Microsoft SC-100 Microsoft Cybersecurity Architect Exam Practice Test
Microsoft Cybersecurity Architect Questions and Answers
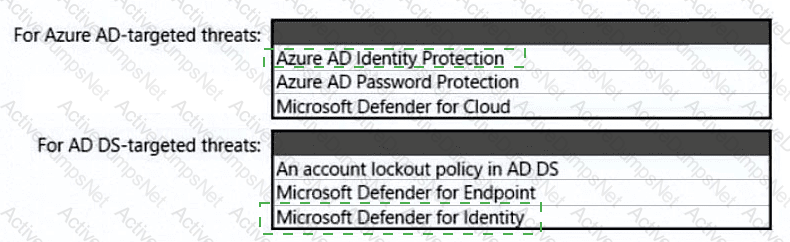
You have Microsoft Defender for Cloud assigned to Azure management groups.
You have a Microsoft Sentinel deployment.
During the triage of alerts, you require additional information about the security events, including suggestions for remediation. Which two components can you use to achieve the goal? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
You are designing a security operations strategy based on the Zero Trust framework.
You need to increase the operational efficiency of the Microsoft Security Operations Center (SOC).
Based on the Zero Trust framework, which three deployment objectives should you prioritize in sequence? To answer, move the appropriate objectives from the list of objectives to the answer area and arrange them in the correct order.
Your company has the virtual machine infrastructure shown in the following table.
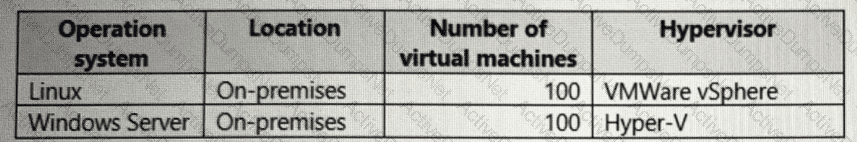
The company plans to use Microsoft Azure Backup Server (MABS) to back up the virtual machines to Azure.
You need to provide recommendations to increase the resiliency of the backup strategy to mitigate attacks such as ransomware.
What should you include in the recommendation?
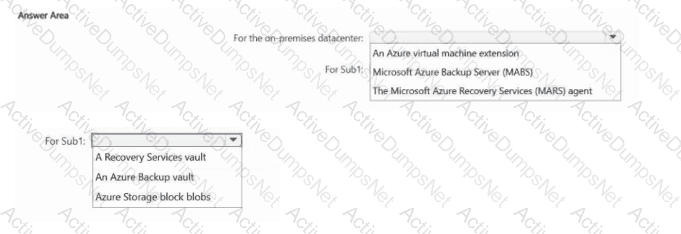
You have an on-premises datacenter. The datacenter contains a server named Server1 that runs Windows Server 2022 and a firewall that prevents Server1 from connecting to the internet.
You have an Azure subscription named Sub1.
You need to recommend a resiliency strategy for Server1 that incorporates a backup plan to transfer the data from Server1 to Sub1.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to recommend a solution to add a watermark to email attachments that contain sensitive data. What should you include in the recommendation?
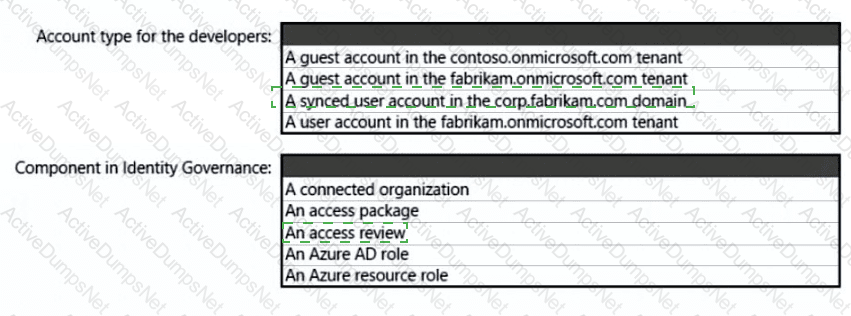
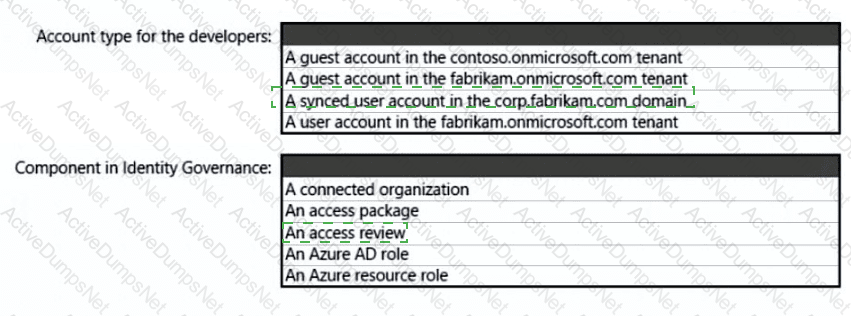
Your network contains an on-premises Active Directory Domain Services (AO DS) domain. The domain contains a server that runs Windows Server and hosts shared folders The domain syncs with Azure AD by using Azure AD Connect Azure AD Connect has group writeback enabled.
You have a Microsoft 365 subscription that uses Microsoft SharePoint Online.
You have multiple project teams. Each team has an AD DS group that syncs with Azure AD Each group has permissions to a unique SharePoint Online site and a Windows Server shared folder for its project. Users routinely move between project teams.
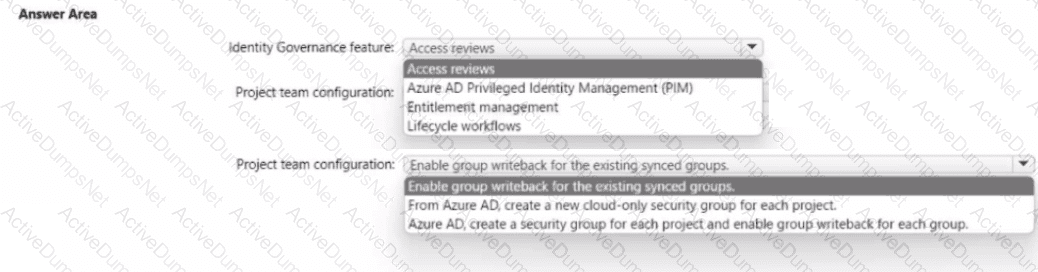
You need to recommend an Azure AD identity Governance solution that meets the following requirements:
• Project managers must verify that their project group contains only the current members of their project team
• The members of each project team must only have access to the resources of the project to which they are assigned
• Users must be removed from a project group automatically if the project manager has MOT verified the group s membership for 30 days.
