Huawei H12-821_V1.0 HCIP-Datacom-Core Technology V1.0 Exam Practice Test
HCIP-Datacom-Core Technology V1.0 Questions and Answers
The VRID of the VRRP virtual router is 3 and the virtual IP address is 100.1.1.10. What is the virtual MAC address?
A network entity title consists of an area address and a system ID. It is a special NSAP (the SEL has a fixed value of 00) and is mainly used for route calculation.
Four routers run ISIS and have established adjacencies. The area IDs and router levels are marked in the following figure. If route leaking is configured on R3, which of the following is the cost of the route from R4 to 10.0.2.2/32?
BFD control packets are encapsulated in UDP packets for transmission. What is the destination port number of multi-hop BFD control packets?
Link aggregation is a common network technology. Which of the following are advantages of link aggregation?
Preferences of routing protocols determine the sequence In which a router selects a route among routes to the same destination /earned through different routing protocols.
OSPF has several types of special areas, which are used to reduce the LSDB size and improve device performance.
Which of the following LSAs cannot be in a totally stub area?
Which of the following LSAs are advertised only within a single area?
On an OSPF or IS-IS network, the filter-policy import command can be run on a router to filter out the LSAs forwarded by its neighbors.
Which of the following routing protocols support the default route through command configuration?
Compared with STP, RSTP defines the different port states. Which of the following statements regarding discarding and learning states are true?
BFD for OSPF is deployed on a directly connected link. If the physical link is disconnected, drag the following BFD processes to the corresponding sequence numbers.
Hackers often obtain the login permissions of system administrators through various attacks.
Which of the following measures can be taken to enhance the security of administrator accounts?(Select all that apply)
TheBFD (Bidirectional Forwarding Detection) state machineimplements athree-way handshakefor BFDsession setup or teardown.Which of the following session states are involved in BFD session setup?
When receiving a packet, a Huawei router matches the packet against ACL rules. The default ACL matching order used by the Huawei router is.
VRRP defines three states. Only the device in which state can forward packets destined for a virtual IP address?
(Write in full and capitalize the first letter.)
Which of the following statements about stack split is false?
On an STP network, only the designated port processes inferior BPDUs. On an RSTP network, a port with any role processes inferior BPDUs.
On an OSPF network, an algorithm is used to prevent loops within an area, but loops may occur between areas. Therefore, OSPF defines a loop prevention mechanism for inter-area routes. Which of the following statements are true about the loop prevention mechanism?
In IGMPv1, querier selection depends on a multicast routing protocol, such as PIM. In IGMPv2 and IGMPv3, the interface with the largest IP address acts as the querier.
BFD can associate with multiple protocols to quickly detect faults.
Which of the following functions are supported?(Select all that apply)
During routineO&M, the administrator checks theIGMP configurationon a router interface. The configuration is as follows:
Interface information of VPN-Instance: public net
GigabitEthernet0/0/1(192.168.1.1):
IGMP is enabled
Current IGMP version is 2
IGMP state: up
IGMP group policy: none
IGMP limit: -
Value of query interval for IGMP (negotiated): -
Value of query interval for IGMP (configured): 60 s
Value of other querier timeout for IGMP: 0 s
Value of maximum query response time for IGMP: 10 s
Querier for IGMP: 192.168.1.1 (this router)
Given this, which of the following statements aretrue?
In IPv6, to communicate with a destination host, a host must obtain the link-layer address of the destination host through ARP.
The Origin attribute is used to define the origin of BGP path information. There are three types of Origin attributes. Which of the following lists the Origin attributes in descending order of priority?
Which of the following statements regarding IGMPv1 and IGMPv2 are true?
On an RSTP network, if a port receives an RST BPDU and finds that its buffered RST BPDU is superior to the received RST BPDU, the port discards the received RST BPDU without responding.
In special scenarios, when advertising routes to an IBGP peer, a BGP device needs to set the next hop to its IP address to prevent blackhole routes. Which of the following commands can be run in this case?
