- Home
- Fortinet
- Fortinet Network Security Expert
- NSE7_SSE_AD-25
- NSE7_SSE_AD-25 - Fortinet NSE 7 - FortiSASE 25 Enterprise Administrator
Fortinet NSE7_SSE_AD-25 Fortinet NSE 7 - FortiSASE 25 Enterprise Administrator Exam Practice Test
Fortinet NSE 7 - FortiSASE 25 Enterprise Administrator Questions and Answers
Refer to the exhibits.
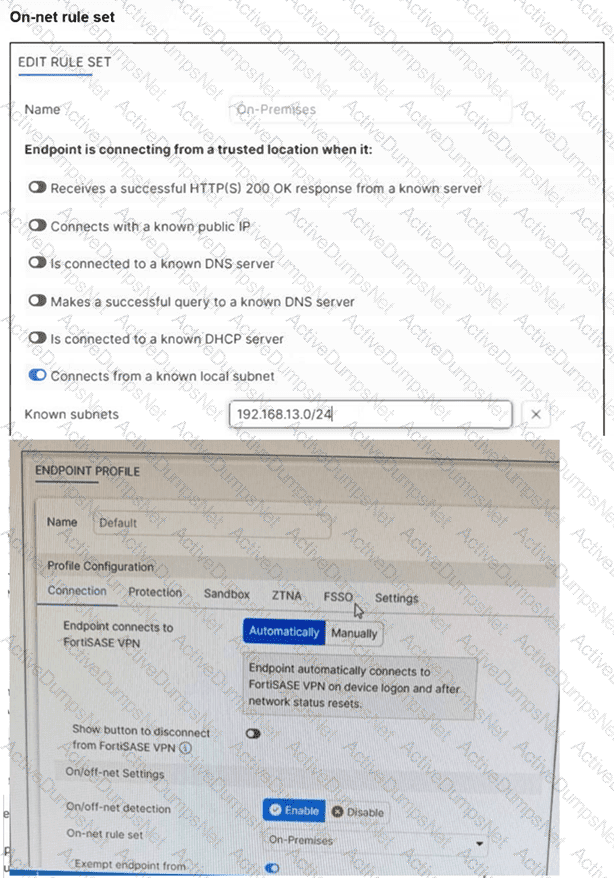
An endpoint is assigned an IP address of 192.168.13.101/24. Which action will be run on the endpoint? (Choose one answer)
Options:
The endpoint will be able to bypass the on-net rule because it is connecting from a known subnet.
The endpoint will be detected as off-net.
The endpoint will be exempted from auto-connect to the FortiSASE tunnel.
The endpoint will automatically connect to the FortiSASE tunnel.
Answer:
CExplanation:
Based on the provided exhibits and the logic of FortiSASE On/off-net detection, the endpoint's behavior is determined by its network environment relative to the configured rules.
Subnet Matching and Detection: The On-net rule set (named "On-Premises") is configured to identify a trusted location when the endpoint "Connects from a known local subnet". The administrator has defined the known subnet as $192.168.13.0/24$. Since the endpoint's IP address is $192.168.13.101$, it falls within this range. Consequently, FortiClient detects the endpoint as being on-net (on-fabric).
Action Logic (Exemption): In a FortiSASE Endpoint Profile, when On/off-net detection is enabled and an endpoint matches an "On-net" rule, the standard behavior is to exempt the endpoint from auto-connecting to the FortiSASE VPN tunnel. This design assumes the endpoint is already in a secured office environment where the corporate firewall (FortiGate) provides the necessary protection, making the SASE tunnel redundant.
Comparison of Other Options: * Option B: Incorrect, because the IP matches the defined "known local subnet" rule for on-net detection.
Option D: Incorrect, as auto-connect only triggers when the endpoint is detected as off-net to ensure remote security.
What is the purpose of security posture tagging in ZTNA? (Choose one answer)
Options:
To assign usernames to different devices for security logs
To ensure that all devices and users are monitored continuously
To provide granular access control based on the compliance status of devices and users1
To categorize devices and users based on their role in the organization
Answer:
CExplanation:
In the context of Zero Trust Network Access (ZTNA), security posture tagging is the fundamental mechanism used to enforce compliance and security standards before granting access to protected resources.
Granular Access Control: The primary purpose of tagging is to provide granular access control.3 Instead of relying solely on static credentials, ZTNA uses these dynamic tags to determine if a device or user meets specific security requirements at the moment of the connection request.
Compliance-Based Enforcement: Tags are assigned based on the compliance status of the endpoint. For example, the FortiSASE Endpoint Management Service (EMS) can verify if a device has an active antivirus, is running a specific OS version, or is joined to the corporate domain.5 If the device fails any of these checks, the "Compliant" tag is removed, and access is automatically revoked.
Dynamic and Continuous Assessment: Unlike traditional VPNs that check posture only at login, ZTNA posture tagging allows for continuous assessment. If a device's security posture changes—for instance, if the user disables their firewall—the tag is updated in real-time across the Security Fabric, and the ZTNA policy will immediately deny further access.8
Integration with Policies: On the FortiGate (acting as a ZTNA proxy) or within FortiSASE, these tags are used as source criteria in ZTNA policies.9 Only traffic originating from endpoints with the required tags (e.g., "EMS-Tag: Corporate-Managed") is permitted to reach the protected application.
