Microsoft SC-401 Administering Information Security in Microsoft 365 Exam Practice Test
Administering Information Security in Microsoft 365 Questions and Answers
You need to meet the technical requirements for the Site1 documents.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

HOTSPOT
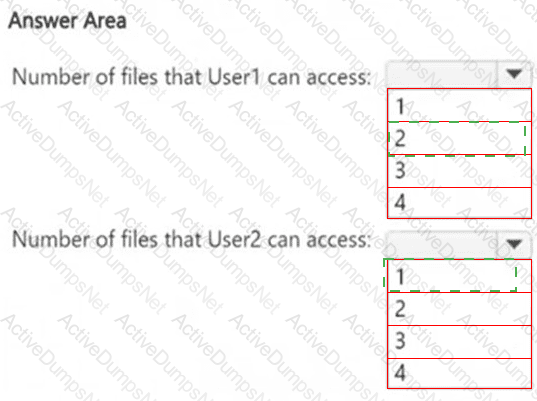
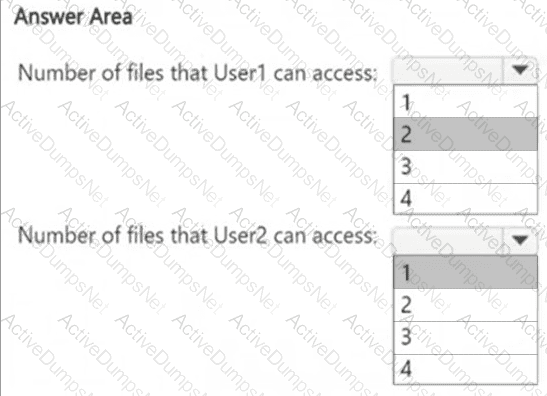
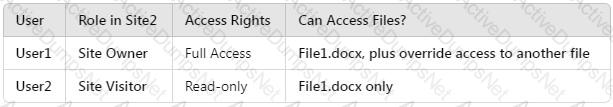
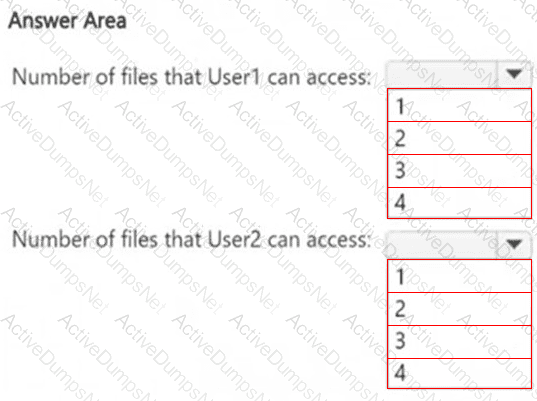
How many files in Site2 can User1 and User2 access after you turn on DLPpolicy1? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
HOTSPOT
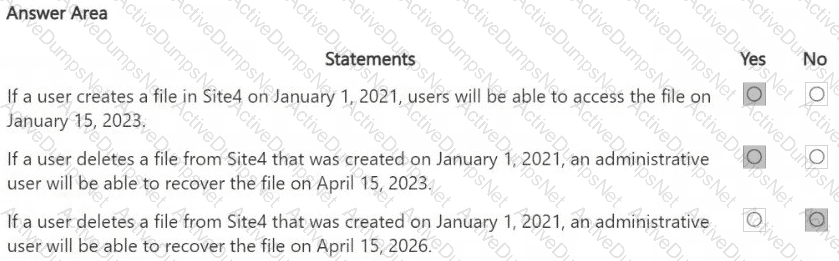
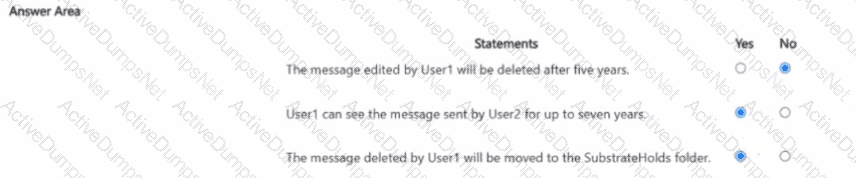
You are reviewing policies for the SharePoint Online environment.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
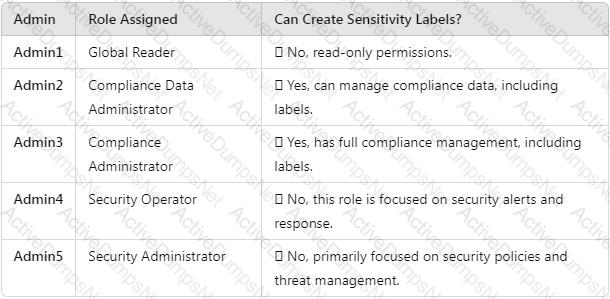
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you assign the Sensitivity Label Administrator role?
