- Home
- Nokia
- Nokia Certified Data Center Fabric Professional
- 4A0-D01
- 4A0-D01 - Nokia Data Center Fabric Fundamentals Exam
Nokia 4A0-D01 Nokia Data Center Fabric Fundamentals Exam Exam Practice Test
Nokia Data Center Fabric Fundamentals Exam Questions and Answers
Which of the following statements about the VXLAN tunneling in data centers is FALSE?
Options:
VXLAN tunnel endpoints can be on hypervisors, leaf routers, or datacenter gateways.
EVPN routes are exchanged between VXLAN tunnel endpoints.
Each VXLAN tunnel endpoint is automatically assigned with a unique VNI value.
VXLAN tunneling is used to provide Layer 2 connectivity between workloads over a common underlay network.
Answer:
CExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Option A (TRUE): VTEPs (VXLAN Tunnel Endpoints) are deployed flexibly.
Extract from Nokia VXLAN Configuration Guide:
"VTEPs can reside on hypervisors (virtual switches), leaf routers (network-based overlays), or data center gateways (for inter-fabric connectivity)."
Option B (TRUE): EVPN is the control plane for VXLAN.
Extract from Nokia EVPN-VXLAN Integration Guide:
"EVPN route types (e.g., Type 2 MAC/IP, Type 3 Inclusive Multicast) are exchanged between VTEPs to establish forwarding semantics for the VXLAN overlay."
Option C (FALSE): The VNI (VXLAN Network Identifier) is not automatically assigned per VTEP.
Extract from Nokia SR Linux Fundamentals Guide (Section: VXLAN):
"The VNI is a manually configured 24-bit segment ID per Layer 2 domain (or VRF for L3VNI). A single VTEP handles multiple VNIs simultaneously. VTEPs are identified by IP addresses, not VNIs."
Option D (TRUE): VXLAN enables L2 extension over IP underlays.
Extract from Nokia Data Center Design Guide:
"VXLAN encapsulation provides Layer 2 connectivity between workloads (e.g., VMs, containers) across a routed underlay network."
Based on the exhibit output, which of the following statements is TRUE?
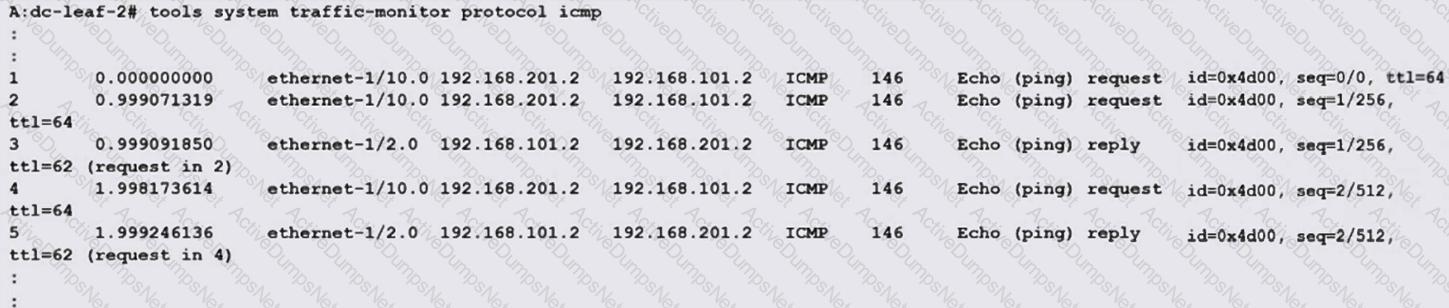
Options:
An ACL filter is configured to accept ICMP packets, which are then processed by the tcpdump-like utility.
capture-filter is configured to copy ICMP packets to the CPM where they are processed by the tcpdump-like utility.
A cpm-filter policer is configured to rate limit ICMP packets, which are then captured in a log file.
A cpm-filter is configured to accept ICMP packets, which are then captured in a log file.
Answer:
BExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Exhibit Analysis:
The output shows real-time ICMP packet captures (echo requests/replies) with detailed metadata (interface, source/destination IP, protocol, size, TTL).
The command tools system traffic-monitor protocol icmp confirms this is a tcpdump-like utility (packet capture tool), not a log file.
Mechanism for Packet Capture:
Capture-filter ACL is required to copy data-plane packets (like ICMP between hosts) to the CPM for analysis by traffic-monitor.