An existing Fortinet SD-WAN customer is reviewing the FortiSASE ordering guide to identify which add-on is needed to allow future FortiSASE remote users to reach private resources. Which add-on should the customer consider to allow private access? (Choose one answer)
Options:
FortiSASE Global add-on
FortiSASE Branch On-Ramp add-on
FortiSASE SPA add-on
FortiSASE Dedicated Public IP Address add-on
Answer:
CExplanation:
To enable remote users to access internal applications located behind an existing FortiGate SD-WAN hub, the customer must license the FortiSASE Secure Private Access (SPA) add-on.
Secure Private Access (SPA) Use Case: This specific add-on is designed to extend the Fortinet Security Fabric into the SASE cloud, allowing for a hub-and-spoke architecture where the FortiSASE PoPs act as spokes and the customer's on-premises FortiGate acts as the hub.
Licensing Requirements: The SPA add-on is a per-hub (per service connection) license. It provides the necessary entitlements to establish IPsec tunnels and BGP peering between the SASE infrastructure and the corporate FortiGate.
Feature Enablement: Once the SPA license is applied, the Configuration > Private Access menu becomes available in the FortiSASE portal. This allows administrators to define "Service Connections" to their private data centers or cloud VPCs.
Analysis of Other Options:
Option A: The Global add-on is typically related to expanding the geographic reach or performance of the SASE PoPs, not specifically for private resource routing.
Option B: The Branch On-Ramp refers to connecting physical office locations (Thin Edge) to SASE, rather than the specific licensing for private application access for remote users.
Option D: Dedicated Public IP Address is used for source IP anchoring (SIA) to ensure remote users egress with a consistent IP for third-party SaaS IP-whitelisting.
Refer to the exhibit.
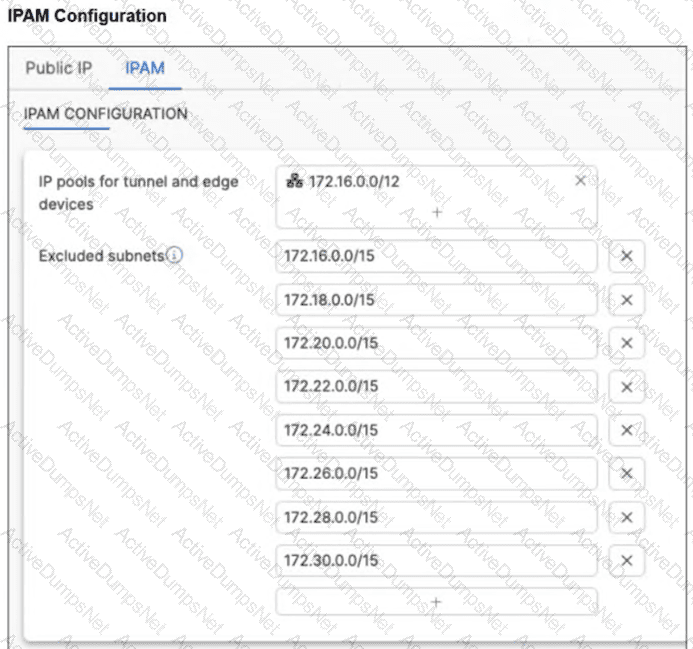
A customer wants to fine-tune network assignments on FortiSASE, so they modified the IPAM configuration as shown in the exhibit. After this configuration, the customer started having connectivity problems and noticed that devices are using excluded ranges. What could be causing the unexpected behavior and connectivity problems? (Choose two answers)
Options:
The pool must include at least one /20 per security POP for the IPAM to work correctly.
The pool must include at least one /16 per Instance for the IPAM to work correctly.
The pool must include at least one /20 per Instance for the IPAM to work correctly.
The customer excluded too many networks from the pool.
Answer:
A, DExplanation:
IP Address Management (IPAM) in FortiSASE is responsible for automatically allocating subnets to various services, including VPN tunnels and Edge devices. When an administrator modifies the default IPAM configuration, they must adhere to specific architectural scaling requirements.
Subnet Requirements per PoP: FortiSASE architecture requires a minimum amount of address space to be available for each provisioned Security Point of Presence (PoP) to handle internal routing and endpoint assignments. For the IPAM engine to function correctly and distribute unique subnets across the global infrastructure, the pool must provide at least one /20 subnet per security PoP. If the available space is smaller than this per-PoP requirement, the allocation logic may fail or produce unpredictable routing behavior.
Impact of Excessive Exclusions: In the exhibit (image_578940.png), the customer has defined a large summary pool of 172.16.0.0/12. However, they have configured eight separate /15 excluded subnets: 172.16.0.0/15, 172.18.0.0/15, 172.20.0.0/15, 172.22.0.0/15, 172.24.0.0/15, 172.26.0.0/15, 172.28.0.0/15, and 172.30.0.0/15.
Calculating the Exhaustion: A /12 network contains exactly eight /15 blocks. By excluding all eight /15 ranges listed in the exhibit, the customer has effectively excluded 100% of the available addresses from the primary 172.16.0.0/12 pool.
