A network administrator applies port security to a port with the send-alarm action. What does the switch do if it detects traffic from an unauthorized MAC address on the port?
Refer to the exhibits.
Exhibit 1
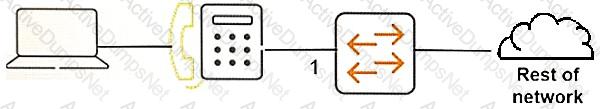
Exhibit 2
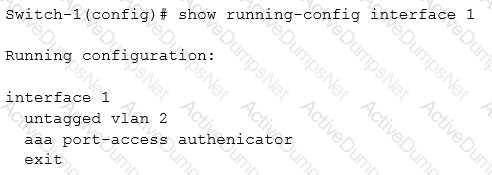
The IP phone in the exhibit is set up to complete 802.1x authentication to the network. How can the netwotk administrator prevent a user on the computer from receiving network access without authentication?
Which switches can be deployed in a mesh topology for backplane stacking?
Refer to the exhibit.
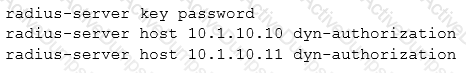
AOS-Switches will enforce 802.1X authentication on edge ports. The company has two RADIUS servers, which are meant to provide redundancy and load sharing of requests. The exhibit shows the planned RADIUS setting to deploy to the switches.
Which adjustment to the plan should administrators make in order to meet the customers’ requirements?
A network administrator plans to apply DSCP 46 to all traffic on a port. What is required for this configuration to work?
What is a reason to create a virtual link between two OSPF routers?
Refer to the exhibit.
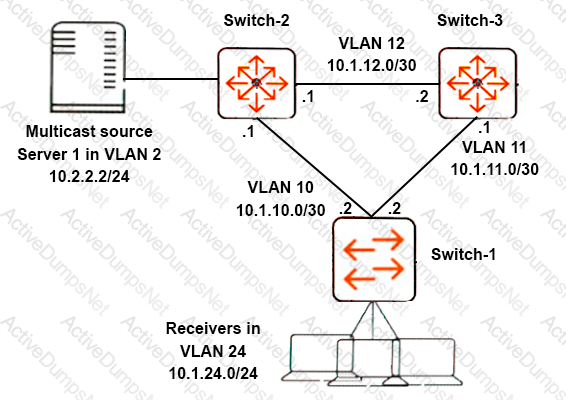
Network administrators set up PIM-DM to route multicast traffic from Server 1 to clients in VLAN 24. The multicasts are not active now, but the administrators want to determine which path the multicasts will take.
What should the administrators check to help them calculate this path?
Refer to the exhibit.
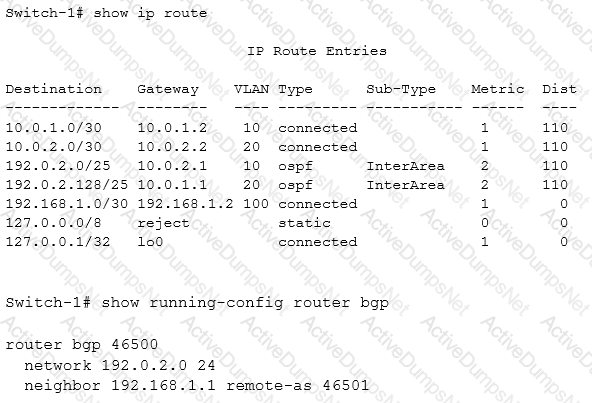
What must the network administrator do on Switch-1 to enable this switch to advertise 192.0.2.0/24 to the router at 192.168.1.1?
What is a reason to implement PIM-DM as opposed to PIM-SM?
A network administrator needs to control traffic based on TCP or UDP application, as well as IP protocol, such as GRE or ICMP. What should the administrator configure for this purpose?
A network administrator can set the OSPF metric-type on an AOS-Switch to Type 1 or Type 2. What is the difference?
Refer to the exhibits.
