Huawei H12-891_V1.0 HCIE-Datacom V1.0 Exam Practice Test
HCIE-Datacom V1.0 Questions and Answers
The Ingress VTEP performs both Layer 2 and Layer 3 table lookup for packet forwarding. The forwarding mode is _____ IRB forwarding. (Capitalize the first letter.)
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
Which of the following statements is correct about 6PE and 6VPE?
As shown in the figure, when PE1 receives an ARP request packet, it forwards the packet to PE4. The packet then carries two labels. The label value 201 is carried by the EVPN Type ____ route. (Enter only digits.)
iMaster NCE-Campus restricts RESTful APIs. If a client sends aGET requestthat invokes a RESTful API to obtain site information from iMaster NCE-Campus, which of the following fields should be included in the request header?
A network administrator runs the display telemetry subscription command on a device to check telemetry subscription information. The command output is as follows. Which of the following statements is incorrect?
[~CE] display telemetry subscription
Sub name : Sub1
Sensor group:
Sensor-name Sample-interval(ms) State
Sensor1 1000 RESOLVED
Destination group:
Dest-name Dest-IP Dest-port State Vpn-name Protocol
Dest1 192.168.56.1 20030 RESOLVED - GRPC
Sub state : PASSIVE
Total subscription number is : 1
Port isolation can be deployed on an Ethernet network to implement both Layer 2 communication and Layer 3 isolation, making the networking more flexible.
TheNETCONF content layercontainsdevice configuration data.
Which of the following statements are correct about the followingNETCONF configuration?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following fields is not carried in BGP EVPN Type 2 routes?
In a scenario whereSR Policiesare dynamically established through thecontroller, which of the following statements about theSR Policy solution architectureis incorrect?
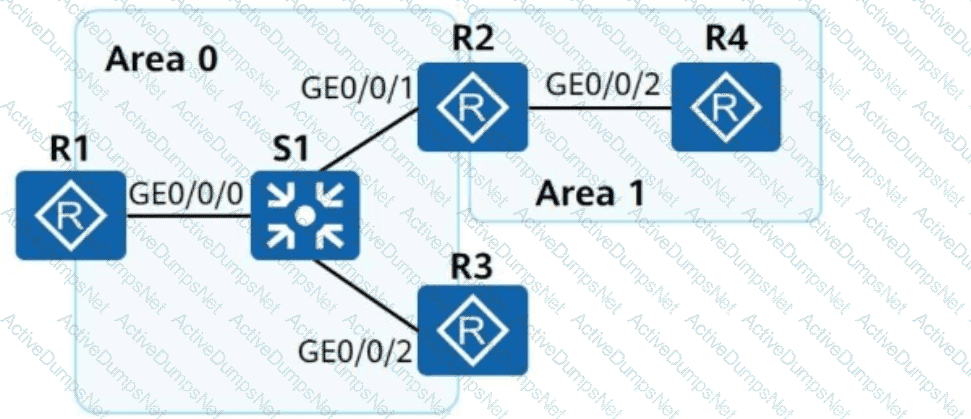
The following figure shows some configurations of R1. Based on these configurations, which of the following statements about IS-IS on R1 are correct?
