- Home
- Fortinet
- Fortinet Certified Professional Security Operations
- NSE7_SOC_AR-7.6
- NSE7_SOC_AR-7.6 - Fortinet NSE 7 - Security Operations 7.6 Architect
Fortinet NSE7_SOC_AR-7.6 Fortinet NSE 7 - Security Operations 7.6 Architect Exam Practice Test
Fortinet NSE 7 - Security Operations 7.6 Architect Questions and Answers
When you use a manual trigger to save user input as a variable, what is the correct Jinja expression to reference the variable? (Choose one answer)
Options:
{{ vars.input.params.
{{ globalVars.
{{ vars.item.
{{ vars.steps.
Answer:
AExplanation:
Comprehensive and Detailed Explanation From FortiSOAR 7.6., FortiSIEM 7.3 Exact Extract study guide:
InFortiSOAR 7.6, the playbook engine utilizes Jinja2 expressions to handle dynamic data. When a playbook is configured with aManual Trigger, the administrator can define input fields (such as text, picklists, or checkboxes) that an analyst must fill out when executing the playbook from a record.
Input Parameter Mapping:Any data entered by the user during this manual trigger phase is automatically mapped to the input.params dictionary within the vars object. Therefore, the syntax to retrieve a specific input value is {{ vars.input.params.variable_name }}.
Scope of Variables:This specific path ensures that the variable is pulled from the initial user input rather than from the output of a subsequent step (vars.steps) or a globally defined variable (globalVars).
Refer to the exhibits.
The Malicious File Detect playbook is configured to create an incident when an event handler generates a malicious file detection event.
Why did the Malicious File Detect playbook execution fail?
Options:
The Create Incident task was expecting a name or number as input, but received an incorrect data format
The Get Events task did not retrieve any event data.
The Attach_Data_To_lncident incident task wasexpecting an integer, but received an incorrect data format.
The Attach Data To Incident task failed, which stopped the playbook execution.
Answer:
AExplanation:
Understanding the Playbook Configuration:
The "Malicious File Detect" playbook is designed to create an incident when a malicious file detection event is triggered.
The playbook includes tasks such as Attach_Data_To_Incident, Create Incident, and Get Events.
Analyzing the Playbook Execution:
The exhibit shows that the Create Incident task has failed, and the Attach_Data_To_Incident task has also failed.
The Get Events task succeeded, indicating that it was able to retrieve event data.
Reviewing Raw Logs:
The raw logs indicate an error related to parsing input in the incident_operator.py file.
The error traceback suggests that the task was expecting a specific input format (likely a name or number) but received an incorrect data format.
Identifying the Source of the Failure:
The Create Incident task failure is the root cause since it did not proceed correctly due to incorrect input format.
The Attach_Data_To_Incident task subsequently failed because it depends on the successful creation of an incident.
Conclusion:
The primary reason for the playbook execution failure is that the Create Incident task received an incorrect data format, which was not a name or number as expected.
Refer to the exhibit.
Which two options describe how the Update Asset and Identity Database playbook is configured? (Choose two.)
Options:
The playbook is using a local connector.
The playbook is using a FortiMail connector.
The playbook is using an on-demand trigger.
The playbook is using a FortiClient EMS connector.
Answer:
A, DExplanation:
Understanding the Playbook Configuration:
The playbook named "Update Asset and Identity Database" is designed to update the FortiAnalyzer Asset and Identity database with endpoint and user information.
The exhibit shows the playbook with three main components: ON_SCHEDULE STARTER, GET_ENDPOINTS, and UPDATE_ASSET_AND_IDENTITY.
Analyzing the Components:
ON_SCHEDULE STARTER:This component indicates that the playbook is triggered on a schedule, not on-demand.
GET_ENDPOINTS:This action retrieves information about endpoints, suggesting it interacts with an endpoint management system.
UPDATE_ASSET_AND_IDENTITY:This action updates the FortiAnalyzer Asset and Identity database with the retrieved information.
Evaluating the Options:
Option A:The actions shown in the playbook are standard local actions that can be executed by the FortiAnalyzer, indicating the use of a local connector.
Option B:There is no indication that the playbook uses a FortiMail connector, as the tasks involve endpoint and identity management, not email.