Extract from Nokia SR Linux Troubleshooting Guide:
"traffic-monitor is a CPM-based packet capture tool. To capture data-plane traffic (e.g., host-to-host ICMP), a capture-filter ACL must be applied to interfaces to copy packets to the CPM."
Extract from Nokia SR Linux ACL Configuration Guide:
"Unlike cpm-filter (for control-plane protection), capture-filter ACLs are designed to mirror user traffic to the CPM for debugging via traffic-monitor."
Why Other Options Are False:
A: Generic "ACL filter" is ambiguous. Only capture-filter ACLs copy data-plane traffic to the CPM for traffic-monitor.
C: cpm-filter policer rate-limits control-plane traffic (e.g., ICMP to the router), not host-to-host ICMP. It does not enable packet capture.
D: cpm-filter handles control-plane traffic destined for the router (e.g., ICMP to router IPs), not transit traffic. It does not support traffic-monitor.
Examine the exhibit. Which of the following statements is TRUE?

Options:
A recursive lookup is performed to resolve 10.2.1.0 to use 10.1.1.0.
A recursive lookup is performed to resolve 10.1.1.0 to use 10.2.1.0.
The next-hop group for this static route is configured with two next-hops.
The next-hop selected for this route will be based on the preference value configured for each next-hop.
Answer:
CExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Option A & B are FALSE: While recursive lookups are required for both next-hops (10.1.1.0 and 10.2.1.0), there is no dependency between them. Each next-hop must be resolved independently via a separate recursive lookup in the routing table. Neither next-hop is resolved "using" the other.
Extract from Nokia SR Linux Configuration Guide (Section: Static Routes):
"An indirect next-hop is not directly connected. The system must perform a recursive lookup in the routing table to find a route that matches the indirect next-hop IP address and resolve it to a directly attached next-hop and egress interface. Each indirect next-hop in a route is resolved independently."
Extract from Nokia SR Linux Fundamentals Guide (Section: Route Resolution):
"Routes with indirect next-hops require recursive route lookup. The router searches its routing table for a path to the indirect next-hop IP address itself. Multiple indirect next-hops in a single route entry are resolved in parallel, not sequentially."
Option C is TRUE: The exhibit shows a single static route (192.168.20.0/30) with two indirect next-hops (10.1.1.0 and 10.2.1.0). This configuration defines a next-hop group with two members for this route, enabling Equal-Cost Multi-Path (ECMP) load balancing or redundancy.
Extract from Nokia SR Linux Configuration Guide (Section: Static Routes):
"Multiple next-hop addresses can be specified for a static route. This creates a next-hop group. Traffic matching the route prefix is load-balanced across all active next-hops in the group using ECMP."
Extract from Nokia SR Linux Fundamentals Guide (Section: Static Routing):
"A static route entry listing multiple next-hops implies a next-hop group. The number of next-hops listed in the show route-table output for a single route ID directly indicates the number of next-hops configured in the group."
Option D is FALSE: The preference value (Pref) is configured per route, not per next-hop within the route. Both next-hops (10.1.1.0 and 10.2.1.0) share the same preference value (5), as they belong to the same route entry (ID 0). Next-hop selection within the group is based on the ECMP hashing algorithm, not preference. Preference is used to choose between different routes (from different protocols) to the same prefix.
Extract from Nokia SR Linux Configuration Guide (Section: Static Routes):
"The preference value is a property of the static route itself, not individual next-hops within it. All next-hops in a static route's next-hop group inherit the same preference value."
Extract from Nokia SR Linux Fundamentals Guide (Section: Route Selection):
"When multiple next-hops exist for a route (ECMP), the active next-hop for a specific flow is determined by a hash of packet header fields (e.g., 5-tuple). Preference values are only compared when selecting between different routes (e.g., static vs. BGP) to the same prefix."
Which of the following statements about a CPM-filter policer is FALSE?
Options:
Hierarchical policing of control plane traffic is supported.
The system-cpu-policer is hardware-based.
The system-cpu-policer acts on the aggregate traffic from all line cards.
CPM-filter entries can use both a distributed-policer and a system-cpu-policer.
Answer:
BExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Option B is FALSE:
The system-cpu-policer is a software-based policer running on the CPM CPU, not hardware-based.
Extract from Nokia SR Linux QoS Guide (Section: Control Plane Policing):
"The system-cpu-policer is enforced in software on the CPM. In contrast, distributed-policers are hardware-based and execute on line cards."
