Juniper JN0-335 Security, Specialist (JNCIS-SEC) Exam Practice Test
Security, Specialist (JNCIS-SEC) Questions and Answers
On an SRX Series firewall, what are two ways that Encrypted Traffic Insights assess the threat of the traffic? (Choose two.)
Click the Exhibit button.
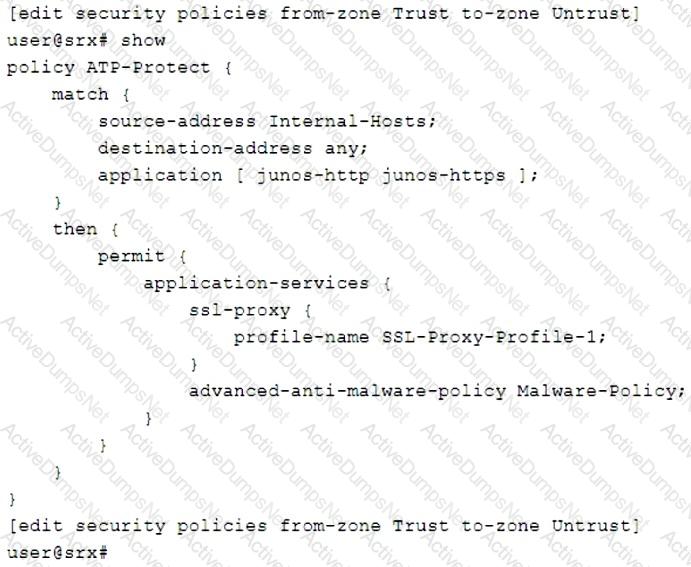
You are asked to create a security policy that will automatically add infected hosts to the infected hosts feed and block further communication through the SRX Series device.
What needs to be added to this configuration to complete this task?
Which two statements about unified security policies are correct? (Choose two.)
Which two features are configurable on Juniper Secure Analytics (JSA) to ensure that alerts are triggered when matching certain criteria? (Choose two.)
You are asked to determine how much traffic a popular gaming application is generating on your network.
Which action will you perform to accomplish this task?
You want to manually failover the primary Routing Engine in an SRX Series high availability cluster pair.
Which step is necessary to accomplish this task?
A client has attempted communication with a known command-and-control server and it has reached the configured threat level threshold.
Which feed will the clients IP address be automatically added to in this situation?
After JSA receives external events and flows, which two steps occur? (Choose two.)
You are implementing an SRX Series device at a branch office that has low bandwidth and also uses a cloud-based VoIP solution with an outbound policy that permits all traffic.
Which service would you implement at your edge device to prioritize VoIP traffic in this scenario?
Which two statements are true about application identification? (Choose two.)
While working on an SRX firewall, you execute the show security policies policy-name
Which function does this command accomplish?
Your manager asks you to provide firewall and NAT services in a private cloud.
Which two solutions will fulfill the minimum requirements for this deployment? (Choose two.)
You want to permit access to an application but block application sub-Which two security policy features provide this capability? (Choose two.)
Which two statements are correct about SSL proxy server protection? (Choose two.)
You are deploying a new SRX Series device and you need to log denied traffic.
In this scenario, which two policy parameters are required to accomplish this task? (Choose two.)
What are two benefits of using a vSRX in a software-defined network? (Choose two.)
Which two statements are true about Juniper ATP Cloud? (Choose two.)