• Administrative effort must be minimized.
What should you include in the recommendation? To answer select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Your company has a Microsoft 365 E5 subscription.
Users use Microsoft Teams, Exchange Online, SharePoint Online, and OneDrive for sharing and collaborating. The company identifies protected health information (PHI) within stored documents and communications. What should you recommend using to prevent the PHI from being shared outside the company?
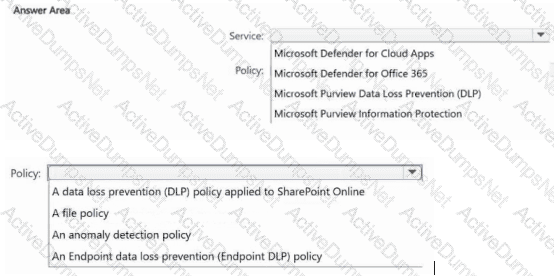
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and Microsoft Purview.
You need to recommend a data protection solution. The solution must ensure that you can identify users that download atypical amounts of data from Microsoft SharePoint Online.
Which service should you include in the recommendation, and which policy should be configured? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
A customer has a Microsoft 365 E5 subscription and an Azure subscription.
The customer wants to centrally manage security incidents, analyze log, audit activity, and search for potential threats across all deployed services.
You need to recommend a solution for the customer. The solution must minimize costs.
What should you include in the recommendation?
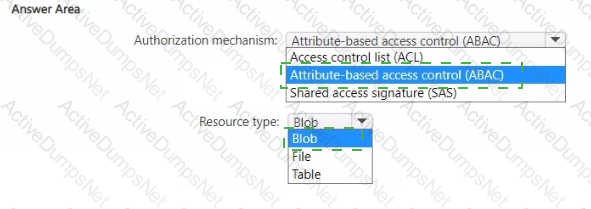
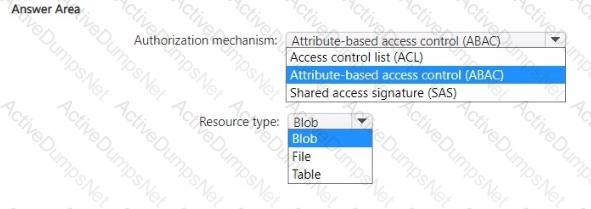
You have an Azure subscription.
You plan to deploy a storage account named storage1 that will store confidential data. You will assign tags to the confidential data.
You need to ensure that access to storage1 can be defined by using the assigned tags.
Which authorization mechanism should you enable, and which type of resource should you use to store the data? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
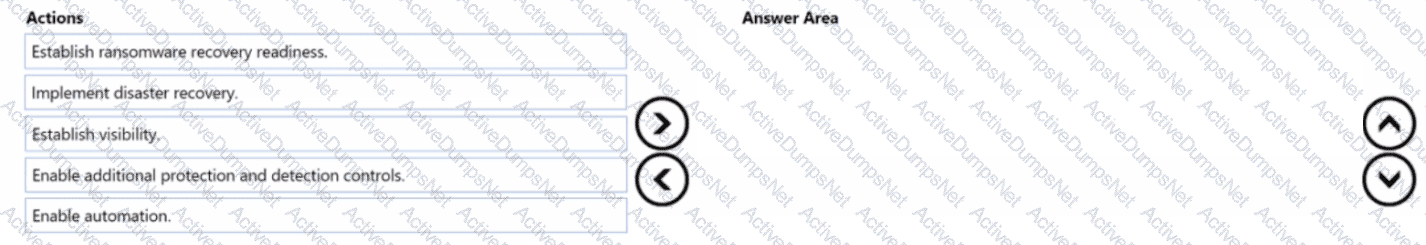
You are designing a ransomware response plan that follows Microsoft Security Best Practices.
You need to recommend a solution to minimize the risk of a ransomware attack encrypting local user files.
What should you include in the recommendation?
Your company has on-premises datacenters in Seattle, Chicago, and New York City.
You plan to migrate the on-premises workloads to the East US Azure region.
You need to design a governance solution for the management group hierarchy. The solution must be based on Microsoft Cloud Adoption Framework for Azure principles and must ensure that the hierarchy aligns with the Azure landing conceptual architecture.
What should you use to identify which archetype-aligned management groups to create beneath the landing zones management group?
You have a multicloud environment that contains an Azure subscription, an Amazon Web Services (AWS) subscription, and a Google Cloud Platform (GCP) subscription.
You plan to assess data security and compliance.
You need to design a Compliance Manager solution that meets the following requirements:
• Provides recommended improvement actions that include detailed implementation guidance
• Automatically monitors regulatory compliance
• Minimizes administrative effort
What should you include in the solution?
