Fortinet NSE7_CDS_AR-7.6 Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect Exam Practice Test
Fortinet NSE 7 - Public Cloud Security 7.6.4 Architect Questions and Answers
An administrator would like to use FortiCNP to keep track of sensitive data files located in the Amazon Web Services (AWS) S3 bucket and protect it from malware. Which FortiCNP feature should the administrator use?
Refer to the exhibit.
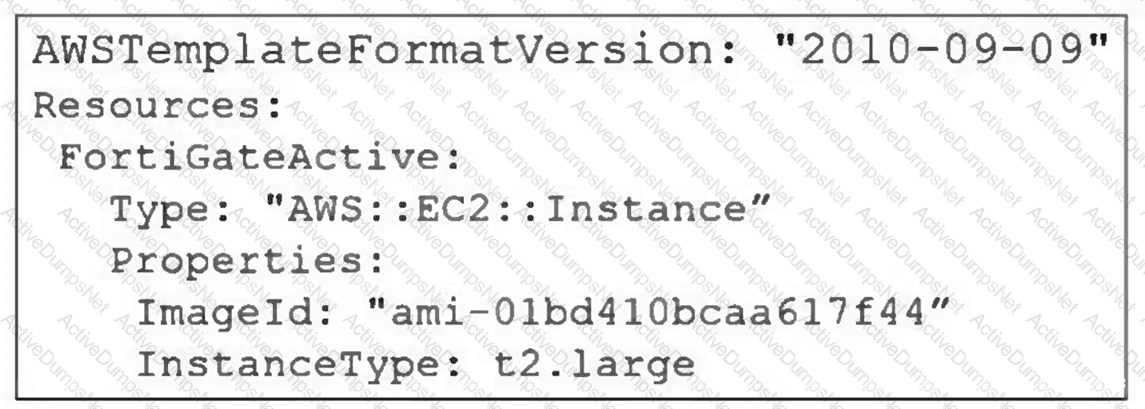
A senior administrator in a multinational organization needs to include a comment in the template shown in the exhibit to ensure that administrators from other regions change the EC2 instance size value to one that meets the requirements in their local deployments. How can the administrator add the comment in that section of the file? (Choose one answer)
Your DevOps team is evaluating different Infrastructure as Code (IaC) solutions for deploying complex Azure environments.
What is an advantage of choosing Azure Bicep over other IaC tools available?
Refer to the exhibit.

A managed security service provider (MSSP) administration team is trying to deploy a new HA cluster in Azure to filter traffic to and from a client that is also using Azure. However, every deployment attempt fails, and only some of the resources are deployed successfully. While troubleshooting this issue, the team runs the command shown in the exhibit.
What are the implications of the output of the command?
Refer to the exhibit.
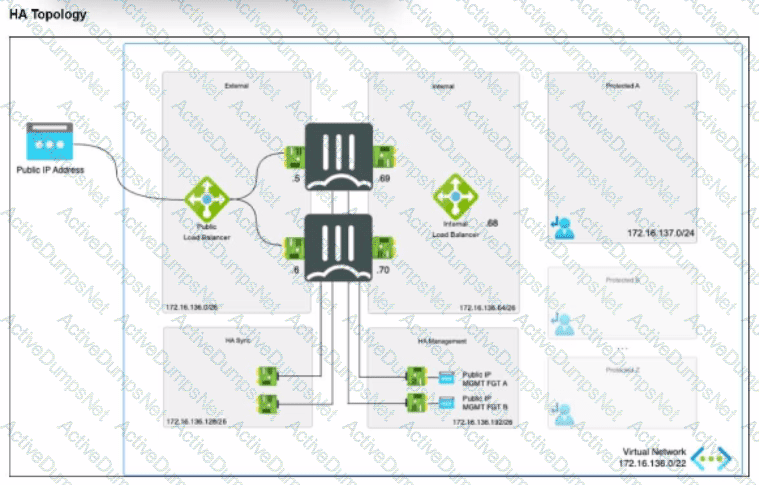
The exhibit shows an active-passive high availability FortiGate pair with external and internal Azure load balancers There is no SDN connector used in this solution.