Connectivity Problems: When the IPAM pool is exhausted or overly restricted, FortiSASE cannot assign valid, non-overlapping subnets to the PoPs. This leads to connectivity problems for remote users and can cause the system to "fall back" to ranges it believes are available, even if they were intended to be excluded, or simply fail to establish tunnels entirely.
To resolve this, the administrator must ensure that the excluded subnets do not consume the entire pool and that the remaining unexcluded space is large enough to provide a /20 block for every active PoP in their subscription.
In the Secure Private Access (SPA) use case, which two FortiSASE features facilitate access to corporate applications? (Choose two answers)
Options:
SD-WAN
zero trust network access (ZTNA)
thin edge
cloud access security broker (CASB)
Answer:
A, BExplanation:
In a FortiSASE deployment, the Secure Private Access (SPA) use case is specifically designed to provide remote users with secure, high-performance connectivity to internal corporate applications hosted in private data centers or public clouds.5 This is achieved through two primary architectural methods:
SD-WAN Integration (A): FortiSASE integrates natively with existing Fortinet Secure SD-WAN networks.6 In this architecture, the FortiSASE global PoPs act as spokes that establish automated IPsec tunnels to the organization’s FortiGate SD-WAN hubs. This allows the platform to use intelligent application steering and dynamic routing to find the shortest, most efficient path to private resources, ensuring a superior user experience.
Zero Trust Network Access (ZTNA) (B): FortiSASE provides Universal ZTNA to enforce granular, per-session access control.7 Unlike traditional VPNs that grant broad network access, ZTNA verifies the user's identity and the endpoint's security posture (via ZTNA tags) before every application session. This ensures that users only have access to the specific corporate applications they are authorized to use, significantly reducing the attack surface.
Analysis of Other Options: * Thin Edge (C) is a connectivity method used to secure branch offices and micro-branches (typically using FortiExtender), rather than a specific feature for facilitating private corporate application access for individual remote users.
CASB (D) is used for Secure SaaS Access (SSA) to provide visibility and control over third-party cloud applications like Office 365, rather than private applications hosted on-premises.
When viewing the daily summary report generated by FortiSASE. the administrator notices that the report contains very little data. What is a possible explanation for this almost empty report?
Options:
Digital experience monitoring is not configured.
Log allowed traffic is set to Security Events for all policies.
The web filter security profile is not set to Monitor
There are no security profile group applied to all policies.
Answer:
BExplanation:
If the daily summary report generated by FortiSASE contains very little data, one possible explanation is that the "Log allowed traffic" setting is configured to log only "Security Events" for all policies. This configuration limits the amount of data logged, as it only includes security events and excludes normal allowed traffic.
Log Allowed Traffic Setting:
The "Log allowed traffic" setting determines which types of traffic are logged.
When set to "Security Events," only traffic that triggers a security event (such as a threat detection or policy violation) is logged.
Impact on Report Data:
If the log setting excludes regular allowed traffic, the amount of data captured and reported is significantly reduced.
This results in reports with minimal data, as only security-related events are included.
When configuring the DLP rule in FortiSASE using Regex format, what would be the correct order for the configuration steps? (Place the four correct steps in order)

Options:
Answer:

Explanation:
1. DLP Data Pattern
2. DLP Dictionary
3. DLP Sensor
4. DLP Profile
The FortiSASE Data Loss Prevention (DLP) framework follows a hierarchical object-oriented structure. When creating a custom DLP rule using Regular Expressions (Regex), the administrator must build the components from the most granular level upward to the policy level.
DLP Data Pattern: This is the first step where the actual Regex string is defined. The pattern specifies what specific data string (e.g., a specific credit card format or employee ID) the engine should look for.
DLP Dictionary: Once the pattern is created, it must be added to a Dictionary. The dictionary acts as a container that groups one or more data patterns together for easier management.
DLP Sensor: The dictionary is then linked to a DLP Sensor. Within the sensor, you define the "Rule" which specifies the dictionary to use and the action to take (such as block, log, or quarantine) when a match occurs.
DLP Profile: Finally, the sensor is applied to a DLP Profile. This profile is the high-level object that is ultimately selected within a FortiSASE Security Policy to inspect traffic for sensitive data.
For monitoring potentially unwanted applications on endpoints, which information is available on the FortiSASE software installations page? (Choose two answers)
Options:
The endpoint the software is installed on1
The license status of the software2
The vendor of the software3
The usage frequency of the software
Answer:
A, CExplanation:
In FortiSASE, the Software Installations page (located under Network > Managed Endpoints) provides a centralized view of all software inventory reported by the FortiClient agents. This feature is essential for administrators to maintain visibility into the environment and identify potentially unwanted applications (PUA) or unauthorized software installed on remote devices.
Software Inventory Reporting: FortiClient sends the endpoint's software inventory to FortiSASE upon initial registration and updates the portal whenever a change—such as an installation, update, or removal—occurs on the endpoint.
Available Information (Vendor): When viewing the global list of applications, the portal displays detailed metadata for each software entry. This includes the Vendor of the software and its specific version, allowing administrators to differentiate between reputable enterprise applications and suspicious third-party utilities.
