HP HPE7-A02 Aruba Certified Network Security Professional Exam Exam Practice Test
Aruba Certified Network Security Professional Exam Questions and Answers
A company wants to apply a standard configuration to all AOS-CX switch ports and have the ports dynamically adjust their configuration based on the identity of
the user or device that connects. They want to centralize configuration of the identity-based settings as much as possible.
What should you recommend?
You are establishing a cluster of HPE Aruba Networking ClearPass servers. (Assume that they are running version 6.9.).
For which type of certificate it is recommended to install a CA-signed certificate on the Subscriber before it joins the cluster?
You are establishing a cluster of HPE Aruba Networking ClearPass servers. (Assume that they are running version 6.9.).
For which type of certificate is it recommended to install a CA-signed certificate on the Subscriber before it joins the cluster?
Refer to Exhibit:
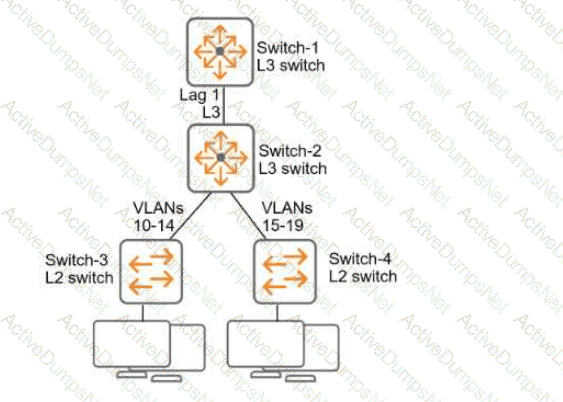
All of the switches in the exhibit are AOS-CX switches.
What is the preferred configuration on Switch-2 for preventing rogue OSPF routers in this network?
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to periodically poll Microsoft Endpoint Manager (formerly Intune) for attributes about its managed clients.
What should you do on ClearPass to permit this integration?
Refer to Exhibit.

A company is using HPE Aruba Networking ClearPass Device Insight (CPDI) (the standalone application). In the CPDI interface, you go to the Generic Devices
page and see the view shown in the exhibit.
What correctly describes what you see?
You have created this rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) service's enforcement policy: IF Authorization [Endpoints Repository]
Conflict EQUALS true THEN apply "quarantine_profile"
What information can help you determine whether you need to configure cluster-wide profiler parameters to ignore some conflicts?
A company assigns a different block of VLAN IDs to each of its access layer AOS-CX switches. The switches run version 10.07. The IDs are used for standard
purposes, such as for employees, VolP phones, and cameras. The company wants to apply 802.1X authentication to HPE Aruba Networking ClearPass Policy
Manager (CPPM) and then steer clients to the correct VLANs for local forwarding.
What can you do to simplify setting up this solution?
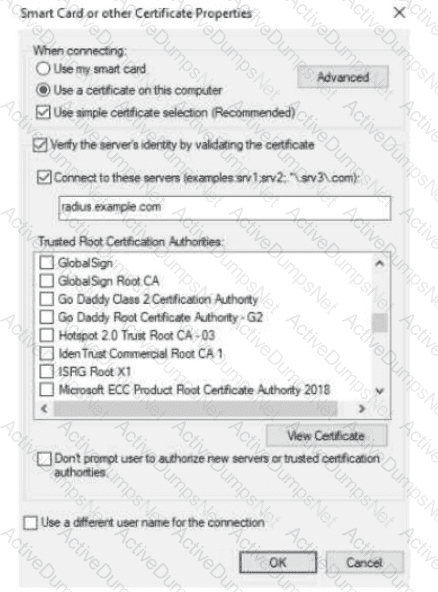
The exhibit shows the 802.1X-related settings for Windows domain clients. What should admins change to make the settings follow best security practices?
An AOS-CX switch has this admin user account configured on it:
netadmin in the operators group.