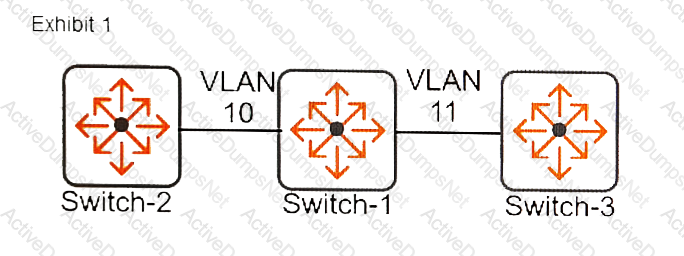
Exhibit 2
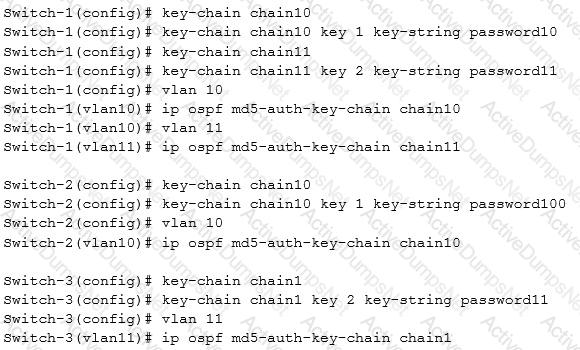
The network administrator configures the commands shown in Exhibit 2. Which mismatch will cause an issue?
The security policy for a company requires that switches use SNMPv3 and accept all read-only SNMPv2c messages. The network administrator enables SNMPv3. Which additional action should the network administrator take to comply with this policy?
An AOS-Switch enforces 802.1X. It receives an Access-Accept with this HPE VSA from its Radius server:
Attribute Name and ID = HPE-User-Role (25) Value = contractor
The switch then rejects the client. What is one requirement for the switch to accept the message and authorize the client?
The security plan for AOS-Switches requires protection from incoming malware traffic generated from a worm-or virus-infected host.
Which feature should be implemented to provide the required protection?
Which situation requires an AOS-Switch interface to support MAC-based VLANs?
What is a reason for hello packets between two OSPF routers?
Refer to the exhibits.
Exhibit 1
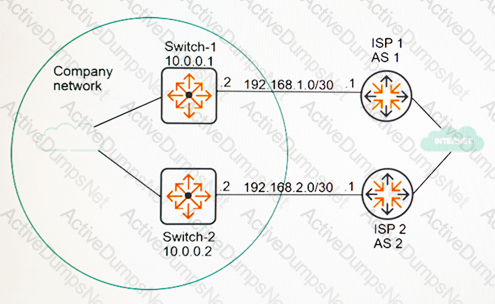
Exhibit 2

Exhibit 1 shows a portion of the BGP routing table when the BGP solution was first deployed. Exhibit 2 shows the same portion at the current time. What can explain the current state?
A company wants to implement RADIUS authentication of all managers who log in to AOS-Switches via SSH. The RADIUS server also sends VSAs that indicate which commands users can enter, and switches must honor these.
What must the administrator do to meet the company’s requirements?
Refer to the exhibit.
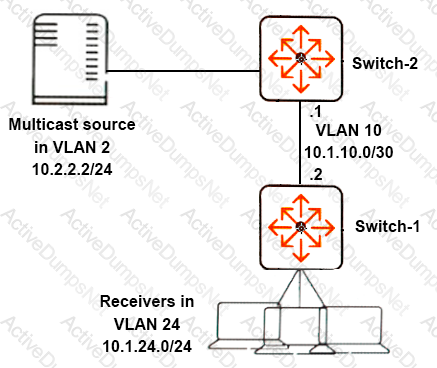
Network administrators want the network to use PIM-DM to route multicasts from Server 1 to receivers in VLAN 24.
Which protocols should the administrators enable on which VLANs on Switch-1?
A network administrator configures VSF settings on two Aruba 2930F switches. The switches form two separate VSF fabrics. What should the administrator check?
Refer to the exhibit.
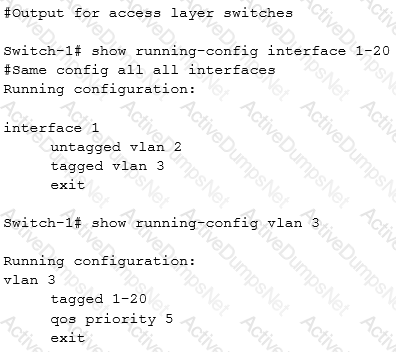
A company has IP phones that are LLDP-MED capable. The exhibit shows the configuration for the VLAN to which IP phones belong, as well as the configuration for ports to which phones will connect. AOS-Switches at the access layer are set up to use LLDP-MED. The administrator wants to automatically provision the phones to send traffic with the right VLAN tag and priority.