Available Information (Endpoint Association): The interface includes an Endpoint Count field that indicates how many devices have a specific application installed. By selecting a specific application and using the View Endpoints action, the administrator can see a list of every individual endpoint where that software is currently active.
Incorrect Options: While license management is a general feature of the ecosystem, the Software Installations page itself does not track the license status of individual third-party applications (Option B). Similarly, while FortiSASE monitors traffic, the Software Installations inventory page does not report on the usage frequency (how often a user opens or uses the app) of the installed binaries (Option D).
By leveraging this inventory, administrators can proactively manage risk by identifying endpoints that possess high-risk software and taking remediation steps or applying ZTNA posture tags based on the presence of specific unauthorized software.
What is the role of ZTNA tags in the FortiSASE Secure Internet Access (SIA) and Secure Private Access (SPA) use cases? (Choose one answer)
Options:
ZTNA tags are created to isolate browser sessions in SIA and enforce data loss prevention in SPA for all devices.
ZTNA tags determine device posture for non-web traffic protocols and are applied only in agentless deployments for SIA.
ZTNA tags determine device posture for endpoints running FortiClient and are used to grant or deny access in SIA or SPA based on that posture.
ZTNA tags are applied to unmanaged endpoints without FortiClient to secure HTTP and HTTPS traffic in SIA and SPA.
Answer:
CExplanation:
In the Fortinet SASE architecture, Zero Trust Network Access (ZTNA) tags (which have been renamed to Security Posture Tags starting with FortiClient/EMS 7.4.0) play a critical role in continuous posture assessment. These tags are dynamic metadata assign8ed to an endpoint based on specific conditions or "tagging rules" defined in the FortiSASE Endpoint Management Service (EMS).
Posture Determination: The FortiClient agent, installed on the endpoint, monitors the device for various security attributes—such as whether an antivirus is running, the presence of specific registry keys, OS version, or the absence of critical vulnerabilities.
SIA (Secure Internet Access) Use Case: In SIA scenarios, FortiSASE uses these tags within security policies to control internet access. For example, a policy may allow full internet access only to endpoints tagged as "Compliant" while redirecting "Non-Compliant" devices to a restricted remediation portal.
SPA (Secure Private Access) Use Case: In SPA (specifically ZTNA Proxy mode), the tags are synchronized from FortiSASE to the corporate FortiGate (acting as the ZTNA Access Proxy).12 When a user attempts to access a private application, the FortiGate checks the endpoint's client certificate and its synchronized ZTNA tags.13 If the endpoint does not meet the required posture (e.g., it is missing a required "Domain-Joined" tag), access is denied at the session level.
According to the FortiSASE 25 Enterprise Administrator Study Guide, ZTNA tags are fundamental to the "Zero Trust" principle because they move beyond static identity (username/password) to verify the real-time security state of the device before granting access to either the internet or internal private resources.
Which two additional components does FortiSASE use for application control to act as an inline-CASB? (Choose two.)
Options:
intrusion prevention system (IPS)
SSL deep inspection
DNS filter
Web filter with inline-CASB
Answer:
B, DExplanation:
FortiSASE uses the following components for application control to act as an inline-CASB (Cloud Access Security Broker):
SSL Deep Inspection:
SSL deep inspection is essential for decrypting and inspecting HTTPS traffic to identify and control applications and data transfers within encrypted traffic.
This allows FortiSASE to enforce security policies on SSL/TLS encrypted traffic, providing visibility and control over cloud applications.
Web Filter with Inline-CASB:
The web filter component integrates with inline-CASB to monitor and control access to cloud applications based on predefined security policies.
This combination provides granular control over cloud application usage, ensuring compliance with security policies and preventing unauthorized data transfers.
Refer to the exhibit.
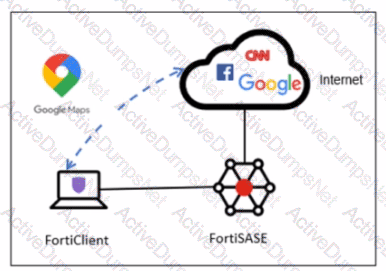
A company has a requirement to inspect all the endpoint internet traffic on FortiSASE, and exclude Google Maps traffic from the FortiSASE VPN tunnel and redirect it to the endpoint physical Interface.
Which configuration must you apply to achieve this requirement?
Options:
Exempt the Google Maps FQDN from the endpoint system proxy settings.
Configure a static route with the Google Maps FQDN on the endpoint to redirect traffic
Configure the Google Maps FQDN as a split tunneling destination on the FortiSASE endpoint profile.
Change the default DNS server configuration on FortiSASE to use the endpoint system DNS.
Answer:
CExplanation:
To meet the requirement of inspecting all endpoint internet traffic on FortiSASE while excluding Google Maps traffic from the FortiSASE VPN tunnel and redirecting it to the endpoint's physical interface, you should configure split tunneling. Split tunneling allows specific traffic to bypass the VPN tunnel and be routed directly through the endpoint's local interface.
Split Tunneling Configuration:
Split tunneling enables selective traffic to be routed outside the VPN tunnel.
By configuring the Google Maps Fully Qualified Domain Name (FQDN) as a split tunneling destination, you ensure that traffic to Google Maps bypasses the VPN tunnel and uses the endpoint's local interface instead.
