GIAC GSNA GIAC Systems and Network Auditor Exam Practice Test
GIAC Systems and Network Auditor Questions and Answers
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the list of the filesystems mounted automatically at startup by the mount -a command in the /etc/rc startup file. Which of the following Unix configuration files can you use to accomplish the task?
You work as a professional Ethical Hacker. You are assigned a project to perform blackbox testing of the security of www.we-are-secure.com. Now you want to perform banner grabbing to retrieve information about the Webserver being used by we-are-secure. Which of the following tools can you use to accomplish the task?
Which of the following is a wireless auditing tool that is used to pinpoint the actual physical location of wireless devices in the network?
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system. Which of the following Unix commands can you use to accomplish the task?
What does CSS stand for?
Which of the following statements is true about a relational database?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He notices that UDP port 137 of the We-are-secure server is open. Assuming that the Network Administrator of We-are-secure Inc. has not changed the default port values of the services, which of the following services is running on UDP port 137?
Which of the following tools works both as an encryption-cracking tool and as a keylogger?
Which of the following mechanisms is closely related to authorization?
Which of the following statements about a perimeter network are true? (Choose three)
You work as a Network Administrator for TechPerfect Inc. The company has a secure wireless network. Since the company's wireless network is so dynamic, it requires regular auditing to maintain proper security. For this reason, you are configuring NetStumbler as a wireless auditing tool. Which of the following statements are true about NetStumbler?
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system. He wants to sniff the we-are-secure network and intercept a conversation between two employees of the company through session hijacking. Which of the following tools will John use to accomplish the task?
Which of the following statements are true about data aggregation?
Which of the following controls define the direction and behavior required for technology to function properly?
Which of the following commands can be used to convert all lowercase letters of a text file to uppercase?
John used to work as a Network Administrator for We-are-secure Inc. Now he has resigned from the company for personal reasons. He wants to send out some secret information of the company. To do so, he takes an image file and simply uses a tool image hide and embeds the secret file within an image file of the famous actress, Jennifer Lopez, and sends it to his Yahoo mail id. Since he is using the image file to send the data, the mail server of his company is unable to filter this mail. Which of the following techniques is he performing to accomplish his task?
Which of the following are known as safety critical software?
This is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards. The main features of these tools are as follows: It displays the signal strength of a wireless network, MAC address, SSID, channel details, etc. It is commonly used for the following purposes: a.War driving b.Detecting unauthorized access pointsc.Detecting causes of interference on a WLAN d.WEP ICV error trackinge.Making Graphs and Alarms on 802.11 Data, including Signal Strength This tool is known as __________.
Which of the following is a type of web site monitoring that is done using web browser emulation or scripted real web browsers?
Mark works as the Network Administrator for XYZ CORP. The company has a Unix-based network. Mark wants to scan one of the Unix systems to detect security vulnerabilities. To accomplish this, he uses TARA as a system scanner. What can be the reasons that made Mark use TARA?
Which of the following types of attack is described in the statement below? "It is a technique employed to compromise the security of network switches. In this attack, a switch is flooded with packets, each containing different source MAC addresses. The intention is to consume the limited memory set aside in the switch to store the MAC address-to-physical port translation table."
Which of the following protocols is the mandatory part of the WPA2 standard in the wireless networking?
You work as the Network Administrator for XYZ CORP. The company has a Linux-based network. You are a root user on the Red Hat operating system. You want to see first five lines of the file /etc/passwd. Which of the following commands should you use to accomplish the task?
In which of the following does a Web site store information such as user preferences to provide customized services to users?
Which of the following processes is described in the statement below? "This is the process of numerically analyzing the effect of identified risks on overall project objectives."
John works as a Network Administrator for Perfect Solutions Inc. The company has a Debian Linux-based network. He is working on the bash shell in which he creates a variable VAR1. After some calculations, he opens a new ksh shell. Now, he wants to set VAR1 as an environmental variable so that he can retrieve VAR1 into the ksh shell. Which of the following commands will John run to accomplish the task?
Data access auditing is a surveillance mechanism that watches over access to all sensitive information contained within the database. What are the questions addressed in a perfect data access auditing solution?
Which of the following Web attacks is performed by manipulating codes of programming languages such as SQL, Perl, Java present in the Web pages?
You work as a Database Administrator for XYZ CORP. The company has a multi-platform network. The company requires fast processing of the data in the database of the company so that answers to queries can be generated quickly. To provide fast processing, you have a conceptual idea of representing the dimensions of data available to a user in the data cube format. Which of the following systems can you use to implement your idea?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He performs Web vulnerability scanning on the We-are-secure server. The output of the scanning test is as follows: C.\whisker.pl -h target_IP_address -- whisker / v1.4.0 / rain forest puppy / www.wiretrip.net -- = - = - = - = - = = Host: target_IP_address = Server: Apache/1.3.12 (Win32) ApacheJServ/1.1 mod_ssl/2.6.4 OpenSSL/0.9.5a mod_perl/1.22 + 200 OK: HEAD /cgi-bin/printenv John recognizes /cgi-bin/printenv vulnerability ( 'Printenv' vulnerability) in the We_are_secure server. Which of the following statements about 'Printenv' vulnerability are true?