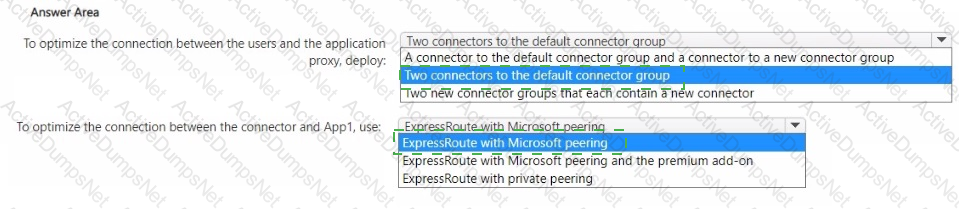
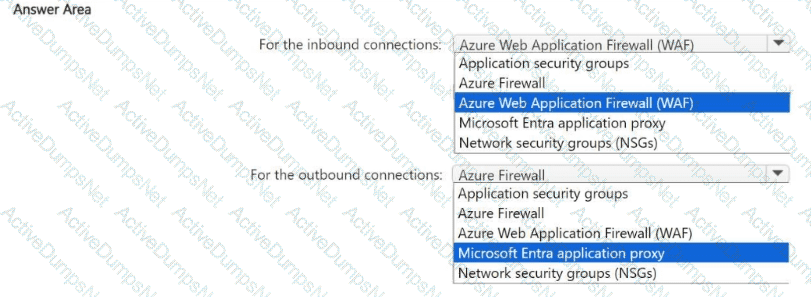
You have an Azure subscription that contains a virtual network named VNet1. VNet1 contains a 10-node virtual machine scale set that hosts a web search app named App1. Customers access App1 from the internet. The nodes establish outbound HTTP and HTTPS connections to the internet.
You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Inbound connections to App1 that contain security threats specified in the Core Rule. Set (CRS) from the Open Web Application Security Project (OWASP) must be blocked.
• Outbound HTTP and HTTPS connections from the virtual machine scale set that contain security threats identified by the Microsoft Defender Threat Intelligence (Defender Tl) feed must be blocked.
What should you include in the recommendation? To answer, select the options in the answer area,
NOTE: Each correct answer is worth one point.
You have a Microsoft 365 subscription that syncs with Active Directory Domain Services (AD DS).
You need to define the recovery steps for a ransomware attack that encrypted data in the subscription The solution must follow Microsoft Security Best Practices.
What is the first step in the recovery plan?
Your company is developing a new Azure App Service web app. You are providing design assistance to verify the security of the web app.
You need to recommend a solution to test the web app for vulnerabilities such as insecure server configurations, cross-site scripting (XSS), and SQL injection. What should you include in the recommendation?
You have a Microsoft 365 E5 subscription.
You plan to deploy Global Secure Access universal tenant restrictions v2.
Which authentication plane resources and which data plane resources will be protected? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have an Azure subscription
You plan to deploy multiple containerized microservice-based apps to Azure Kubemetes Service (AKS)
You need to recommend a solution that meets the following requirements:
• Manages secrets
• Provides encryption
• Secures service-to-service communication by using mTLS encryption
• Minimizes administrative effort
What should you include in the recommendation?
You have a Microsoft 365 tenant named contoso.com.
You need to ensure that users can authenticate only to contoso.com. The solution must meet the following requirements:
• Prevent the users from authenticating to other Microsoft 365 tenants.
• Minimize administrative effort.
What should you use?
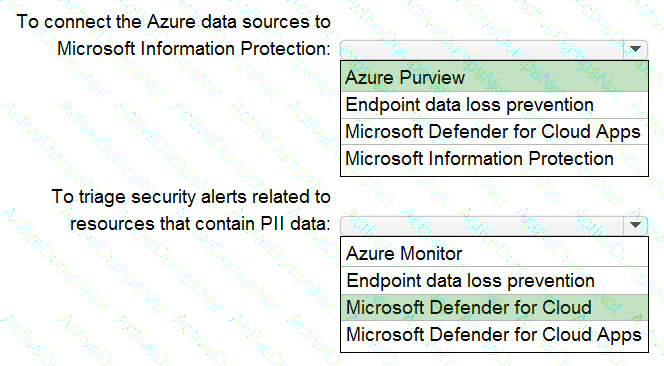
Your company is migrating data to Azure. The data contains Personally Identifiable Information (Pll). The company plans to use Microsoft Information Protection for the Pll data store in Azure. You need to recommend a solution to discover Pll data at risk in the Azure resources.
What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
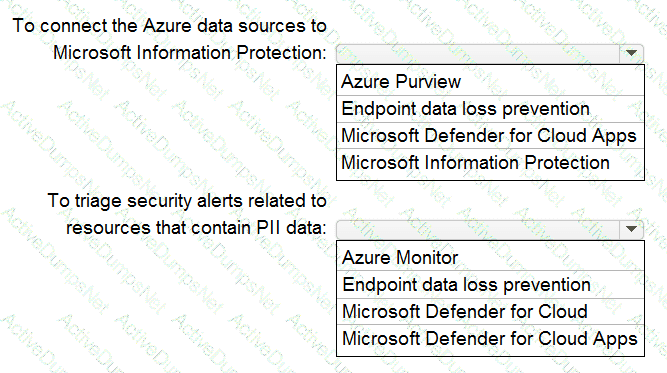
You have a Microsoft 365 subscription.
You are designing a user access solution that follows the Zero Trust principles of the Microsoft Cybersecurity Reference Architectures (MCRA).
You need to recommend a solution that automatically restricts access to Microsoft Exchange Online. SharePoint Online, and Teams m near-real-lime (NRT) in response to the following Azure AD events:
• A user account is disabled or deleted
• The password of a user is changed or reset.
• All the refresh tokens for a user are revoked
• Multi-factor authentication (MFA) is enabled for a user
Which two features should you include in the recommendation? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
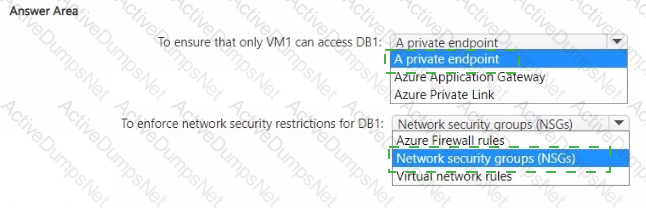
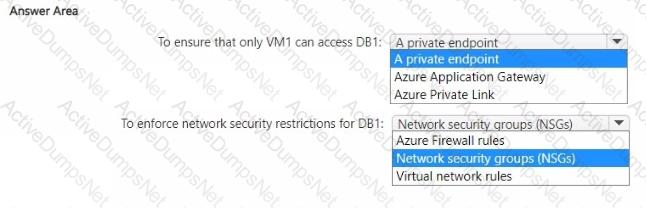
You have an Azure subscription that contains the resources shown in the following table.

