GIAC GPEN GIAC Penetration Tester Exam Practice Test
GIAC Penetration Tester Questions and Answers
Which of the following statements are true about NTLMv1?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Penetration tester in the Secure Inc. Your company takes the projects to test the security of various companies. Recently, Secure Inc. has assigned you a project to test the security of a Web site. You go to the Web site login page and you run the following SQL query:
SELECT email, passwd, login_id, full_name
FROM members
WHERE email = 'attacker@somehwere.com'; DROP TABLE members; --'
What task will the above SQL query perform?
You want to scan your network quickly to detect live hosts by using ICMP ECHO Requests. What type of scanning will you perform to accomplish the task?
Which of the following is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards and also detects wireless networks marking their relative position with a GPS?
Which of the following tasks can be performed by using netcat utility?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following can be used as a countermeasure against the SQL injection attack?
Each correct answer represents a complete solution. Choose two.
Which of the following tools connects to and executes files on remote systems?
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. Rick, your assistant, is configuring some laptops for wireless access. For security, WEP needs to be configured for wireless communication. By mistake, Rick configures different WEP keys in a laptop than that is configured on the Wireless Access Point (WAP). Which of the following statements is true in such situation?
You have obtained the hash below from the /etc/shadow file. What are you able to discern simply by looking at this hash?
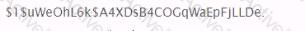
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully performed the following steps of the preattack phase to check the security of the We-are-secure network:
l Gathering information
l Determining the network range
l Identifying active systems
Now, he wants to find the open ports and applications running on the network. Which of the following tools will he use to accomplish his task?
Which of the following tools can be used as a Linux vulnerability scanner that is capable of identifying operating systems and network services?
Each correct answer represents a complete solution. Choose all that apply.
Ryan wants to create an ad hoc wireless network so that he can share some important files with another employee of his company. Which of the following wireless security protocols should he choose for setting up an ad hoc wireless network?
Each correct answer represents a part of the solution. Choose two.
You want to run the nmap command that includes the host specification of 202.176.56-57.*. How many hosts will you scan?
What will the following scapy commands do?

Which of the following statements are true about firewalking?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He is assigned a project to test the security of www.we-are-secure.com. He has to ping 500 computers to find out whether these computers are connected to the server or not. Which of the following will he use to ping these computers?
You work as a Network Administrator in the Secure Inc. Your company is facing various network attacks due to the insecure wireless network. You are assigned a task to secure your wireless network. For this, you have turned off broadcasting of the SSID. However, the unauthorized users are still able to connect to the wireless network. Which of the following statements can be the reason for this issue?
Each correct answer represents a complete solution. Choose all that apply.
You are concerned about war driving bringing hackers attention to your wireless network. What is the most basic step you can take to mitigate this risk?
One of the sales people in your company complains that sometimes he gets a lot of unsolicited messages on his PDA. After asking a few questions, you determine that the issue only occurs in crowded areas like airports. What is the most likely problem?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. On the We-are-secure login page, he enters = 'or''=' as a username and successfully logs in to the user page of the Web site. The We-are-secure login page is vulnerable to a __________.
John works as a Professional Ethical Hacker for we-are-secure Inc. The company is using a Wireless network. John has been assigned the work to check the security of WLAN of we-aresecure.
For this, he tries to capture the traffic, however, he does not find a good traffic to analyze data. He has already discovered the network using the ettercap tool. Which of the following tools can he use to generate traffic so that he can crack the Wep keys and enter into the network?
Which of the following can be used as a countermeasure against the SQL injection attack?
Each correct answer represents a complete solution. Choose two.
Which of the following are considered Bluetooth security violations?
Each correct answer represents a complete solution. Choose two.
When you conduct the XMAS scanning using Nmap, you find that most of the ports scanned do not give a response. What can be the state of these ports?
You want to search the Apache Web server having version 2.0 using google hacking. Which of the following search queries will you use?
You work as a Network Security Analyzer. You got a suspicious email while working on a forensic project. Now, you want to know the IP address of the sender so that you can analyze various information such as the actual location, domain information, operating system being used, contact information, etc. of the email sender with the help of various tools and resources. You also want to check whether this email is fake or real. You know that analysis of email headers is a good starting point in such cases. The email header of the suspicious email is given below:
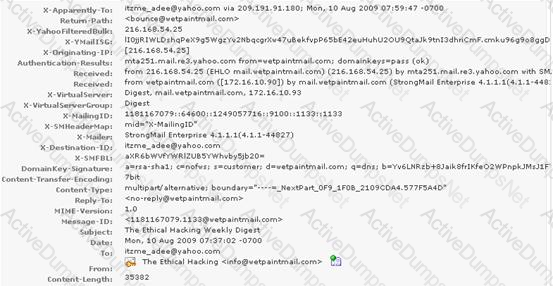
What is the IP address of the sender of this email?
GSM uses either A5/1 or A5/2 stream cipher for ensuring over-the-air voice privacy. Which of the following cryptographic attacks can be used to break both ciphers?
Which of the following are the countermeasures against WEP cracking?
Each correct answer represents a part of the solution. Choose all that apply.
Which of the following attacks can be overcome by applying cryptography?
Which of the following tools can be used to automate the MITM attack?
Which of the following tools is a wireless sniffer and analyzer that works on the Windows operating system?
Which of the following is a Windows-based tool that is used for the detection of wireless LANs using the IEEE 802.11a, 802.11b, and 802.11g standards and also detects wireless networks marking their relative position with a GPS?
Which of the following techniques are NOT used to perform active OS fingerprinting?
Each correct answer represents a complete solution. Choose all that apply.
In which of the following attacks does an attacker use packet sniffing to read network traffic between two parties to steal the session cookie?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He is using a tool to crack the wireless encryption keys. The description of the tool is as follows:

Which of the following tools is John using to crack the wireless encryption keys?
You want to run the nmap command that includes the host specification of 202.176.56-57.*. How many hosts will you scan?
Which of the following tools allow you to perform HTTP tunneling?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following is a web ripping tool?
Which of the following Penetration Testing steps includes network mapping and OS fingerprinting?
Which of the following does NOT use a proxy software to protect users?
You want to connect to your friend's computer and run a Trojan on it. Which of the following tools will you use to accomplish the task?
You want to retrieve password files (stored in the Web server's index directory) from various Web sites. Which of the following tools can you use to accomplish the task?
Which of the following is a tool for SSH and SSL MITM attacks?
Which of the following tools is based on the SATAN tool?
In which layer of the OSI model does a sniffer operate?
Analyze the command output below. What action is being performed by the tester?
You are conducting a penetration test for a private company located in the UK. The scope extends to all internal and external hosts controlled by the company. You have gathered necessary hold-harmless and non-disclosure agreements. Which action by your group can incur criminal liability under the computer Misuse Act of 1990?
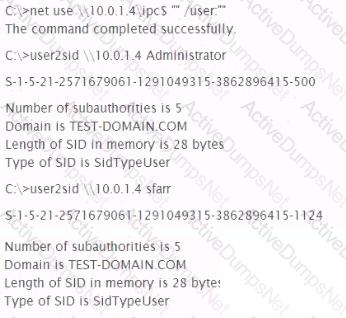
A penetration tester wishes to stop the Windows Firewall process on a remote host running Windows Vista She issues the following commands:
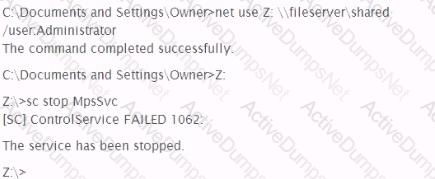
A check of the remote host indicates that Windows Firewall is still running. Why did the command fail?
Analyze the command output below. Given this information, which is the appropriate next step for the tester?
Starting Nmap4.53 (hnp://insecure.org I at2010-09-30 19:13 EDT interesting ports on 192.163.116.101:
PORT STATE SERVICE
130/tcp filtered cisco-fna
131/tcp filtered cisco-tna
132/tcp filtered cisco-sys
133/tcp filtered statsrv
134/tcp filtered Ingres-net
135/tcp filtered msrpc
136/tcp filtered profile
137/tcp filtered netbios-ns
138/tcp filtered netbios-dgm
139/tcp open netbios-ssn
140/tcp filtered emfis-data
MAC Address: 00:30:1&:B8:14:8B (Shuttle)
warning: OSS can results may be unreliable because we could not find at least l open and l
closed port
Device type, general purpose
Running: Microsoft Windows XP
OS details: Microsoft Windows XP SP2
Network Distance : 1 hop
Nmap done: I IP address (I host up) scanned in l .263 seconds
You have been contracted to penetration test an e-mail server for a client that wants to know for sure if the sendmail service is vulnerable to any known attacks. You have permission to run any type of test, how will you proceed to give the client the most valid answer?
You suspect that system administrators In one part of the target organization are turning off their systems during the times when penetration tests are scheduled, what feature could you add to the ' Rules of engagement' that could help your team test that part of the target organization?
What is the main difference between LAN MAN and NTLMv1 challenge/responses?
How does OWASP ZAP function when used for performing web application assessments?
What is the MOST important document to obtain before beginning any penetration testing?
Approximately how many packets are usually required to conduct a successful FMS attack onWEP?
Which of the following best describes a client side exploit?
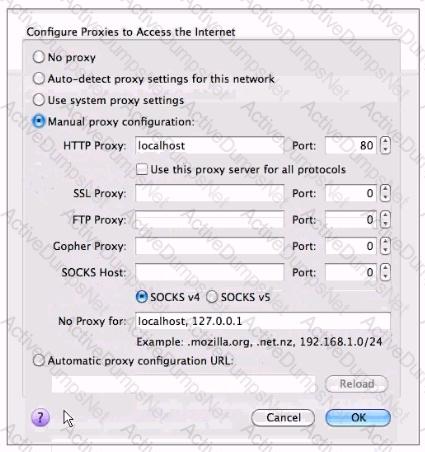
A junior penetration tester at your firm is using a non-transparent proxy for the first time to test a web server. He sees the web site In his browser but nothing shows up In the proxy. He tells you that he just installed the non-transparent proxy on his computer and didn't change any defaults. After verifying the proxy is running, you ask him to open up his browser configuration, as shown in the figure, which of the following recommendations will correctly allow him to use the transparent proxy with his browser?