Huawei H12-831_V1.0 HCIP-Datacom-Advanced Routing & Switching Technology V1.0 Exam Practice Test
HCIP-Datacom-Advanced Routing & Switching Technology V1.0 Questions and Answers
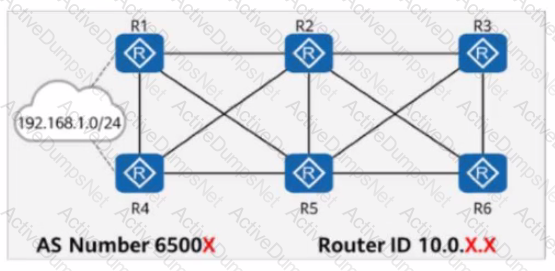
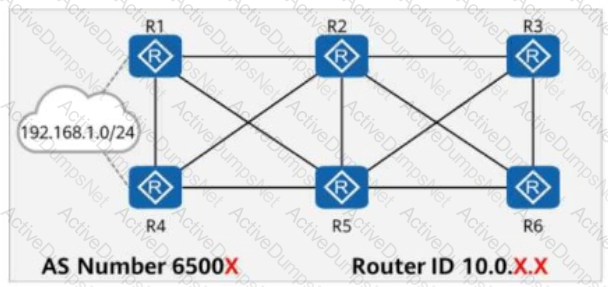
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces.
The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router.
Both R1 and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command.
R1 adds a community attribute (1:1) to the route before advertising it to its peers.
All routers are configured to propagate community attributes.
R3 is configured with a routing policy that rejects routes with the community attribute 1:1.
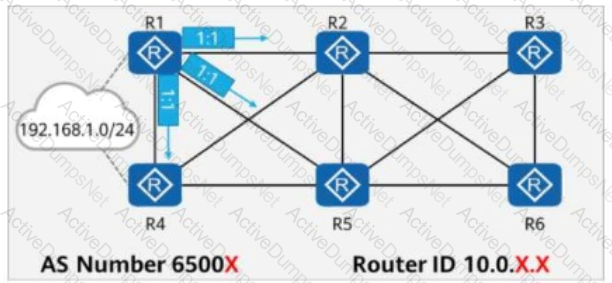
In this case, which of the following is the path for traffic from R3 to 192.168.1.0/24?
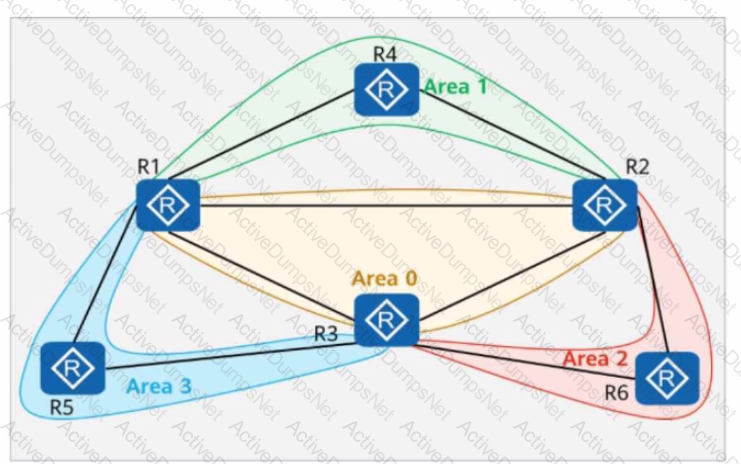
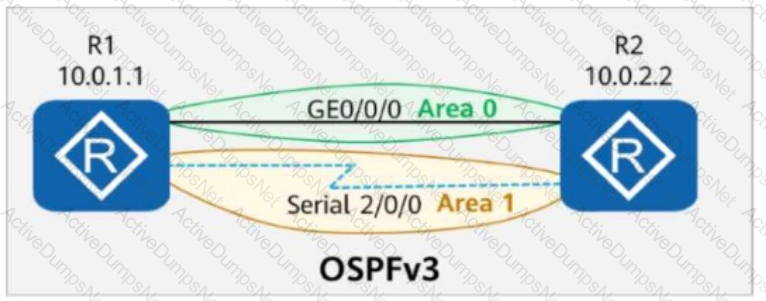
On the OSPFv3 network shown in the figure, area 1 is a stub area, area 2 is a common area, and area 3 is an NSSA. Which of the following LSAs is displayed only in area 2?
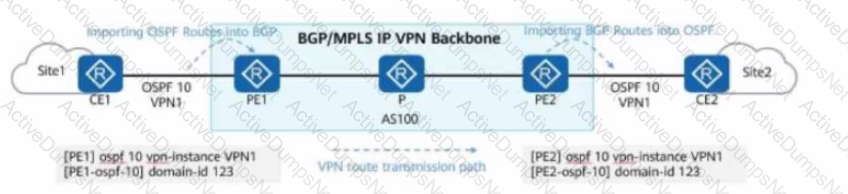
On a BGP/MPLS IP VPN network, which of the following are carried when a PE advertises VPNv4 routes?
To protect a device against the attacks of forged BGP messages, you can configure GTSM to check whether the TTL value in the IP message header is within the specified range. If the peer x.x.x.x valid-ttl-hops 100 command is configured on a device, the valid TTL value range of the detected message is [155, 255].