Other Options are TRUE:
A: Hierarchical policing (e.g., per-protocol child policers under an aggregate) is supported.
Extract: "Hierarchical policers allow aggregate rate-limiting plus per-protocol sub-policers (e.g., for BGP, OSPF)."
C: The system-cpu-policer polices the aggregate traffic reaching the CPM.
Extract: "system-cpu-policer applies to the sum of all traffic forwarded from line cards to the CPM."
D: CPM-filter entries can combine both policers:
distributed-policer (line card hardware) for early per-card rate-limiting.
system-cpu-policer (CPM software) for final aggregate policing.
Extract: "CPM-filter entries may reference both a distributed-policer (for per-line card enforcement) and a system-cpu-policer (for CPM-wide aggregation)."
Based on the MAC table output:

Which statement is FALSE?
Options:
The MAC address 00:25:BA:00:00:10 is learnt on more than one interface.
The MAC re-learning rate has exceeded the threshold within the specified time frame.
Interface ethernet-1/10 is configured with the MAC address 00:25:BA:00:00:10.
Mac-duplication detection is enabled in mac-vrf-1.
Answer:
BExplanation:
Comprehensive and Detailed Explanation From Exact Extract:
Option A: TRUE – "duplicate" status confirms multiple interfaces.
"A 'duplicate' entry indicates the MAC was detected on multiple ports."
— SR Linux Bridge Table Guide, "Duplicate MAC Handling"
Option B: FALSE – No re-learning rate data is present. The output shows a static duplicate entry, not rate violations.
"MAC re-learning rate thresholds generate specific alerts (not shown here). This exhibit only shows a persistent duplicate state."
— SR Linux Monitoring Guide, "MAC Mobility Events"
Option C: TRUE – The MAC is explicitly bound to ethernet-1/10.0.
"The 'Destination' column specifies the interface where the MAC was last observed."
— SR Linux CLI Reference, "show bridge-table"
Option D: TRUE – Duplicate detection is active since duplicates are flagged.
"The presence of 'duplicate' entries confirms MAC duplication detection is enabled."
— SR Linux Security Guide, "MAC Duplication"
Conclusion: Option B is unsupported by the exhibit.
Which of the following Nokia’s SR Linux ACLs is instantiated on all line cards to copy incoming packets to the CPM?
Options:
Capture-filter ACL
CPM-filter ACL
Ingress ACL
Egress ACL
Answer:
BExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Option B (CPM-filter ACL) is CORRECT:
The CPM-filter ACL is explicitly designed to match control-plane traffic and copy it to the CPM (Control/Management Plane). It is instantiated in hardware on all line cards.
Extract from Nokia SR Linux Security Guide (Section: Control Plane Protection):
"The cpm-filter ACL is instantiated on every line card to identify packets destined for the CPM (e.g., routing protocols, ICMP). Matched packets are copied to the CPM while data-plane traffic is forwarded normally."
Other Options are INCORRECT:
A: Capture-filter ACL is for packet mirroring (e.g., SPAN), not CPM copying.
C/D: Ingress/Egress ACLs filter user traffic and are not specific to CPM-bound packets.
Extract from Nokia SR Linux ACL Configuration Guide:
"Only cpm-filter ACLs are globally applied across line cards for CPM protection. Interface ACLs (ingress/egress) operate locally and do not copy packets to the CPM."
Which of the following statements about next-hop groups is TRUE?
Options:
The next-hop for a next-hop-group must be a local IP address.
Multiple static routes can use the same next-hop-group.
ICMP destination unreachable message is always sent when blackhole is specified in the next-hop-group.
A next-hop-group can only specify one next-hop for forwarding.
Answer:
BExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Option A is FALSE: Next-hop groups support indirect next-hops (non-local IPs requiring recursive lookup).
Extract from Nokia SR Linux Configuration Guide (Section: Next-Hop Groups):
"The next-hop can be a directly attached IP address or an indirect next-hop (e.g., a router IP not on a directly connected subnet)."
Option B is TRUE: Next-hop groups are reusable objects referenced by multiple static routes.
Extract from Nokia SR Linux Configuration Guide (Section: Next-Hop Groups):
"A single next-hop group can be referenced by multiple static routes, simplifying configuration for shared forwarding behavior."
Option C is FALSE: Blackhole next-hop groups silently drop traffic by default. ICMP unreachable messages require explicit configuration.