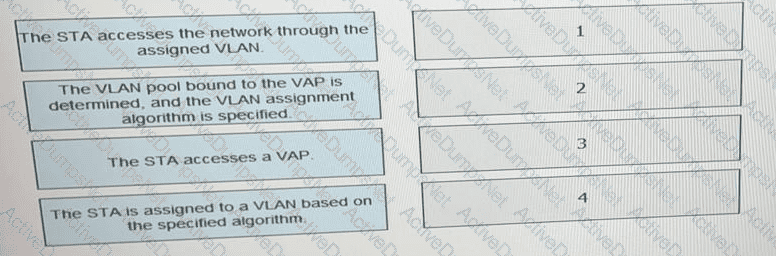
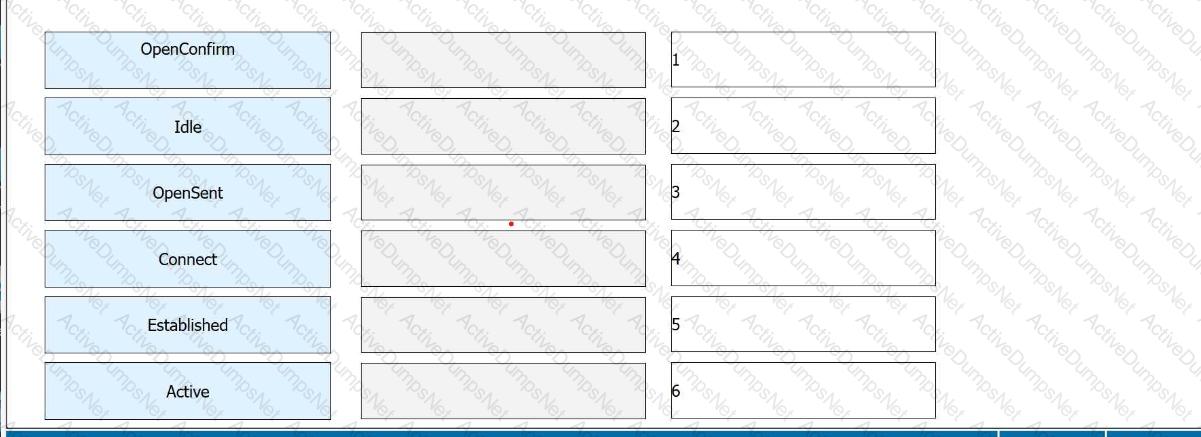
On a WLAN, engineers can use the VLAN pool mechanism to assign access users to different VLANs, which helps reduce the number of broadcast domains and improve network performance. VLAN pools support two VLAN assignment algorithms: even and hash. Drag the advantages and disadvantages to the two algorithms.(Token is reusable)
On an RSTP network, port priorities may be compared during root port or designated port election. Which of the following values is the default priority of a port on a Huawei switch?
On an IS-IS network, two directly connected routers establish a neighbor relationship through the three-way handshake mechanism by default, regardless of whether the network type is P2P or broadcast.
SSHis a secure protocol that establishes tunnels for users on insecure networks.Which of the following statements is false about SSH login?
OSPF neighbors have multiple states, such as Down, Init, 2-way, Loading, or Full. In which of the following states do OSPF routers negotiate the master and slave roles?
In addition to numerous normal service packets, the CPUs of devices on a network may also receive large numbers of attack packets. To ensure that the CPUs can properly respond to normal services, the devices provide the local attack defense function.
Which of the following statements are true about this function?(Select all that apply)
After the administrator of an enterprise deploys a DHCP server, employees complain that their clients cannot obtain IP addresses from the DHCP server. Which of the following may cause this problem?
On an IS-IS network, all routers generate LSPs. Which of the following types of information isnotcontained in the LSPs generated by pseudonodes?
See the command output of a router below. Which of the following statements is true?
OSPF Process 1 with Router ID 10.0.2.2
Interface: 10.0.12.2 (GigabitEthernet 0/0/0)
Cost: 1 State: BDR Type: Broadcast MTU: 1500
Priority: 1
Designated Router: 10.0.12.1
Backup Designated Router: 10.0.12.2
Timers: Hello 10 , Dead 40 , Poll 120 , Retransmit 5 , Transmit Delay 1
See the following figure. All routers on the network run IS-IS and are in area 49.0001. By referring to the LSDB of R1, the Level-2 DIS is. (Enter the device name, for example, R1.)
AnIP prefix listis a common matching tool in routing policies. When anIP prefix listis configured on a Huawei router, which of the following parameters areoptional?