Service routes of an enterprise are transmitted on the network. Some configurations of PE1 and PE2 are shown in the figure. Which of the following LSAs may CE2 receive?
IPSG is a source IP address filtering technology based on Layer 3 interfaces. It prevents malicious hosts from forging authorized hosts' IP addresses to access authorized network resources.
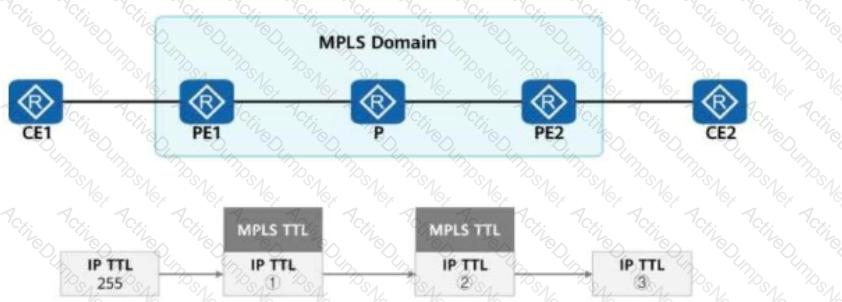
When an IP packet passes through an MPLS network, an MPLS device processes the TTL value in the packet.
If the pipe mode is used in the topology shown in the figure, which of the following is the TTL value in the IP packet?
Options:
IS-IS LSP fragments are identified by the LSP Number field in their LSP IDs. This field is 4 bits long. Therefore, an IS-IS process can generate a maximum of 256 LSP fragments, which means only a limited amount of information can be carried. By adding additional system IDs, you can enable the IS-IS process to generate more LSP fragments.
Options:
On the OSPFv3 network shown in the figure:
OSPFv3 is enabled on the interfaces connecting R1, R2, and R3.
The router ID of each router is 10.0.X.X, where X is the number of the router.
When checking detailed information about an LSA on R3, the command output shows that the LSA is generated by R2 and describes the IPv6 prefix address associated with the Network-LSA.
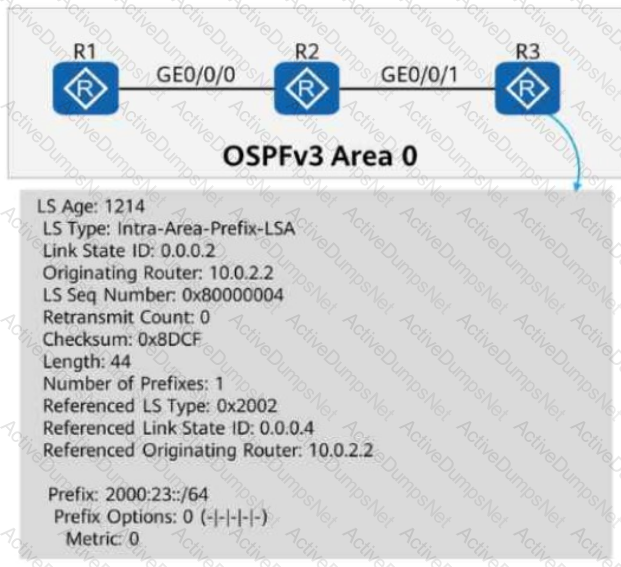
Based on this information, which of the following statements is correct?
On the OSPF network shown in the figure, a network engineer finds that R1 and R2 have the same router ID, and both have imported default routes (with the default-route-advertise always command configured). Given this, which of the following statements is false?
On the OSPF network shown in the figure, area 1 is an NSSA, area 2 is a common area, and R4 imports an external route 10.0.4.4/32. The router ID of each router is 10.0.X.X, where X is the router number. If the asbr-summary 10.0.4.0 255.255.255.0 command is run in the OSPF processes of R1 and R3, which of the following routers have the route 10.0.4.0/24 in their routing tables?
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces. The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router. Both Rl and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command. R3 is configured with the peer y.y.y.y as-path-filter 1 import command for all peers. Which of the following sets of commands enables R3 to select the route with the longest AS_Path to 192.168.1.0/24?
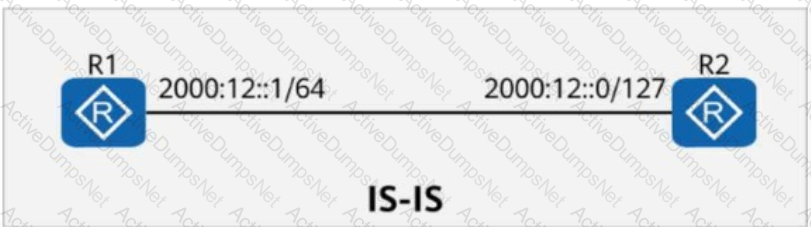
On the IS-IS IPv6 network shown in the figure, after the network becomes stable:
R1 can ping 2000:12::0, and
The display ipv6 neighbors command can be used to display the MAC address corresponding to 2000:12::0.
Is this statement TRUE or FALSE?
