Huawei H12-721 Huawei Certified ICT Professional - Constructing Infrastructure of Security Network Exam Practice Test
Huawei Certified ICT Professional - Constructing Infrastructure of Security Network Questions and Answers
What are the drainage schemes that can be used in the scenario of bypass deployment in Huawei's abnormal traffic cleaning solution?
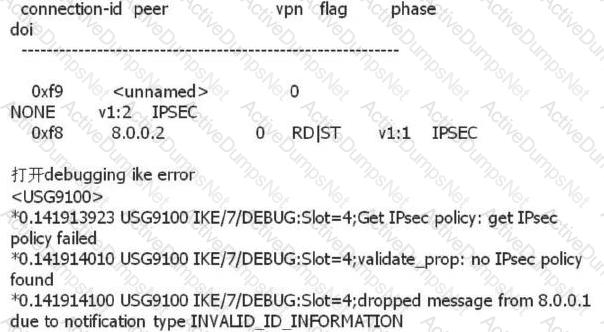
Two USG firewalls failed to establish an IPSec VPN tunnel through the NAT traversal mode. Run the display ike sa command to view the session without any UDP 500 session. What are the possible reasons?
A user SSL VPN authentication succeeds. The network extension is enabled on the PC. The assigned address has been obtained. The user PC cannot access the resources of the intranet server. Possible reasons?
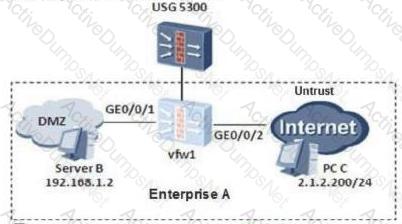
On the following virtual firewall network, the USG unified security gateway provides leased services to the enterprise. The VPN instance vfw1 is leased to enterprise A. The networking diagram is as follows. The PC C of the enterprise A external network user needs to access the intranet DMZ area server B through NAT. To achieve this requirement, what are the following key configurations?
What are the following attacks that are special message attacks?
Virtual firewall virtualizes multiple logical firewalls on a physical firewall device and implements multiple instances?
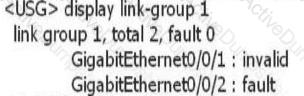
After the link-group is configured on the device, use the display link-group 1 command to obtain the following information. What information can I get?
The static fingerprint filtering function is to defend the attack traffic by configuring a static fingerprint to process the packets that hit the fingerprint. Generally, the anti-DDoS device capture function can be used to input fingerprint information to static fingerprint filtering.
In the L2TP over IPSec application scenario, the USG device encrypts the original data packet with IPSec and then encapsulates the packet with L2TP.
The traffic limiting policy feature only supports the number of connections initiated by the specified IP or the number of connections received.
Site to Site IPSec VPN Tunnel Negotiation Fails. How do I view the establishment and configuration of the IKE Phase 2 security association?
The classification of cyber-attacks includes traffic-based attacks, scanning and snooping attacks, malformed packet attacks, and special packet attacks.
Avoid DHCP server spoofing attacks. DHCP snooping is usually enabled. What is the correct statement?
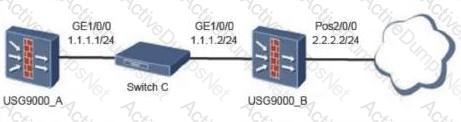
The topology diagram of the BFD-bound static route is as follows: The administrator has configured the following on firewall A: [USG9000_A] bfd [USG9000_A-bfd] quit [USG9000_A] bfd aa bind peer-ip 1.1.1.2 [USG9000_A- Bfd session-aa] discriminator local 10 [USG9000_A-bfd session-aa] discriminator remote 20 [USG9000_A-bfd session-aa] commit [USG9000_A-bfd session-aa] quit What are the correct statements about this segment?
The hot standby and IPSec functions are combined. Which of the following statements is correct?
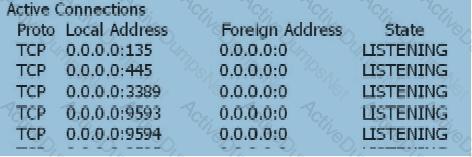
When the user's SSL VPN has been successfully authenticated, the user cannot access the Web-link resource. On the Web server, view the information as follows: netstat -anp tcp With the following information, which of the following statements is correct?
As shown in the figure, the firewall is dual-system hot standby. In this networking environment, all service interfaces of the firewall work in routing mode, and OSPF is configured on the upper and lower routers. Assume that the convergence time of OSPF is 30s after the fault is rectified. What is the best configuration for HRP preemption management?
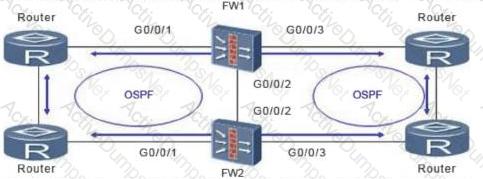
An administrator can view the IPSec status information and Debug information as follows. What is the most likely fault?
If the IPSec policy is configured in the policy template and sub-policy mode, the firewall applies the policy template first and then applies the sub-policy.
Which of the following statements is true about L2TP over IPSec VPN?
USG A and USG B are configured with a static BFD session. The following is true about the process of establishing and tearing down a BFD session.
The default interval for sending VGMP hello packets is 1 second. That is, when the hello packet sent by the peer is not received within the range of three hello packets, the peer is considered to be faulty. Master status.
The Tracert packet attack is an ICMP timeout packet returned by the attacker when the TTL is ____, and the ICMP port unreachable packet returned when the destination address is reached to find the path through which the packet arrives at the destination. Spying on the structure of the network
What is the correct statement about the ip-link feature?
For IP-MAC address binding, packets with matching IP and MAC address will enter the next processing flow of the firewall. Packets that do not match IP and MAC address will be discarded.
Which of the following statements is correct about the IKE main mode and the aggressive mode?
In the case of IPSec VPN NAT traversal, you must use IKE's aggressive mode.
When an IPSec VPN is set up on both ends of the firewall, the security ACL rules of both ends are mirrored.
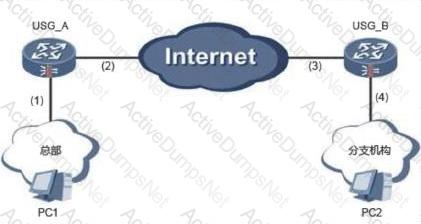
The branch firewall of an enterprise is configured with NAT. As shown in the figure, USG_B is the NAT gateway. The USG_B is used to establish an IPSec VPN with the headquarters. Which parts of the USG_B need to be configured?
The SSL VPN authentication login is unsuccessful and the message "Bad username or password" is displayed. Which one is wrong?
Which of the following is incorrect about IKE V1 and IKE V2?
