GIAC GCED GIAC Certified Enterprise Defender Exam Practice Test
GIAC Certified Enterprise Defender Questions and Answers
How does the Cisco IOS IP Source Guard feature help prevent spoofing attacks?
Which control would BEST help detect a potential insider threat?
Which tool uses a Snort rules file for input and by design triggers Snort alerts?
Which of the following is an operational security control that is used as a prevention mechanism?
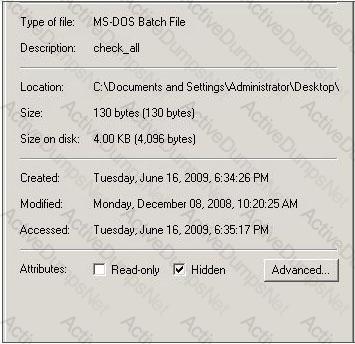
Which command tool can be used to change the read-only or hidden setting of the file in the screenshot?
Which of the following applies to newer versions of IOS that decrease their attack surface?
If a Cisco router is configured with the “service config” configuration statement, which of the following tools could be used by an attacker to apply a new router configuration?
At the start of an investigation on a Windows system, the lead handler executes the following commands after inserting a USB drive. What is the purpose of this command? C:\ >dir / s / a dhsra d: \ > a: \ IRCD.txt
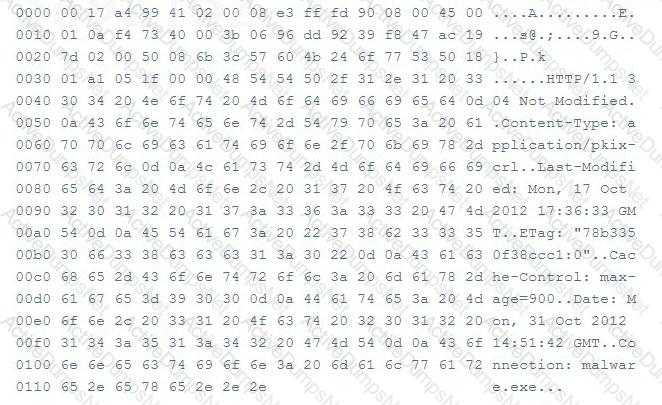
Although the packet listed below contained malware, it freely passed through a layer 3 switch. Why didn’t the switch detect the malware in this packet?
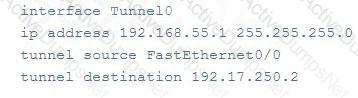
How would an attacker use the following configuration settings?
Michael, a software engineer, added a module to a banking customer’s code. The new module deposits small amounts of money into his personal bank account. Michael has access to edit the code, but only code reviewers have the ability to commit modules to production. The code reviewers have a backlog of work, and are often willing to trust the software developers’ testing and confidence in the code.
Which technique is Michael most likely to engage to implement the malicious code?
Which Windows tool would use the following command to view a process:
process where name=’suspect_malware.exe’list statistics
Which action would be the responsibility of the First Responder once arriving at the scene of a suspected incident as part of a Computer Security Incident Response Plan (CSIRP)?
