminate special characters from the user name.
Key shape: 4096 bits
Enter the OCID of the Master Encryption Key created in the provided text box:
Task 2: Create a Compute Instance and Install the Web Server
Create a compute instance, where:
Name: PBT-CERT-VM-01
Image: Oracle Linux 8
Shape: VM.Standard.A1.Flex
Subnet: Compute-Subnet-PBT-CERT
Install and configure Apache web server:
a.
Install Apache
sudo yum -y install httpd
b.
Enable and start Apache
sudo systemctl enable httpd
sudo systemctl restart httpd
2. Install and configure Apache web server:
a. Install Apache
sudo yum -y install httpd
b. Enable and start Apache
sudo systemctl enable httpd
sudo systemctl restart httpd
c. Configure firewall to allow HTTP traffic (port 80)
sudo firewall-cmd --permanent --add-port=80/tcp
sudo firewall-cmd --reload
d. Create an index.html file
sudo bash -c 'echo You are visiting Web Server 1 >> /var/www/html/index.html'
Enter the OCID of the created compute instance PBT-CERT-VM-01 in the text box below.
An OCI administrator notices that a compute instance running in the production compartment is unable to create Object Storage buckets using the OCI CLI command:
oci os bucket create --name mybucket --compartment-id
The error message returned states:
"NotAuthorizedOrNotFound: You are not authorized to perform this action."
The administrator verifies that the instance has Internet access and can reach OCI endpoints.
What then could be causing the issue?
When trying to encrypt plaintext using Command Line Interface (CLI), the developer gets a Service Error. This is the command the developer tried to run:
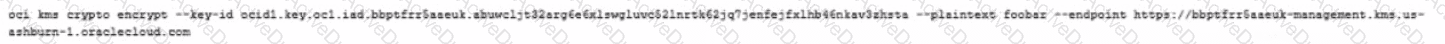
What is the reason for this error?
Your organization needs to implement strong password policies for users in OCI.
Which of the following statements is TRUE about password policies in OCI IAM?
You are the first responder of a security incident for ABC Org. You have identified several IP addresses and URLs in the logs that you suspect may be related to the incident. However, you need more information to confidently determine whether they are indeed malicious or not.
Which OCI service can you use to obtain a more refined information and confidence score for these identified indicators?
A company has deployed OCI Zero Trust Packet Routing (ZPR) to secure its network. They have two compute instances, VM1-01 and VM-02, in a public subnet. VM-01 is tagged with the security attribute app:vm01, and VM-02 is tagged with app:vm02. The VCN is labeled with network:vcn01, The ZPR policy states:

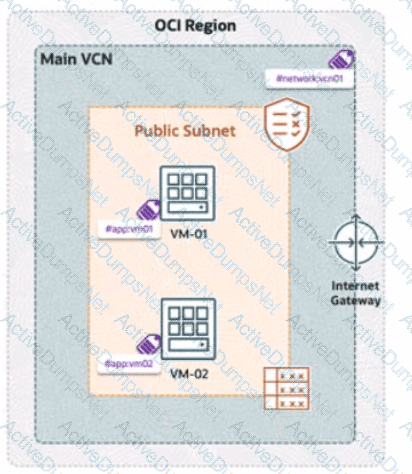
"What is the expected outcome of this policy?