You need to recommend a network security solution for App1. The solution must meet the following requirements:
• Only the virtual machines that are connected to Subnet1 must be able to connect to D81.
• DB1 must be inaccessible from the internet
• Costs must be minimized.
What should you include in the recommendation? To answer, select the options in the answer area. NOTE: Each correct answer is worth one point.
You have a Microsoft 365 subscription.
You need to design a solution to block file downloads from Microsoft SharePoint Online by authenticated users on unmanaged devices.
Which two services should you include in the solution? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Your company is preparing for cloud adoption.
You are designing security for Azure landing zones.
Which two preventative controls can you implement to increase the secure score? Each NOTE: Each correct selection is worth one point.
You have an Azure subscription that contains multiple Azure Blob Storage accounts.
You need to recommend a solution to detect threats in files after the files are uploaded to a blob container.
What should you include in the recommendation?
You need to recommend a solution for securing the landing zones. The solution must meet the landing zone requirements and the business requirements.
What should you configure for each landing zone?
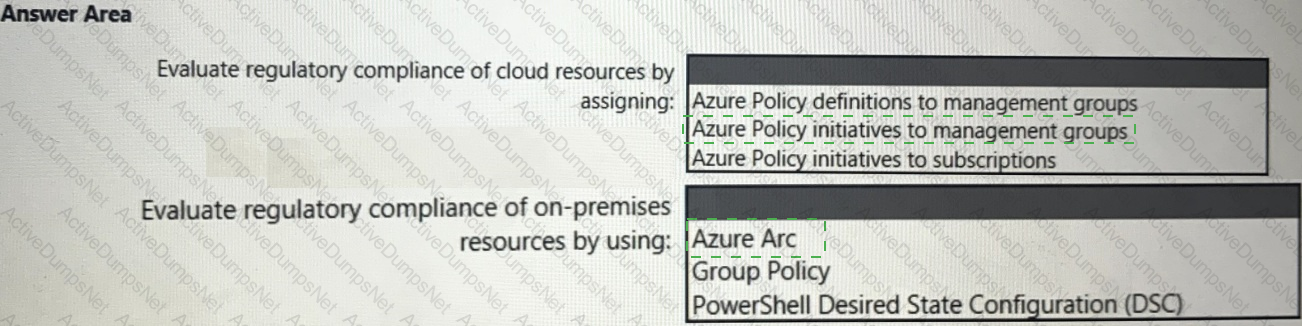
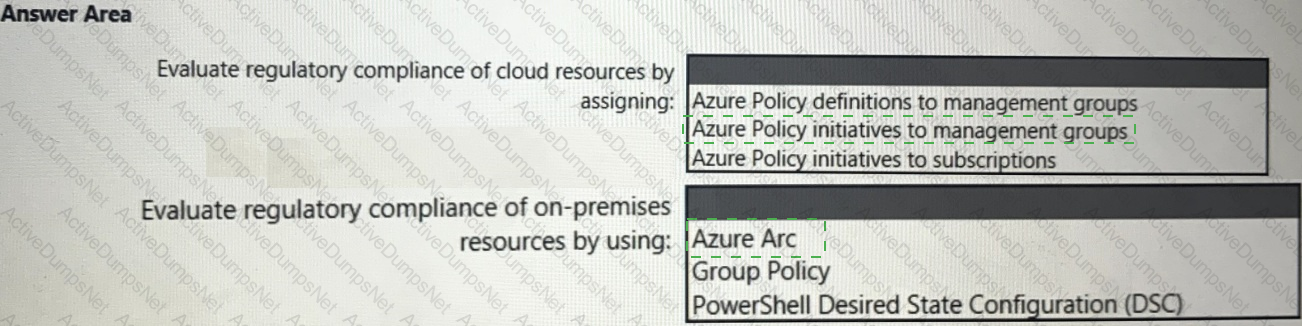
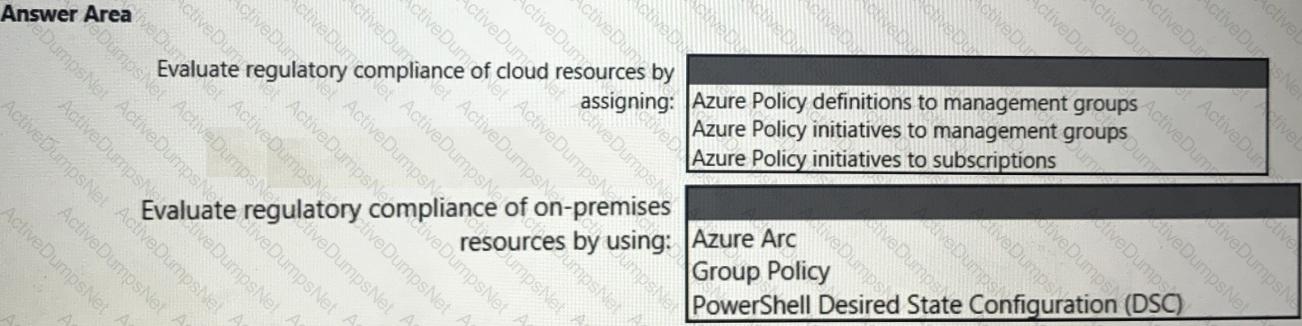
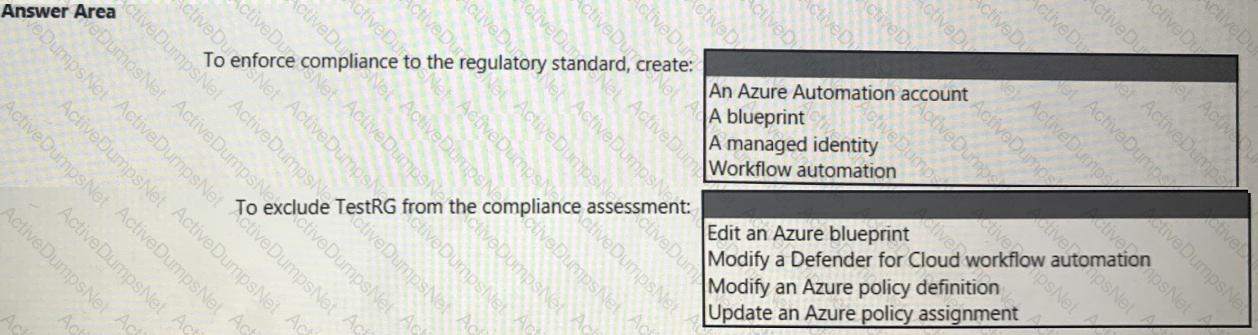
You need to recommend a solution to evaluate regulatory compliance across the entire managed environment. The solution must meet the regulatory compliance requirements and the business requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to design a strategy for securing the SharePoint Online and Exchange Online data. The solution must meet the application security requirements.