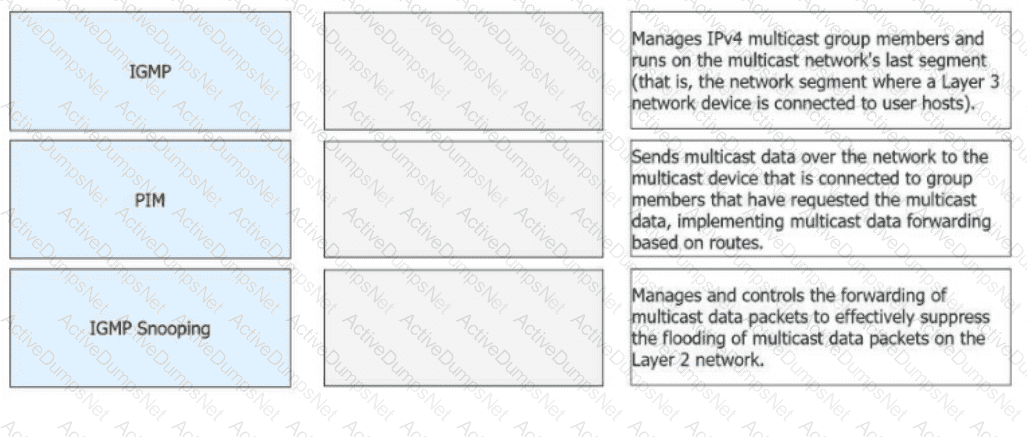
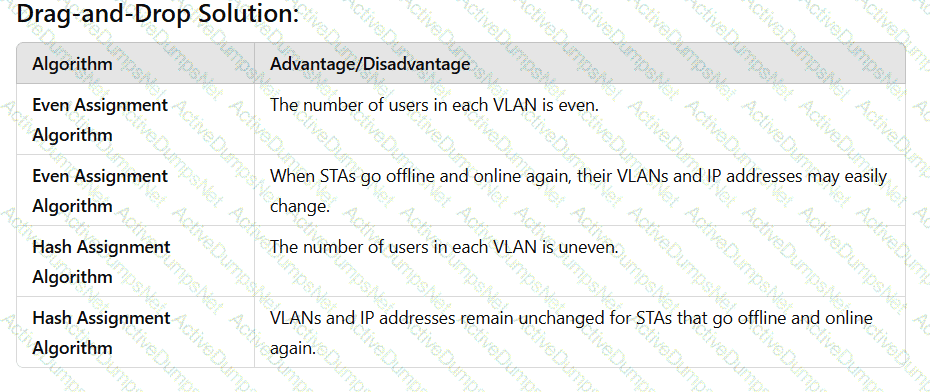
Match the following IPv4 multicast protocols with the corresponding functions.
A switch runs MSTP. The configuration is shown in the figure. What is the role of this switch in MSTI 1?
Which of the following statements is true about BGP?
STAs stay on different subnets before and after Layer 3 roaming. To enable the STAs to access the original network after roaming, network engineers need to configure user traffic to be forwarded to the original subnet over a CAPWAP tunnel.
When receiving a packet, a router matches the packet againstACL rules. The ACL matching result is eitherMatchedorUnmatched. If the matching result isUnmatched, which of the following are possible causes?
When a BGP device sends an Open message to establish a peer connection, which of the following information is carried?
Which of the following statements regarding the MED value in BGP are true?
Which of the following statements about BFD operating modes are true?
The Internet Assigned Numbers Authority (IANA) allocates Class D addresses to IPv4 multicast. An IPv4 address is 32 bits long, and the four most significant bits of a Class D address are 1110.
IGMPV3 not only supports IGMPv1 General Query and IGMPv2 Group-Specific Query, and also IGMPv3 Source/Group-Specific Query.
A Layer 2 switch supports multiple types of Ethernet interfaces. Similar to a trunk interface, a hybrid interface allows data frames from multiple VLANs to pass through. In addition, you can determine whether data frames from a VLAN sent out from a hybrid interface are tagged or untagged.
Which of the following statements regarding an IP prefix are true?
After IPsec is deployed on an enterprise network, services are interrupted. The administrator finds that no data flow triggers IKE negotiation.