Option C:The playbook is using an "ON_SCHEDULE" trigger, which contradicts the description of an on-demand trigger.
Option D:The action "GET_ENDPOINTS" suggests integration with an endpoint management system, likely FortiClient EMS, which manages endpoints and retrieves information from them.
Conclusion:
The playbook is configured to use a local connector for its actions.
It interacts with FortiClient EMS to get endpoint information and update the FortiAnalyzer Asset and Identity database.
A customer wants FortiAnalyzer to run an automation stitch that executes a CLI command on FortiGate to block a predefined list of URLs, if a botnet command-and-control (C&C) server IP is detected.
Which FortiAnalyzer feature must you use to start this automation process?
Options:
Playbook
Data selector
Event handler
Connector
Answer:
CExplanation:
Understanding Automation Processes in FortiAnalyzer:
FortiAnalyzer can automate responses to detected security events, such as running commands on FortiGate devices.
Analyzing the Customer Requirement:
The customer wants to run a CLI command on FortiGate to block predefined URLs when a botnet C&C server IP is detected.
This requires an automated response triggered by a specific event.
Evaluating the Options:
Option A:Playbooks orchestrate complex workflows but are not typically used for direct event-triggered automation processes.
Option B:Data selectors filter logs based on criteria but do not initiate automation processes.
Option C:Event handlers can be configured to detect specific events (such as detecting a botnet C&C server IP) and trigger automation stitches to execute predefined actions.
Option D:Connectors facilitate communication between FortiAnalyzer and other systems but are not the primary mechanism for initiating automation based on log events.
Conclusion:
To start the automation process when a botnet C&C server IP is detected, you must use anEvent handlerin FortiAnalyzer.
Your company is doing a security audit To pass the audit, you must take an inventory of all software and applications running on all Windows devices
Which FortiAnalyzer connector must you use?
Options:
FortiClient EMS
ServiceNow
FortiCASB
Local Host
Answer:
AExplanation:
Requirement Analysis:
The objective is to inventory all software and applications running on all Windows devices within the organization.
This inventory must be comprehensive and accurate to pass the security audit.
Key Components:
FortiClient EMS (Endpoint Management Server):
FortiClient EMS provides centralized management of endpoint security, including software and application inventory on Windows devices.
It allows administrators to monitor, manage, and report on all endpoints protected by FortiClient.
Connector Options:
FortiClient EMS:
Best suited for managing and reporting on endpoint software and applications.
Provides detailed inventory reports for all managed endpoints.
Selected as it directly addresses the requirement of taking inventory of software and applications on Windows devices.
ServiceNow:
Primarily a service management platform.
While it can be used for asset management, it is not specifically tailored for endpoint software inventory.
Not selected as it does not provide direct endpoint inventory management.
FortiCASB:
Focuses on cloud access security and monitoring SaaS applications.
Not applicable for managing or inventorying endpoint software.
Not selected as it is not related to endpoint software inventory.
Local Host:
Refers to handling events and logs within FortiAnalyzer itself.
Not specific enough for detailed endpoint software inventory.
Not selected as it does not provide the required endpoint inventory capabilities.
Implementation Steps:
Step 1: Ensure all Windows devices are managed by FortiClient and connected to FortiClient EMS.
Step 2: Use FortiClient EMS to collect and report on the software and applications installed on these devices.
Step 3: Generate inventory reports from FortiClient EMS to meet the audit requirements.
Fortinet Documentation on FortiClient EMS FortiClient EMS Administration Guide
By using the FortiClient EMS connector, you can effectively inventory all software and applications on Windows devices, ensuring compliance with the security audit requirements.
Match the FortiSIEM device type to its description. Select each FortiSIEM device type in the left column, hold and drag it to the blank space next to its corresponding description in the column on the right.