Which two services should you leverage in the strategy? Each correct answer presents part of the solution. NOTE; Each correct selection is worth one point.
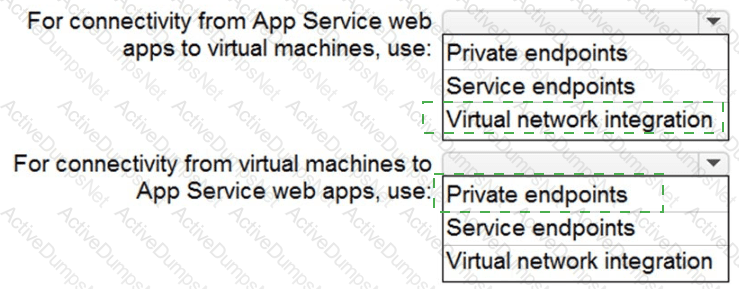
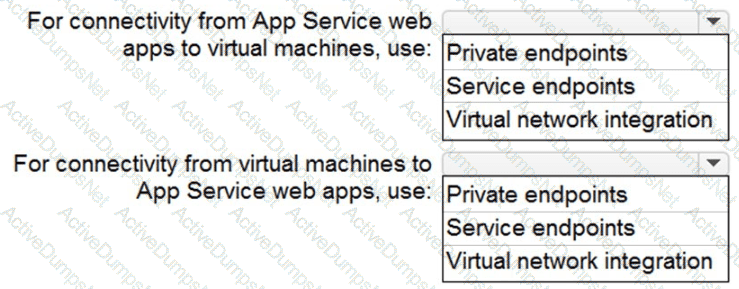
You need to recommend a strategy for App Service web app connectivity. The solution must meet the landing zone requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE Each correct selection is worth one point.
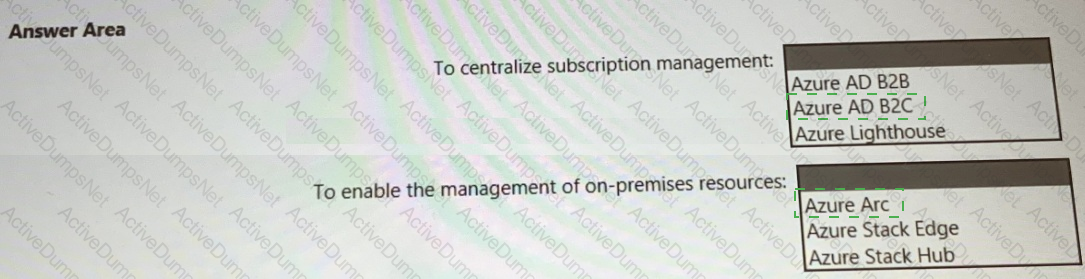
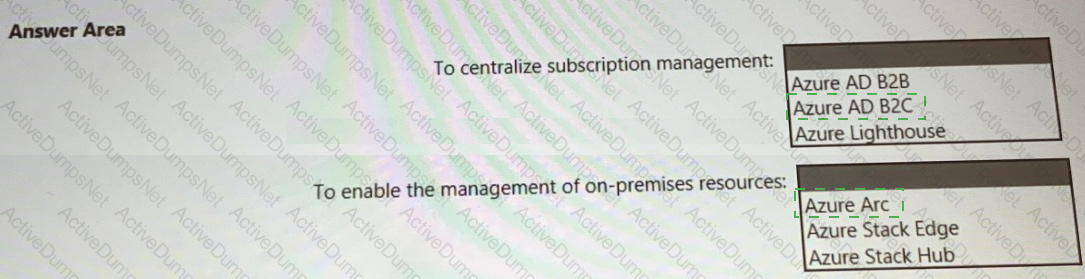
You need to recommend a multi-tenant and hybrid security solution that meets to the business requirements and the hybrid requirements. What should you recommend? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
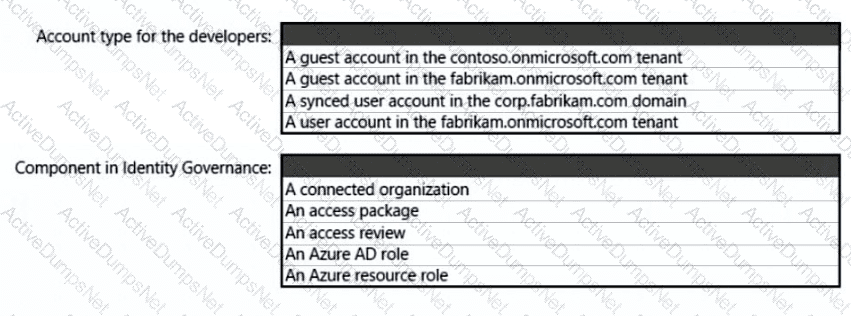