Which of the following are possible causes?(Select all that apply)
Which Of the following IEEE 802.11 standards is also known as Wi-Fi 6?
Which of the following is the default interval at which the DIS on a broadcast IS_IS network sends CSNPs.
Similar to the OSPF DR, the IS-IS DIS needs to be elected on a broadcast network. However, the OSPF DR is preemptive by default, whereas the IS-IS DIS is not preemptive by default.
Regarding the route-policy set-cost configuration below, which of the following statements is true?

An enterprise administrator wants to configure single-hop BFD to implement fast detection of direct links. Which of the following configurations are mandatory?
This configuration is part of RTA configuration. Which of the following statements regarding the configuration are true?
[RTA] ospf 100
[RTA-ospf-100]silent-interface GigabitEthernet 1/0/0
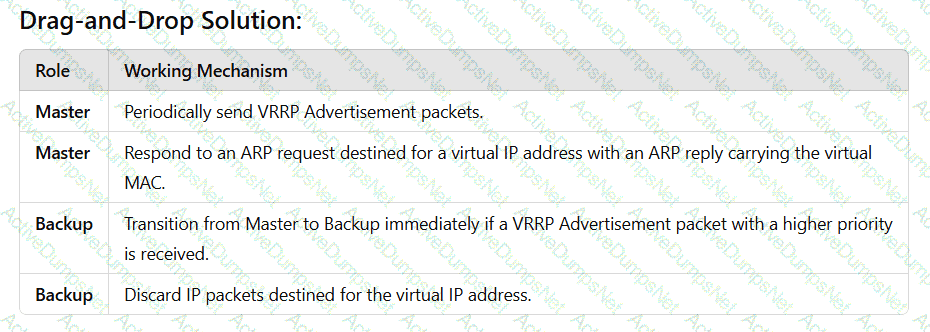
In VRRP networking, devices assume the Master and Backup roles after election. Match the two roles with their working mechanisms.(Token is reusable)
Depending on the type of algorithms used, routing protocols are classified into distance-vector protocols and link-state protocols. Which of the following routing protocols are link-state protocols?
During BGP route summarization configuration, the keyword can be used to suppress all specific routes so that only the summary route is advertised. The summary route carries the Atomic-aggregate attribute rather than the community attributes of specific routes.
Compared with RSTP, which of the following port roles are added to MSTP?
Which of the following statements regarding routing policy and policy-based routing are true?
On an OSPF network, interfaces are classified into four types based on link layer protocols. Which of the following types can interfaces on an IS-IS network be classified into based on physical links?
As shown in the figure, data traffic is forwarded in tunnel mode along the path of STA -> HAP -> HAC -> upper-layer network before roaming. What is the flow direction of data traffic after Layer 3 roaming?
Route attributes are specific descriptions of routes. BGP route attributes can be classified into four types. Which of the following are well-known discretionary attributes?
What is the correct procedure for a VLAN pool to assign terminals to VLANs.
VRRP is implemented based on thepriority and preemption functionsof VRRP routers.Which of the following statements is false about the VRRP solution?
InIP multicast transmission, packets are transmitted from a source to agroup of receivers. Which of the following statements aretrueabout IP multicast technologies?
An enterprise uses OSPF to implement network communication. To ensure data validity and security, all authentication modes supported by OSPF are enabled on routers. In this case, interface authentication is preferentially used by the routers.
In addition to a route reflector, the confederation is another method that reduces the number of IBGP connections in an AS.
Which of the following statements are true about the confederation technology? (Choose all that apply)
An engineer sets the CAPWAP heartbeat detection interval to 20 of the active link before an active/standby switchover occurs?