Exhibit
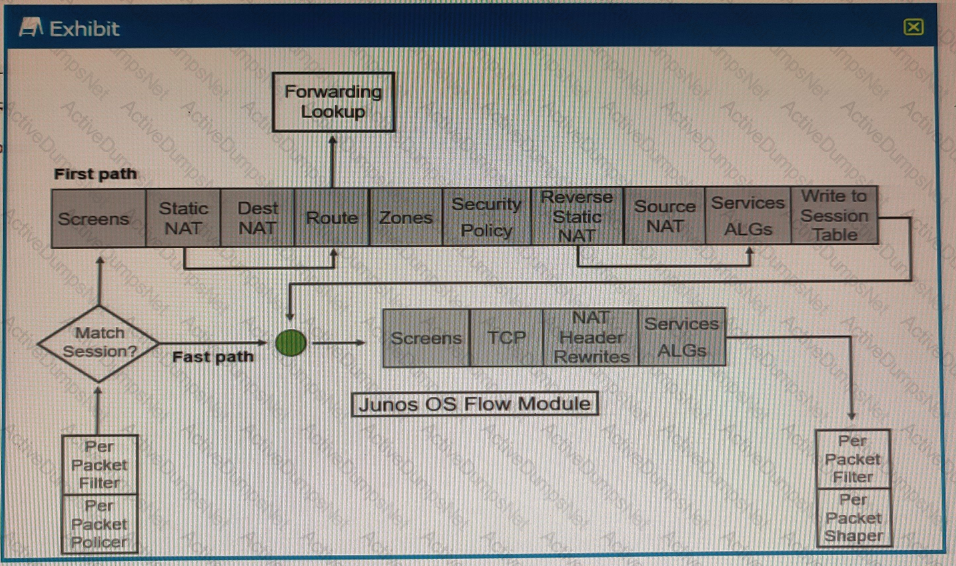
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
Which two functions does Juniper ATP Cloud perform to reduce delays in the inspection of files? (Choose two.)
You are asked to find systems running applications that increase the risks on your network. You must ensure these systems are processed through IPS and Juniper ATP Cloud for malware and virus protection.
Which Juniper Networks solution will accomplish this task?
Which statement defines the function of an Application Layer Gateway (ALG)?
Your network uses a single JSA host and you want to implement a cluster.
In this scenario, which two statements are correct? (Choose two.)
Exhibit
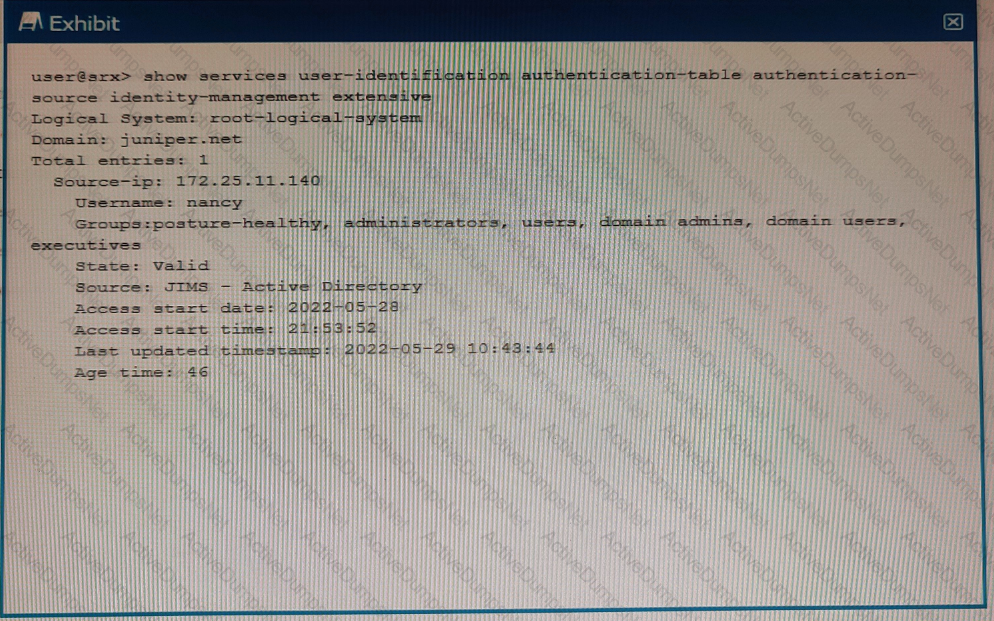
Referring to the exhibit, which two statements are true? (Choose two.)
Your company is using the Juniper ATP Cloud free model. The current inspection profile is set at 10 MB You are asked to configure ATP Cloud so that executable files up to 30 MB can be scanned while at the same time minimizing the change in scan time for other file types.
Which configuration should you use in this scenario?
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
Which two devices would you use for DDoS protection with Policy Enforcer? (Choose two.)
What are two types of system logs that Junos generates? (Choose two.)
How does Juniper ATP Cloud protect a network from zero-day threats?
How does the SSL proxy detect if encryption is being used?