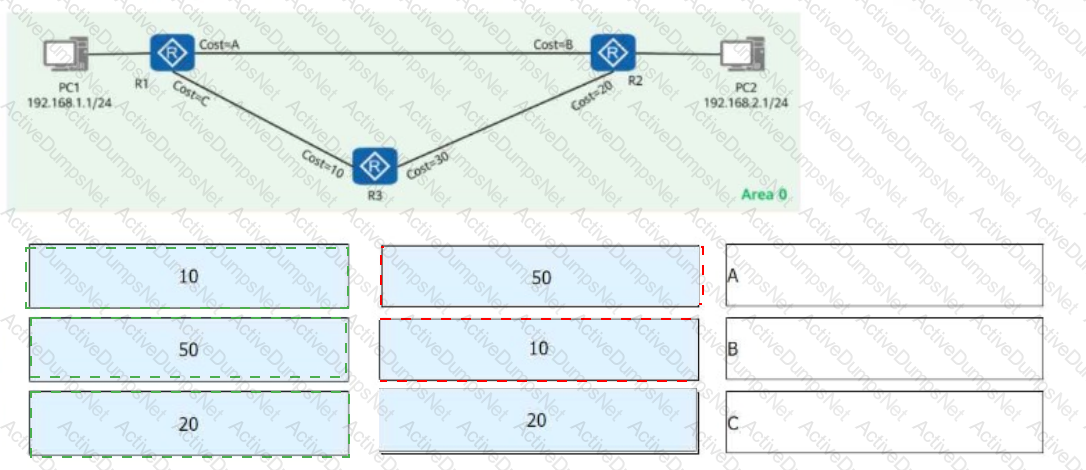
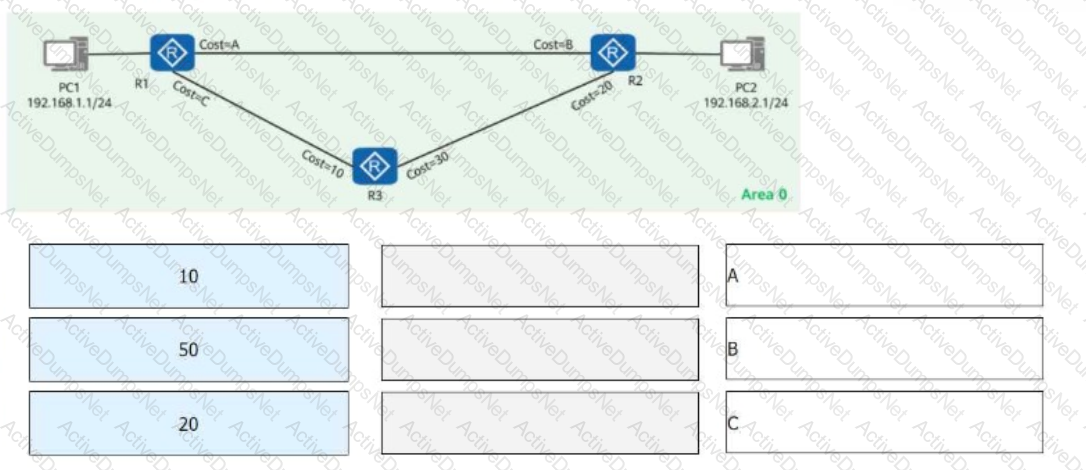
On the OSPF network shown in the figure, drag the values on the left to the correct positions so that:
Traffic from PC1 to PC2 follows the path:PC1 -> R1 -> R3 -> R2 -> PC2
Traffic from PC2 to PC1 follows the path:PC2 -> R2 -> R1 -> PC1
Which of the following OSPF cost values should be assigned to Cost-A, Cost-B, and Cost-C to achieve this routing behavior?
In the figure, a network administrator configures a static LSP to implement MPLS data forwarding. The lower part of the topology shows the packet header information obtained from a device.
Which of the following statements are true?
Options:
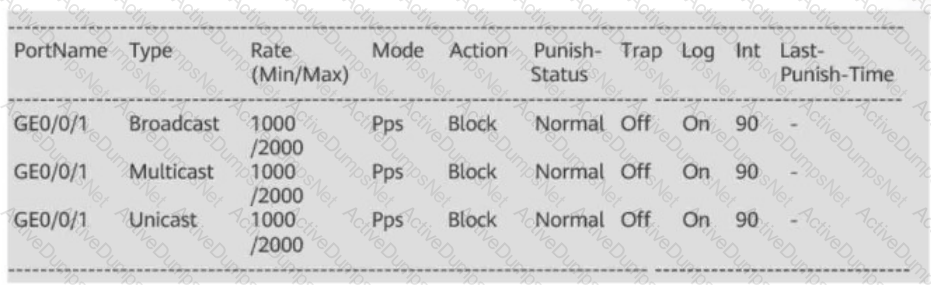
An interface of a switch is in error-down state. A possible cause is that the average rate of broadcast packets received by the interface exceeds the upper threshold set by the administrator for storm control.
On an enterprise network shown in the figure, EBGP is deployed between CEs and PEs.
CE1 sends a VPN route to PE1.

Which of the following statements are false?
Options:
On the OSPFv3 network shown in the figure, area 1 is a stub area.
Which of the following LSAs is generated by only one router?
The figure shows the Router-LSA generated by a router. Which of the following statements are true based on the LSA?