You have configured these commands on an AOS-CX switch:
tacacs-server host cp.example.com key plaintext &12xl,powmay7855
aaa authentication login ssh group tacacs local
aaa authentication allow-fail-through
A user accesses the switch with SSH and logs in as netadmin with the correct password. When the switch sends a TACACS+ request to the ClearPass server at cp.example.com, the server does not send a response. Authentication times out.
What happens?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI) and has integrated the
two. CPDI admins have created a tag. CPPM admins have created rules that use that tag in the wired 802.1X and wireless 802.1X services' enforcement policies.
The company requires CPPM to apply the tag-based rules to a client directly after it learns that the client has that tag.
What is one of the settings that you should verify on CPPM?
HPE Aruba Networking switches are implementing MAC-Auth to HPE Aruba Networking ClearPass Policy Manager (CPPM) for a company's printers. The company wants to quarantine a client that spoofs a legitimate printer's MAC address. You plan to add a rule to the MAC-Auth service enforcement policy for this purpose. What condition should you include?
A company has AOS-CX switches and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants switches to implement 802.1X
authentication to CPPM and download user roles.
What is one task that you must complete on the switches to support this use case?
You have set up a mirroring session between an AOS-CX switch and a management station, running Wireshark. You want to capture just the traffic sent in the
mirroring session, not the management station's other traffic.
What should you do?
A company lacks visibility into the many different types of user and loT devices deployed in its internal network, making it hard for the security team to address
those devices.
Which HPE Aruba Networking solution should you recommend to resolve this issue?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. You want
to assign managers to groups on the AOS-CX switch by name.
How do you configure this setting in a CPPM TACACS+ enforcement profile?
What is a use case for running periodic subnet scans on devices from HPE Aruba Networking ClearPass Policy Manager (CPPM)?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. The company wants CPPM to control which commands managers are allowed to enter.
Which service must you add to the managers' TACACS+ enforcement profile?
You need to create a rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) role mapping policy that references a ClearPass Device Insight Tag. Which Type (namespace) should you specify for the rule?
Refer to the exhibit.

The exhibit shows a saved packet capture, which you have opened in Wireshark. You want to focus on the complete conversation between 10.1.70.90 and 10.1.79.11 that uses source port 5448.
What is a simple way to do this in Wireshark?
Refer to the exhibit.
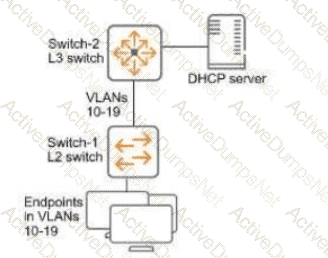
You have verified that AOS-CX Switch-1 has constructed an IP-to-MAC binding table in VLANs 10-19. Now you need to enable ARP inspection for the endpoint connected to Switch-1. What must you do first to prevent traffic disruption?
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to respond to Syslog messages from its Palo Alto Next Generation Firewall (NGFW)
by quarantining clients involved in security incidents.
Which step must you complete to enable CPPM to process the Syslogs properly?
You have enabled "rogue AP containment" in the Wireless IPS settings for a company’s HPE Aruba Networking APs. What form of containment does HPE Aruba Networking recommend?
Your company wants to implement Tunneled EAP (TEAP).
How can you set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to enforce certificated-based authentication for clients using TEAP?
You are using OpenSSL to obtain a certificate signed by a Certification Authority (CA). You have entered this command:
openssl req -new -out file1.pem -newkey rsa:3072 -keyout file2.pem
Enter PEM pass phrase: **********
Verifying - Enter PEM pass phrase: **********
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:California
Locality Name (eg, city) []:Sunnyvale
Organization Name (eg, company) [Internet Widgits Pty Ltd]:example.com
Organizational Unit Name (eg, section) []:Infrastructure
Common Name (e.g. server FQDN or YOUR name) []:radius.example.com
What is one guideline for continuing to obtain a certificate?