You need to meet the retention requirement for the users' Microsoft 365 data.
What is the minimum number of retention policies required to achieve the goal?
HOTSPOT
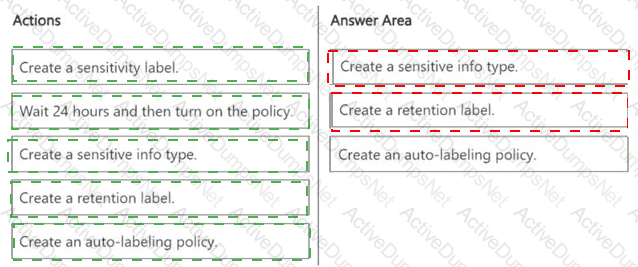
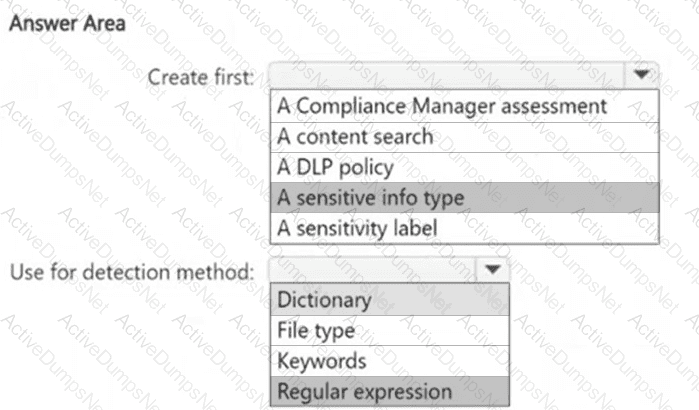
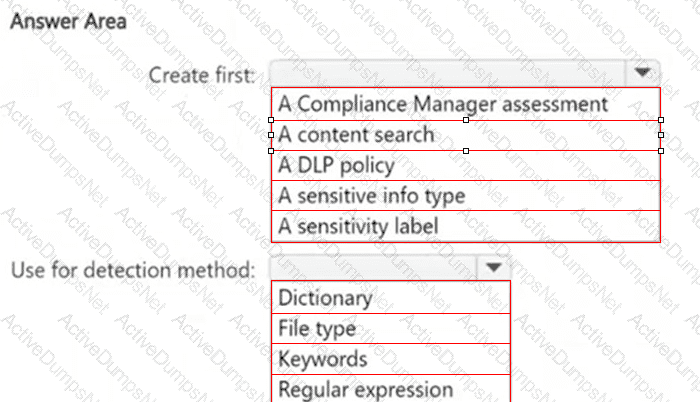
You need to meet the technical requirements for the confidential documents.
What should you create first, and what should you use for the detection method? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
DRAG DROP
You have a Microsoft 365 E5 subscription that has data loss prevention (DLP) implemented.
You need to create a custom sensitive info type. The solution must meet the following requirements:
● Match product serial numbers that contain a 10-character alphanumeric string.
● Ensure that the abbreviation of SN appears within six characters of each product serial number.
● Exclude a test serial number of 1111111111 from a match.
Which pattern settings should you configure for each requirement? To answer, drag the appropriate settings to the correct requirements. Each setting may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
Solution: You run the Set-AdminAuditLogConfig -AdminAuditLogEnabled $true -AdminAuditLogCmdlets *Mailbox* command.
Does that meet the goal?
