GIAC GASF GIAC Advanced Smartphone Forensics Exam Practice Test
GIAC Advanced Smartphone Forensics Questions and Answers
Which artifact(s) can be extracted from a logical image only if the device the image was acquired from was jailbroken?
Which of the following items is found in the Kernel Space for an iOS device?
In 2015, Apple’s iTunes store was found to be hosting several malicious applications that were infected as a result of hacked version of the developer toolkit used to create applications. Which Apple developer suite was targeted?
What is the MAIN difference between a Full Root and a Shell/Soft Root?
An analyst investigating a Nokia S60 Symbian device wants to know if an Adobe Flash file on the handset is compromised.
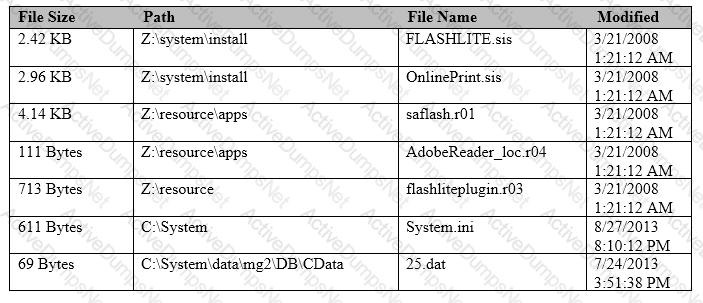
Which file in the image will best target the Adobe Flash files?
Examine the file, Bluetooth, what is the name of the device being examined?
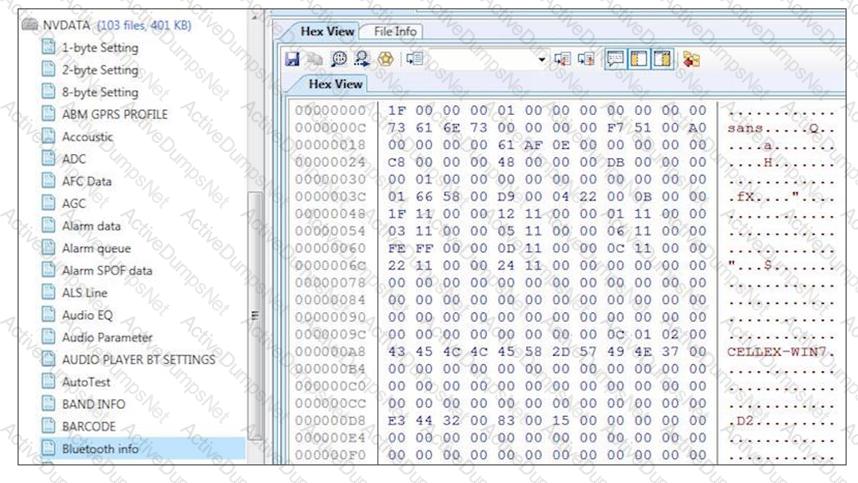
You have conducted a keyword search over flash.bin and notice that multiple instances of the same data
appear many times throughout the flash image. What is this an example of?
What is the essential piece of information is most often required in order to decrypt the contents of BlackBerry OS 10 handsets?
Property list (Plist) files are used by iOS devices to store datA. Which of the file formats below is common to
plist files?
Which of the following actions described below would populate the suggestions table on an Android phone?
Which of the following files provides the most accurate reflection of the device’s date/timestamp related to the
last device wipe?