Implementation Steps:
Access the FortiSASE endpoint profile configuration.
Add the Google Maps FQDN to the split tunneling destinations list.
This configuration directs traffic intended for Google Maps to bypass the VPN tunnel and be routed directly through the endpoint's physical network interface.
How does FortiSASE address the market trends of multicloud and Software-as-a-Service (SaaS) adoption, hybrid workforce, and zero trust? (Choose one answer)
Options:
It focuses solely on securing on-premises networks, ignoring cloud and remote work challenges.
It prioritizes legacy VPN connections for hybrid workforces, bypassing modern cloud and zero-trust security measures.
It provides visibility and control for multicloud and SaaS environments, ensures secure and seamless access for hybrid workforces, and implements zero-trust principles.1
It supports only zero-trust frameworks without addressing multicloud or hybrid workforce needs.
Answer:
CExplanation:
FortiSASE is designed as a unified, single-vendor solution that specifically targets the convergence of networking and security to address the modern challenges of a distributed enterprise.2
Multicloud and SaaS Adoption: FortiSASE addresses the surge in cloud-first strategies by providing Next-Generation Dual-Mode CASB (Cloud Access Security Broker).3 This feature uses both inline and API-based inspection to provide comprehensive visibility into sanctioned and unsanctioned SaaS applications (Shadow IT), ensuring that data is protected regardless of whether it resides in AWS, Azure, Google Cloud, or SaaS platforms like Microsoft 365.
Hybrid Workforce: To support a workforce that moves between the home, the office, and public spaces, FortiSASE delivers consistent security posture.5 It replaces the inconsistent experience of legacy VPNs with a geographically dispersed network of over 150 Points of Presence (PoPs), ensuring low-latency access to applications while maintaining high-performance SSL inspection and threat detection for all remote users.
Zero Trust Integration: Central to the FortiSASE architecture is Universal ZTNA (Zero Trust Network Access).7 Unlike traditional VPNs that grant broad network access, ZTNA applies the principle of "never trust, always verify". It grants access on a per-session, per-application basis, continuously verifying the device posture and user identity before and during application access.9 This shift from implicit to explicit trust significantly reduces the internal attack surface and mitigates the risk of lateral movement by attackers.
By integrating these components into a single operating system (FortiOS) and managed via a single console, FortiSASE simplifies IT operations while delivering the visibility and control required for today's multicloud and hybrid environments.
Which FortiSASE feature ensures least-privileged user access to all applications?
Options:
secure web gateway (SWG)
SD-WAN
zero trust network access (ZTNA)
thin branch SASE extension
Answer:
CExplanation:
Zero Trust Network Access (ZTNA) is the FortiSASE feature that ensures least-privileged user access to all applications. ZTNA operates on the principle of "never trust, always verify," providing secure access based on the identity of users and devices, regardless of their location.
Zero Trust Network Access (ZTNA):
ZTNA ensures that only authenticated and authorized users and devices can access applications.
It applies the principle of least privilege by granting access only to the resources required by the user, minimizing the potential for unauthorized access.
Implementation:
ZTNA continuously verifies user and device trustworthiness and enforces granular access control policies.
This approach enhances security by reducing the attack surface and limiting lateral movement within the network.
A customer wants to upgrade their legacy on-premises proxy to a could-based proxy for a hybrid network. Which FortiSASE features would help the customer to achieve this outcome?
Options:
SD-WAN and NGFW
SD-WAN and inline-CASB
zero trust network access (ZTNA) and next generation firewall (NGFW)
secure web gateway (SWG) and inline-CASB
Answer:
DExplanation:
For a customer looking to upgrade their legacy on-premises proxy to a cloud-based proxy for a hybrid network, the combination of Secure Web Gateway (SWG) and Inline Cloud Access Security Broker (CASB) features in FortiSASE will provide the necessary capabilities.
Secure Web Gateway (SWG):
SWG provides comprehensive web security by inspecting and filtering web traffic to protect against web-based threats.
It ensures that all web traffic, whether originating from on-premises or remote locations, is inspected and secured by the cloud-based proxy.
Inline Cloud Access Security Broker (CASB):
CASB enhances security by providing visibility and control over cloud applications and services.
Inline CASB integrates with SWG to enforce security policies for cloud application usage, preventing unauthorized access and data leakage.
Refer to the exhibits.
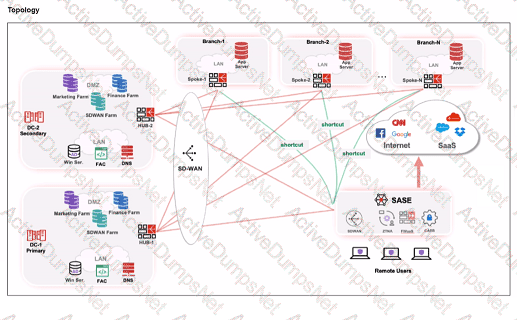
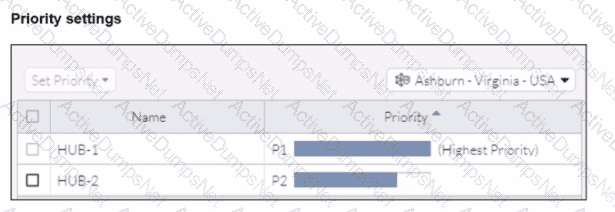
When remote users connected to FortiSASE require access to internal resources on Branch-2. how will traffic be routed?
