GIAC GSLC GIAC Security Leadership Certification (GSLC) Exam Practice Test
GIAC Security Leadership Certification (GSLC) Questions and Answers
Which model is a software development process combining elements of both design and prototyping-in-stages, in an effort to combine advantages of top-down and bottom-up concepts?
Which of the following is responsible for maintaining certificates in a public key infrastructure (PKI)?
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. The company's headquarters is located at Los Angeles. A branch office of the company is located at Denver. You are about to send a message to Rick who is a Network Administrator at Denver. You want to ensure that the message cannot be read by anyone but the recipient. Which of the following keys will you use to encrypt the message?
Which of the following terms describes an attempt to transfer DNS zone data?
Which of the following statements about a host-based intrusion prevention system (HIPS) are true?
Each correct answer represents a complete solution. Choose two.
Which of the following is a fake target that deters hackers from locating your real network?
You work as a Network Administrator in a company. The NIDS is implemented on the network.
You want to monitor network traffic. Which of the following modes will you configure on the network interface card to accomplish the task?
Which of the following uses public key cryptography to encrypt the contents of files?
Which of the following are the countermeasures against a man-in-the-middle attack?
Each correct answer represents a complete solution. Choose all that apply.
In which of the following malicious hacking steps does email tracking come under?
Which of the following files must be configured to enable hostname lookups to use the Domain Name Service (DNS)?
You work as a Network Administrator for Infonet Inc. The company has a Windows Server 2008 domain-based network. The network has three Windows Server 2008 member servers and 150 Windows Vista client computers. The network contains a Windows Server 2008 Core computer named SERVER1 with NTFS file system. SERVER1 has a 802.11 wireless LAN adapter. The Wireless LAN Service is installed on SERVER1. You want to know about the 802.11 wireless LAN interface information, network information, and wireless settings on the system on SERVER1.
Which of the following commands will you use to accomplish the task?
You and your project team have identified the project risks and now are analyzing the probability and impact of the risks. What type of analysis of the risks provides a quick and high-level review of each identified risk event?
Adam works as a Professional Penetration Tester for Umbrella Inc. A project has been assigned to him to carry out a Black Box penetration testing as a regular evaluation of the system security and integrity of the company's network. Which of the following statements are true about the Black Box penetration testing?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following U.S. Federal laws addresses computer crime activities in communication lines, stations, or systems?
Which of the following sections come under the ISO/IEC 27002 standard?
You work as a Network Administrator for Net Perfect Inc. The company's intranet Web site netperfect.com uses a digital certificate issued by the company's Enterprise Certificate Authority. The Enterprise Certificate Authority is located on a server named certificates.netperfect.com. Kate, a user, complains that she is unable to access the secure Web site on her computer using Internet Explorer. An error message appears stating that the digital certificate is not from a trusted source. What is the most likely cause?
Which of the following is used to translate domain names into the numerical (binary) identifiers associated with networking equipment for the purpose of locating and addressing these devices worldwide?
IP blocking is a technique that prevents the connection between a server/website and certain IP addresses or ranges of addresses. Which of the following tools use this technique?
Each correct answer represents a complete solution. Choose all that apply.
John works as an IT Technician for PassGuide Inc. One morning, John receives an e-mail from the company's Manager asking him to provide his logon ID and password, but the company policy restricts users from disclosing their logon IDs and passwords. Which type of possible attack is this?
Which of the following attacks is any form of cryptanalysis where the attacker can observe the operation of a cipher under several different keys whose values are initially unknown, but where some mathematical relationship connecting the keys is known to the attacker?
Which of the following exists between the client and the server system to provide security and allows customized NAT traversal filters to be plugged into the gateway to support address and port translation for certain application layer protocols?
Which of the following statements about reconnaissance is true?
Which of the following types of attacks cannot be prevented by a firewall?
Each correct answer represents a complete solution. Choose all that apply.
You are writing the change management plan for your upcoming project. You want to address mistakes that could happen during the execution of the project. Your change management plan requires the project team to correct any errors that deviate from the project scope as an error is technically an unapproved scope change. What else should you address in regard to errors in project team execution?
Which method is used to configure several disk drives into a logical disk drive and provides faulttolerance, redundancy, lower latency, and higher bandwidth for read/write operations?