You work as an Exchange Administrator for XYZ CORP. The network design of the company is given below:
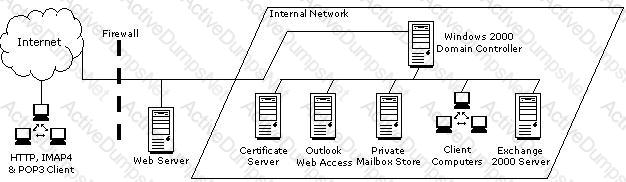
Employees are required to use Microsoft Outlook Web Access to access their emails remotely. You are required to accomplish the following goals: Ensure fault tolerance amongst the servers. Ensure the highest level of security and encryption for the Outlook Web Access clients. What will you do to accomplish these goals?
Which of the following protocols are used to provide secure communication between a client and a server over the Internet? (Choose two)
You work as a Network Administrator for Infosec Inc. Nowadays, you are facing an unauthorized access in your Wi-Fi network. Therefore, you analyze a log that has been recorded by your favorite sniffer, Ethereal. You are able to discover the cause of the unauthorized access after noticing the following string in the log file: (Wlan.fc.type_subtype eq 32 and llc.oui eq 0x00601d and llc.pid eq 0x0001) When you find All your 802.11b are belong to us as the payload string, you are convinced about which tool is being used for the unauthorized access. Which of the following tools have you ascertained?
You work as the Network Administrator of a Windows 2000 Active Directory network. Your company's offices are at Dallas and New York. Your company wants to configure a secure, direct Internet link. The company's management wants to accomplish the following tasks: Keep the offices' internal resources secure from outsiders. Keep communication secure between the two offices. You install a firewall in each office. Which of the tasks does this action accomplish?
You work as a Network Administrator for Tech-E-book Inc. You are configuring the ISA Server 2006 firewall to provide your company with a secure wireless intranet. You want to accept inbound mail delivery though an SMTP server. What basic rules of ISA Server do you need to configure to accomplish the task.
You are the Security Consultant and have been hired to check security for a client's network. Your client has stated that he has many concerns but the most critical is the security of Web applications on their Web server. What should be your highest priority then in checking his network?
Which of the following is used to execute a SQL statement from the SQL buffer?
You are the Security Consultant and you frequently do vulnerability assessments on client computers. You want to have a standardized approach that would be applicable to all of your clients when doing a vulnerability assessment. What is the best way to do this?
You are the Security Administrator for an Internet Service Provider. From time to time your company gets subpoenas from attorneys and law enforcement for records of customers' access to the internet. What policies must you have in place to be prepared for such requests?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to perform a stealth scan to discover open ports and applications running on the We-are-secure server. For this purpose, he wants to initiate scanning with the IP address of any third party. Which of the following scanning techniques will John use to accomplish his task?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully completed the following pre-attack phases while testing the security of the server: Footprinting Scanning Now he wants to conduct the enumeration phase. Which of the following tools can John use to conduct it?
Which of the following techniques can be used to determine the network ranges of any network?
You work as a Database Administrator for Dolliver Inc. The company uses Oracle 11g as its database. You have used the LogMiner feature for auditing purposes. Which of the following files store a copy of the data dictionary? (Choose two)
Which of the following is a technique of using a modem to automatically scan a list of telephone numbers, usually dialing every number in a local area code to search for computers, Bulletin board systems, and fax machines?
Which of the following statements are true about KisMAC?
You work as the Network Administrator for XYZ CORP. The company has a Unix-based network. You want to see the username, real name, home directory, encrypted password, and other information about a user. Which of the following Unix configuration files can you use to accomplish the task?
In which of the following social engineering attacks does an attacker first damage any part of the target's equipment and then advertise himself as an authorized person who can help fix the problem.
Which of the following methods will free up bandwidth in a Wireless LAN (WLAN)?
Which of the following does an anti-virus program update regularly from its manufacturer's Web site?
You want to record auditing information in the SYS.AUD$ table, and also want to record SQL bind variables as well as the SQL text in the audit trail. Which of the following statements will accomplish this task?
Which of the following tools is a Windows-based commercial wireless LAN analyzer for IEEE 802.11b and supports all high level protocols such as TCP/IP, NetBEUI, and IPX?
Which of the following policies helps reduce the potential damage from the actions of one person?
What does a firewall check to prevent certain ports and applications from getting the packets into an Enterprise?
You work as a Network Administrator for NTY Inc. The company has a secure wireless network. While auditing the network for maintaining security, you find an unknown node. You want to locate that node. Which tool will you use to pinpoint the actual physical location of the node?
Which of the following are the limitations for the cross site request forgery (CSRF) attack?

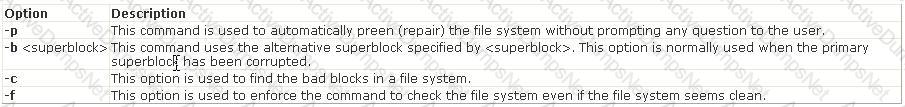 C:\Documents and Settings\user-nwz\Desktop\1.JPG
C:\Documents and Settings\user-nwz\Desktop\1.JPG