GIAC GSSP-Java GIAC Secure Software Programmer – Java Exam Practice Test
GIAC Secure Software Programmer – Java Questions and Answers
The java.util.logging package provides the classes and interfaces of the Java platform's core logging facilities. Which of the following are the main target uses of logs?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following syntaxes can be used to retrieve a URL to a resource specified as WEBINF/example/sessionObject.txt?
Note. Assume that session is an instance of the HttpSession interface, request is an instance of the HttpServletRequest interface, and context is an instance of the ServletContext interface.
Peter works as a Software Developer for Neon Inc. He is developing an application in Java. He declares an interface. Which of the following field declarations are valid within the body of an interface?
Each correct answer represents a complete solution. Choose three.
You work as programmer for PassGuide.Inc. You have purchased a Web application named
SecureProgrammer that uses the programmatic authorization, and the security roles that are not used in your organization. Which of the following deployment descriptor elements must you use so that the SecureProgrammer application can work with your organization?
Which of the following statements about data integrity of a container are true?
Each correct answer represents a complete solution. Choose two.
Which of the following classes is an engine class designed to provide conversions between opaque cryptographic keys and allows you to build an opaque key object from a given key specification?
Which of the following elements contains the
Mark works as a Programmer for InfoTech Inc. He develops a code snippet for a class named
servletClassA that extends the HttpServlet class. Which of the following HttpServlet class methods are not required to be overridden by the servletClassA?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements about various authentication mechanisms in J2EE are true?
You work as a Software Developer for UcTech Inc. You are building a Web site that will contain study materials on the Java language. The company wants that members can access all the pages, but nonmembers have only limited access to the Web site pages. Which of the following security mechanisms will you use to accomplish the task?
Given the following directory structure.

Assuming that the current directory is com, which of the below options can be used to create a jar file called TestJar.jar that contains all the files from the directory testApp?
Rachel works as a Software Developer for Vivanet Inc. She writes the following code using Java.
class catchexcp
{public static void metha()
{int x=4/0;System.out.print("Caught exception");}
public static void main(String args[])
{try{metha();}catch(ArithmeticException ae){System.out.print("Caught ArithmeticException");}finally{try{metha();}catch(ArithmeticException ae){System.out.print("ReCaught ArithmeticException");}}}}
What will happen when she tries to compile and execute the code?
Which of the following validates an HTML form at client-side before submitting it to the server?
Mark works as a Programmer for InfoTech Inc. He develops a RefreshFailed.jsp page for a servlet. He wants that the RefreshFailed.jsp page will be displayed when the
javax.security.auth.RefreshFailedException is thrown. Which of the following error-page deployment descriptor element declarations will be used?
Mark works as a Programmer for InfoTech Inc. He develops a session bean class named
accountService. Which of the following rules must be conformed by the session bean class?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Software Developer for BlueTech Inc. You create code using EJB 3.0. You want to ensure that each new record is checked for validation before it is inserted into the database. Which of the following callback methods will you use to write the logic for validation?
Harry works as a Software Developer for SoftTech Inc. He has developed a Java application to perform various SQL statements such as INSERT, UPDATE, etc., against a database table named Employee. He has used the executeUpdate() method to perform various SQL queries and to know the exact affected rows in the database if any of the operations is performed against the database table.
Which of the following types of values is returned by this method?
What will be the output of the following program?
class Stringtest
{
public static void main(String args[])
{
String s= "test";
s.concat("paper");
System.out.println(s);
}
}
Which of the following statements about the String, StringBuffer, and StringBuilder classes are true?
Each correct answer represents a complete solution. Choose all that apply.
You have created a Java application that will retrieve and insert data into a database table. Which of the following objects will you use to pass the JDBC Driver to obtain a connection to the database server?
You work as a Programmer for InfoTech Inc and develop the following two
declarations.
</auth-constraint>
Which of the following statements is true about the
Which of the following exceptions will be thrown if the caller does not have permission to invoke the doAsPrivileged method?
You work as a Software Developer for UcTech Inc. You create a session using the HttpSession interface. You want the attributes to be informed when the session is moved from one JVM to another and also when an attribute is added or removed from the session. Which of the following interfaces can you use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Sam works as a Software Developer for Gentech Inc. He writes the following code.
1. class TryFinallyTest {
2. public static void main(String[] args) {
3. try {
4. int i=15/0;
5. System.out.println("Testing Try");
6. }
7. catch(ArithmeticException ae) {
8. System.out.println("Arithmetic exception");
9. }
10. System.out.println("Correct");
11. finally {
12. System.out.println("Must execute");
13. }
14. }
15. }
What will happen when he attempts to compile and execute the code?
Which of the following classes is an engine class that provides an opaque representation of cryptographic parameters?
Which of the following statements are true about object serialization?
Each correct answer represents a complete solution. Choose all that apply.
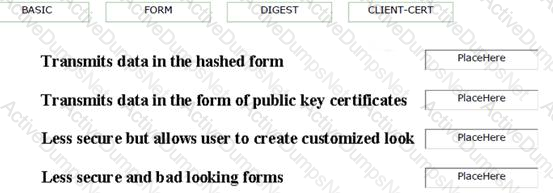
Drag and drop the appropriate authentication types from the given options to match their properties.
You write the following code.
class Father {public void Method() {System.out.println("I am Father");}}
public class Son extends Father {public static void main(String argv[]) {Son son = new Son();son.Method();}
private void Method() {System.out.println("I am Son");}}
Which of the following will be the result, when you try to compile and run the code?
Which of the following annotations specifies the roles that are allowed to invoke a particular bean method?
Which of the following exceptions will be thrown if a cipher is in decryption mode but the decrypted data is not bounded by the appropriate bytes?
Which of the following exceptions will be thrown if the checkSecurityAccess() method uses an empty target as its parameter value?
Which of the following is the return type of the getInitParameter() method of the ServletContext interface?
Which of the following methods throws a SecurityException if the calling thread is not allowed to open a socket connection to the specified host and port number?
Which of the following exceptions will be thrown if the commit() method fails?
Which of the following statements about the String, StringBuffer, and StringBuilder classes are true?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements is true about the Java synchronized keyword?
Which of the following statements are true?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following elements is used as a parameter in the EJBContext.isCallerInRole() method?
The ______________ method of the EJBContext interface tests whether the client is a member of the role specified in the argument to the method.
Which of the following deployment descriptor elements is used to declare the reference of a
client's application to an external resource?
You have written the following code snippet.
1. public class Read {
2. protected int ReadText(int x) { return 0; }
3. }
4. class Text extends Read {
5. /*insert code here*/
6. }
Which of the following methods, inserted independently at line 5, will compile?
Each correct answer represents a complete solution. Choose all that apply.