isis 1
is-level level-2
cost-style wide
network-entity 49.0022.ee8c.a0c2.baf1.00
isis 2 vpn-instance tt
is-level level-2
cost-style wide
network-entity 47.00ce.390d.efdc.b3e1.00
isis 3 vpn-instance rr
is-level level-2
cost-style wide
network-entity 47.cc0a.3efb.bbdd.aae1.00
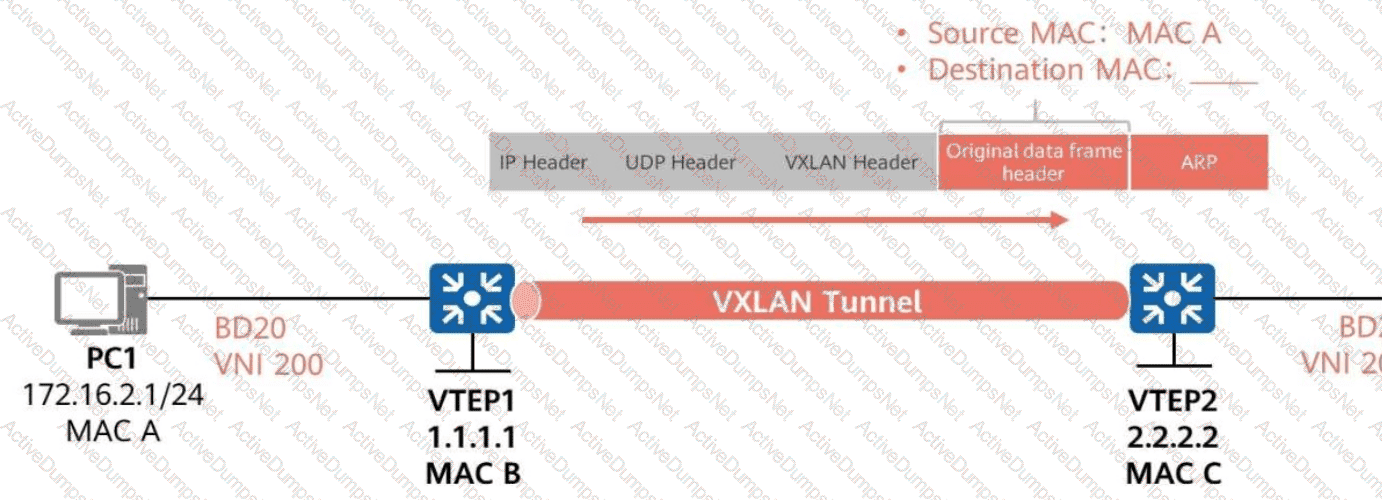
As shown in the figure,ARP broadcast suppression is enabled on VTEP1inBD 20 (VNI 200).
VTEP1 learns ARP informationaboutPC2 through BGP EVPN routes.
WhenVTEP1 forwards the ARP request for PC1’s MAC address to VTEP2,
What is the destination MAC address of the inner data frame?
Which of the following languages is integrated into the OPS?
In thesmall and midsize campus network designbased on theHuawei CloudCampus Solution, when over100 branchesneed to communicate with each other, which of the following interconnection networking models is recommended?
Which of the following can be used to transmit traffic to a VXLAN network and implement intra-subnet communication on the same VXLAN network?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, run the command on the VTEP to view BGP EVPN routes. The route entries shown in the following figure are displayed. Which of the following statements about these routing entries are correct?
Network (EthTagId/IP Prefix/IP PrefixLen)
NextHop
*>i 0:172.16.2.0:24 1.1.1.2
*>i 0:172.16.13.0:24 1.1.1.2
*>i 0:192.168.122.0:30 1.1.1.2
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following fields is NOT carried in BGP EVPN Type 5 routes?
In the Huawei CloudCampus Solution, which of the following deployment modes are supported by Huawei switches?
An engineer needs todownload the configuration file vrpcfg.cfgto a local device throughSFTP, rename the configuration file to backup.cfg, and upload it to thedefault directory of the device.
The configuration file is located at /vrpcfg.cfg (default directory of the remote device), and the local directory is C:\.
Which of the followingPython Paramikocode lines can implement the required operations?
Which of the following channels are involved in the Huawei SD-WAN Solution?
The command can be run to completely isolate Layer 2 and Layer 3 of different interfaces in a VLAN. (Use lowercase letters to supplement the command, which cannot be abbreviated.)
Refer to the following command output on the router R3. Which of the following statements are correct?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:26 UTC-08:00
Description: HUAWEI, AR Series, Tunnel0/0/0 Interface
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.2/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.3.3 (LoopBack0), destination 10.0.1.1
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
During the configuration of L3VPNv4 over SRv6 BE, if an RR is deployed in the SR domain, which command must be run on the RR to ensure that the PEs at both ends can correctly learn VPNv4 routes?
