GIAC GCCC GIAC Critical Controls Certification (GCCC) Exam Practice Test
GIAC Critical Controls Certification (GCCC) Questions and Answers
IDS alerts at Service Industries are received by email. A typical day process over 300 emails with fewer than 50 requiring action. A recent attack was successful and went unnoticed due to the number of generated alerts. What should be done to prevent this from recurring?
Acme Corporation is doing a core evaluation of its centralized logging capabilities. Which of the following scenarios indicates a failure in more than one CIS Control?
Which of the following actions produced the output seen below?
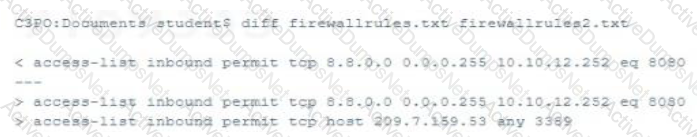
An organization is implementing a control for the Account Monitoring and Control CIS Control, and have set the Account Lockout Policy as shown below. What is the risk presented by these settings?
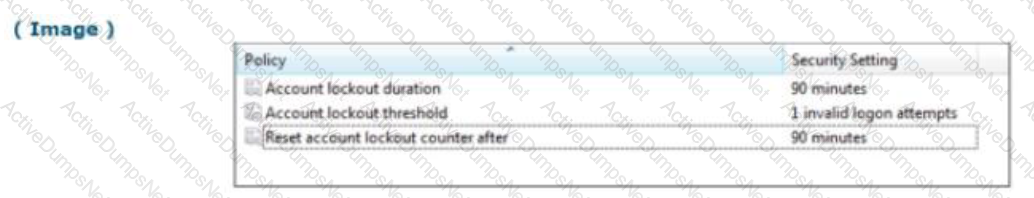
An organization has implemented a control for penetration testing and red team exercises conducted on their network. They have compiled metrics showing the success of the penetration testing (Penetration Tests), as well as the number of actual adversary attacks they have sustained (External Attacks). Assess the metrics below and determine the appropriate interpretation with respect to this control.
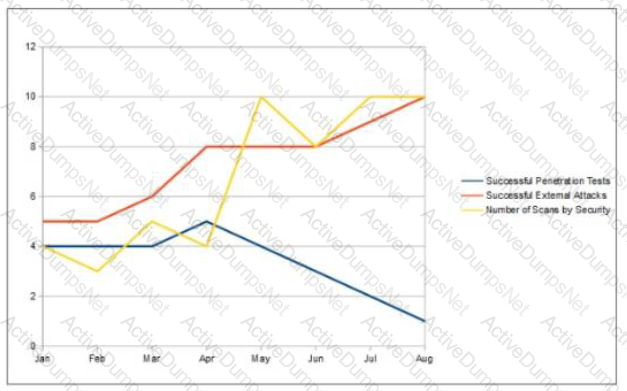
An organization has installed a firewall for Boundary Defense. It allows only outbound traffic from internal workstations for web and SSH, allows connections from the internet to the DMZ, and allows guest wireless access to the internet only. How can an auditor validate these rules?
Which of the following archiving methods would maximize log integrity?
An organization has implemented a policy to continually detect and remove malware from its network. Which of the following is a detective control needed for this?
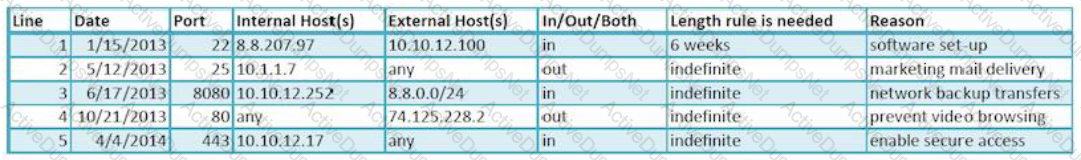
Dragonfly Industries requires firewall rules to go through a change management system before they are configured. Review the change management log. Which of the following lines in your firewall ruleset has expired and should be removed from the configuration?
When evaluating the Wireless Access Control CIS Control, which of the following systems needs to be tested?
Given the audit finding below, which CIS Control was being measured?
What tool creates visual network topology output and results that can be analyzed by Ndiff to determine if a service or network asset has changed?
Which type of scan is best able to determine if user workstations are missing any important patches?
