Juniper JN0-637 Security, Professional (JNCIP-SEC) Exam Practice Test
Security, Professional (JNCIP-SEC) Questions and Answers
Click the Exhibit button.
Referring to the exhibit, which two statements are true? (Choose two.)
You need to generate a certificate for a PKI-based site-to-site VPN. The peer is expecting to
user your domain name vpn.juniper.net.
Which two configuration elements are required when you generate your certificate request? (Chose two,)
Which two statements are correct about automated threat mitigation with Security Director? (Choose two.)
Referring to the exhibit, you have been assigned the user LogicalSYS1 credentials shown in
the configuration.
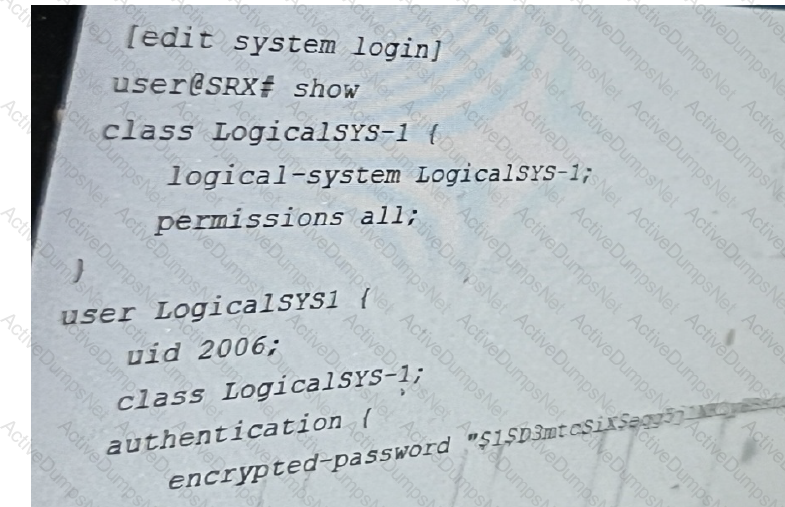
In this scenario, which two statements are correct? (Choose two.)
You are using trace options to troubleshoot a security policy on your SRX Series device.
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit:
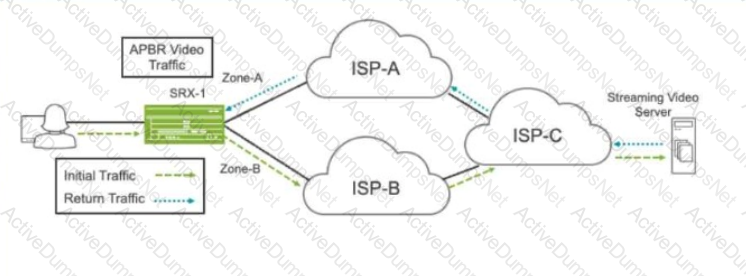
Referring to the exhibit, a default static route on SRX-1 sends all traffic to ISP-A. You have configured APBR to send all requests for streaming video traffic to ISP-B. However, the return traffic from the streaming video server is coming through ISP-A, and the traffic is being dropped by SRX-1. You can only make changes on SRX-1.
How do you solve this problem?
A user reports that a specific application is not working properly. This application makes
multiple connection to the server and must have the same address every time from a pool and this behavior needs to be changed.
What would solve this problem?
Exhibit:
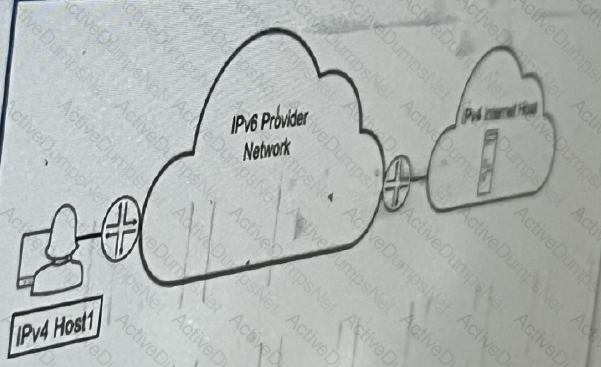
Referring to the exhibit, which technology would you use to provide communication between
IPv4 host1 and ipv4 internal host
You are deploying OSPF over IPsec with an SRX Series device and third-party device using GRE.