R1, R2, R3, and R4 run IS-IS, and the DIS priorities of their interfaces are shown in the following figure. Ifall these devices are started simultaneously, will be elected as the DIS. (Enter the device name, for example, R1.)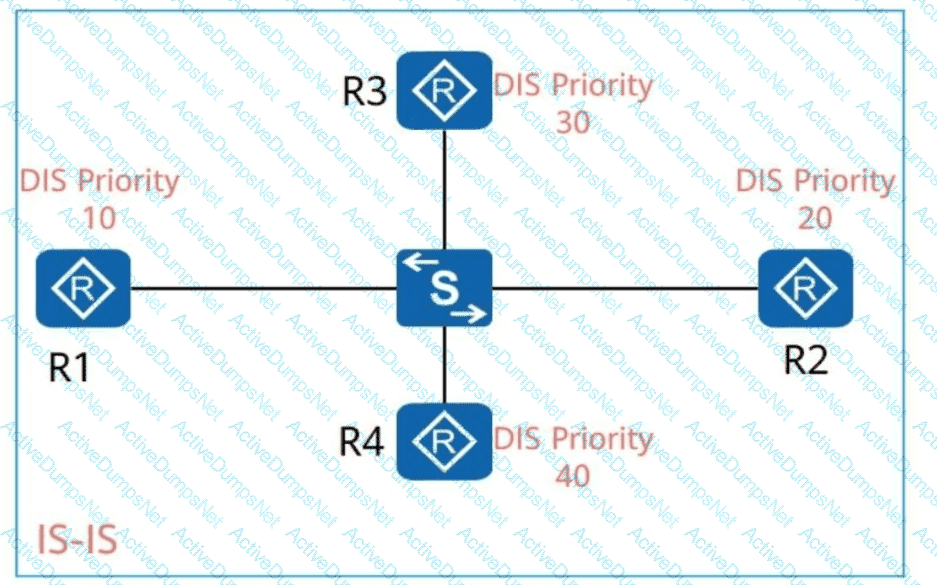
A forwarding information database (FIB) can directly guide packet forwarding on a router.
Which of the following PIM protocol packets have unicast destination addresses.
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
Route summarization is a mechanism that combines multiple routes.BGP supports automatic summarization and manual summarization on IPv6 networks.
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
Which of the following is used as the destination port for single-hop BFD?
On an OSPF network, there are multiple types of packets, each with a different function. Which of the following are the main functions of Hello packets?
IGMP has three versions. Different versions support different features. Which of the following features is supported by all versions?
Which of the following statements regarding the stateful inspection firewall is true?
To prevent inter-area routing loops, OSPF does not allow advertising routing information between two non-backbone areas and allows sing routing information only within an area or between the backbone area and a non-backbone area. Therefore, each ABR must be connected to the backbone area.
By default, a router interface sends PIM Hello messages at an interval of __________ seconds.
OSPF has five types of packets, which have the same header format. If the Auth Type field in the packet header is 1, which of the following authentication modes is used?
To overcome the disadvantages ofSTP,RSTPchanges the format ofconfiguration BPDUs. Which of the following fields inSTP BPDUsis used to specify theport role?
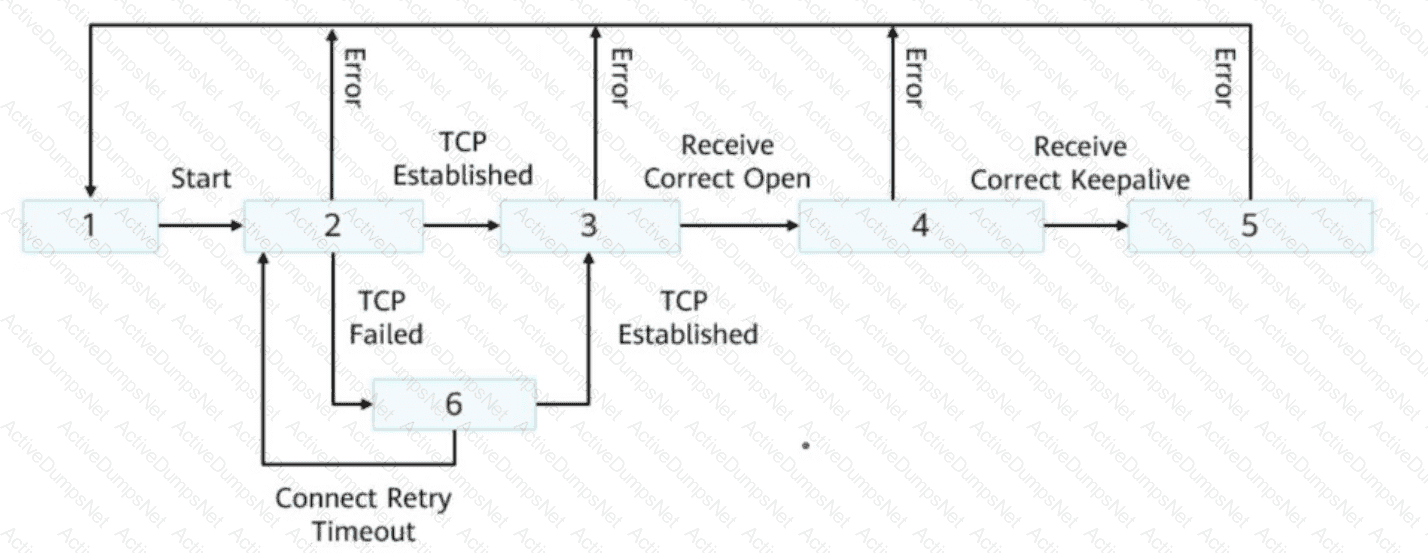
The following figure shows the BGP state switching mechanism. Drag the following BGP states to the corresponding sequence numbers.