To meet the application security requirements, which two authentication methods must the applications support? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
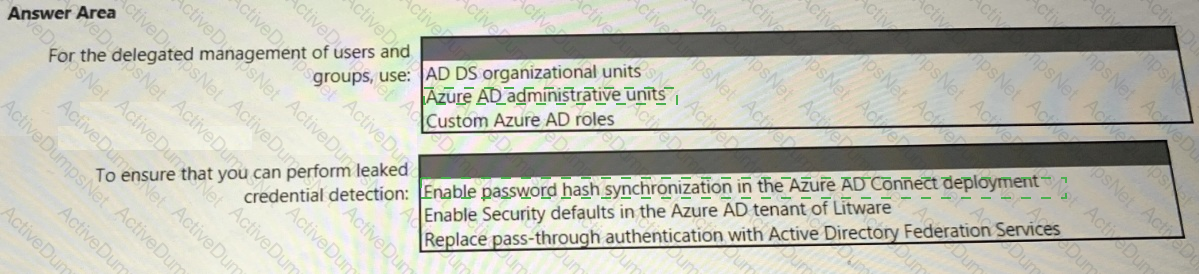
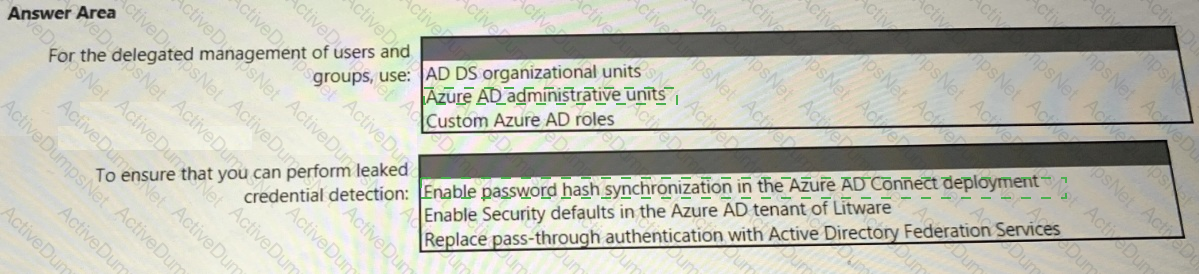
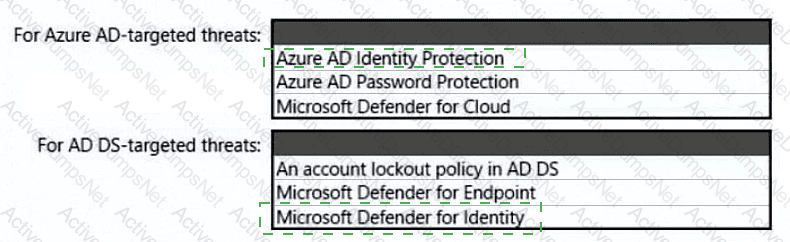
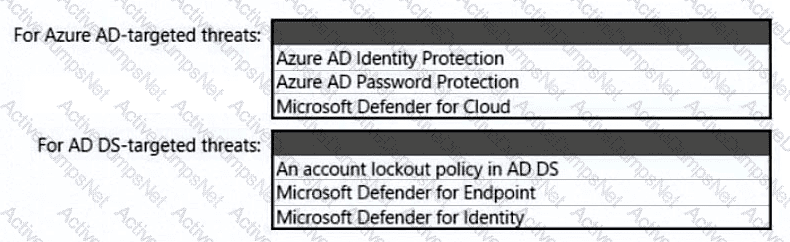
You need to recommend an identity security solution for the Azure AD tenant of Litware. The solution must meet the identity requirements and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
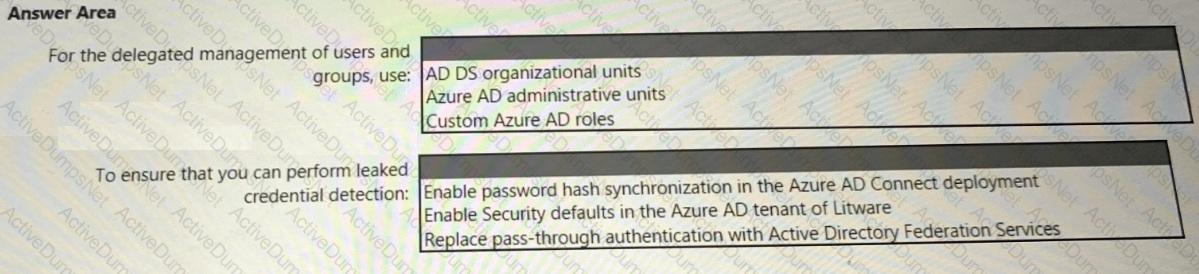
You need to recommend a strategy for securing the litware.com forest. The solution must meet the identity requirements. What should you include in the recommendation? To answer, select the appropriate options in the answer area. NOTE; Each correct selection is worth one point.