In the firewall hot standby scenario, when VGMP works in load balancing mode, which of the following functions must be enabled on the firewalls to prevent the return traffic from being discarded because it does not match any session entry in the case of inconsistent forward and return paths?
VLAN-based MAC address flapping detection is configured. If MAC address flapping occurs, actions to be taken on an interface can be configured as required. Which of the following actions cannot be configured?
Which of the following methods can be used to establish IPsec SAs? (Select All that Apply)
The following figure shows the inter-AS MPLS L3VPN Option C (Solution 2). ASBR-PE2 is connected to CE3 and runs eBGP.
To enable all CEs to communicate with each other, which of the following address families must peer relationships be enabled in the BGP process of ASBR-PE2?
Which of the following number sequences can be matched by the regular expression 100.s?
To obtain thetoken IDofiMaster NCE, you need to send anHTTP requestusing the followingPython codeto invoke aniMaster NCE RESTful API:
Which of the following statements isincorrect?
In OSPF, an ABR translates all Type 7 LSAs in a Not-So-Stubby Area (NSSA) into Type 5 LSAs.
As shown in the figure, what is known about the default routes on R4?
Routing Table on R4:
Destination/Mask Proto Pre Cost Flags NextHop Interface
0.0.0.0/0 ISIS-L1 15 10 D 10.1.24.1 GigabitEthernet0/0/1
ISIS-L1 15 10 D 10.1.34.1 GigabitEthernet0/0/0
172.16.1.2/32 ISIS-L1 15 10 D 10.1.24.1 GigabitEthernet0/0/1
172.16.1.3/32 ISIS-L1 15 10 D 10.1.34.1 GigabitEthernet0/0/0
SR-MPLS uses IGP extensions to advertise labels and reserve bandwidth to support high-bandwidth services.
Which of the following statements regarding RT are correct?
MPLS supports forwarding equivalence class (FEC). Which of the following cannot be used as an FEC allocation standard?
In the figure,SR-MPLSis enabled onR1, R2, and R3. TheSRGB (Segment Routing Global Block) rangeonR3is from20000 to 21000, and theprefix SID indexconfigured on theloopback1 interface of R3 is 30.
In this case, theMPLS label corresponding to the loopback1 interface of R3 is _____.
(Enter anArabic numeralwithout symbols.)
AH is an IP-based transport-layer protocol. The protocol number is _____. (Enter only digits.)
Which of the following are carried in the HTTP/1.1 response header?
When static IPsec VPN is used for WAN interconnection in the Huawei CloudCampus Solution, the AP, Router, and _____ can be used as egress devices. (Use full spelling with the first letter capitalized.)
Which of the following statements is incorrect about the user authentication points on the network?
Congestion management technology can be used to discard data packets in the buffer queue to prevent the buffer queue from being exhausted.
By default, the domain ID of an OSPF process is the same as the process ID. You can run the domain-id command in the OSPF process view to change a domain ID.
To deploy a virtual campus network using iMaster NCE-Campus, the following steps are performed. From top to bottom, sort the steps in the order in which they occur during network deployment and management.
Which of the following statements are correct about the command:
ping -aX -cY -sZ -vpn-instance M 10.5.16.2
On acampus network,iMaster NCE-Campusis used to deploy twoVNs (Virtual Networks):R&D VNandMarketing VN. Users in these two VNs belong to twoseparate security groups.
The campus network requiresR&D personnel and sales personnel to communicate with each other. To meet this requirement, which of the following tasks does a network administrator need to perform?
Huawei Open Programmability System (OPS) uses standard HTTP methods to access managed objects to manage network devices. Which of the following HTTP methods is used to configure the value of a network device's managed object?
NAFTIR policing can only be applied to the inbound direction. Its purpose is to monitor the traffic entering the device and ensure that the upstream device does not unnecessarily consume network resources.