Which two statements are correct? (Choose two.)
You configured two SRX series devices in an active/passive multimode HA setup.
In this scenario, which statement is correct?
Which two statements about transparent mode and Ethernet switching mode on an SRX series
device are correct.
Referring to the exhibit, you are assigned the tenantSYS1 user credentials on an SRX series
device.
In this scenario, which two statements are correct? (Choose two.)
Exhibit:

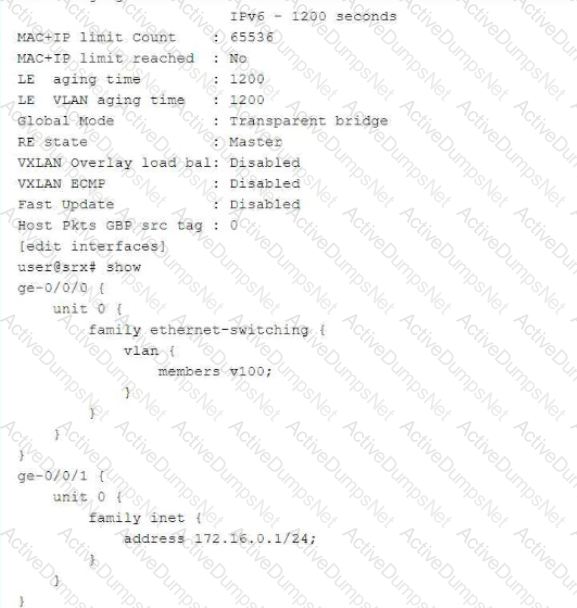
In which mode is the SRX Series device?
You have configured the backup signal route IP for your multinode HA deployment, and the ICL link fails.
Which two statements are correct in this scenario? (Choose two.)