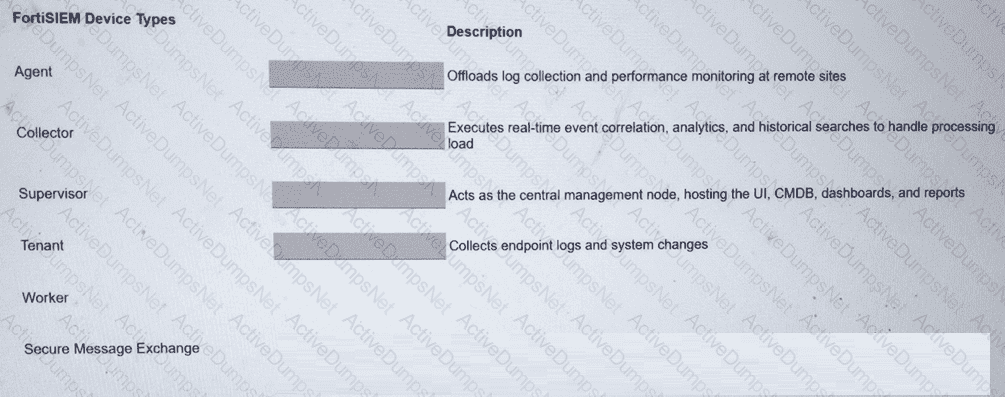
Options:
Answer:
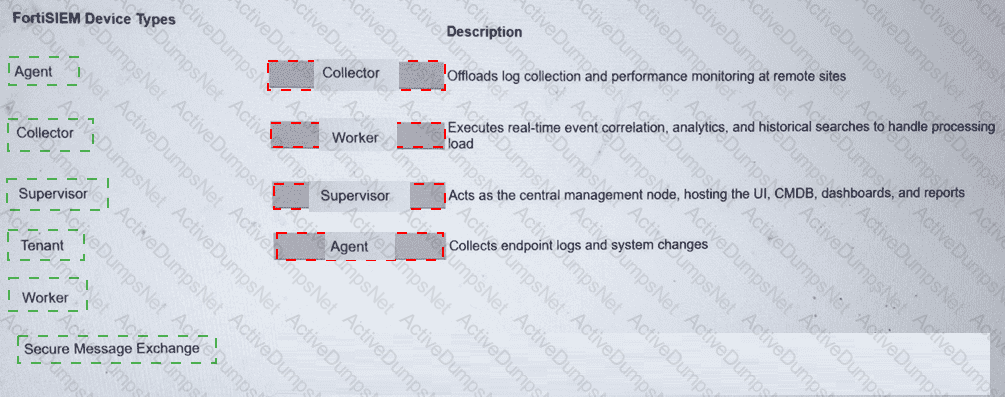
Explanation:
Collector2.Worker3.Supervisor4.Agent
The FortiSIEM 7.3 architecture is built upon a distributed multi-tenant model consisting of several distinct functional roles to ensure scalability and performance:
Supervisor:This is the primary management node in a FortiSIEM cluster. It hosts the Graphical User Interface (GUI), the Configuration Management Database (CMDB), and manages the overall system configurations, reporting, and dashboarding.
Worker:These nodes are responsible for the heavy lifting of data processing. They execute real-time event correlation against the rules engine, perform historical search queries, and handle the analytics workload to ensure the Supervisor node is not overwhelmed.
Collector:Collectors are typically deployed at remote sites or different network segments to offload log collection from the central cluster. They receive logs via Syslog, SNMP, or WMI, compress the data, and securely forward it to the Workers or Supervisor. They also perform performance monitoring of local devices.
Agent:These are lightweight software components installed directly on endpoints (Windows/Linux). Their primary role is to collect local endpoint logs, monitor file integrity (system changes), and track user activity that cannot be captured via traditional network-based logging.
Refer to the exhibits.