Which of the following statements about IPSG is incorrect?
The path of an SR-MPLS TE tunnel can be calculated by the controller or tunnel ingress.
Which of the following statements are correct about the authentication protocols used inPortal authentication?
As shown in the figure, PE1 establishes an EVPN peer relationship with each of PE2 and PE3. When the network is initialized, CE1 sends an ARP request packet.
Which of the following statements are correct about how a PE processes the packet?
Which of the following inter-AS MPLS L3VPN solutions need VPN user data packets to carry MPLS labels when being forwarded between ASs?
Refer to the following command output on the router R1. Which of the following statements isincorrect?
Tunnel0/0/0 current state : UP
Line protocol current state : UP
Last line protocol up time : 15:21:23 UTC-08:00
Description: ! 0.0.3.3
Route Port, The Maximum Transmit Unit is 1500
Internet Address is 20.1.1.1/24
Encapsulation is TUNNEL, loopback not set
Tunnel source 10.0.1.1 (LoopBack0), destination 10.0.3.3
Tunnel protocol/transport GRE/IP, key disabled
keepalive disabled
Checksumming of packets disabled
Current system time: 15:21:37-08:00
300 seconds input rate 0 bits/sec, 0 packets/sec
300 seconds output rate 0 bits/sec, 0 packets/sec
13 seconds input rate 0 bits/sec, 0 packets/sec
13 seconds output rate 448 bits/sec, 0 packets/sec
9 packets output, 824 bytes
0 output error
Input bandwidth utilization : -
Output bandwidth utilization : -
In DU label advertisement mode, if the liberal label retention mode is used, the device reserves labels received from all the LDP peers regardless of whether the LDP peer is the optimal next hop for reaching the destination network.
Whenstatic IPsec VPNis used for WAN interconnection in theHuawei CloudCampus Solution, theAP, Router, and ____can be used as egress devices.
NETCONF provides a set of mechanisms for managing network devices. What layers can NETCONF be conceptually partitioned into?
IPsec SAs can be established in either manual mode or IKE auto-negotiation mode. Which of the following statements about the two modes is incorrect?
In addition to indicating priority, the DSCP value can also indicate the drop probability. Which of the following DSCP values is set with the highest drop probability?
During WLAN planning and design, channels 1, 6, and 11 are recommended on the 2.4 GHz frequency band, and channels 1, 5, 9, and 13 are recommended in high-density scenarios. On the 5 GHz frequency band, it is recommended thathigh-frequency and low-frequency channels of adjacent APs be staggered to prevent overlapping.
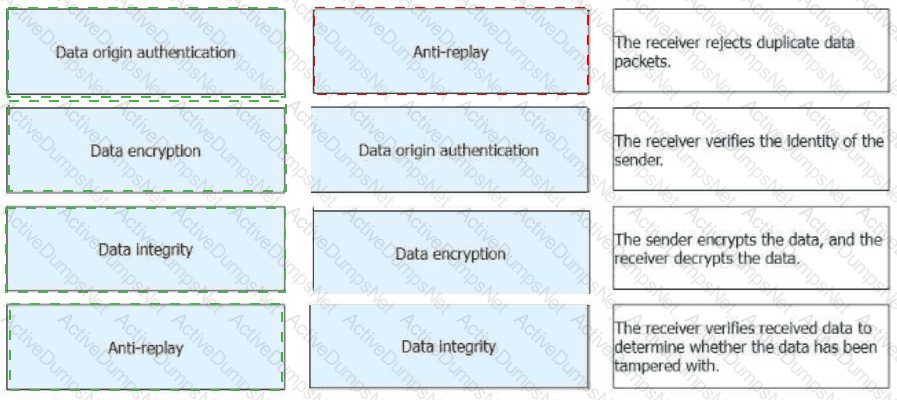
Drag theIPsec functionson the left to the corresponding function description on the right.