You are deploying IPsec VPNs to securely connect several enterprise sites with ospf for dynamic
routing. Some of these sites are secured by third-party devices not running Junos.
Which two statements are true for this deployment? (Choose two.)
Exhibit:
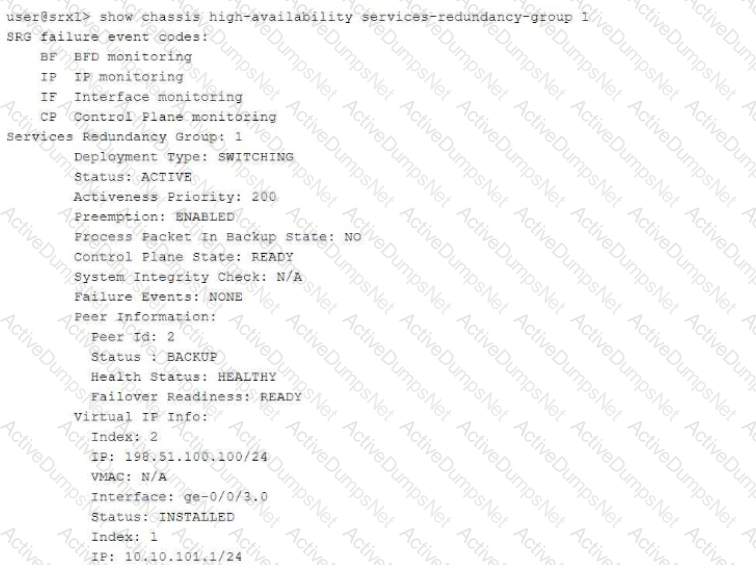
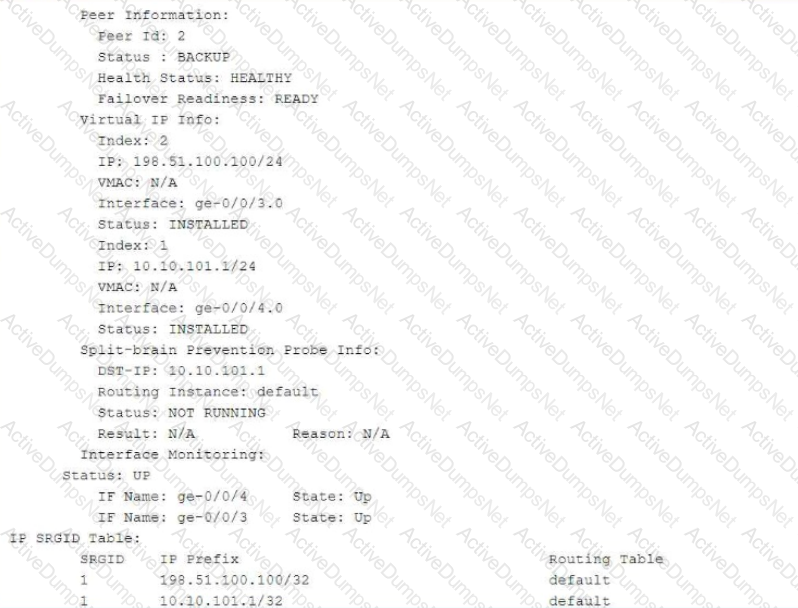
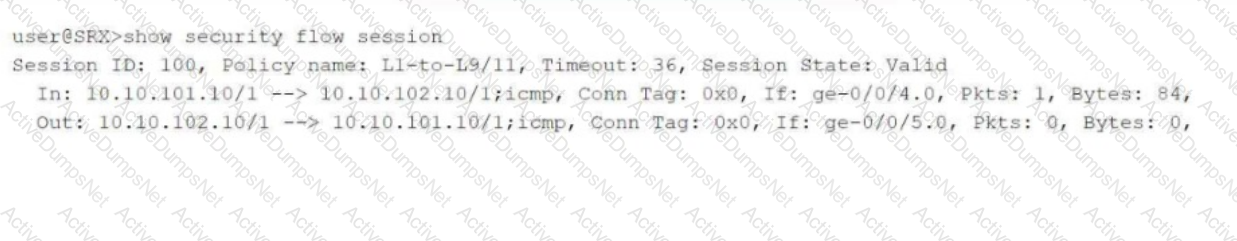
Referring to the exhibit, which two statements are correct? (Choose two.)
You are configuring an interconnect logical system that is configured as a VPLS switch to allow two logical systems to communicate.
Which two parameters are required when configuring the logical tunnel interfaces? (Choose two.)
Exhibit:
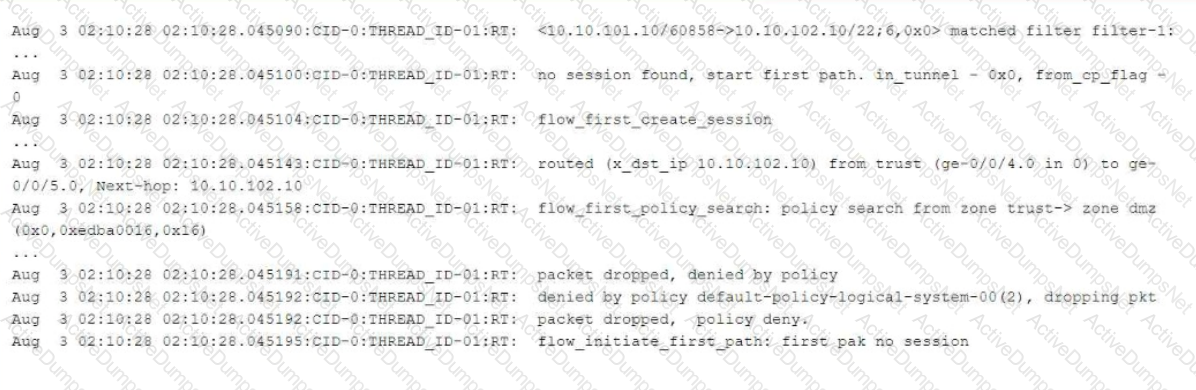
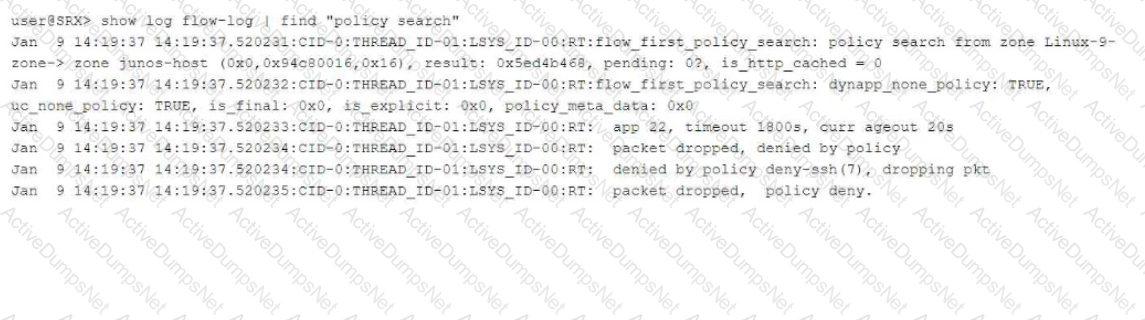
Referring to the flow logs exhibit, which two statements are correct? (Choose two.)
How does an SRX Series device examine exception traffic?
Exhibit:
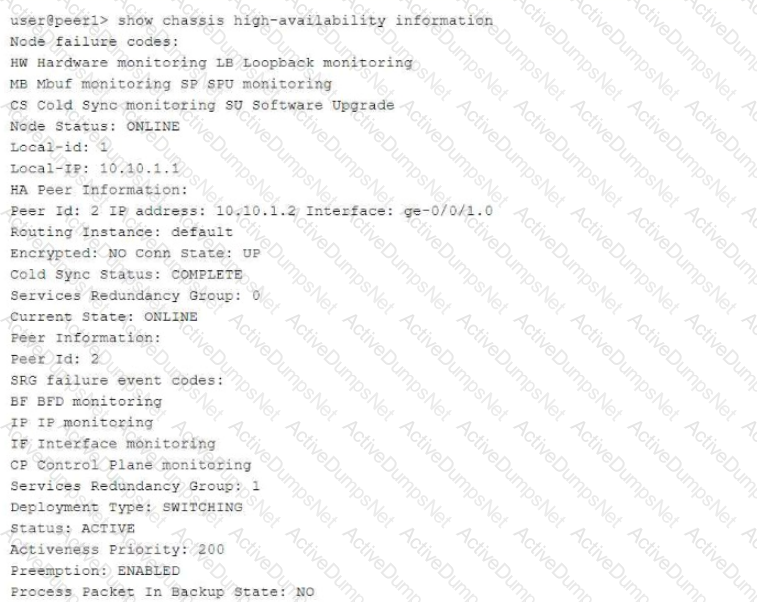
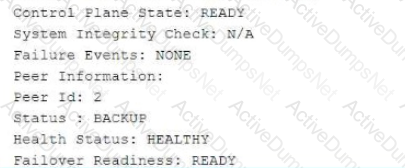
Referring to the exhibit, which statement is true?
Which encapsulation type must be configured on the lt-0/0/0 logical units for an interconnect
logical systems VPLS switch?
Which two statements are correct about mixed mode? (Choose two.)
Exhibit:
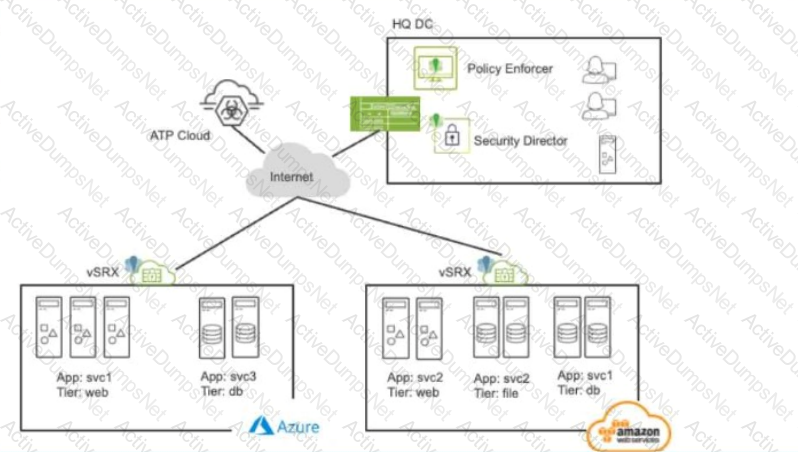
Referring to the exhibit, what do you use to dynamically secure traffic between the Azure and AWS clouds?