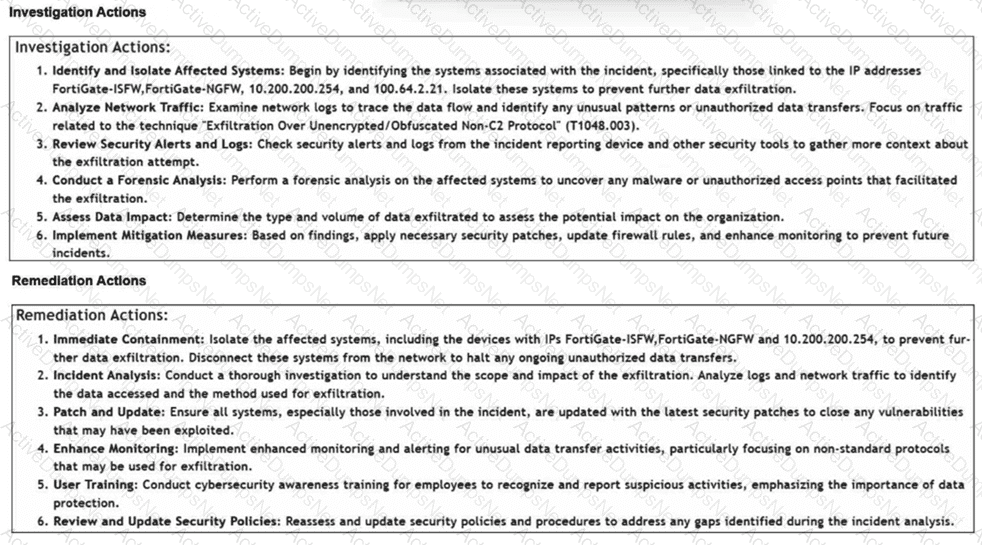
How is the investigation and remediation output generated on FortiSIEM? (Choose one answer)
Options:
By exporting an incident
By running an incident report
By using FortiAI to summarize the incident
By viewing the Context tab of an incident
Answer:
CExplanation:
Comprehensive and Detailed Explanation From FortiSOAR 7.6., FortiSIEM 7.3 Exact Extract study guide:
InFortiSIEM 7.3, a key innovation is the integration ofFortiAI, which provides generative AI capabilities to assist SOC analysts during the triage and response process.
Generative AI Summary:When an incident occurs, FortiAI can automatically analyze the underlying logs, correlation logic, and MITRE ATT&CK techniques (such as "Exfiltration Over Alternative Protocol" shown in the exhibit) to generate a human-readable summary.
Structured Output:The output displayed in the exhibit—specifically the categorizedInvestigation Actions(identifying affected systems, analyzing traffic) andRemediation Actions(immediate containment, patching, user training)—is the typical result of a FortiAI summary request.
Analyst Efficiency:This feature is designed to reduce the "mean time to respond" (MTTR) by providing analysts with immediate, actionable steps without requiring them to manually piece together the recommended response plan from static documentation or disparate log views.
Why other options are incorrect:
Exporting an incident (A):Exporting an incident typically results in a raw data file (CSV/JSON/PDF) containing the log data and metadata, rather than an AI-generated strategic plan for investigation and remediation.
Running an incident report (B):Standard incident reports provide statistical and historical data about incidents over time. They do not dynamically generate specific, numbered investigation steps tailored to the unique context of a single live incident.
Context tab (D):The Context tab in FortiSIEM is primarily used to view theCMDBinformation of the involved assets (e.g., host details, owner, location) and related historical events. While it provides thedataneeded for an investigation, it does not provide thelist of actionsto take.
What are three capabilities of the built-in FortiSOAR Jinja editor? (Choose three answers)
Options:
It renders output by combining Jinja expressions and JSON input.
It checks the validity of a Jinja expression.
It creates new records in bulk.
It loads the environment JSON of a recently executed playbook.
It defines conditions to trigger a playbook step.
Answer:
A, B, DExplanation:
Comprehensive and Detailed Explanation From FortiSOAR 7.6., FortiSIEM 7.3 Exact Extract study guide:
The built-in Jinja editor inFortiSOAR 7.6is a powerful utility designed to help playbook developers write and test complex data manipulation logic without having to execute the entire playbook. Its primary capabilities include:
Renders output (A):The editor provides a "Preview" or "Evaluation" pane. By combining aJinja expressionwith a sampleJSON input(manually entered or loaded), the editor dynamically calculates and displays the resulting output. This allows for immediate verification of data transformation logic.
Checks validity (B):The editor includes built-in linting and syntax validation. It alerts the developer to errors such as unclosed brackets, incorrect filter usage, or invalid syntax, ensuring that only valid Jinja code is saved into the playbook step.