The naming of SRv6 instructions complies with certain rules. You can quickly determine the function of an instruction based on the instruction name. Which of the following statements about the keywords in SRv6 instruction names are correct?
The display current-configuration command displays the running configurations in memory.
Network Quality Analysis (NQA) is a real-time network performance detection and measurement technology. It monitors the performance of multiple protocols running on a network. Which of the following protocols can be monitored by NQA?
The TTL field encapsulated in the MPLS label header can prevent infinite loops of MPLS packets. Which of the following statements regarding the TTL field are correct?
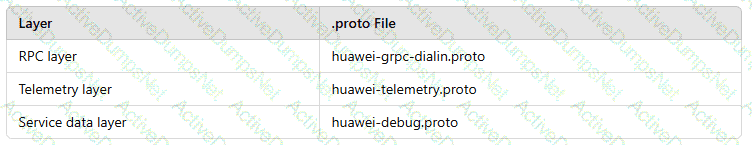
In the gRPC-based telemetry protocol, the data model layer consists of theRPC layer,telemetry layer, andservice data layer. Drag the.proto fileto the layer where the file should be located.
On a virtualized network deployed using iMaster NCE-Campus, after creating VNs, you need to configure inter-VN communication. Which of the following configurations is used to achieve VN communication?
NETCONF provides a set of mechanisms for managing network devices. NETCONF operations take place on a configuration datastore of network devices. Which of the following statements is incorrect about the configuration datastore?
On a campus network, which of the following problems may occur when you manually create a static VXLAN tunnel?
If the number of MAC addresses learned on an interface enabled with port security reaches the upper limit, which of the following actions may the switch take?
Which of the following is the type ofnorthbound APIused byiMaster NCE-WAN?
In a BGP/MPLS IP VPN scenario, if a PE and CE use OSPF to exchange routing information, domain IDs are used to identify whether the routes imported to VPN instances are from the same OSPF domain.
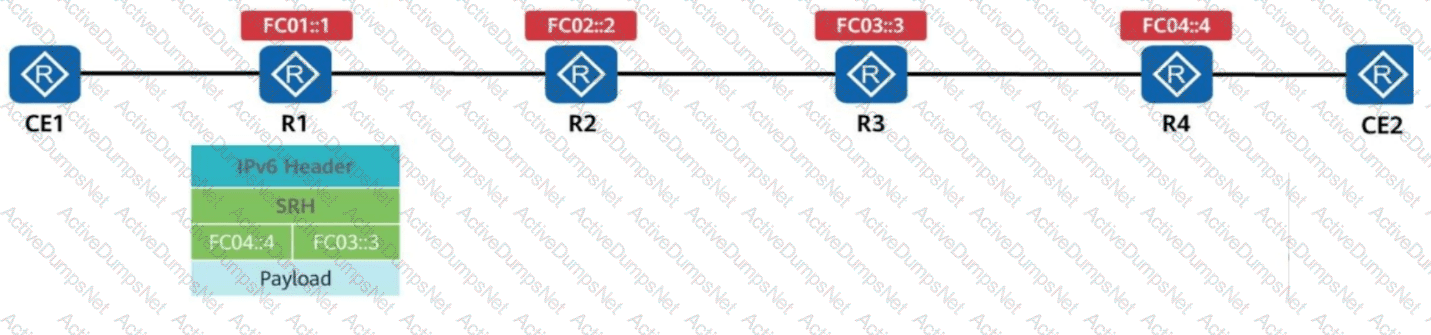
R1 receives a common IPv6 packet from the CE and generates a packet carrying the SRH (Segment Routing Header), as shown in the figure. The packet is forwarded along the path R1 → R2 → R3 → R4. Identify the node type of each device based on their role in SRv6 processing.

On traditional campus networks, network admission control (NAC), VLAN, and ACL technologies are used to control users' network access rights. This results in heavy network O&M workload. Which of the following improvements does the free mobility solution of iMaster NCE-Campus make to traditional campus networks in terms of policy management and control?