You have a multinode HA default mode deployment and the ICL is down.
In this scenario, what are two ways that the SRX Series devices verify the activeness of their peers? (Choose two.)
Your customer needs embedded security in an EVPN-VXLAN solution.
What are two benefits of adding an SRX Series device in this scenario? (Choose two.)
You are attempting to ping an interface on your SRX Series device, but the ping is unsuccessful.
What are three reasons for this behavior? (Choose three.)
Referring to the exhibit,
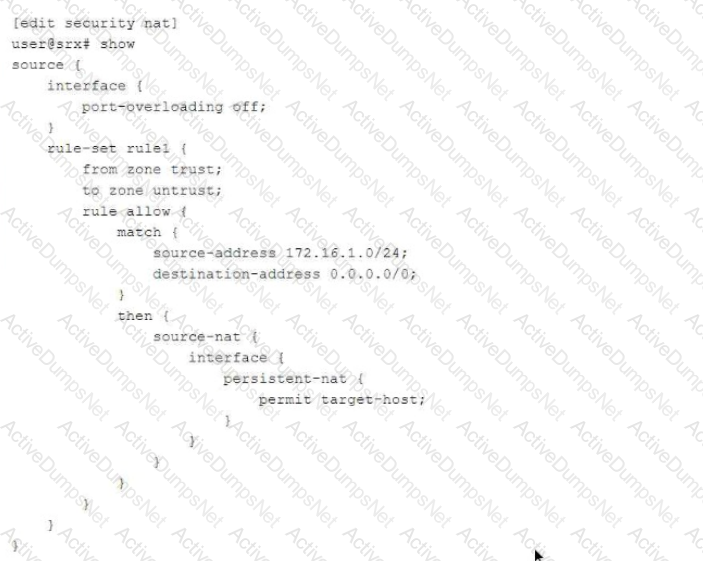
which two statements are correct about the NAT configuration? (Choose two.)
Exhibit:

You have configured a CoS-based VPN that is not functioning correctly.
Referring to the exhibit, which action will solve the problem?
You are configuring advanced policy-based routing. You have created a static route with next
hop of an interface in your inet.0 routing table
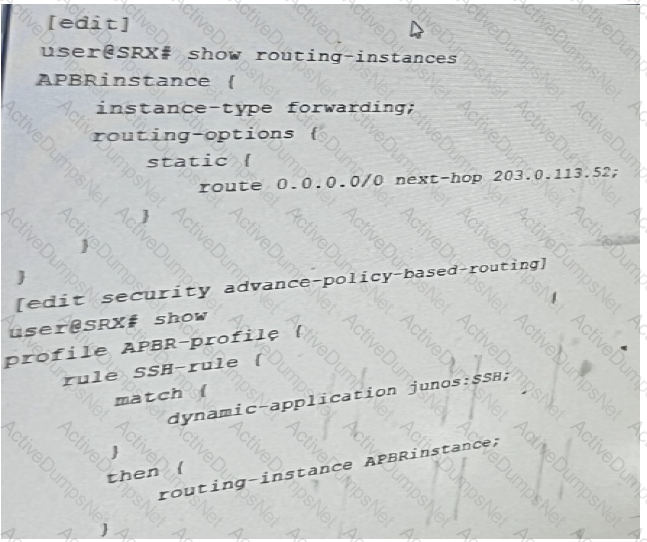

Referring to the exhibit, what should be changed to solve this issue?
You are asked to see if your persistent NAT binding table is exhausted.