Which of the following is a computer worm that caused a denial of service on some Internet hosts and dramatically slowed down general Internet traffic?
Which of the following authentication methods is used to enable a Web browser to provide credentials when making a request during an HTTP transaction?
Which of the following tools provides a visual diagram of a network?
Which of the following functions can you use to mitigate a command injection attack?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is used to identify a particular 802.11 wireless LAN?
You have inserted a Trojan on your friend's computer and you want to put it in the startup so that whenever the computer reboots the Trojan will start to run on the startup. Which of the following registry entries will you edit to accomplish the task?
A helpdesk technician received a phone call from an administrator at a remote branch office. The administrator claimed to have forgotten the password for the root account on UNIX servers and asked for it. Although the technician didn't know any administrator at the branch office, the guy sounded really friendly and since he knew the root password himself, he supplied the caller with the password.
What type of attack has just occurred?
Which of the following are outputs of the Direct and Manage Project Execution process?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following security protocols can be used to support MS-CHAPv2 for wireless client authentication?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for Tech Perfect Inc. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server 2003. You install access points for enabling a wireless network. The sales team members and the managers in the company will be using laptops to connect to the LAN through wireless connections. Therefore, you install WLAN network interface adapters on their laptops. However, you want to restrict the sales team members and managers from communicating directly to each other. Instead, they should communicate through the access points on the network. Which of the following topologies will you use to accomplish the task?
John works as a Network Security Professional. He is assigned a project to test the security of www.we-are-secure.com. He is working on the Linux operating system and wants to install an Intrusion Detection System on the We-are-secure server so that he can receive alerts about any hacking attempts. Which of the following tools can John use to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
PassGuide Research and Training Center is developing its new network model. Which of the following protocols should be implemented in the new network? (Click the Exhibit button on the toolbar to see the case study.) Each correct answer represents a complete solution. Choose two.
Which of the following malware spread through the Internet and caused a large DoS attack in 1988?
Maria has been recently appointed as a Network Administrator in Gentech Inc. She has been tasked to perform network security testing to find out the vulnerabilities and shortcomings of the present network infrastructure. Which of the following testing approaches will she apply to accomplish this task?
Which of the following documents is described in the statement below?
"It is developed along with all processes of the risk management. It contains the results of the qualitative risk analysis, quantitative risk analysis, and risk response planning."
Which of the following applications work as mass-emailing worms?
Each correct answer represents a complete solution. Choose two.
The 3-way handshake method is used by the TCP protocol to establish a connection between a client and the server. It involves three steps:
1. In the first step, a SYN message is sent from a client to the server.
2. In the second step, a SYN/ACK message is sent from the server to the client.
3. In the third step, an ACK (usually called SYN-ACK-ACK) message is sent from the client to the server. At this point, both the client and the server have received acknowledgements of the TCP connection. If the Initial Sequence Numbers of the client and server were 241713111 and 241824111 respectively at the time when the client was sending the SYN message in the first step of the TCP 3-way handshake method, what will be the value of the acknowledgement number field of the server's packet when the server was sending the SYN/ACK message to the client in the second step of the TCP 3-way handshake method?
You are a Web Administrator of Millennium Inc. The company has hosted its Web site within its network. The management wants the company's vendors to be able to connect to the corporate site from their locations through the Internet. As a public network is involved in this process, you are concerned about the security of data transmitted between the vendors and the corporate site. Which of the following can help you?
Which of the following is a structured review of the procurement process originated at the Plan Procurements process?
Your IDS discovers that an intruder has gained access to your system. You immediately stop that access, change passwords for administrative accounts, and secure your network. You discover an odd account (not administrative) that has permission to remotely access the network. What is this most likely?
Which of the following is a computer worm that caused a denial of service on some Internet hosts and dramatically slowed down general Internet traffic?
Which of the following are the types of access controls?
Each correct answer represents a complete solution. Choose three.
Which of the following attacks can be performed by Brutus for cracking a password?
Each correct answer represents a complete solution. Choose two.
In which technique are phases overlapped that would normally be done in sequence?
Which field is NOT defined while creating rules for the Network Honeypot rulebase?
Which of the following malware spread through the Internet and caused a large DoS attack in
1988?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He finds that the We-are-secure server is vulnerable to attacks. As a countermeasure, he suggests that the Network Administrator should remove the IPP printing capability from the server. He is suggesting this as a countermeasure against __________.