Loads environment JSON (D):One of the most significant features for troubleshooting is the ability toload the environment JSONfrom a recent execution. This populates the editor's variable context (vars) with the actual data from a specific playbook run, allowing the developer to test expressions against real-world data that recently passed through the system.
Why other options are incorrect:
Creates new records in bulk (C):While Jinja expressions are used to format the data that goes into a record, the actual creation of records is handled by the"Create Record"step or specificConnectors, not by the Jinja editor utility itself.
Defines conditions to trigger a playbook step (E):Jinja is thelanguageused to write conditions within a "Decision" step or "Step Utilities," but the Jinja Editor is a tool forevaluating and testingthose expressions. The definition of the condition logic and the triggering behavior is a function of the Playbook Engine and Step configuration, not the editor's standalone capabilities.
Review the following incident report:
Attackers leveraged a phishing email campaign targeting your employees.
The email likely impersonated a trusted source, such as the IT department, and requested login credentials.
An unsuspecting employee clicked a malicious link in the email, leading to the download and execution of a Remote Access Trojan (RAT).
The RAT provided the attackers with remote access and a foothold in the compromised system.
Which two MITRE ATT&CK tactics does this incident report capture? (Choose two.)
Options:
Initial Access
Defense Evasion
Lateral Movement
Persistence
Answer:
A, DExplanation:
Understanding the MITRE ATT&CK Tactics:
The MITRE ATT&CK framework categorizes various tactics and techniques used by adversaries to achieve their objectives.
Tactics represent the objectives of an attack, while techniques represent how those objectives are achieved.
Analyzing the Incident Report:
Phishing Email Campaign:This tactic is commonly used for gaining initial access to a system.
Malicious Link and RAT Download:Clicking a malicious link and downloading a RAT is indicative of establishing initial access.
Remote Access Trojan (RAT):Once installed, the RAT allows attackers to maintain access over an extended period, which is a persistence tactic.
Mapping to MITRE ATT&CK Tactics:
Initial Access:
This tactic covers techniques used to gain an initial foothold within a network.
Techniques include phishing and exploiting external remote services.
The phishing campaign and malicious link click fit this category.
Persistence:
This tactic includes methods that adversaries use to maintain their foothold.
Techniques include installing malware that can survive reboots and persist on the system.
The RAT provides persistent remote access, fitting this tactic.
Exclusions:
Defense Evasion:
This involves techniques to avoid detection and evade defenses.
While potentially relevant in a broader context, the incident report does not specifically describe actions taken to evade defenses.
Lateral Movement:
This involves moving through the network to other systems.
The report does not indicate actions beyond initial access and maintaining that access.
Conclusion:
The incident report captures the tactics ofInitial AccessandPersistence.
Which two ways can you create an incident on FortiAnalyzer? (Choose two.)
Options:
Using a connector action
Manually, on the Event Monitor page
By running a playbook
Using a custom event handler
Answer:
B, DExplanation:
Understanding Incident Creation in FortiAnalyzer:
FortiAnalyzer allows for the creation of incidents to track and manage security events.
Incidents can be created both automatically and manually based on detected events and predefined rules.
Analyzing the Methods:
Option A:Using a connector action typically involves integrating with other systems or services and is not a direct method for creating incidents on FortiAnalyzer.
Option B:Incidents can be created manually on the Event Monitor page by selecting relevant events and creating incidents from those events.
Option C:While playbooks can automate responses and actions, the direct creation of incidents is usually managed through event handlers or manual processes.
Option D:Custom event handlers can be configured to trigger incident creation based on specific events or conditions, automating the process within FortiAnalyzer.
Conclusion:
The two valid methods for creating an incident on FortiAnalyzer are manually on the Event Monitor page and using a custom event handler.
Which role does a threat hunter play within a SOC?
Options:
investigate and respond to a reported security incident
Collect evidence and determine the impact of a suspected attack
Search for hidden threats inside a network which may have eluded detection
Monitor network logs to identify anomalous behavior
Answer:
CExplanation:
Role of a Threat Hunter:
A threat hunter proactively searches for cyber threats that have evaded traditional security defenses. This role is crucial in identifying sophisticated and stealthy adversaries that bypass automated detection systems.