Which show command would you use to accomplish this task?
You have deployed an SRX Series device at your network edge to secure Internet-bound sessions for your local hosts using source NAT. You want to ensure that your users are able to interact with applications on the Internet that require more than one TCP session for the same application session.
Which two features would satisfy this requirement? (Choose two.)
Click the Exhibit button.
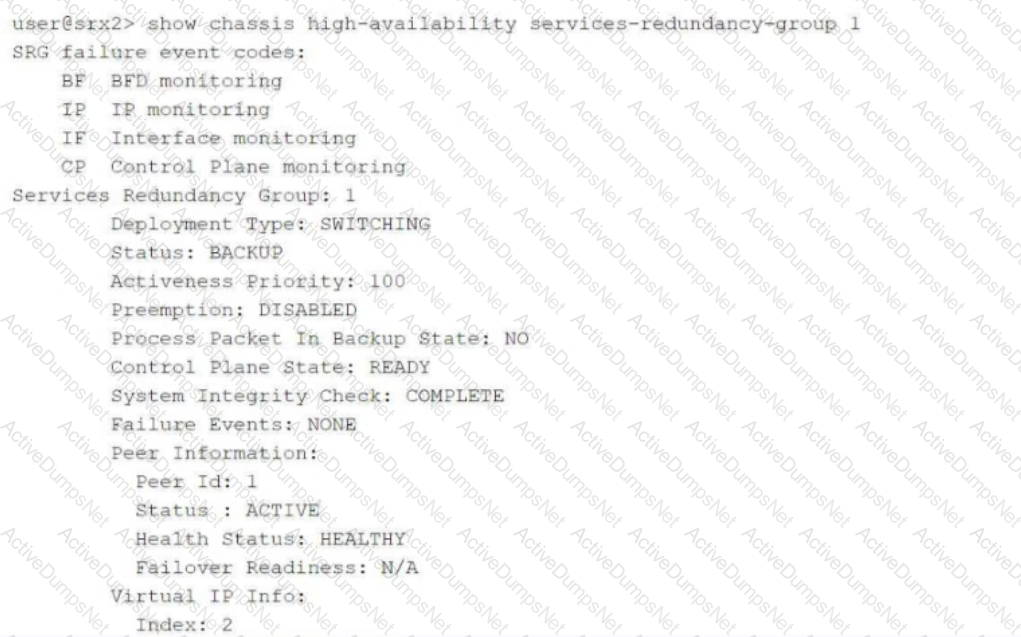
Referring to the exhibit, which two statements are correct? (Choose two.)
You are asked to establish IBGP between two nodes, but the session is not established. To troubleshoot this problem, you configured trace options to monitor BGP protocol message exchanges.


Referring to the exhibit, which action would solve the problem?
The SRX series device is performing static NAT. you want to ensure that host A can reach the
internal webserver www.juniper.net using domain name.
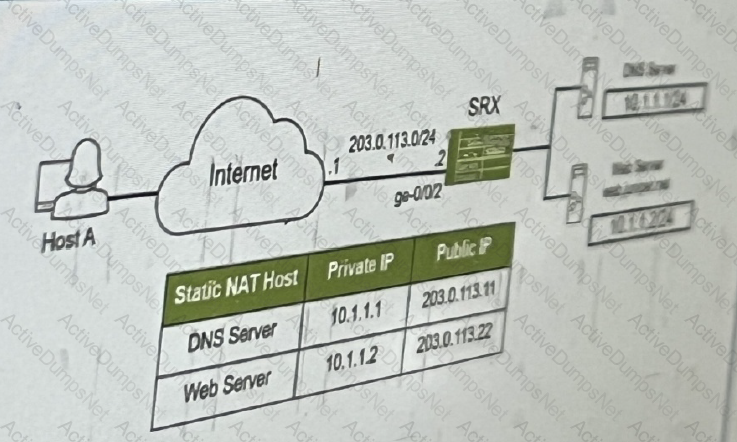
Referring to the exhibit, which two Junos features are required to accomplish this task? (Choose two.)