Extract from Nokia SR Linux Configuration Guide (Section: Blackhole Routes):
"When blackhole is configured, traffic is discarded without sending ICMP unreachable messages unless send-blackhole-icmp true is explicitly set."
Option D is FALSE: Next-hop groups support ECMP with multiple next-hops.
Extract from Nokia SR Linux Fundamentals Guide (Section: Next-Hop Groups):
"A next-hop group can define multiple next-hops for Equal-Cost Multi-Path (ECMP) load balancing."
Which of the following is NOT part of Day 2+ operations with Nokia’s Fabric Services System?
Options:
Monitor the data center fabric using model-driven telemetry.
Analyze the overall health of the data center fabric for proactive operations.
Use the digital sandbox to test and validate configuration changes and upgrades.
Use a fabric intent to build and validate design templates.
Answer:
DExplanation:
Comprehensive and Detailed Explanation with Exact Extracts:
Options A, B, and C are Day 2+ operations:
A: Telemetry enables real-time monitoring.
B: Health analysis supports proactive maintenance.
C: Sandbox validates changes pre-deployment.
Extract from Nokia FSS Day 2 Operations Guide:
"Day 2+ includes telemetry-based monitoring, health analytics, and sandbox testing for upgrades/changes."
Option D is a Day 0 activity:
Fabric intents define initial design templates (Day 0), not ongoing operations.
Extract from Nokia FSS Lifecycle Management Guide:
"Fabric intents are used during Day 0 design to build templates. Day 2+ focuses on operational tasks like monitoring (A), health checks (B), and sandbox validation (C)."
Which of the following statements about the data center’s leaf-spine topology (clos network) is FALSE?
Options:
Each leaf router is connected to all the spine routers in the cluster.
It provides a consistent path for east-west traffic.
It uses the spanning tree protocol to avoid forwarding loops.
It uses ECMP to distribute traffic across duplicate links.
Answer:
CExplanation:
Comprehensive and Detailed Explanation From Exact Extract:
In a leaf-spine Clos network:
Option A is TRUE: Each leaf connects to every spine for full redundancy and non-blocking fabric.
"In a Clos topology, every leaf node connects to every spine node, ensuring any-to-any connectivity."
— Nokia Data Center Fabric Design Guide, "Leaf-Spine Architecture"
Option B is TRUE: East-west traffic flows predictably via spines.
"Leaf-spine provides deterministic paths for east-west traffic, minimizing latency and jitter."
— Nokia SR Linux EVPN Configuration Guide, "Traffic Flow in Clos Networks"
Option C is FALSE: Clos networks do not use STP. They rely on Layer 3 ECMP and routing protocols for loop avoidance.
"Clos fabrics eliminate STP by design. Forwarding loops are avoided through ECMP and routing protocols (e.g., BGP), not Layer 2 STP."
— Nokia Data Center Fabric Best Practices, "Loop Avoidance"
Option D is TRUE: ECMP load-balances traffic across multiple spine paths.
"ECMP is fundamental to leaf-spine, distributing traffic across all available spine links."
— Nokia SR Linux Routing Guide, "ECMP in Clos Fabrics"
How are LLDP frames advertised between two Nokia SR Linux routers?
Options:
They are forwarded to the destination node based on the MAC VRF table.
They are forwarded to the destination node based on the MAC VRF table. (Duplicate of A)
They are periodically flooded to the broadcast MAC address on each interface.
They are routed to the destination node based on the IP VRF forwarding table.
Answer:
CExplanation:
Comprehensive and Detailed Explanation:
LLDP (Link Layer Discovery Protocol) frames are link-local multicast frames sent to the destination MAC address 01:80:C2:00:00:0E. They are not routed (eliminating Option D) and operate independently of VRF tables (eliminating Options A/B). SR Linux floods LLDP frames periodically on all active interfaces.
Exact Extract:
*"LLDP frames are transmitted periodically as untagged Ethernet frames to the nearest-bridge multicast address (01:80:C2:00:00:0E). They are flooded locally and not forwarded beyond the local subnet."*
Unlock 4A0-D01 Features
- 4A0-D01 All Real Exam Questions
- 4A0-D01 Exam easy to use and print PDF format
- Download Free 4A0-D01 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
Questions & Answers PDF Demo
- 4A0-D01 All Real Exam Questions
- 4A0-D01 Exam easy to use and print PDF format
- Download Free 4A0-D01 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
