Huawei H12-722 Huawei Certified ICT Professional - Constructing Service Security Network (HCIP-Security-CSSN V3.0) Exam Practice Test
Huawei Certified ICT Professional - Constructing Service Security Network (HCIP-Security-CSSN V3.0) Questions and Answers
Misuse detection is through the detection of similar intrusions in user behavior, or those that use system flaws to indirectly violate system security rules
To detect intrusions in the system. Which of the following is not a feature of misuse detection 2
Regarding the description of file reputation technology in anti-virus engines, which of the following options is correct?
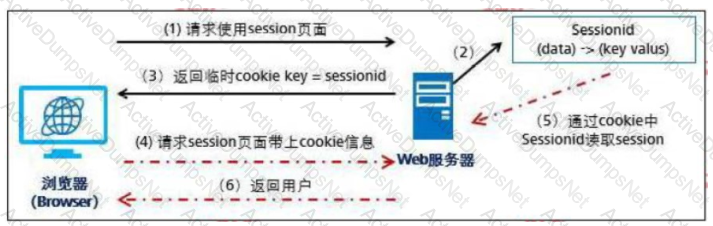
The process of a browser carrying a cookie to request resources from a server is shown in the following figure. Which of the following steps contains SessionID information in the message?
SQl injection attacks generally have the following steps:
①Elevate the right
②Get the data in the database
③Determine whether there are loopholes in the webpage
④ Determine the database type
For the ordering of these steps, which of the following options is correct?
Which of the following statements about IPS is wrong?
Regarding the Anti-DDoS cloud cleaning solution; which of the following statements is wrong?
The security management system is only optional, and anti-virus software or anti-hacking technology can be a good defense against network threats.
In the deployment of Huawei NIP6000 products, only port mirroring can be used for streaming replication.
The realization of content security filtering technology requires the support of the content security combination license.
Use BGP protocol to achieve diversion, the configuration command is as follows
[sysname] route-policy 1 permit node 1
[sysname-route-policy] apply community no-advertise
[sysname-route-policy] quit
[sysname]bgp100
155955cc-666171a2-20fac832-0c042c04
29
[sysname-bgp] peer
[sysname-bgp] import-route unr
[sysname- bgpl ipv4-family unicast
[sysname-bgp-af-ipv4] peer 7.7.1.2 route-policy 1 export
[sysname-bgp-af-ipv4] peer 7.7. 1.2 advertise community
[sysname-bgp-af-ipv4] quit
[sysname-bgp]quit
Which of the following options is correct for the description of BGP diversion configuration? (multiple choice)
Which of the following behaviors is a false positive of the intrusion detection system?
Which of the following options does not belong to the basic DDoS attack prevention configuration process?
Regarding HTTP behavior, which of the following statements is wrong?
Due to differences in network environment and system security strategies, intrusion detection systems are also different in specific implementation. From the perspective of system composition, the main
Which four major components are included?
Which of the following is the correct configuration idea for the anti-virus strategy?
1. Load the feature library
2. Configure security policy and reference AV Profile
3. Apply and activate the license
4. Configure AV Profile
5. Submit
For the description of URPF technology, which of the following options are correct? (multiple choice)
For the basic mode of HTTP Flood source authentication, which of the following options are correct? (multiple choice)
Content filtering is a security mechanism for filtering the content of files or applications through Huawei USCG00 products. Focus on the flow through deep recognition
Contains content, the device can block or alert traffic containing specific keywords.
Regarding the anti-spam local black and white list, which of the following statements is wrong?
Which of the following options will not pose a security threat to the network?
When you suspect that the company's network has been attacked by hackers, you have carried out a technical investigation. Which of the following options does not belong to the behavior that occurred in the early stage of the attack?
Which of the following technologies can achieve content security? (multiple choice)
The configuration command to enable the attack prevention function is as follows; n
[FW] anti-ddos syn-flood source-detect
[FW] anti-ddos udp-flood dynamic-fingerprint-learn
[FW] anti-ddos udp-frag-flood dynamic fingerprint-learn
[FW] anti-ddos http-flood defend alert-rate 2000
[Fwj anti-ddos htp-flood source-detect mode basic
Which of the following options is correct for the description of the attack prevention configuration? (multiple choice)
IPS is an intelligent intrusion detection and defense product. It can not only detect the occurrence of intrusions, but also can respond in real time through certain response methods.
Stop the occurrence and development of intrusions, and protect the information system from substantial attacks in real time. According to the description of PS, the following items are wrong?
USG6000V software logic architecture is divided into three planes: management plane, control plane and
Which of the following descriptions are correct for proxy-based anti-virus gateways? (multiple choice)