Which additional configuration step must the administrator complete?
Refer to the exhibit.
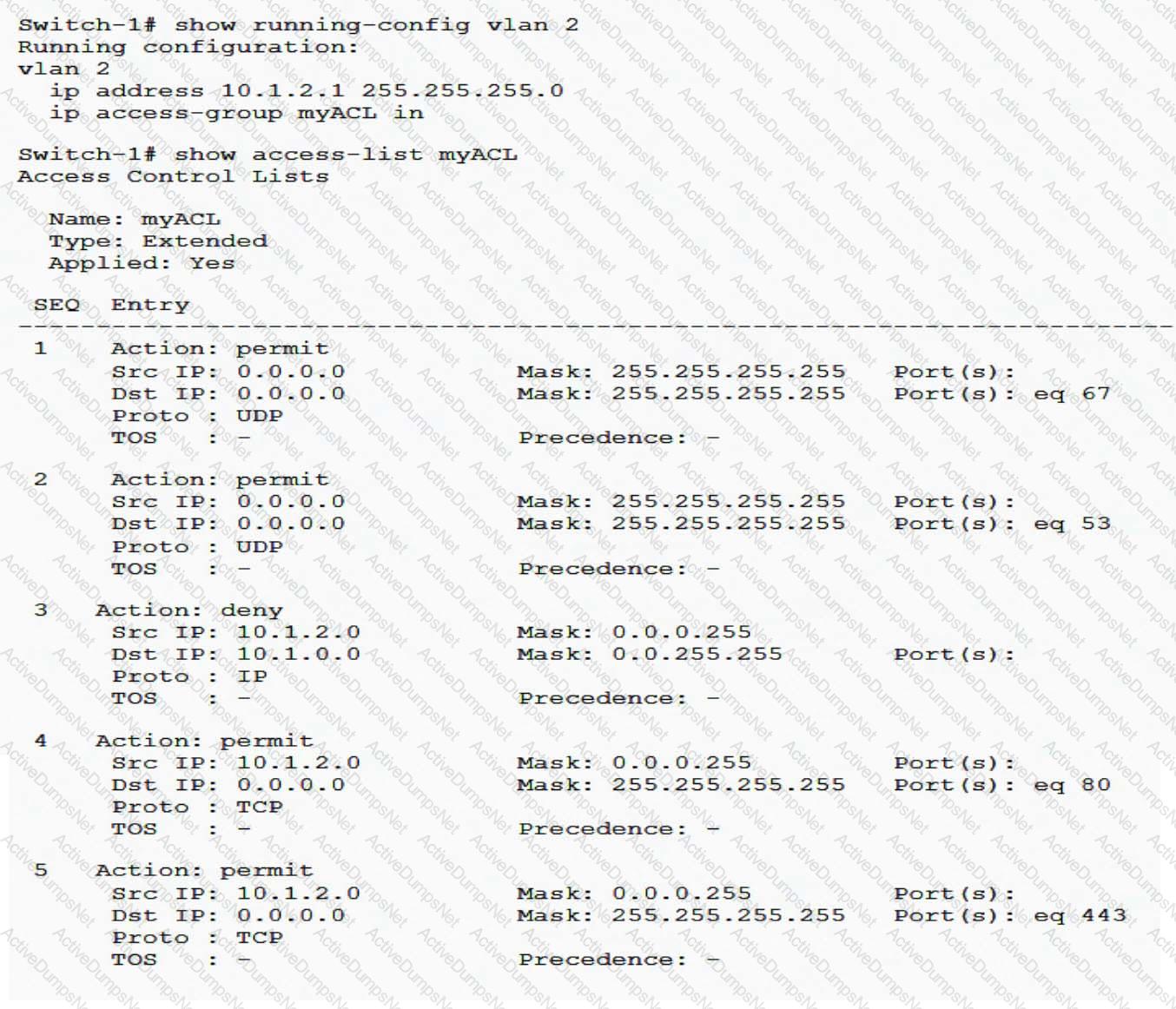
A network administrator needs to alter myACL so that it permits all traffic that arrives in VLAN 2 and is destined to 10.1.10.0/24. Besides this change, the ACL must continue to act as it does now. The administrator plans this new rule:
permit ip any 10.1.10.0/24
How should the administrator apply this rule to meet all requirements?