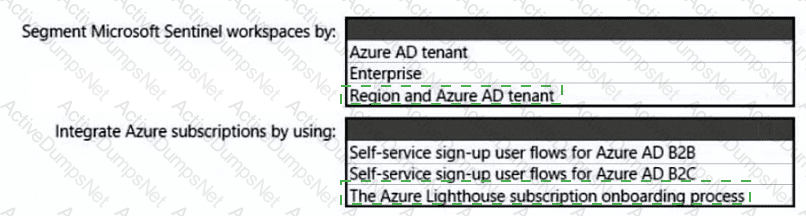
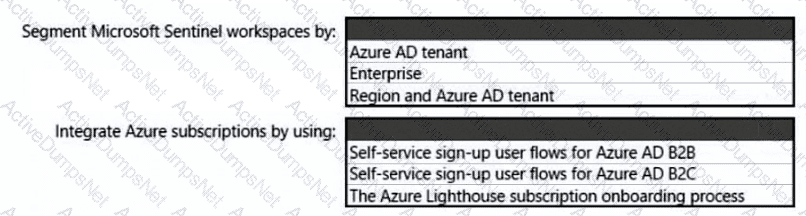
You need to recommend a SIEM and SOAR strategy that meets the hybrid requirements, the Microsoft Sentinel requirements, and the regulatory compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
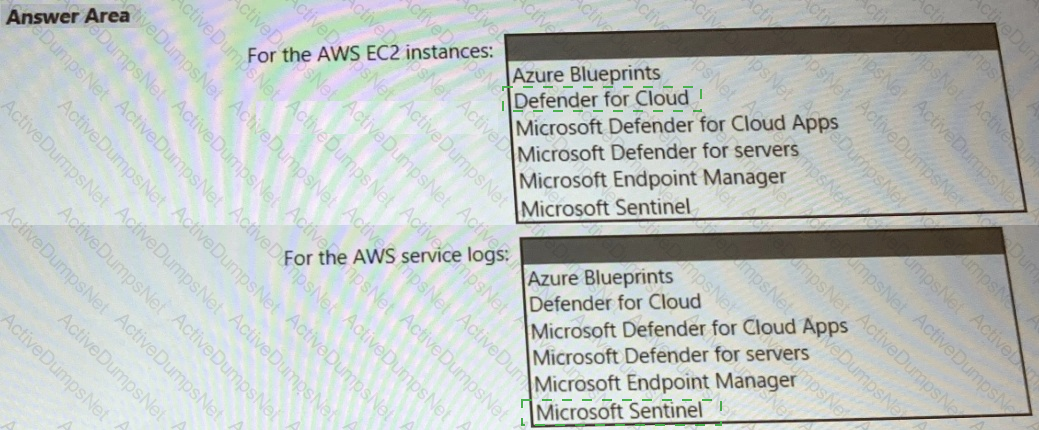
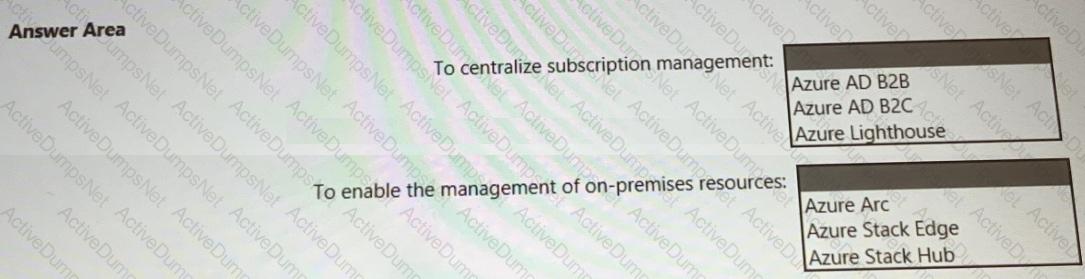
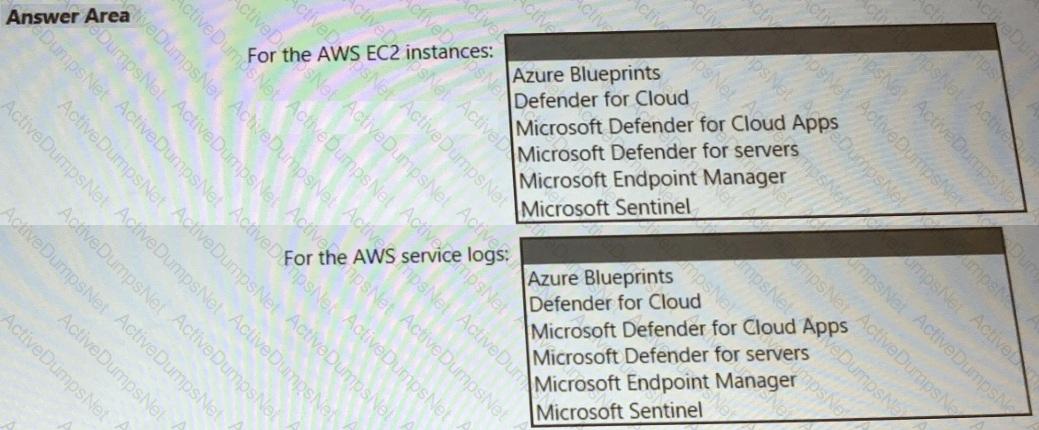
You need to recommend a solution to meet the AWS requirements.
What should you include in the recommendation? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
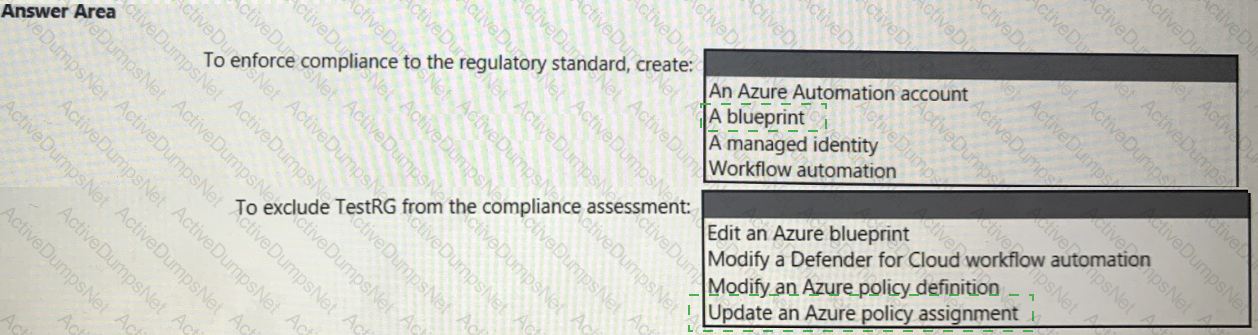
You need to recommend a solution to meet the compliance requirements.
What should you recommend? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to secure the MedicalHistory data in the ClaimsDetail table. The solution must meet the Contoso developer requirements.
What should you include in the recommendation?
You need to recommend a solution to resolve the virtual machine issue. What should you include in the recommendation? (Choose Two)
You need to recommend a solution to meet the security requirements for the virtual machines.
What should you include in the recommendation?
You need to recommend a solution to meet the security requirements for the InfraSec group.
What should you use to delegate the access?