Key Responsibilities:
Proactive Threat Identification:
Threat hunters use advanced tools and techniques to identify hidden threats within the network. This includes analyzing anomalies, investigating unusual behaviors, and utilizing threat intelligence.
Refer to the exhibits.
You configured a custom event handler and an associated rule to generate events whenever FortiMail detects spam emails. However, you notice that the event handler is generating events for both spam emails and clean emails.
Which change must you make in the rule so that it detects only spam emails?
Options:
In the Log Type field, select Anti-Spam Log (spam)
In the Log filter by Text field, type type==spam.
Disable the rule to use the filter in the data selector to create the event.
In the Trigger an event when field, select Within a group, the log field Spam Name (snane) has 2 or more unique values.
Answer:
AExplanation:
Understanding the Custom Event Handler Configuration:
The event handler is set up to generate events based on specific log data.
The goal is to generate events specifically for spam emails detected by FortiMail.
Analyzing the Issue:
The event handler is currently generating events for both spam emails and clean emails.
This indicates that the rule's filtering criteria are not correctly distinguishing between spam and non-spam emails.
Evaluating the Options:
Option A:Selecting the "Anti-Spam Log (spam)" in the Log Type field will ensure that only logs related to spam emails are considered. This is the most straightforward and accurate way to filter for spam emails.
Option B:Typing type==spam in the Log filter by Text field might help filter the logs, but it is not as direct and reliable as selecting the correct log type.
Option C:Disabling the rule to use the filter in the data selector to create the event does not address the issue of filtering for spam logs specifically.
Option D:Selecting "Within a group, the log field Spam Name (snane) has 2 or more unique values" is not directly relevant to filtering spam logs and could lead to incorrect filtering criteria.
Conclusion:
The correct change to make in the rule is to select "Anti-Spam Log (spam)" in the Log Type field. This ensures that the event handler only generates events for spam emails.
You are trying to create a playbook that creates a manual task showing a list of public IPv6 addresses. You were successful in extracting all IP addresses from a previous action into a variable calledip_list, which contains both private and public IPv4 and IPv6 addresses. You must now filter the results to display only public IPv6 addresses. Which two Jinja expressions can accomplish this task? (Choose two answers)
Options:
{{ vars.ip_list | ipv6addr('public') }}
{{ vars.ip_list | ipaddr('public') | ipv6 }}
{{ vars.ip_list | ipaddr('!private') | ipv6 }}
{{ vars.ip_list | ipv6 | ipaddr('public') }}
Answer:
B, DExplanation:
Comprehensive and Detailed Explanation From FortiSOAR 7.6., FortiSIEM 7.3 Exact Extract study guide:
InFortiSOAR 7.6, the playbook engine utilizes the powerful ipaddr family of Jinja filters (derived from the Ansible netaddr library) to manipulate network data. To isolate public IPv6 addresses from a mixed list, the order of operations in the filter chain ensures the correct data is extracted:
Double Filtering Sequence (B):In the expression {{ vars.ip_list | ipaddr('public') | ipv6 }}, the first filter ipaddr('public') processes the entire list and retains only public addresses, including both IPv4 and IPv6 versions. The second filter in the pipe, | ipv6, then takes that subset of public addresses and filters them again to keep only those that conform to the IPv6 standard. The final result is a list containing only public IPv6 addresses.
Version-First Filtering (D):In the expression {{ vars.ip_list | ipv6 | ipaddr('public') }}, the logic is reversed but equally effective. The first filter | ipv6 immediately strips all IPv4 and non-IP strings from the list, leaving only IPv6 addresses (both private and public). The subsequent filter | ipaddr('public') then evaluates these IPv6 addresses and discards any that fall within the private/unique-local ranges (like ULA or link-local), resulting in the same set of public IPv6 addresses.
Why other options are incorrect:
A (ipv6addr 'public'):While ipv6addr is a valid filter in many Ansible environments, FortiSOAR's standard documentation for manual task creation and data manipulation primarily emphasizes the use of the generic ipaddr filter with specific flags or chained version filters (like | ipv6) to ensure cross-compatibility with the underlying Python libraries used by the SOAR engine.