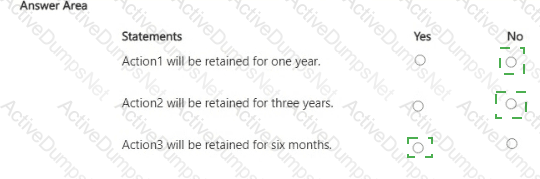
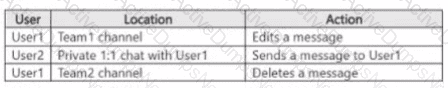
You have a Microsoft 365 ES subscription that uses Microsoft Teams and contains the users shown in the following table.
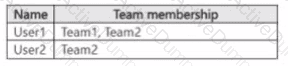
You have the retention policies shown in the following table.

The users perform the actions shown in the following table.
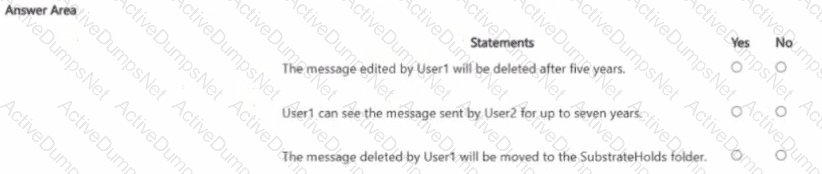
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point
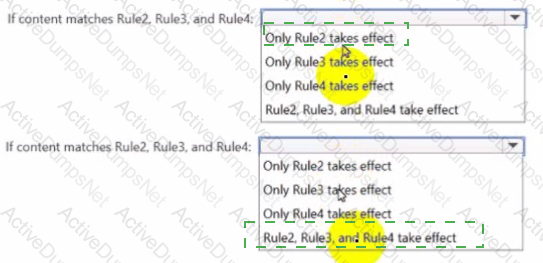
You have a data loss prevention (DIP) policy that has the advanced DIP rules shown in the following table.
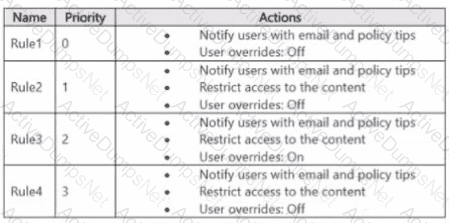
You need to identity which rules will apply when content matches multiple advanced DIP rules.
Which rules should you identify? To answer, select the appropriate options in the answer area.
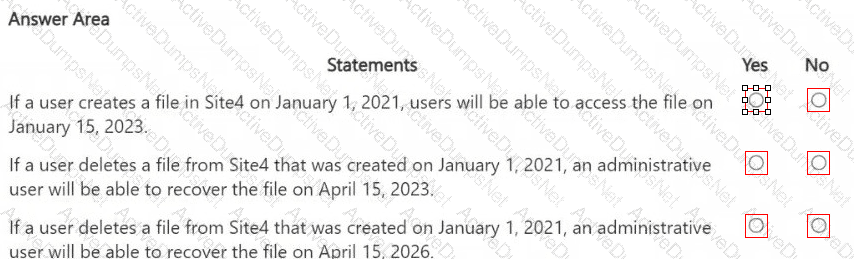
You have a Microsoft 365 E5 subscription that uses Microsoft Purview Audit (Premium) with the 10-Year Audit Log Retention add-on license.
The subscription contains the audit retention policies shown in the following table.
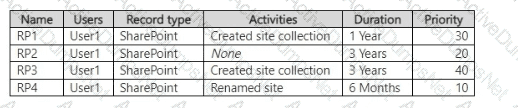
From the SharePoint Online admin center, User1 performs the actions shown in the following table.
