IBM C1000-162 IBM Security QRadar SIEM V7.5 Analysis Exam Practice Test
IBM Security QRadar SIEM V7.5 Analysis Questions and Answers
Which two (2) statements regarding indexed custom event properties are true?
Which reference set data element attribute governs who can view its value?
During an active offense review, an analyst observed that a single source system generated a significant amount of high-rate traffic for transferring ^bound mail via port 25. The system responsible for this traffic was not authorized to function as a mail server.
lat is the correct action in this situation?
What Is the result of the following AQL statement?
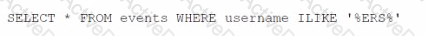
Which statement regarding the Assets tab is true?
What does this example of a YARA rule represent?
rule ibm_forensics : qradar
meta:
description = “Complex Yara rule.“
strings:
Shexl = {4D 2B 68 00 ?? 14 99 F9 B? 00 30 Cl 8D}
Sstrl = "IBM Security!"
condition:
Shexl and (#strl > 3)
Which property types can be used to reduce the overall data volume searched and shorten search time to address searches taking longer than expected?
Events can be exported from the QRadar Log Activity tab in which file formats?
After how much time will QRadar mark an Event offense dormant if no new events or flows occur?
When investigating an offense, how does one find the number of flows or events associated with it?
A Security Analyst has noticed that an offense has been marked inactive.
How long had the offense been open since it had last been updated with new events or flows?
What type of building blocks would you use to categorize assets and server types into CIDR/IP ranges to exclude or include entire asset categories in rule tests?
A QRadar analyst wants predefined searches, reports, custom rules, and custom properties for HIPAA compliance.
Which option does the QRadar analyst use to look for HIPAA compliance on QRadar?
New vulnerability scanners are deployed in the company's infrastructure and generate a high number of offenses. Which function in the Use Case Manager app does an analyst use to update the list of vulnerability scanners?

An analyst runs a search with correct AQL. but no errors or results are shown.
What is one reason this could occur?
A Security Analyst was asked to search for an offense on a specific day. The requester was not sore of the time frame, but had Source Host information to use as well as networks involved, Destination IP and username.
Which fitters can the Security Analyst use to search for the information requested?
An analyst wants to share a dashboard in the Pulse app with colleagues.
The analyst exports the dashboard by using which format?
What process is used to perform an IP address X-Force Exchange Lookup in QRadar?
a selection of events for further investigation to somebody who does not have access to the QRadar system.
Which of these approaches provides an accurate copy of the required data in a readable format?
Create a list that stores Username as the first key. Source IP as the second key with an assigned cidr data type, and Source Port as the value.
The example above refers to what kind of reference data collections?
Offense chaining is based on which field that is specified in the rule?
QRadar analysts can download different types of content extensions from the IBM X-Force Exchange portal. Which two (2) types of content extensions are supported by QRadar?
On the Offenses tab, which column explains the cause of the offense?
After analyzing an active offense where many source systems were observed connecting to a specific destination via local-to-local LDAP traffic, an ^lyst discovered that the targeted system is a legitimate LDAP server within the organization.
x avoid confusion in future analyses, how can this type of traffic to the target system be flagged as expected and be excluded from further offense ation?
On which lab can an analyst perform a "Flow Bias" Quick Search?
Which QRadar component provides the user interface that delivers real-time flow views?
What are two (2) Y-axis types that are available in the scatter chart type in the Pulse app?
When examining lime fields on Event Information, which one represents the time QRadar received the raw event?
The Use Case Manager app has an option to see MITRE heat map.
Which two (2) factors are responsible for the different colors in MITRE heat map?
Which IBM X-Force Exchange feature could be used to query QRadar to see if any of the lOCs were detected for COVID-19 activities?
What type of reference data collection would you use to correlate a unique key to a value?
What does the Next Run Time column display when a report is queued for generation in QRadar?
An analyst wants to implement an AQL search in QRadar. Which two (2) tabs can be used to accomplish this implementation?
Reports can be generated by using which file formats in QRadar?
How do events appear in QRadar if there was an error in the JSON parser for a new log source to which a custom log source extension was created?
Which types of information does QRadar analyze to create an offense from the rule?
Which two (2) options are at the top level when an analyst right-clicks on the Source IP or Destination IP that is associated with an offense at the Offense Summary?
When searching for all events related to "Login Failure", which parameter should a security analyst use to filter the events?
A QRadar analyst wants to limit the time period for which an AOL query is evaluated. Which functions and clauses could be used for this?
How does a QRadar analyst get to more information about a MITRE entry in the Use Case Manager?
What does an analyst need to do before configuring the QRadar Use Case Manager app?