Network administrators want to gain insight into network utilization, traffic patterns, and the types of applications in use across the network over the long term.
Which technology can help them achieve this goal?
Refer to the exhibits.
Exhibit 1
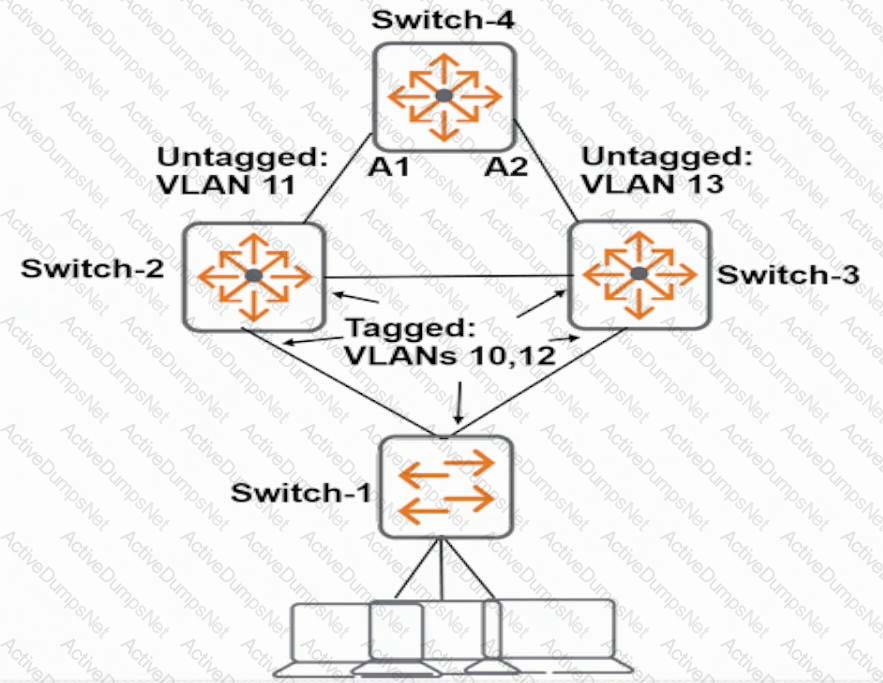
Exhibit 2
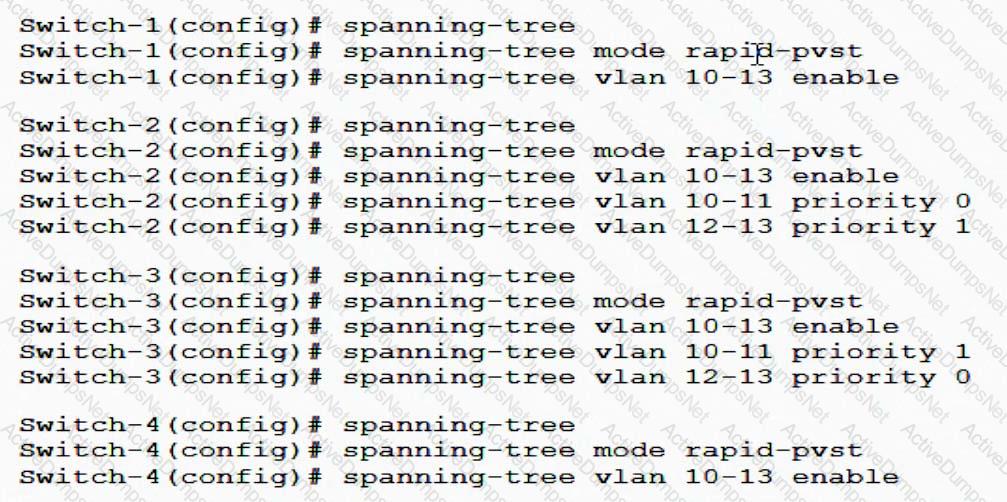
The network administrator enters the commands shown in Exhibit 2. What is the spanning tree status on A1 and A2?