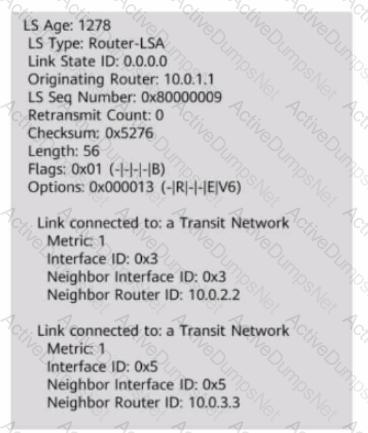
An OSPFv3 NSSA LSA is generated by an ASBR, describes routes to a destination outside the AS, and is advertised in an NSSA.
Options:
A network engineer obtains a multicast data frame whose destination MAC address is 01-00-5e-00-01-01. Given this, which of the following cannot be the destination IPv4 address of this frame?
Options:
On the network shown in the figure, the network administrator deploys DHCP snooping on the switch to defend against bogus DHCP server attacks.
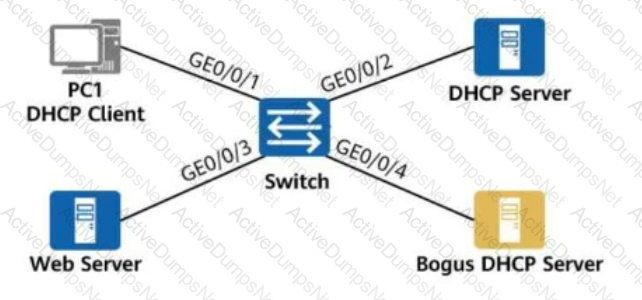
Which of the following interfaces should be configured as the DHCP trusted interface?
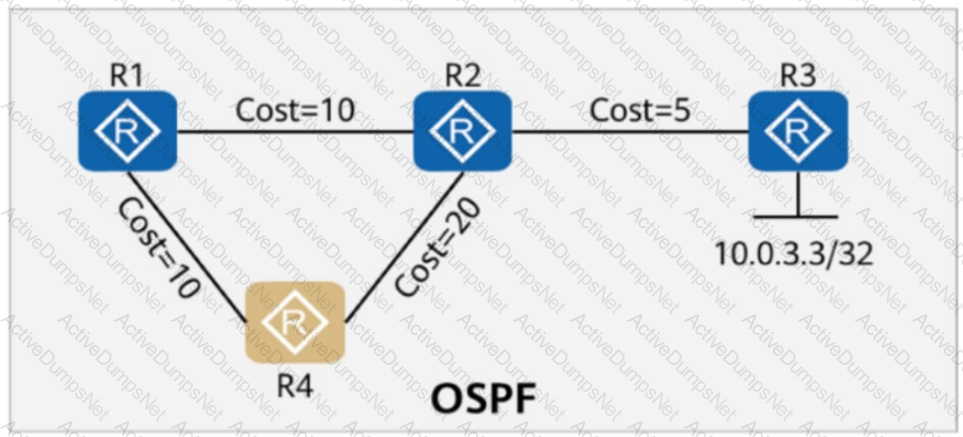
On the OSPF network shown in the figure, the cost values of links are marked. OSPF IP FRR is enabled on R1. The primary path from R1 to 10.0.3.3/32 is R1 -> R2 -> R3, and the backup path is R1 -> R4 -> R2 -> R3.
The path that IP packets pass through on an MPLS network is called a label switched path (LSP). An LSP is a bidirectional path that specifies the transmission direction of data flows.
On the network shown in the figure, single-hop BFD is configured on R1 and R2.
A network engineer finds that the BFD session goes down. To locate the fault, the network engineer queries the BFD configurations on R1 and R2.
According to the configuration information marked in the figure, it can be determined that mismatched time parameter settings on R1 and R2 cause the BFD session to go down.

Is this statement TRUE or FALSE?
On the OSPFv3 network shown in the figure, area 1 is a common area. R2 generates an Inter-Area-Prefix-LSA to describe the routes of a network segment in the area. Such an LSA exists in both area 0 and area 1.
On the IS-IS IPv6 network shown in the figure, multi-topology is enabled on all routers. The IPv6 address of Loopback0 on R4 is 2000::/128. The IPv6 summary 2000::/64 level-1-2 command is configured in the IS-IS processes of R2 and R1. Which of the following statements is false?