C (!private syntax):The ipaddr filter utilizes specific keywords for classification. While "not private" is the logical requirement, the filter expects positive assertions such as 'public', 'private', or 'multicast'. The !private syntax is not a supported or documented operator for this filter within the Fortinet SOC ecosystem.
Which two statements about the FortiAnalyzer Fabric topology are true? (Choose two.)
Options:
Downstream collectors can forward logs to Fabric members.
Logging devices must be registered to the supervisor.
The supervisor uses an API to store logs, incidents, and events locally.
Fabric members must be in analyzer mode.
Answer:
B, DExplanation:
Understanding FortiAnalyzer Fabric Topology:
The FortiAnalyzer Fabric topology is designed to centralize logging and analysis across multiple devices in a network.
It involves a hierarchy where the supervisor node manages and coordinates with other Fabric members.
Analyzing the Options:
Option A:Downstream collectors forwarding logs to Fabric members is not a typical configuration. Instead, logs are usually centralized to the supervisor.
Option B:For effective management and log centralization, logging devices must be registered to the supervisor. This ensures proper log collection and coordination.
Option C:The supervisor does not primarily use an API to store logs, incidents, and events locally. Logs are stored directly in the FortiAnalyzer database.
Option D:For the Fabric topology to function correctly, all Fabric members need to be in analyzer mode. This mode allows them to collect, analyze, and forward logs appropriately within the topology.
Conclusion:
The correct statements regarding the FortiAnalyzer Fabric topology are that logging devices must be registered to the supervisor and that Fabric members must be in analyzer mode.
Refer to the exhibits.
What can you conclude from analyzing the data using the threat hunting module?
Options:
Spearphishing is being used to elicit sensitive information.
DNS tunneling is being used to extract confidential data from the local network.
Reconnaissance is being used to gather victim identity information from the mail server.
FTP is being used as command-and-control (C&C) technique to mine for data.
Answer:
BExplanation:
Understanding the Threat Hunting Data:
The Threat Hunting Monitor in the provided exhibits shows various application services, their usage counts, and data metrics such as sent bytes, average sent bytes, and maximum sent bytes.
The second part of the exhibit lists connection attempts from a specific source IP (10.0.1.10) to a destination IP (8.8.8.8), with repeated "Connection Failed" messages.
Analyzing the Application Services:
DNS is the top application service with a significantly high count (251,400) and notable sent bytes (9.1 MB).
This large volume of DNS traffic is unusual for regular DNS queries and can indicate the presence of DNS tunneling.
DNS Tunneling:
DNS tunneling is a technique used by attackers to bypass security controls by encoding data within DNS queries and responses. This allows them to extract data from the local network without detection.
The high volume of DNS traffic, combined with the detailed metrics, suggests that DNS tunneling might be in use.
Connection Failures to 8.8.8.8:
The repeated connection attempts from the source IP (10.0.1.10) to the destination IP (8.8.8.8) with connection failures can indicate an attempt to communicate with an external server.
Google DNS (8.8.8.8) is often used for DNS tunneling due to its reliability and global reach.
Conclusion:
Given the significant DNS traffic and the nature of the connection attempts, it is reasonable to conclude that DNS tunneling is being used to extract confidential data from the local network.
Why Other Options are Less Likely:
Spearphishing (A): There is no evidence from the provided data that points to spearphishing attempts, such as email logs or phishing indicators.
Reconnaissance (C): The data does not indicate typical reconnaissance activities, such as scanning or probing mail servers.
FTP C&C (D): There is no evidence of FTP traffic or command-and-control communications using FTP in the provided data.
SANS Institute: "DNS Tunneling: How to Detect Data Exfiltration and Tunneling Through DNS Queries" SANS DNS Tunneling
OWASP: "DNS Tunneling" OWASP DNS Tunneling
By analyzing the provided threat hunting data, it is evident that DNS tunneling is being used to exfiltrate data, indicating a sophisticated method of extracting confidential information from the network.
