Nutanix NCP-US Nutanix Certified Professional – Unified Storage (NCP-US) v6 exam Exam Practice Test
Nutanix Certified Professional – Unified Storage (NCP-US) v6 exam Questions and Answers
An administrator needs to deploy a new Linux log collector package which creates a directory for each monitored item. The logs would be analyzed by a Windows application.
Which action should the administrator take, that will provide the best performance and simplicity?
Refer the exhibit.
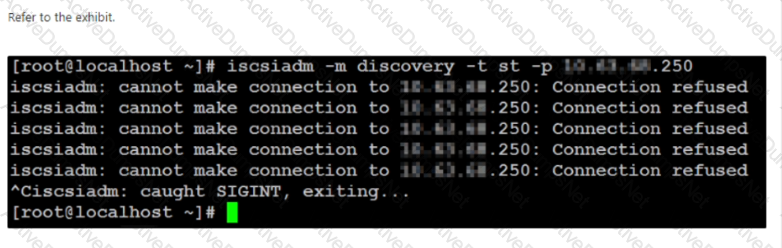
An administrator has received a support request indicating that after an update and reboot Of a Linux VM, the VM is no longer able to access the Volume Groups (VG) assigned to it.
When the administrator investigates the issue, the error message shown in the exhibit is displayed.
What are two possible reasons for the behavior? (Choose two.)
An administrator configured WORM on an existing Objects bucket at 4 p.m. on Monday. During the configuration, the administrator did not select Enable Version. At 8 a.m. the next morning, a ticket was submitted to update the bucket to include versioning.
What are the correct steps to make the requested change?
A corporate compliance team has asked an administrator to stop using default passwords in the environment. The administrator needs to update the password used on the FSVM.
In which order should the administrator change the FSVM’s default password?
Task Step
Step 1
Step 2
step 3
Step 4
Select
Log onto a file server VM via SSH
Change the password
Respond to the prompts, providing the current and new Nutanix user password
Repeat the steps on the remaining FSVMs
A company decided to switch their existing Windows file server to a new Files instance. After successfully deploying Files. an administrator now needs to plan to reduce the impact of any potential outage. As the source file server resides across the WAN from the destination file server over an unreliable network connection.
The administrator needs to ensure there is minimal impact to data already copied, should a network outage occur.
How should the administrator meet this requirement?
Due to a new IP addressing plan for the vDesktops network, an administrator needs to change the Files client-side network.
Which action should the administrator perform first?
An existing Objects bucket was created for backups with these parameters:
A)WORM policy of three years
B)Versioning policy of two years
C)Lifecycle policy of two years
The customer reports that the cluster is nearly full due to backups created during a recent crypto locker attack. The customer would like to automatically delete backups older than one year to free up space in the cluster.
How should the administrator change settings within Objects?
An administrator needs to configure a service to collect data from a forensic software package that audits client access to a specific location. Data need to be immutable,
Which option meets these requirements?
An administrator of an existing Nutanix cluster running Kubernetes with multiple PODs notices that NCC checks report that some volume groups experience the following error:
Node x .x.x.x:
FAIL: Volume Group pvc -XXXXXX-XXXX-XXXX-XXXX-XXXXXXXXX space usage (908)
The administrator checks the volume group usage from the Kubernetes pod and get different usage results. The current stats are 55% used disk space.
The results of the NCC check do not match what manually-executed checks report.
What is the cause of this behavior?
A company has distributed a new document bundle, entitled Health and Security Policies to all employees. HR has asked an administrator to verify if key users have opened the document.
How can an administrator support this request with File Analytics?
An administrator is implementing a VDI solution in a Nutanix cluster running AHV. The implementation includes home shares for user files. The shares have to be highly available, only accessible by the named user, and replicated to a DR site.
What solution would best fulfill these requirements?
A company has a number of thin clients which need to boot over the network. The company is using Volumes for this project.
Which component is needed to meet this requirement?(Choose two.)