An AOS-CX switch has been configured to implement UBT to two HPE Aruba Networking gateways that implement VRRP on the users' VLAN. What correctly describes how the switch tunnels UBT users' traffic to those gateways?
What correctly describes an HPE Aruba Networking AP's Device (TPM) certificate?
You are using Wireshark to view packets captured from HPE Aruba Networking infrastructure, but you’re not sure that the packets are displaying correctly. In which circumstance does it make sense to configure Wireshark to ignore protection bits with the IV for the 802.11 protocol?
A company wants to turn on Wireless IDS/IPS infrastructure and client detection at the high level on HPE Aruba Networking APs. The company does not want to
enable any prevention settings.
What should you explain about HPE Aruba Networking recommendations?
A company needs to enforce 802.1X authentication for its Windows domain computers to HPE Aruba Networking ClearPass Policy Manager (CPPM). The
company needs the computers to authenticate as both machines and users in the same session.
Which authentication method should you set up on CPPM?
What is one use case that companies can fulfill using HPE Aruba Networking ClearPass Policy Manager's (CPPM's) Device Profiler?
Refer to the exhibit:
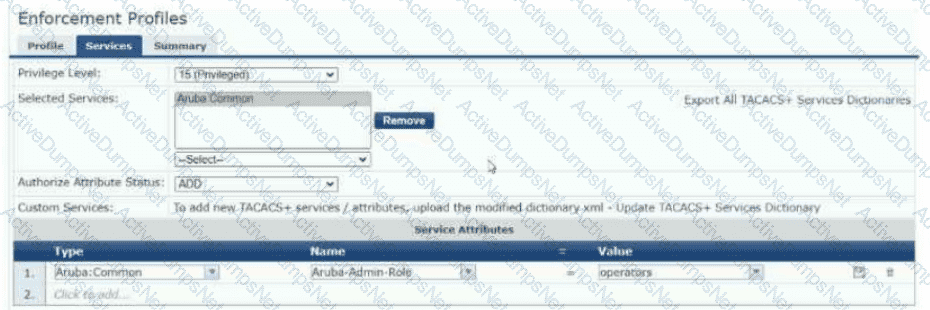
The exhibit shows the TACACS+ enforcement profile that HPE Aruba Networking ClearPass Policy Manager (CPPM) assigns to a manager. When this manager logs into an AOS-CX switch, what does the switch do?
HPE Aruba Networking Central displays an alert about an Infrastructure Attack that was detected. You go to the Security > RAPIDS events and see that the attack was "Detect adhoc using Valid SSID." What is one possible next step?
A company has HPE Aruba Networking APs, which authenticate users to HPE Aruba Networking ClearPass Policy Manager (CPPM).
What does HPE Aruba Networking recommend as the preferred method for assigning clients to a role on the AOS firewall?
A company has AOS-CX switches. The company wants to make it simpler and faster for admins to detect denial of service (DoS) attacks, such as ping or ARP floods, launched against the switches.
What can you do to support this use case?
You are configuring the HPE Aruba Networking ClearPass Device Insight Integration settings on ClearPass Policy Manager (CPPM). For which use case should you set the 'Tag Updates Action" to "apply for all tag updates"?
You have created a Web-based Health Check Service that references a posture policy. You want the service to trigger a RADIUS change of authorization (CoA) when a client receives a Healthy or Quarantine posture. Where do you configure those rules?
A company has HPE Aruba Networking Central-managed APs. The company wants to block all clients connected through the APs from using YouTube.
Which steps should you take?
A company has AOS-CX switches at the access layer, managed by HPE Aruba Networking Central. You have identified suspicious activity on a wired client. You want to analyze the client's traffic with Wireshark, which you have on your management station.
What should you do?
HPE Aruba Networking Central displays an alert about an Infrastructure Attack that was detected. You go to the Security > RAPIDS events and see that the attack
was "Detect adhoc using Valid SSID."
What is one possible next step?