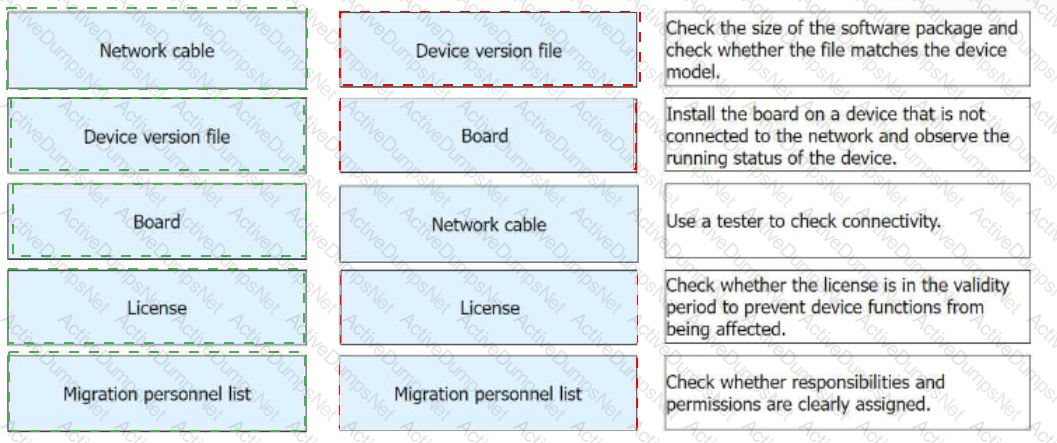
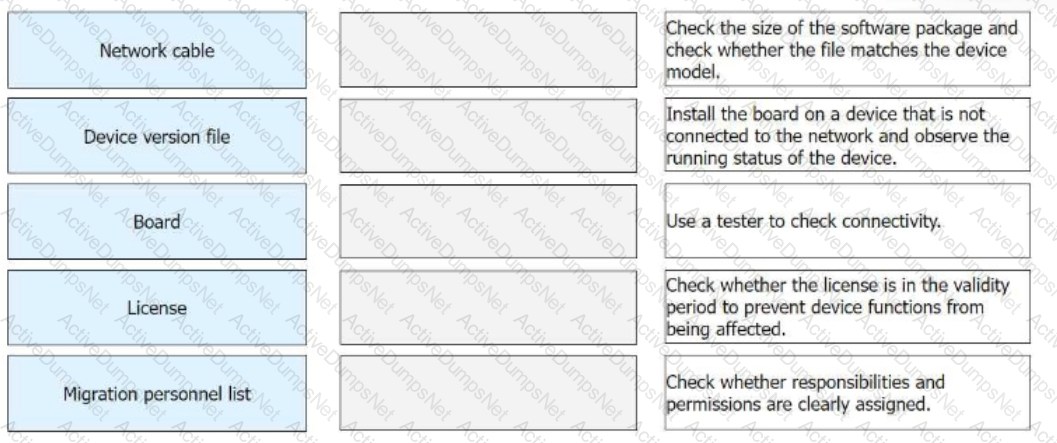
In the preparation phase of a migration project, the software and hardware need to be checked. Match the operation objects in the preparation phase with the corresponding operation contents.
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces. The AS number is 6500X, where X is the number of the router. Both Rl and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command. By default, in the routing table of R3, which of the following is the AS_Path attribute carried in the route to 192.168.1.0/24?
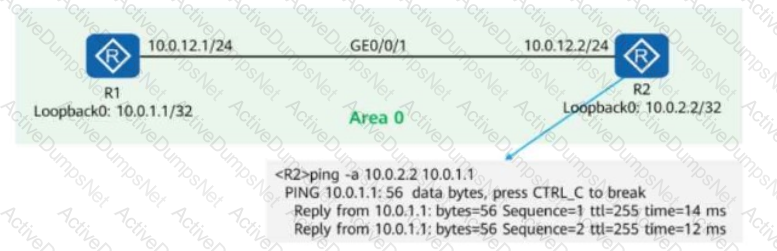
On the OSPF network shown in the figure, R1 and R2 use OSPF to communicate with each other through Loopback0. In addition:
MPLS LDP is enabled on R1 and R2.
The LDP transport address is the IP address of Loopback0.
A network engineer finds that an LDP session cannot be established between R1 and R2 and runs diagnostic commands (shown in the figure) to locate the fault.
Given this, which of the following are possible causes of the fault?
Options:
A network engineer provides a troubleshooting report after rectifying a fault. The actual network is simplified into the one shown in the figure, where R1 and R2 both have OSPF enabled and function as the gateways of PC1 and PC2, respectively.
Given this, which of the following statements are true?
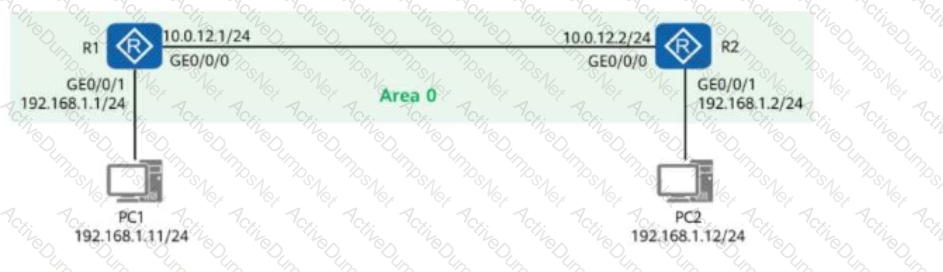
Network Topology:
R1:
Interface GE0/0/0: 10.0.12.1/24 (Connected to R2)
Interface GE0/0/1: 192.168.1.1/24 (Gateway for PC1)
R2:
Interface GE0/0/0: 10.0.12.2/24 (Connected to R1)
Interface GE0/0/1: 192.168.1.2/24 (Gateway for PC2)
Options:
OSPFv3 packets are encapsulated in IPv6 packets. Which of the following is the value of the Next Header field in the IPv6 packet header?
Options:
On the network shown in the figure, IS-IS runs on R1, R2, R4, and R5, and the area ID is 49.0001. IS-IS runs on R3 and R6, and the area ID is 49.0002. The import-route isis level-2 into level-1 command is configured on R2.