Options:
FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-2. which will then route traffic to Branch-2.
FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a static route
FortiSASE will use the SD-WAN capability and determine that traffic will be directed to HUB-1, which will then route traffic to Branch-2.
FortiSASE will use the AD VPN protocol and determine that traffic will be directed to Branch-2 directly, using a dynamic route
Answer:
CExplanation:
When remote users connected to FortiSASE require access to internal resources on Branch-2, the following process occurs:
SD-WAN Capability:
FortiSASE leverages SD-WAN to optimize traffic routing based on performance metrics and priorities.
In the priority settings, HUB-1 is configured with the highest priority (P1), whereas HUB-2 has a lower priority (P2).
Traffic Routing Decision:
FortiSASE evaluates the available hubs (HUB-1 and HUB-2) and selects HUB-1 due to its highest priority setting.
Once the traffic reaches HUB-1, it is then routed to the appropriate branch based on internal routing policies.
Branch-2 Access:
Since HUB-1 has the highest priority, FortiSASE directs the traffic to HUB-1.
HUB-1 then routes the traffic to Branch-2, providing the remote users access to the internal resources.
Which service is included in a secure access service edge (SASE) solution, but not in a security service edge (SSE) solution? (Choose one answer)
Options:
SWG
SD-WAN1
CASB
ZTNA
Answer:
BExplanation:
The distinction between SASE (Secure Access Service Edge) and SSE (Security Service Edge) is a fundamental architectural concept in modern networking and security.
SASE Definition: SASE is a comprehensive framework that converges networking capabilities (specifically SD-WAN) with cloud-native security services (SSE) into a single, unified service model.
SSE Definition: SSE represents the security-focused subset of SASE.4 It encompasses the core security pillars required for secure access, including Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA).
The Key Differentiator: While both solutions share the same security stack (SWG, CASB, ZTNA), SD-WAN (Software-Defined Wide Area Network) is the specific networking component that exists in a full SASE solution to provide intelligent path selection and optimized connectivity. SSE intentionally excludes these wide-area networking functions, focusing purely on the security service delivery layer.
According to the FortiSASE 25 Enterprise Administrator Study Guide, organizations that already have a robust networking infrastructure and only require a cloud-delivered security overlay would opt for SSE, whereas those seeking a complete transformation of both network and security would deploy a full SASE solution that includes SD-WAN.
Which two statements about FortiSASE Geofencing with regional compliance are true? (Choose two answers)
Options:
You can configure regional compliance on the security POP or the on-premises device, not both.1
If no regional compliance rule is configured, the connection is made to the closest security POP.
A regional compliance rule can connect only to an on-premises device or only to a security POP.2
The connection order for a regional compliance rule is always the security POP first, followed by the on-premises device.
Answer:
B, CExplanation:
FortiSASE Geofencing and Regional Compliance allow administrators to control where remote users connect based on their physical location, which is determined by the endpoint's public IP address.3
Default Connection Behavior: By default, FortiSASE uses a "best-effort" geolocation logic to ensure the lowest latency for the user. If an administrator has not configured a specific regional compliance rule for a user's country or region, FortiClient will automatically attempt to connect to the closest available FortiSASE security PoP (Point of Presence) based on proximity.4
Regional Compliance Rules: When an organization must enforce data residency or specific security routing requirements, they create Regional Compliance rules. According to the FortiSASE 25 Feature Administration Guide, these rules allow the administrator to override the default "closest PoP" behavior for specific countries.
Connectivity Options: Within a regional compliance rule, the administrator must specify the destination for the traffic. The system provides a choice between two distinct connection types: a FortiSASE Security PoP or an On-premises device (such as a FortiGate acting as a gateway).5 The documentation specifies that a rule is designed to point to one of these types at a time to satisfy the compliance requirement for that specific region.
Connection Priority: While multiple connections can be managed in a priority table, the logic for Regional Compliance is focused on directing the user to the designated compliant entry point. Option D is incorrect because the connection order is determined by the Priority and custom fail-over connections table; an administrator can manually adjust the sequence, so it is not "always" the security PoP first.
A company must provide access to a web server through FortiSASE secure private access for contractors. What is the recommended method to provide access? (Choose one answer)
Options:
Configure a TCP access proxy forwarding rule and push it to the contractor FortiClient endpoint.
Publish the web server URL on a bookmark portal and share it with contractors.
Update the PAC file with the web server URL and share it with contractors.
Update the DNS records on the endpoint to access private applications.
Answer:
BExplanation:
When providing Secure Private Access (SPA) to external contractors who may not be using managed corporate devices, FortiSASE offers specific methods to ensure security while maintaining ease of use.
Bookmark Portal (Clientless Access): For web-based resources like a web server, the recommended and most efficient method for contractors is to use the ZTNA portal (bookmark portal). This allows for clientless access, meaning the contractor does not need to install the FortiClient agent or any specific software on their personal machine.