In a scenario where a VXLAN tunnel is dynamically established through BGP EVPN, which of the following statements about symmetric IRB forwarding are correct?
BGP routing policies can be used to control the advertisement and acceptance of routes.
The free mobility function is deployed on the iMaster NCE-Campus on a campus network. Which of the following information should an administrator pay attention to?
Which of the following technologies can be used to measure performance based on actual service traffic in Huawei's CloudWAN solution?
SSH connections are usually established based on TCP/IP connections. In specific cases, SSH connections can be established based on UDP connections.
At the NETCONF content layer, the
On a CloudCampus virtualized campus network, virtual networks are defined based on services. Each virtual network corresponds to a service, and isolation needs to be manually configured between virtual networks.
In OSPFv3, which of the following types of LSAs can be flooded in the entire AS?
BFD can implement millisecond-level link status detection.
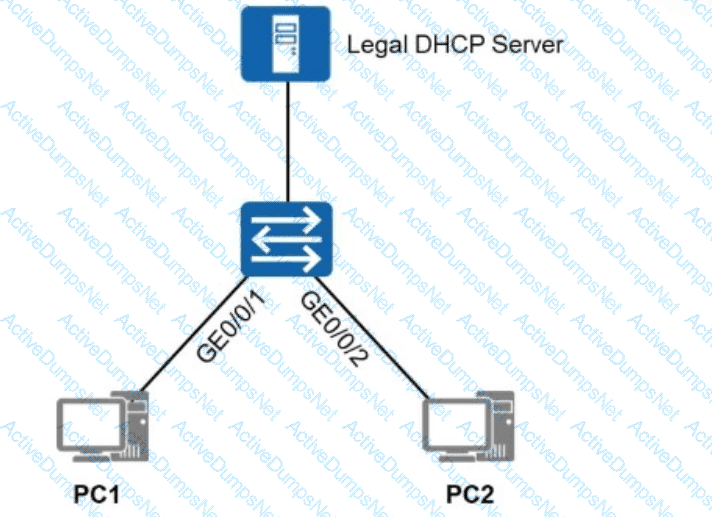
To allow only authorized users (users who obtain IP addresses through authorized DHCP servers or use specified static IP addresses) to access the network shown in the figure, which of the following solutions can be used?
A network administrator needs to retrieve atoken IDfromiMaster NCEusing the following Python code:
import requests
nbi_name = "demol3@north.com"
nbi_pwd = "qqcOVcVel@"
host = "139.9.213.72"
port = "18002"
URI = "/controller/v2/tokens"
post_token_url = "https:// " + host + ":" + port + URI
headers_post = {'Content-Type': 'application/json', 'Accept': 'application/json'}
r = requests.post(post_token_url, headers=headers_post, json={"userName": nbi_name, "password": nbi_pwd}, verify=incorrect)
Which of the following statements is incorrect?
BGP Link State (BGP-LS) introduces a new NLRI into BGP. The NLRI carries link, node, topology prefix, and other information, and is also referred to as the link state NLRI.
The telemetry network model is broadly and narrowly defined. Which of the following modules are involved intelemetry in a narrow sense (device-side telemetry)?
On the campus network shown, IPv6 is deployed for service tests. Four routers are deployed on the network, and these routers use OSPFv3 for network connectivity. Which of the following statements about LSAs generated by the OSPFv3 network is incorrect?
Which of the following are potential risks in HTTP communication?
In the following figure, OSPF is enabled on all router interfaces. The IP addresses marked in the figure belong to Loopback0 of the routers.
