GIAC GCFR GIAC Cloud Forensics Responder (GCFR) Exam Practice Test
GIAC Cloud Forensics Responder (GCFR) Questions and Answers
What 1$ a drawback of analyzing a snapshot outside of AWS?
Which performance feature of an Amazon EC2 instance is configured to add additional resources based on set trigger points?
Access Kibana via http://10.0.1.7:5601 and use the azure-* index pattern. Between March 31st, 2021 and April 3rd, 2021, how many virtual machines were created that use a Linux operating system?
What is the example AWS data below an example of?

What unique identifier is used by AWS to identify a specific account and allow integration with external organizations?
What AWS service will allow an organization to set custom compliance metrics and force compliance on an organizational, sub-organizational, or individual account level?
Which is a limitation of AWS Lambdas?
After registering the application in Azure AD, what is the next step to take in order to use Microsoft Graph API?
What method does Google use to alert Gmail account holders that they may be under attack by government sponsored attackers?
What can be inferred about the ARN below?
arn:aws:!am::457787814323:user/giac
An engineer is troubleshooting a complaint that a web server in AWS cannot receive incoming traffic, but the server can connect to the internet otherwise. What is needed to solve this problem?
An investigator is evaluating a client's Microsoft 365 deployment using the web portals and has identified that the Purview compliance portal states that the Unified Audit Logs are not enabled. Based on the additional Information gathered below, what is most likely the cause of this configuration message?
Subscription creation date: December 4, 2021 Number of administrators: 2 Number of non-administrative user accounts: 74 Last tenant administration change: December 4,2021
What would prevent GCP 1AM from linking to Google Workspace tomanageusers and groups?
Sensitive company data is found leaked on the internet, and the security team didn't
get any alert and is unsure of how the breach occurred.
Which logs would be a preferable starting point for an investigation?
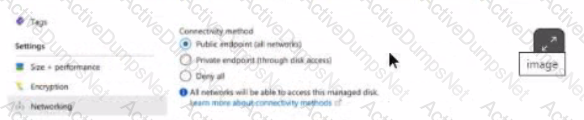
What is shown in the screenshot?
A cloud administrator needs to determine which user account allowed SSH Inbound from the internet on an Azure Network security group. Which type of log does the administrator need to examine?
Which Azure blob storage option is typically used to store virtual hard drive (VHD) Ales?
What Pub/Sub component is used to forward GCP logs to their final location?
Which EBS volumetype would be appropriate to support a business critical SQL server hosted In AWS?
Which of the following actions described below would populate the suggestions table on an Android phone?
A company using PaaS to host and develop their software application is experiencing a DOS attack. What challenge will a DFIR analyst experience when investigating this attack?
What is the expected time delay for Azure AD logs to become searchable in the Microsoft 365 Unified Audit Log?
Microsoft.Key Vault is an example of which component of Azure's structure?