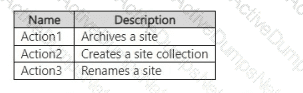
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
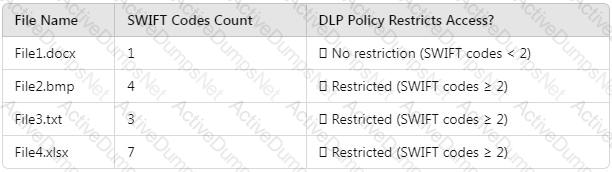
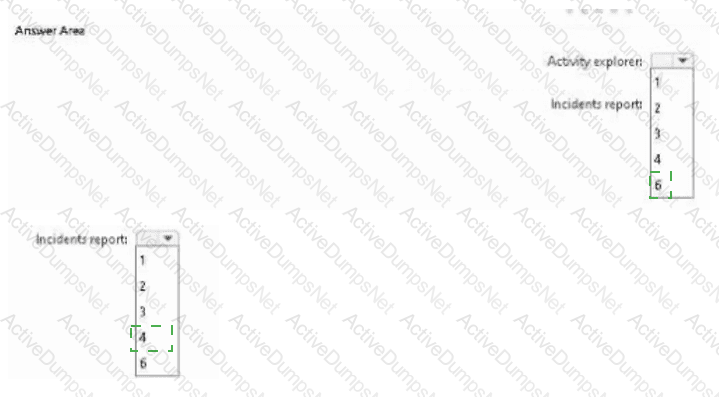
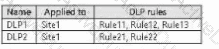
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains three files named File1, File2, and File3.
You create the data loss prevention (DLP) policies shown in the following table.
The DLP rule matches for each file are shown in the following table.
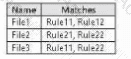
How many DLP policy matches events will be added to Activity explorer, and how many policy matches will be added to the DLP incidents report? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

HOTSPOT
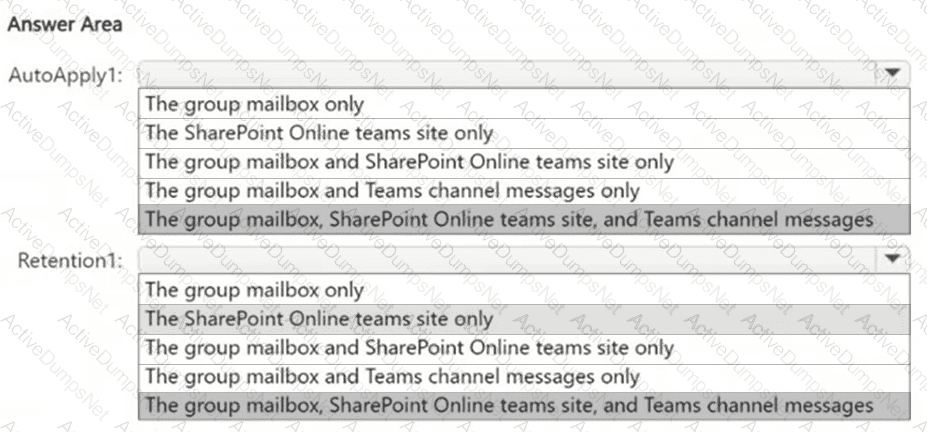
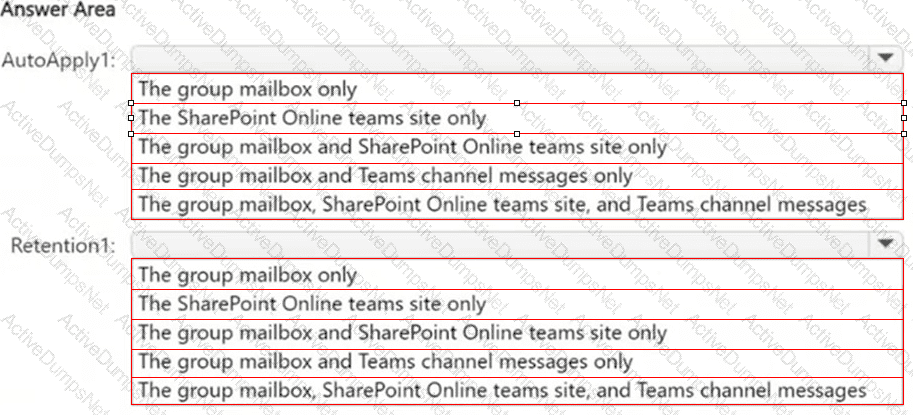
You have a Microsoft 365 E5 subscription that contains two Microsoft 365 groups named Group1 and Group2. Both groups use the following resources:
● A group mailbox
● Microsoft Teams channel messages
● A Microsoft SharePoint Online teams site
You create the objects shown in the following table.
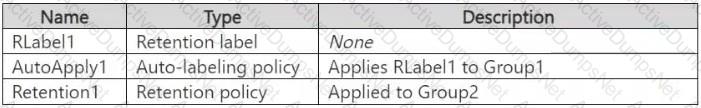
To which resources will AutoApply1 and Retention1 be applied? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription. You create a retention policy and apply the policy to Exchange Online mailboxes.
You need to ensure that the retention policy tags can be assigned to mailbox items as soon as possible.
What should you do?
You have a Microsoft 565 E5 subscription.
You plan to use Microsoft Purview insider risk management.
You need to create an insider risk management policy that will detect data theft from Microsoft SharePoint Online by users that submitted their resignation or are near their employment termination date.
What should you do first?
You have a Microsoft 365 E5 subscription. The subscription contains a user named User1 and the sensitivity labels shown in the following table.

You publish the labels to User1.
The subscription contains the files shown in the following table.
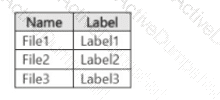
Which files can Microsoft 365 Copilot summarize for User1?
You have a Microsoft 365 subscription.
You need to ensure that users can apply retention labels to individual documents in their Microsoft SharePoint libraries.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You plan to implement insider risk management for users that manage sensitive data associated with a project.
You need to create a protection policy for the users. The solution must meet the following requirements:
● Minimize the impact on users who are NOT part of the project.
● Minimize administrative effort.
What should you do first?
You have a Microsoft 365 E5 tenant that uses a domain named contoso.com.
A user named User 1 sends link based, branded emails that are encrypted by using Microsoft Purview Advanced Message Encryption to the recipients shown in the following table.
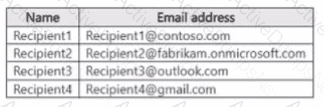
For which recipients Can User1 revoke the emails?
You have a Microsoft 365 E5 subscription that contains a user named User1.
You need to ensure that all email messages that contain attachments are encrypted automatically by using Microsoft Purview Message Encryption.
What should you create?
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Cloud Apps.
You plan to deploy a Defender for Cloud Apps file policy that will be triggered when the following conditions are met:
● A file is shared externally.
● A file is labeled as internal only.
Which filter should you use for each condition? To answer, drag the appropriate filters to the correct conditions. Each filter may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

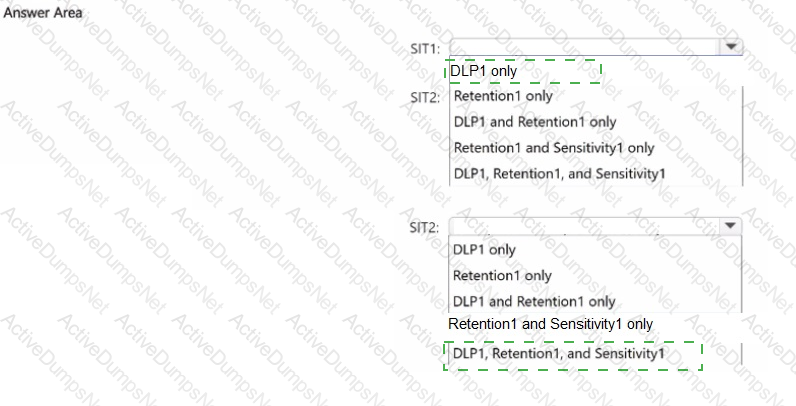
You have a Microsoft 365 E5 subscription that contains the sensitive information types (SITs) shown in the following table.
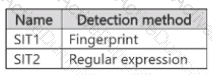
You plan to create the policies shown in the following table and assign them to a Microsoft SharePoint Online site.
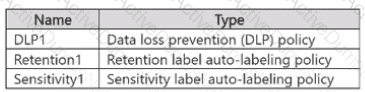
Which policies can use SIT1. and which policies can use SIT2? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to ensure that encrypted email messages sent to an external recipient can be revoked or will expire within seven days.
What should you configure first?
You have a Microsoft 365 E5 subscription.
You are implementing insider risk management.