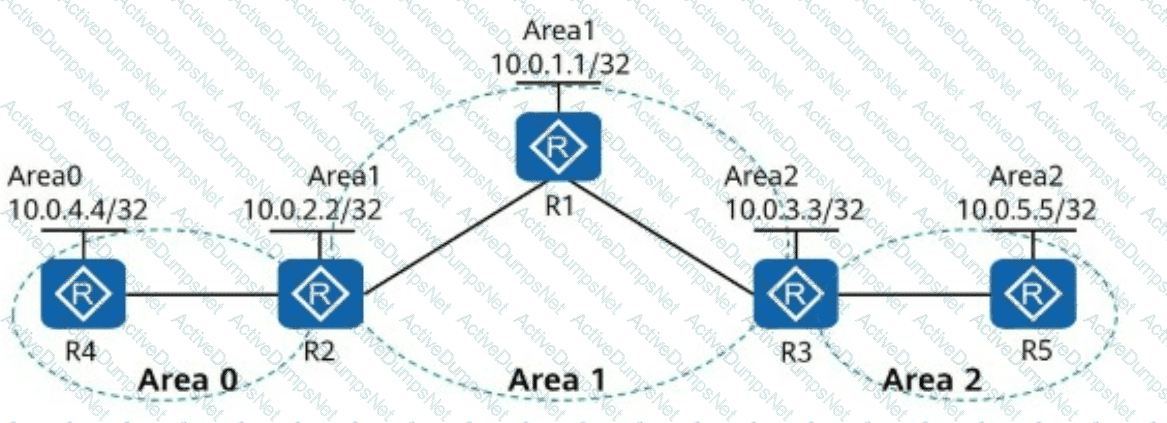
The Loopback0 addresses of R1 and R2 are advertised in Area 1, the Loopback0 address of R4 is advertised in Area 0, and the Loopback0 addresses of R3 and R5 are advertised in Area 2. Given this, which of the following IP addresses can ping each other?
SR-MPLS is enabled on all routers. The label information encapsulated byR1into a data packet is shown in the figure.
Which of the following is the forwarding path of the data packet?
If an engineer wants to remotely log in to a Huawei device, the engineer uses the Paramiko library to compile the following code when compiling the SSH Python script:
cli = ssh.invoke_shell()
cli.send("screen-length 0 temporary\n")
What is the function of screen-length 0 temporary?
If SRv6 needs to be deployed on a bearer WAN, which of the following technologies are required? (Select all that apply)
Flavors are additional behaviors defined to enhance theEnd series instructionsinSRv6. Which of the followingEnd instructionscan thePSP flavorbe attached to?
In Huawei SD-WAN Solution, which of the following tunneling technologies is used to establish data channels?
Which of the following statements are correct about authentication points and policy enforcement points in Huawei's free mobility solution?
In the following figure, a GRE tunnel is established between R1 and R2. If the command ping -a 10.1.1.1 10.3.1.1 is run on R1, which of the following statements is correct about the ICMP packet sent by GE0/0/1 of R1?
Which of the following intelligent traffic steering policies can be used to fully utilize link bandwidth and implement link bandwidth-based load balancing on an enterprise network with multiple links?

 A screenshot of a computer AI-generated content may be incorrect.
A screenshot of a computer AI-generated content may be incorrect.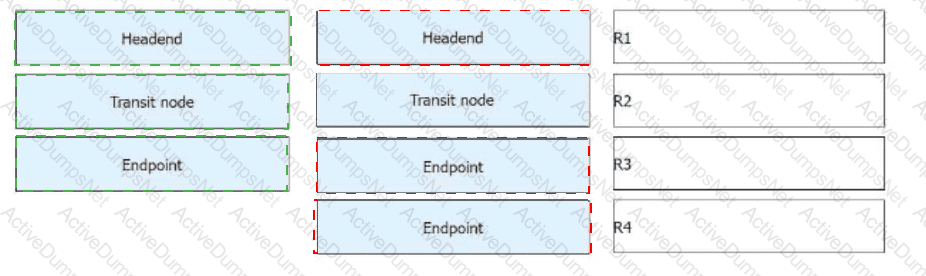
 A white background with black lines
AI-generated content may be incorrect.
A white background with black lines
AI-generated content may be incorrect.