In AS 65000, R1, R3, R4, and R6 each establish iBGP peer relationships with R2 and R5. R2 and R5 are Route Reflectors (RRs), and R1, R4, R3, and R6 are clients.
The iBGP peer relationships are established using Loopback0. The IP address of Loopback0 on each router is 10.0.X.X/32, and the router ID is 10.0.X.X, where X is the number of the router.
R1 and R4 import the external route 192.168.1.0/24 to BGP through the import-route command, and R3 and R6 import the external route 192.168.2.0/24 to BGP through the import-route command.
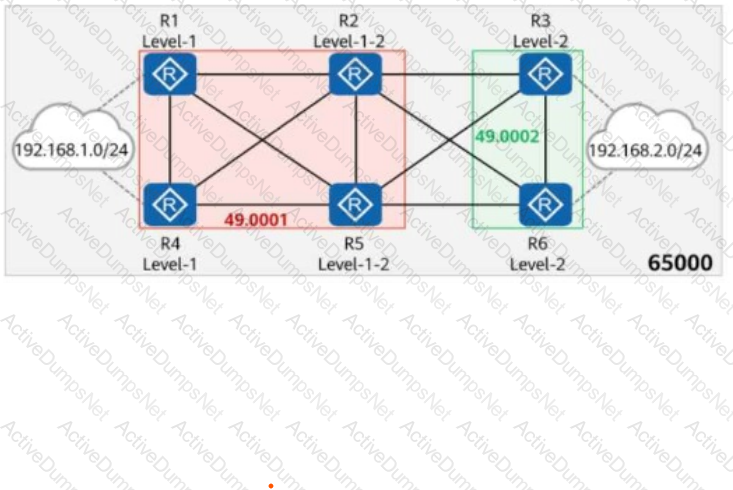
Which of the following statements are true?
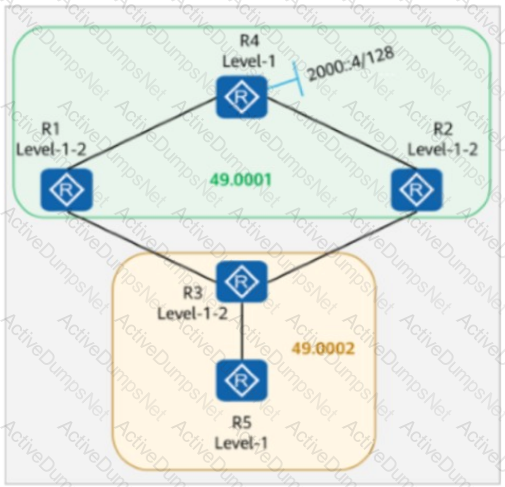
On the IS-IS IPv6 network shown in the figure, multi-topology is enabled on all routers.
The IPv6 address of Loopback0 on R4 is 2000::4/128.
The command ipv6 summary 2000::/64 level-1-2 is configured in the IS-IS process of R4.
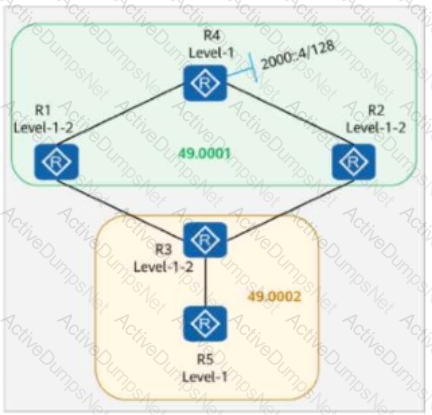
Which of the following statements is false?
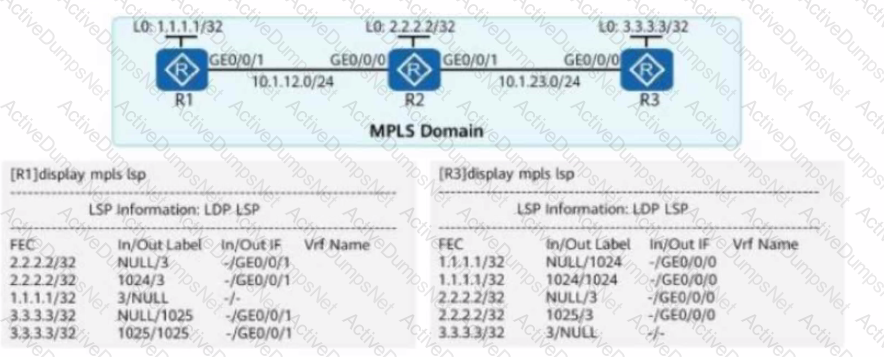
The figure shows the LSP information of R1 and R3 on an MPLS network. An administrator runs the ping -a 1.1.1.1 3.3.3.3 command on R1. Given this, which of the following statements is true?