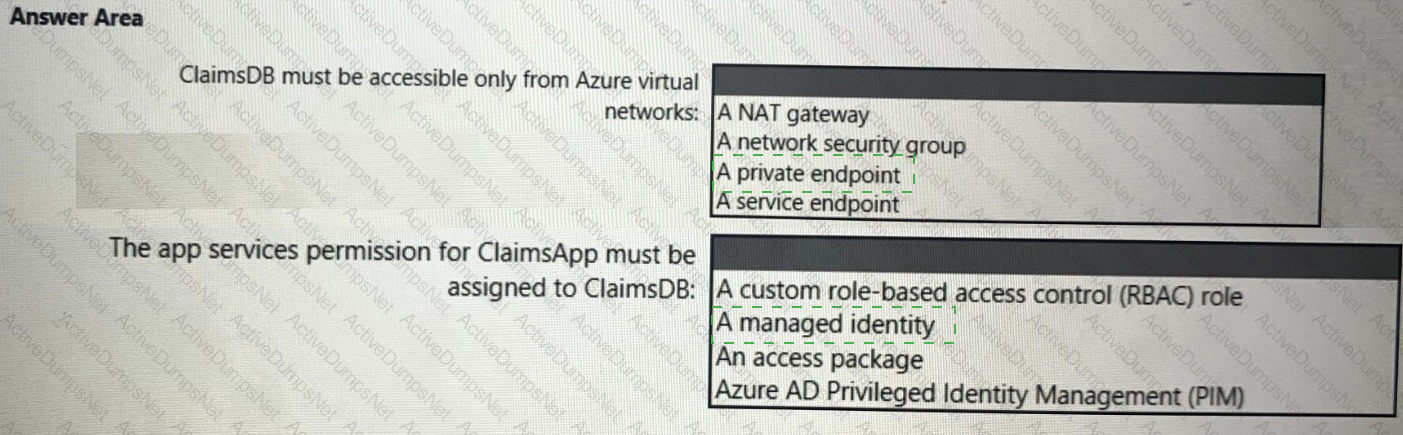
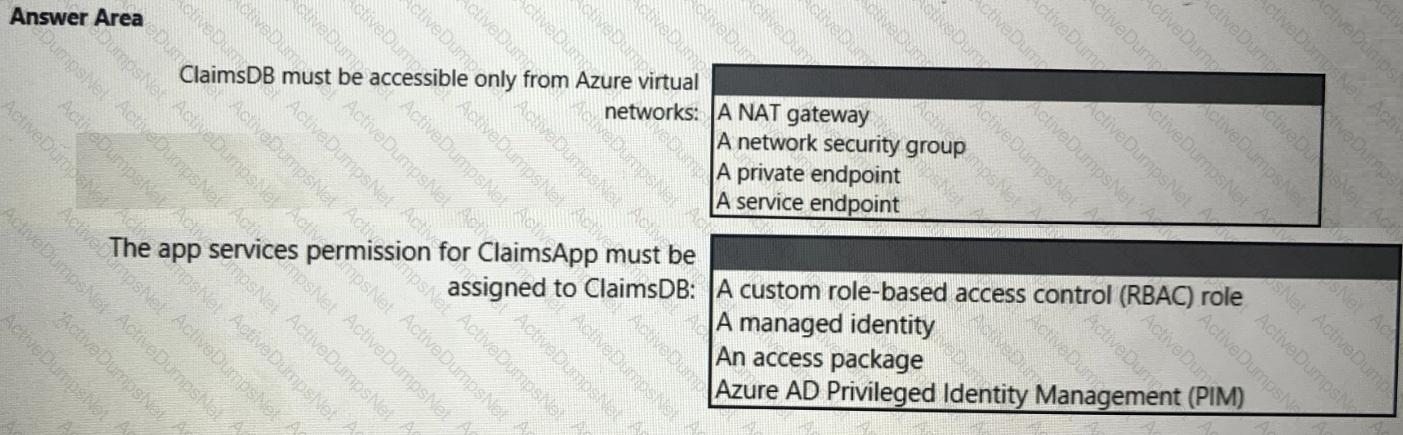
You need to recommend a solution to meet the requirements for connections to ClaimsDB.
What should you recommend using for each requirement? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You need to recommend a solution to scan the application code. The solution must meet the application development requirements. What should you include in the recommendation?
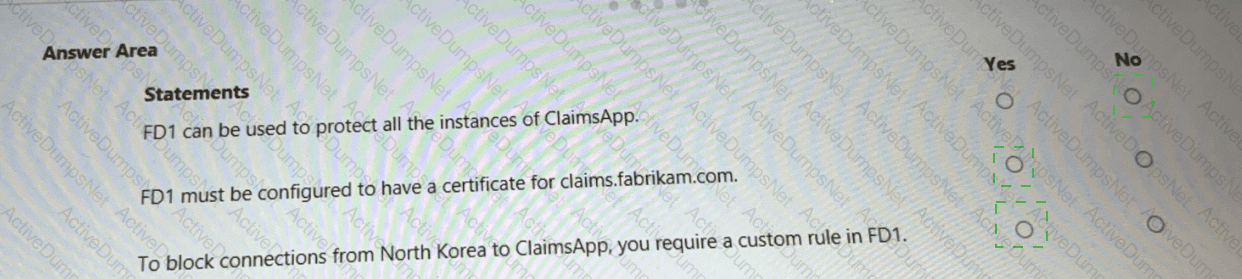
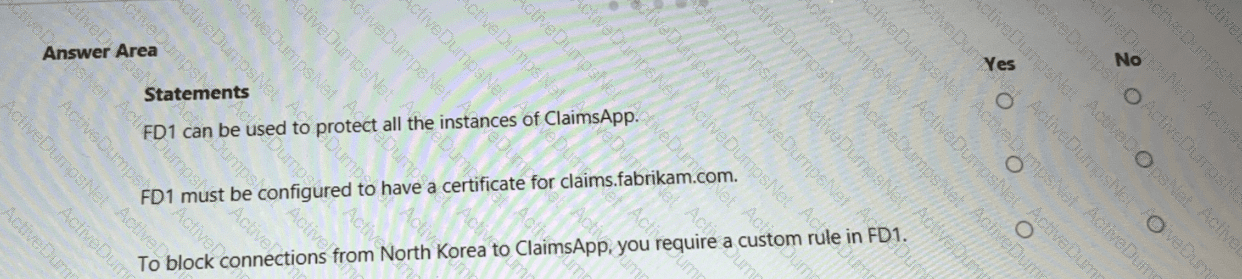
You are evaluating the security of ClaimsApp.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE; Each correct selection is worth one point.
What should you create in Azure AD to meet the Contoso developer requirements?