Which three end user logs does FortiAnalyzer use to identify possible IOC compromised hosts? (Choose three answers)
Options:
Web filter logs1
Email filter logs
DNS filter logs2
Application filter logs
IPS logs
Answer:
A, C, EExplanation:
Comprehensive and Detailed Explanation From FortiSOAR 7.6., FortiSIEM 7.3 Exact Extract study guide:
In the context of the Fortinet Security Fabric,FortiAnalyzerperforms Indicator of Compromise (IOC) detection by correlating various security logs against a threat intelligence database.3The IOC engine specifically analyzes the following logs of each end user to identify potentially compromised hosts:
Web Filter Logs (A):The engine parses web filtering logs to identify access attempts to blacklisted URLs, malicious domains, or IPs associated with known malware distribution sites.4If a match is found in the threat database, the host is flagged as compromised.
DNS Filter Logs (C):DNS requests are a primary indicator of a compromise. The engine monitors these logs for queries directed at known Command and Control (C2) servers or domains generated by Domain Generation Algorithms (DGA).5
IPS Logs (E):Intrusion Prevention System (IPS) logs provide critical data on signature matches for known attacks. In newer Security Operations (SOC) curricula, IPS logs are used alongside Web and DNS logs to provide a high-fidelity assessment of whether a host is currently infected and attempting to communicate with an external threat actor.
Why other options are incorrect:
Email Filter Logs (B):While important for detecting phishing attempts (Initial Access), email logs are generally used for content filtering and antispam rather than being a primary source for the IOC engine's behavioral "calling home" detection in the FortiAnalyzer Compromised Hosts view.
Application Filter Logs (D):Application control logs provide visibility into software usage but are less commonly used by the core IOC engine for identifying blacklisted network destinations compared to Web and DNS filtering.
Which statement describes automation stitch integration between FortiGate and FortiAnalyzer?
Options:
An event handler on FortiAnalyzer executes an automation stitch when an event is created.
An automation stitch is configured on FortiAnalyzer and mapped to FortiGate using the FortiOS connector.
An event handler on FortiAnalyzer is configured to send a notification to FortiGate to trigger an automation stitch.
A security profile on FortiGate triggers a violation and FortiGate sends a webhook call to FortiAnalyzer.
Answer:
DExplanation:
Overview of Automation Stitches: Automation stitches in Fortinet solutions enable automated responses to specific events detected within the network. This automation helps in swiftly mitigating threats without manual intervention.
FortiGate Security Profiles:
FortiGate uses security profiles to enforce policies on network traffic. These profiles can include antivirus, web filtering, intrusion prevention, and more.
When a security profile detects a violation or a specific event, it can trigger predefined actions.
Webhook Calls:
FortiGate can be configured to send webhook calls upon detecting specific security events.
A webhook is an HTTP callback triggered by an event, sending data to a specified URL. This allows FortiGate to communicate with other systems, such as FortiAnalyzer.
FortiAnalyzer Integration:
FortiAnalyzer collects logs and events from various Fortinet devices, providing centralized logging and analysis.
Upon receiving a webhook call from FortiGate, FortiAnalyzer can further analyze the event, generate reports, and take automated actions if configured to do so.
Detailed Process:
Step 1: A security profile on FortiGate triggers a violation based on the defined security policies.
Step 2: FortiGate sends a webhook call to FortiAnalyzer with details of the violation.
Step 3: FortiAnalyzer receives the webhook call and logs the event.
Step 4: Depending on the configuration, FortiAnalyzer can execute an automation stitch to respond to the event, such as sending alerts, generating reports, or triggering further actions.
Fortinet Documentation: FortiOS Automation Stitches
FortiAnalyzer Administration Guide: Details on configuring event handlers and integrating with FortiGate.
FortiGate Administration Guide: Information on security profiles and webhook configurations.
By understanding the interaction between FortiGate and FortiAnalyzer through webhook calls and automation stitches, security operations can ensure a proactive and efficient response to security events.
Unlock NSE7_SOC_AR-7.6 Features
- NSE7_SOC_AR-7.6 All Real Exam Questions
- NSE7_SOC_AR-7.6 Exam easy to use and print PDF format
- Download Free NSE7_SOC_AR-7.6 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
Questions & Answers PDF Demo
- NSE7_SOC_AR-7.6 All Real Exam Questions
- NSE7_SOC_AR-7.6 Exam easy to use and print PDF format
- Download Free NSE7_SOC_AR-7.6 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