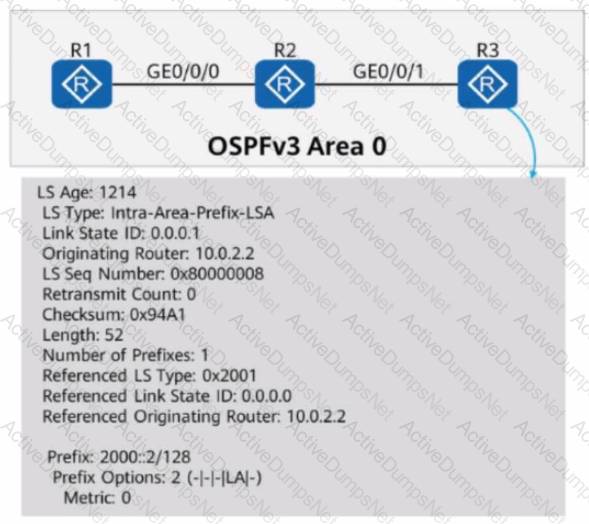
On the OSPFv3 network shown in the figure, OSPFv3 is enabled on the interfaces connecting R1, R2, and R3. The router ID of each router is 10.0.X.X, where X is the number of the router. If you check detailed information about an LSA on R3, the command output shows that the LSA is generated by R2 and describes the IPv6 prefix address associated with the Router-LSA.
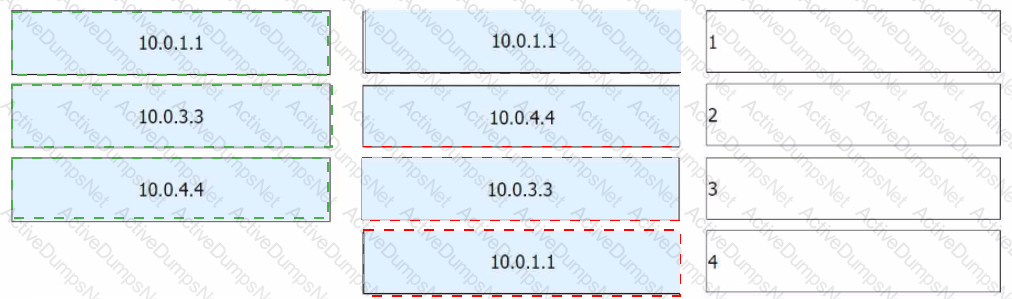
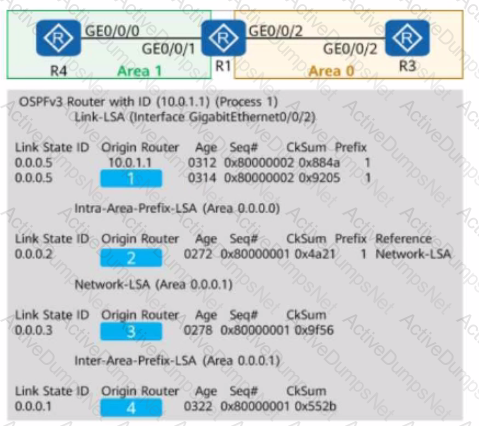
On the OSPFv3 network shown in the figure, OSPFv3 parameters use default values. The LSDB is checked on one of the devices. The router IDs of R1, R3, and R4 are 10.0.1.1, 10.0.3.3, and 10.0.4.4, respectively. The Origin Router part of some LSAs is hidden. Complete this part. (Tokens can be reused.)

The figure shows the output information on a switch.
Which of the following can be determined from the information?
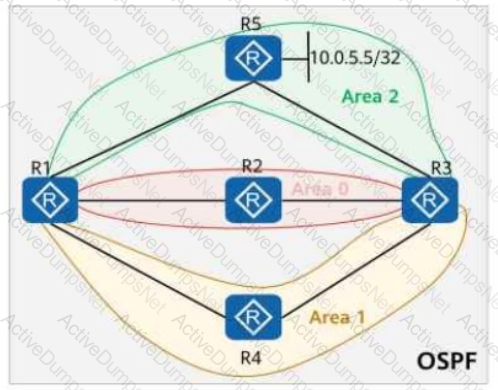
On the OSPF network shown in the figure, area 1 and area 2 are common areas. The IP address of Loopback0 on R5 is 10.0.5.5/32, and OSPF is enabled on this interface. If the abr-summary 10.0.5.0 255.255.255.0 command is run in area 2 (where R1 resides), which of the following routers have the route 10.0.5.0/24 in their routing tables?
In CE multi-homing scenarios, if BGP AS number substitution is enabled on PEs, you can run the peer soo command on the EBGP peers of the PEs and CE to configure the Site of Origin (SoO) attribute to prevent loops.
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces.
The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router.
Both R1 and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command.
Which of the following statements are true?
Network administrators can run the clock timezone command to set the time zone of a device. If two network devices have different time zone settings, they cannot establish a neighbor relationship using a dynamic routing protocol.
Options:
On the network shown in the figure, EBGP peer relationships are established between neighboring routers through directly connected interfaces.
The router ID of each router is 10.0.X.X, and the AS number is 6500X, where X is the number of the router.
Both R1 and R4 have static routes to 192.168.1.0/24, which are imported to BGP through the import-route command.
The aggregate 192.168.1.0/16 detail-suppressed command is configured on R2.
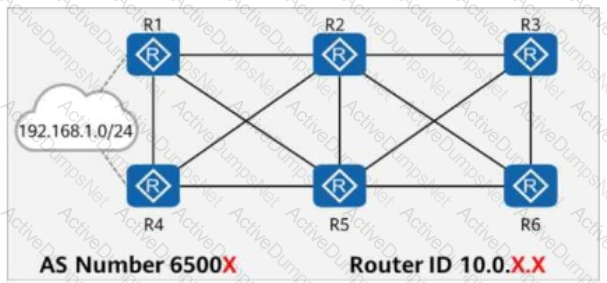
Which of the following is the path for traffic from R3 to 192.168.1.0/24?