On an OSPF network, an IR in area 0 must be a BR, but an ASBR may not be an ABR.
When a routing policy is used to filter routes, which of the following route prefixes will be denied by the IP prefix below?
On an enterprise WLAN where Portal authentication is deployed, an AC functions as an access device and communicates with a Portal server using the Portal protocol. Which of the following statements are true about the Portal protocol?
Without a prior version check, an engineer configures IGMP snooping on a device and the version of IGMP snooping is earlier than the IGMP versions on user hosts. In this case, which of the following situations will occur?
A large enterprise deploys WLAN in VRRP HSB mode to ensure network reliability.
In this networking mode, which of the following data backup modes are supported?(Select all that apply)
By default, if no router ID is configured but multiple loopback interface addresses are configured, BGP selects the largest loopback interface address as the router ID.
An edge port is a new port role added to RSTP to overcome the disadvantages of STP. Which of the following statements is false about this port role?
As shown in the figure, SWA, SWB, and SWC run the Rapid Spanning Tree Protocol (RSTP). What are the roles of SWB's GE0/0/2 and SWC's GE0/0/1?
A non-client is an IBGP peer that functions as neither an RR nor a client. A non-client must establish fully meshed connections with the RR and all the other non-clients.
In the OSPF protocol, intra-area route calculation involves only Router LSA, Network LSA, and Summary LSA.
An OSPF AS-external LSA describes a route to an AS external network. When the field in the LSA is 0.0.0.0, the traffic destined for the external network is sent to the ASBR that imports this external route. (Enter the acronym in uppercase.)
Which of the following statements is false about BFD?

 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated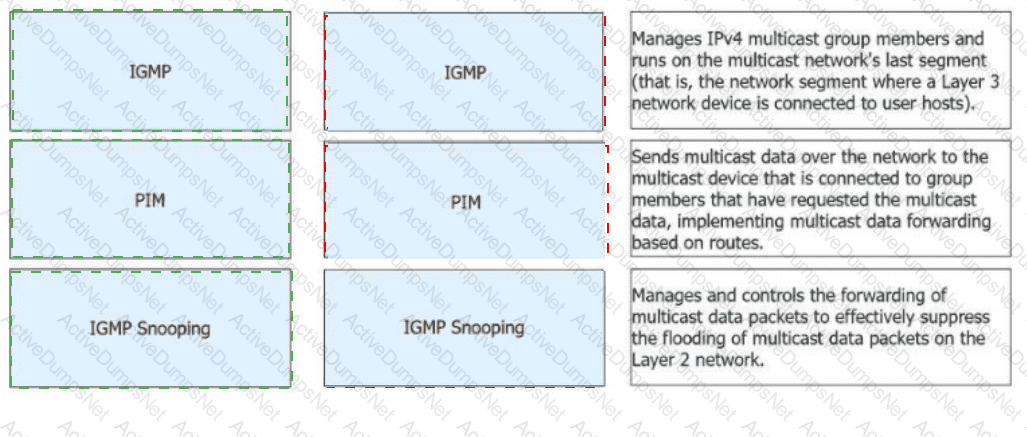
 A screenshot of a computer Description automatically generated
A screenshot of a computer Description automatically generated