Workflow: The administrator publishes the web server URL as a bookmark within the FortiSASE portal. Contractors simply log into the secure SASE web portal via their browser, authenticate, and click the bookmark to access the internal server.
Security Benefits: This method leverages the FortiSASE ZTNA access proxy to mediate the connection. It ensures that the contractor is authenticated and that the traffic is inspected without exposing the internal network directly to the contractor's device.
Analysis of Incorrect Options:
Option A: TCP forwarding rules require the FortiClient agent to be installed and managed on the endpoint. Contractors often use unmanaged devices where installing agents is restricted or undesirable.
Option C: Updating a PAC (Proxy Auto-Configuration) file is part of a Secure Web Gateway (SWG) deployment for internet access, not for routing traffic to private internal web servers via an SPA hub.1
Option D: Manually updating DNS records on a contractor's endpoint is an unscalable, insecure, and administratively heavy task that does not provide the session-level security required by ZTNA.
One user has reported connectivity issues; no other users have reported problems. Which tool can the administrator use to identify the problem? (Choose one answer)
Options:
Mobile device management (MDM) service to troubleshoot the connectivity issue.
Digital experience monitoring (DEM) to evaluate the performance metrics of the remote computer.
Forensics service to obtain detailed information about the user's remote computer performance.
SOC-as-a-Service (SOCaaS) to get information about the user's remote computer.
Answer:
BExplanation:
In a FortiSASE deployment, Digital Experience Monitoring (DEM) is the primary diagnostic tool used to troubleshoot connectivity and performance issues specifically for a single user or endpoint.
End-to-End Visibility: DEM provides real-time, end-to-end visibility into the network path between the end-user's device and the application they are trying to reach. This is critical when only one user reports an issue, as it allows administrators to pinpoint whether the problem resides on the local device, the local ISP, the SASE backbone, or the destination application.
Performance Metrics: The DEM agent (often integrated with the FortiMonitor agent on the endpoint) collects granular performance metrics such as latency, jitter, packet loss, and RTT (Round Trip Time). It also provides device-specific health data, including CPU and memory usage, to determine if the connectivity issue is actually caused by the remote computer's performance.
Hop-by-Hop Analysis: Unlike standard monitoring, DEM offers End-to-End Continuous Hop Analytics. This path monitoring visualizes every "hop" in the traffic route and highlights exactly where degraded service is occurring. For a single user experiencing issues while everyone else is fine, this tool immediately triangulates if a specific "problem hop" in their unique connection path is the cause.
Operational Comparison: * MDM (A) is used for managing device configurations and software distribution, not for real-time network performance troubleshooting.
Forensics (C) is a security-focused service used for investigating malware incidents or data breaches, not for measuring network latency.
SOCaaS (D) is a managed security service for threat monitoring and event triage; while it handles "security" connectivity issues (like a blocked IP), it is not a tool for performance metric evaluation.
Which two advantages does FortiSASE bring to businesses with multiple branch offices? (Choose two.)
Options:
It offers centralized management for simplified administration.
It enables seamless integration with third-party firewalls.
it offers customizable dashboard views for each branch location
It eliminates the need to have an on-premises firewall for each branch.
Answer:
A, DExplanation:
FortiSASE brings the following advantages to businesses with multiple branch offices:
Centralized Management for Simplified Administration:
FortiSASE provides a centralized management platform that allows administrators to manage security policies, configurations, and monitoring from a single interface.
This simplifies the administration and reduces the complexity of managing multiple branch offices.
Eliminates the Need for On-Premises Firewalls:
FortiSASE enables secure access to the internet and cloud applications without requiring dedicated on-premises firewalls at each branch office.
This reduces hardware costs and simplifies network architecture, as security functions are handled by the cloud-based FortiSASE solution.
An organization needs to resolve internal hostnames using its internal rather than public DNS servers for remotely connected endpoints. Which two components must be configured on FortiSASE to achieve this? (Choose two.)
Options:
SSL deep inspection
Split DNS rules
Split tunnelling destinations
DNS filter
Answer:
B, CExplanation:
To resolve internal hostnames using internal DNS servers for remotely connected endpoints, the following two components must be configured on FortiSASE:
Split DNS Rules:
Split DNS allows the configuration of specific DNS queries to be directed to internal DNS servers instead of public DNS servers.
This ensures that internal hostnames are resolved using the organization's internal DNS infrastructure, maintaining privacy and accuracy for internal network resources.
Split Tunneling Destinations:
Split tunneling allows specific traffic (such as DNS queries for internal domains) to be routed through the VPN tunnel while other traffic is sent directly to the internet.
By configuring split tunneling destinations, you can ensure that DNS queries for internal hostnames are directed through the VPN to the internal DNS servers.
Which authentication method overrides any other previously configured user authentication on FortiSASE?
Options:
Local
SSO
RADIUS
MFA
Answer:
BExplanation:
Comprehensive and Detailed Explanation From FortiSASE 24.x/25.x, FortiOS 7.4, FortiAuthenticator 6.5, FortiClient 7.0 and later Exact Extract study guide:
In FortiSASE environments, Single Sign-On (SSO) is prioritized as the primary enterprise authentication mechanism. According to the FortiSASE Configuration Guide and Security Operations documentation, when you configure SAML SSO (Single Sign-On), it serves as a global authentication setting that overrides any previously configured local or remote (RADIUS/LDAP) user authentication methods for the secure web gateway (SWG) and VPN tunnels.