Which of the following terms refers to a prolonged loss of power?
Which of the following uses a variable-length Initialization Vector (IV), where the encrypted data begins?
You work as a professional Ethical Hacker. You are assigned a project to perform blackbox testing of the security of www.we-are-secure.com. Now you want to perform banner grabbing to retrieve information about the Webserver being used by we-are-secure. Which of the following tools can you use to accomplish the task?
Which of the following is the process of comparing cryptographic hash functions of system executables and configuration files?
Which of the following can be performed to verify the effectiveness of a quality management system?
Which type of repudiation states that the creator of the message denies ever creating the message even after creating it?
Which of the following is a physical or logical subnetwork that contains and exposes external services of an organization to a larger network, usually the Internet?
Which of the following is the default security level for the Internet zone?
Which of the following is the encryption subsystem of the NTFS file system?
Which of the following standards is also known as IEEE 802.11i?
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of www.we-are-secure.com. He installs a sniffer on the We-are-secure server thinking that the following protocols of the We-are-secure server are being used in the network:
• HTTP
• SSL
• SSH
• IPSec
Considering the above factors, which of the following types of packets can he expect to see captured in encrypted form when he checks the sniffer's log file?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is an authentication protocol used by clients to dial-in to computers running Windows 2000 Server?
Which networking protocol is used to authenticate users or devices before granting them access to a network?
Maria works as a professional Ethical Hacker. She has been assigned the project of testing the security of www.gentech.com. She is using dumpster diving to gather information about Gentech Inc. In which of the following steps of malicious hacking does dumpster diving come under?
Which of the following is a signature-based intrusion detection system (IDS) ?
You are taking over the security of an existing network. You discover a machine that is not being used as such, but has software on it that emulates the activity of a sensitive database server. What is this?
Which of the following tools is based on Linux and used to carry out the Penetration Testing?
What is the term used to describe the cost of the solution after the solution has been implemented in production by a vendor?
Consider the following diagram:
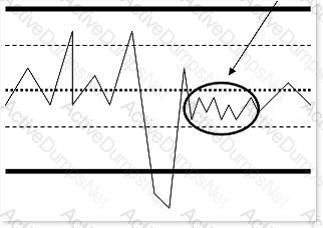
What is the highlighted area of the diagram known as?
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
Fill in the blank with the appropriate term.
NOTE. Do not use abbreviation.
________ is a configurable client identification that allows a client to communicate with a particular base station.
John works as a Website Administrator in ABC Inc. The company has to set a privacy policy on all the computers. The policy requires John to restrict only third party cookies that do not have a compact private policy or that use personally identifiable information without a user's implicit consent. He reports to the Technical Support Executive that he wants to set the policy. The Technical Support Executive asks him to configure the settings in the Privacy tab page. Which of the following privacy settings will John use to accomplish the task?
Which system is designed to analyze, detect, and report on security-related events?
John is a merchant. He has set up a LAN in his office. Some important files are deleted as a result of virus attack. John wants to ensure that it does not happen again. What will he use to protect his data from virus?
Kerberos is a computer network authentication protocol that allows individuals communicating over a non-secure network to prove their identity to one another in a secure manner. Which of the following statements are true about the Kerberos authentication scheme?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following statements is true about the difference between worms and Trojan horses?
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of www.we-are-secure.com. He installs a sniffer on the We-are-secure server thinking that the following protocols of the We-are-secure server are being used in the network:
HTTP
SSL
SSH
IPSec
Considering the above factors, which of the following types of packets can he expect to see captured in encrypted form when he checks the sniffer's log file?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He wants to use Kismet as a wireless sniffer to sniff the We-are-secure network. Which of the following IEEE-based traffic can be sniffed with Kismet?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following processes is NOT a part of the Project Procurement Management Knowledge Area?
Which of the following statements about IPSec are true?
Each correct answer represents a complete solution. Choose two.
Which of the following programs can collect various types of personal information, such as Internet surfing habits, and Web sites that the user has visited?
Mark works as a Network Administrator for Perfect Inc. The company has both wired and wireless networks. An attacker attempts to keep legitimate users from accessing services that they require. Mark uses IDS/IPS sensors on the wired network to mitigate the attack. Which of the following attacks best describes the attacker's intentions?