You need to maximize the amount of historical data that is collected when an event is triggered.
What is the maximum number of days that historical data can be collected?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
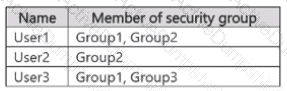
You have the data loss prevention (DLP) policies shown in the following table.
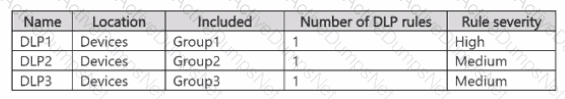
From Insider risk management, you configure a priority user group named PriGroup1 that contains User3 as a member. You have the insider risk policies shown in the following table.
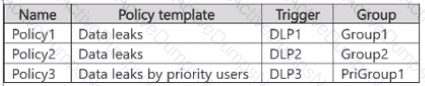
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You have a sensitive information type based on a trainable classifier.
You are unsatisfied with the result of the trainable classifier.
You need to retrain the classifier.
What should you use in the Microsoft Purview portal?
You have a data loss prevention (DIP) policy that applies to the Devices location. The policy protects documents that contain United States passport numbers
Users report that they cannot upload documents to a travel management website because of the pokey.
You need to ensure that the users can upload the documents to the travel management website. The solution must prevent the protected content from being uploaded to other locations.
Which Microsoft 365 Endpoint data loss prevention (Endpoint DIP) setting should you configure?
You have a Microsoft 36S ES subscription.
You need to create the Microsoft Purview insider risk management policies shown in the following table.
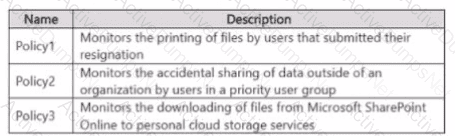
Which policy template should you use for each policy? To answer, drag the appropriate policy templates to the correct polices
Each template may be used once more than once or not at all. You may need to drag the split bar between panes or scroll to view..

You have a Microsoft 365 tenant.
You have a database that stores customer details. Each customer has a unique 13-digit identifier that consists of a fixed pattern of numbers and letters.
You need to implement a data loss prevention (DLP) solution that meets the following requirements:
● Email messages that contain a single customer identifier can be sent outside your company.
● Email messages that contain two or more customer identifiers must be approved by the company's data privacy team.
Which two components should you include in the solution? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
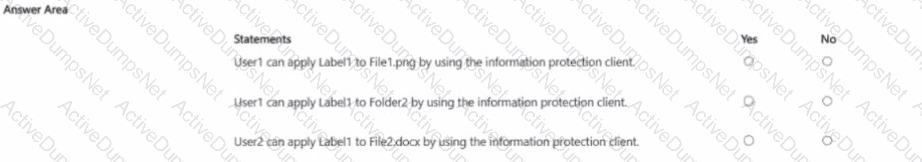
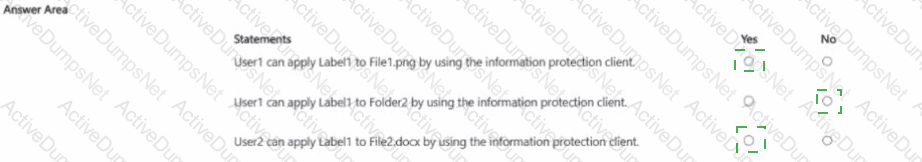
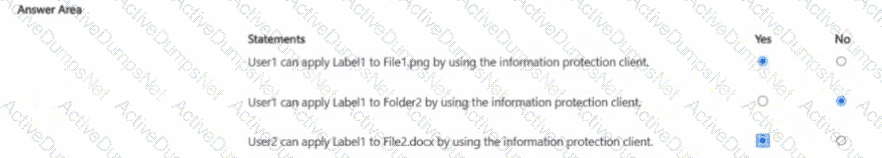
You have a Microsoft 365 IS subscription that contains the resources shown in the following table.

The subscription contains a Windows 11 device named Device 1 and has the Microsoft Purview Information Protection client installed. Device i contains the resources shown in the following table.
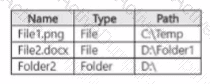
You publish a sensitivity label named Label1 to User1 and Group1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.