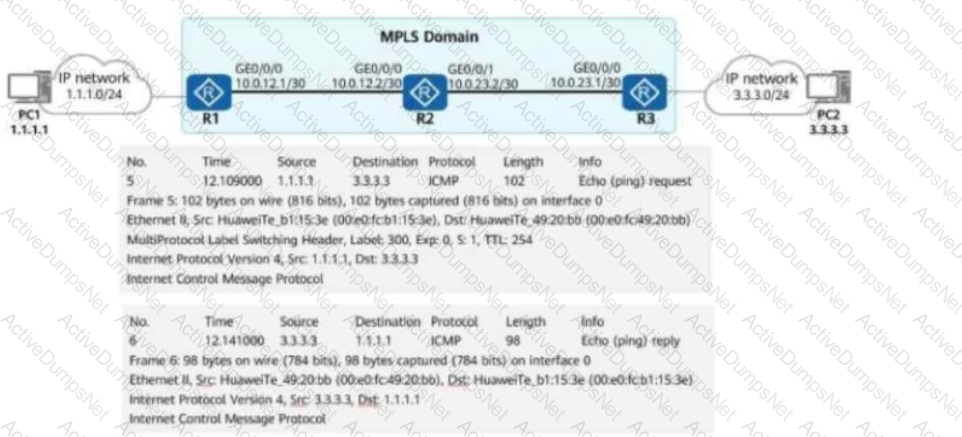
In the figure, packets are forwarded based on MPLS on the network.
When PE2 receives a packet from P2, what is the label value carried in the packet?
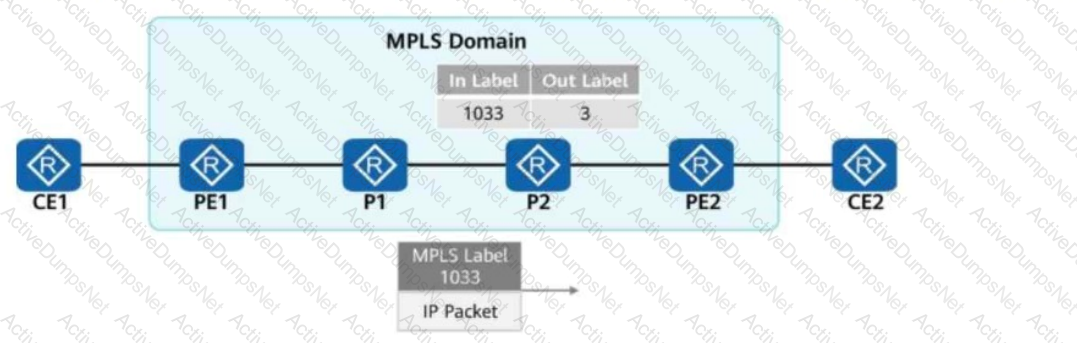
Options:
As shown in the figure, an administrator enables port isolation on the switch’s interfaces connected to terminals.
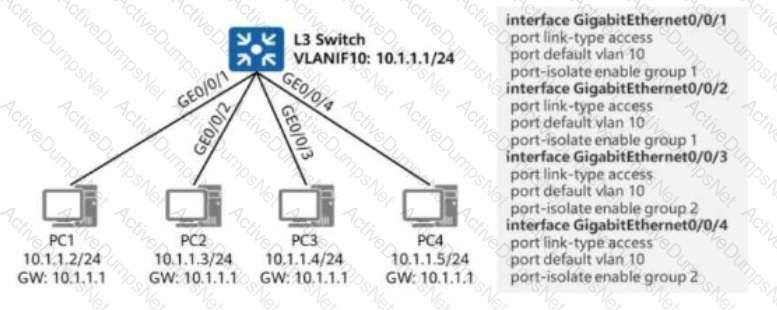
In this scenario, which of the following IP addresses cannot be pinged from PC1?
On the network shown in the figure, an administrator first completes the routing configuration and then enables MPLS and LDP on R1, R2, and R3 and their interconnected interfaces. In this manner, traffic from PC1 to PC2 can be forwarded based on MPLS. Which of the following routing configurations can implement this function?
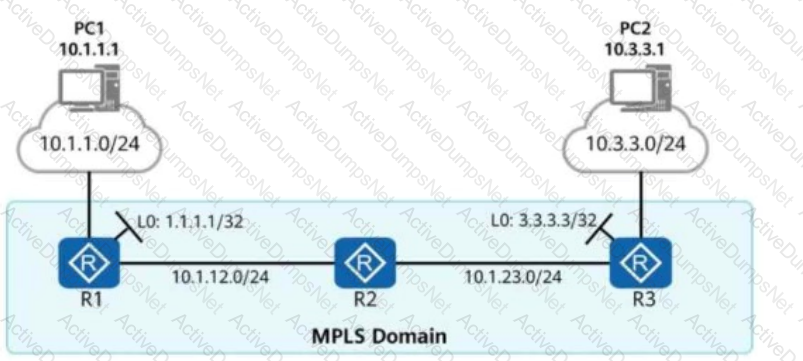
Options: