GIAC GCFA GIACCertified Forensics Analyst Exam Practice Test
GIACCertified Forensics Analyst Questions and Answers
You work as a Network Administrator for Net World International. You have configured the hard disk drive of your computer as shown in the image below:
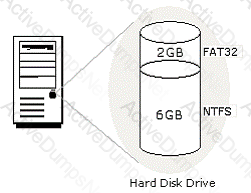
The computer is configured to dual-boot with Windows 2000 Server and Windows 98. While working on Windows 2000 Server, you save a file on the 6GB partition. You are unable to find the file while working on Windows 98. You are not even able to access the partition on which the file is saved. What is the most likely cause?
Which of the following type of file systems is not supported by Linux kernel?
Adam works as a professional Computer Hacking Forensic Investigator. He works with the local police. A project has been assigned to him to investigate an iPod, which was seized from a student of the high school. It is suspected that the explicit child pornography contents are stored in the iPod. Adam wants to investigate the iPod extensively. Which of the following operating systems will Adam use to carry out his investigations in more extensive and elaborate manner?
Which of the following file systems is designed by Sun Microsystems?
Which of the following tools can be used to perform tasks such as Windows password cracking, Windows enumeration, and VoIP session sniffing?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He receives the following e-mail:

The e-mail that John has received is an example of __________.
Which of the following is a file management tool?
Which of the following sections of an investigative report covers the background and summary of the report including the outcome of the case and the list of allegations?
Which of the following is the first computer virus that was used to infect the boot sector of storage media formatted with the DOS File Allocation Table (FAT) file system?
Which of the following parameters is NOT used for calculating the capacity of the hard disk?
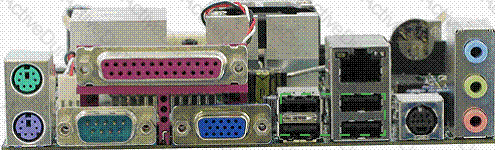
Identify the port in the image given below, which can be connected to the hub to extend the number of ports, and up to 127 devices can be connected to it?
You want to upgrade a partition in your computer's hard disk drive from FAT to NTFS. Which of the following DOS commands will you use to accomplish this?
Maria works as a professional Ethical Hacker. She recently got a project to test the security of www.we-are-secure.com. Arrange the three pre-test phases of the attack to test the security of weare-secure.
You company suspects an employee of sending unauthorized emails to competitors. These emails are alleged to contain confidential company data. Which of the following is the most important step for you to take in preserving the chain of custody?
You work as a Network Administrator for Perfect Solutions Inc. You install Windows 98 on a computer. By default, which of the following folders does Windows 98 setup use to keep the registry tools?
Fill in the blank with the appropriate name.
_____is a list, which specifies the order of volatility of data in a Windows based system.
Mark has been hired by a company to work as a Network Assistant. He is assigned the task to
configure a dial-up connection. He is configuring a laptop. Which of the following protocols should he disable to ensure that the password is encrypted during remote access?
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He wants to test the effect of a virus on the We-are-secure server. He injects the virus on the server and, as a result, the server becomes infected with the virus even though an established antivirus program is installed on the server. Which of the following do you think are the reasons why the antivirus installed on the server did not detect the virus injected by John?
Each correct answer represents a complete solution. Choose all that apply.
John works as a Network Administrator for Perfect Solutions Inc. The company has a Linux-based network. John is working as a root user on the Linux operating system. Which of the following commands will John use to display information about all mounted file systems?
Each correct answer represents a complete solution. Choose all that apply.
You are a professional Computer Hacking forensic investigator. You have been called to collect the evidences of Buffer Overflows or Cookie snooping attack. Which of the following logs will you review to accomplish the task?
Each correct answer represents a complete solution. Choose all that apply.
Brutus is a password cracking tool that can be used to crack the following authentications:
HTTP (Basic Authentication)
HTTP (HTML Form/CGI)
POP3 (Post Office Protocol v3)
FTP (File Transfer Protocol)
SMB (Server Message Block)
Telnet
Which of the following attacks can be performed by Brutus for password cracking?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following firewalls depends on the three-way handshake of the TCP protocol?
You are responsible for maintaining and troubleshooting PC's at your company. The receptionist reports her screen has gone blue. When you get there you notice the 'blue screen of death' with an error message NTFS_FILE_SYSTEM. What is the most likely cause of this error?
Which of the following anti-child pornography organizations helps local communities to create
programs and develop strategies to investigate child exploitation?
Which of the following tools is used to extract human understandable interpretation from the computer binary files?
In which of the following files does the Linux operating system store passwords?
Sandra wants to create a full system state backup of her computer, which is running on Microsoft Windows XP operating system. Which of the following is saved in full state system backup?
Each correct answer represents a complete solution. Choose all that apply.
You work as a Network Administrator for Tech Perfect Inc. The company has a TCP/IP-based network. You are configuring a wireless LAN on the network. You experience interference on your network. Through investigation, you come to know that three foreign WAPs are within the range of your LAN. Although they have different SSIDs than yours, they are working on the same channel as yours.
Which of the following steps will you take to reduce the interference?
John works as a professional Ethical Hacker. He has been assigned the project of testing the security of www.we-are-secure.com. He has successfully completed the following pre-attack phases while testing the security of the server:
Footprinting
Scanning
Now he wants to conduct the enumeration phase. Which of the following tools can John use to conduct it?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following Incident handling process phases is responsible for defining rules, collaborating human workforce, creating a back-up plan, and testing the plans for an enterprise?
John works as a professional Ethical Hacker. He has been assigned the task of testing the security of www.we-are-secure.com. He has performed the footprinting step and now he has enough information to begin scanning in order to detect active computers. He sends a ping request to a computer using ICMP type 13. What kind of ICMP message is John using to send the ICMP ping request message?
Adam works as a Computer Hacking Forensic Investigator. He has been assigned a project to
investigate child pornography. As the first step, Adam found that the accused is using a Peer-to-peer application to network different computers together over the internet and sharing pornographic materials of children with others. Which of the following are Peer-to-Peer applications?
Each correct answer represents a complete solution. Choose all that apply.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. He copies the whole structure of the We-are-secure Web site to the local disk and obtains all the files on the Web site. Which of the following techniques is he using to accomplish his task?
Adam works as a professional Computer Hacking Forensic Investigator. A project has been assigned to him to investigate computer of an unfaithful employee of SecureEnet Inc. Suspect's computer runs on Windows operating system. Which of the following sources will Adam investigate on a Windows host to collect the electronic evidences?
Each correct answer represents a complete solution. Choose all that apply.
Which of the following cryptographic methods are used in EnCase to ensure the integrity of the data, which is acquired for the investigation?
Each correct answer represents a complete solution. Choose two.
Peter works as a Computer Hacking Forensic Investigator for SecureEnet Inc. He has been assigned with a project of investigating a disloyal employee who is accused of stealing secret data from the company and selling it to the competitor company. Peter is required to collect proper evidences and information to present before the court for prosecution. Which of the following parameters is necessary for successful prosecution of this corporate espionage?
Which of the following file attributes are not available on a FAT32 partition?
Each correct answer represents a complete solution. Choose two.
You work as the Network Administrator for McNeil Inc. The company has a Unix-based network. You want to print the super block and block the group information for the filesystem present on a system.
Which of the following Unix commands can you use to accomplish the task?
You work as a Network Administrator for NetTech Inc. To ensure the security of files, you encrypt data files using Encrypting File System (EFS). You want to make a backup copy of the files and maintain security settings. You can backup the files either to a network share or a floppy disk. What will you do to accomplish this?
Which of the following methods can be used to start the Disk Defragmenter utility in Windows 9x?
Each correct answer represents a complete solution. Choose two.
John works as a professional Ethical Hacker. He has been assigned a project to test the security of www.we-are-secure.com. John wants to redirect all TCP port 80 traffic to UDP port 40, so that he can bypass the firewall of the We-are-secure server. Which of the following tools will John use to accomplish his task?
What are the purposes of audit records on an information system?
Each correct answer represents a complete solution. Choose two.
You work as a Network Administrator for NetTech Inc. The company's network is connected to the Internet. For security, you want to restrict unauthorized access to the network with minimum administrative effort. You want to implement a hardware-based solution. What will you do to accomplish this?
Which of the following steps are generally followed in computer forensic examinations?
Each correct answer represents a complete solution. Choose three.
On your dual booting computer, you want to set Windows 98 as the default operating system at startup. In which file will you define this?
The Klez worm is a mass-mailing worm that exploits a vulnerability to open an executable attachment even in Microsoft Outlook's preview pane. The Klez worm gathers email addresses from the entries of the default Windows Address Book (WAB). Which of the following registry values can be used to identify this worm?
Which of the following articles defines illegal access to the computer or network in Chapter 2 of Section 1, i.e., Substantive criminal law of the Convention on Cybercrime passed by the Council of Europe?