The architectural logic is designed to ensure a seamless "Zero Trust" identity provider (IdP) experience. Once SSO is enabled and configured (typically using Azure AD, Okta, or FortiAuthenticator as the IdP), FortiSASE redirects authentication requests to the defined IdP. This effectively supersedes manual local user databases or legacy RADIUS configurations to maintain a single source of truth for identity management. While MFA is often a component of the authentication process, it is a secondary factor, whereas SSO is the foundational method that dictates the authentication flow and overrides prior settings.
Which two components are part of onboarding a secure web gateway (SWG) endpoint? (Choose two)
Options:
FortiSASE CA certificate
proxy auto-configuration (PAC) file
FortiSASE invitation code
FortiClient installer
Answer:
A, BExplanation:
Onboarding a Secure Web Gateway (SWG) endpoint involves several components to ensure secure and effective integration with FortiSASE. Two key components are the FortiSASE CA certificate and the proxy auto-configuration (PAC) file.
FortiSASE CA Certificate:
The FortiSASE CA certificate is essential for establishing trust between the endpoint and the FortiSASE infrastructure.
It ensures that the endpoint can securely communicate with FortiSASE services and inspect SSL/TLS traffic.
Proxy Auto-Configuration (PAC) File:
The PAC file is used to configure the endpoint to direct web traffic through the FortiSASE proxy.
It provides instructions on how to route traffic, ensuring that all web requests are properly inspected and filtered by FortiSASE.
Refer to the exhibits.
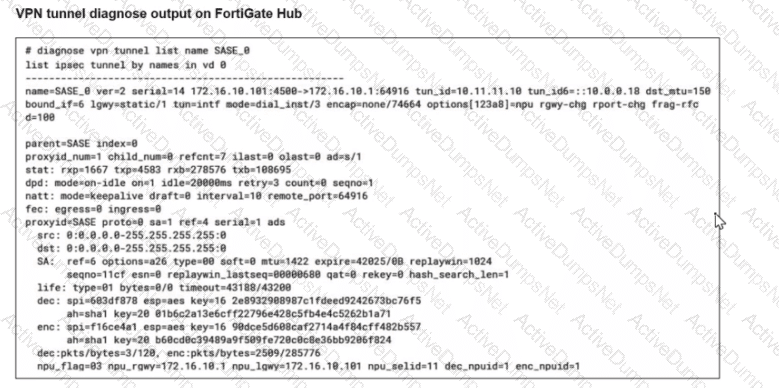
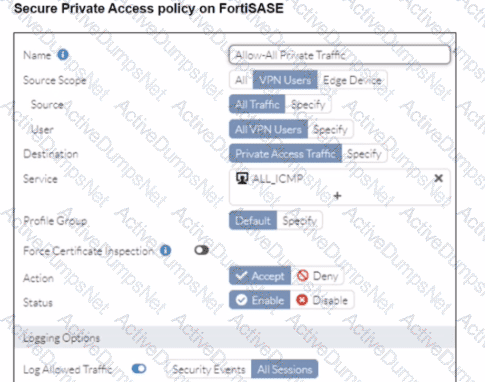
A FortiSASE administrator is trying to configure FortiSASE as a spoke to a FortiGate hub. The tunnel is up to the FortiGale hub. However, the administrator is not able to ping the webserver hosted behind the FortiGate hub.
Based on the output, what is the reason for the ping failures?
Options:
The Secure Private Access (SPA) policy needs to allow PING service.
Quick mode selectors are restricting the subnet.
The BGP route is not received.
Network address translation (NAT) is not enabled on the spoke-to-hub policy.
Answer:
BExplanation:
The reason for the ping failures is due to the quick mode selectors restricting the subnet. Quick mode selectors define the IP ranges and protocols that are allowed through the VPN tunnel, and if they are not configured correctly, traffic to certain subnets can be blocked.
Quick Mode Selectors:
Quick mode selectors specify the source and destination subnets that are allowed to communicate through the VPN tunnel.
If the selectors do not include the subnet of the webserver (192.168.10.0/24), then the traffic will be restricted, and the ping will fail.
Diagnostic Output:
The diagnostic output shows the VPN configuration details, but it is important to check the quick mode selectors to ensure that the necessary subnets are included.
If the quick mode selectors are too restrictive, they will prevent traffic to and from the specified subnets.
Configuration Check:
Verify the quick mode selectors on both the FortiSASE and FortiGate hub to ensure they match and include the subnet of the webserver.
Adjust the selectors to allow the necessary subnets for successful communication.
Unlock NSE7_SSE_AD-25 Features
- NSE7_SSE_AD-25 All Real Exam Questions
- NSE7_SSE_AD-25 Exam easy to use and print PDF format
- Download Free NSE7_SSE_AD-25 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
Questions & Answers PDF Demo
- NSE7_SSE_AD-25 All Real Exam Questions
- NSE7_SSE_AD-25 Exam easy to use and print PDF format
- Download Free NSE7_SSE_AD-25 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