Which configuration must the administrator implement on each FortiGate?
Your administrator instructed you to deploy an Azure vWAN solution to create a connection between the main company site and branch sites to the other company VNETs. What is the best connection solution available between your company headquarters, branch sites, and the Azure vWAN hub? (Choose one answer)
Refer to the exhibit.
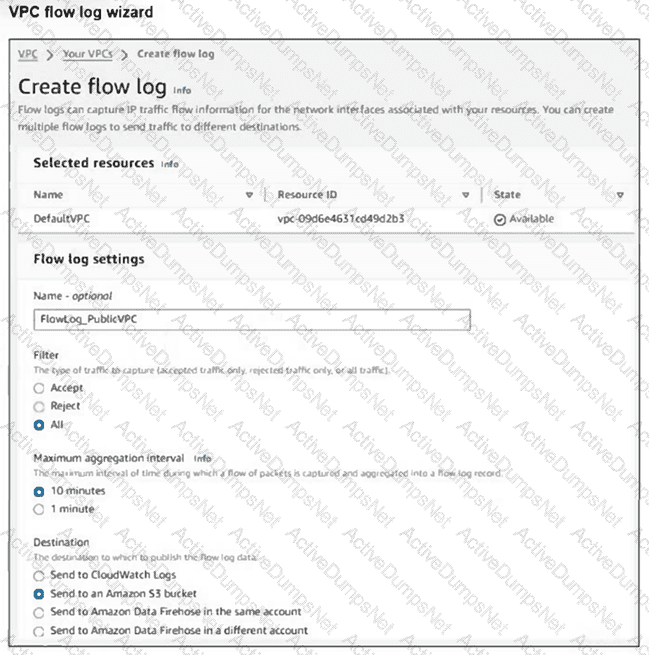
Your team notices an unusually high volume of traffic sourced at one of the organizations FortiGate EC2 instances. They create a flow log to obtain and analyze detailed information about this traffic. However, when they checked the log, they found that it included traffic that was not associated with the FortiGate instance in question.
What can they do to obtain the correct logs? (Choose one answer)
Refer to the exhibit.
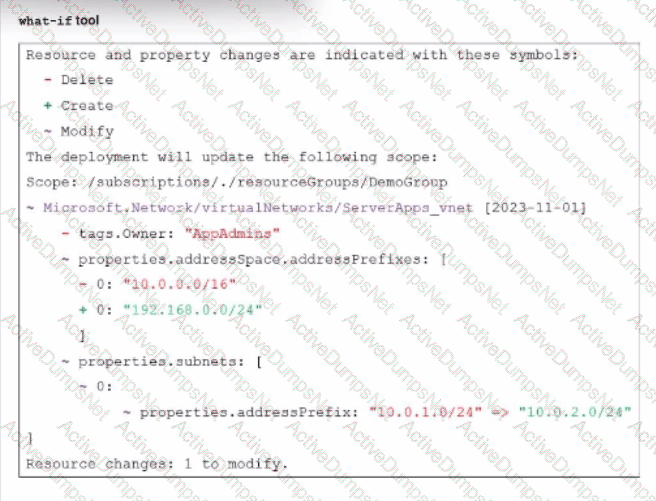
An administrator used the what-if tool to preview changes to an Azure Bicep file.
What will happen if the administrator decides to apply these changes in Azure?
You are experiencing intermittent connectivity issues in a FortiGate HA cluster deployed with Azure gateway load balancer. Traffic is being dropped when it passes through the cluster. What is the cause of the issue? (Choose one answer)1
What are two main features in Amazon Web Services (AWS) network access control lists (NACLs)? (Choose two answers)
As part of your organization's monitoring plan, you have been tasked with obtaining and analyzing detailed information about the traffic sourced at one of your FortiGate EC2 instances.
What can you do to achieve this goal?
You have deployed a FortiGate HA cluster in Azure using a gateway load balancer for traffic inspection. However, traffic is not being routed correctly through the firewalls.
What can be the cause of the issue?
Refer to the exhibit.
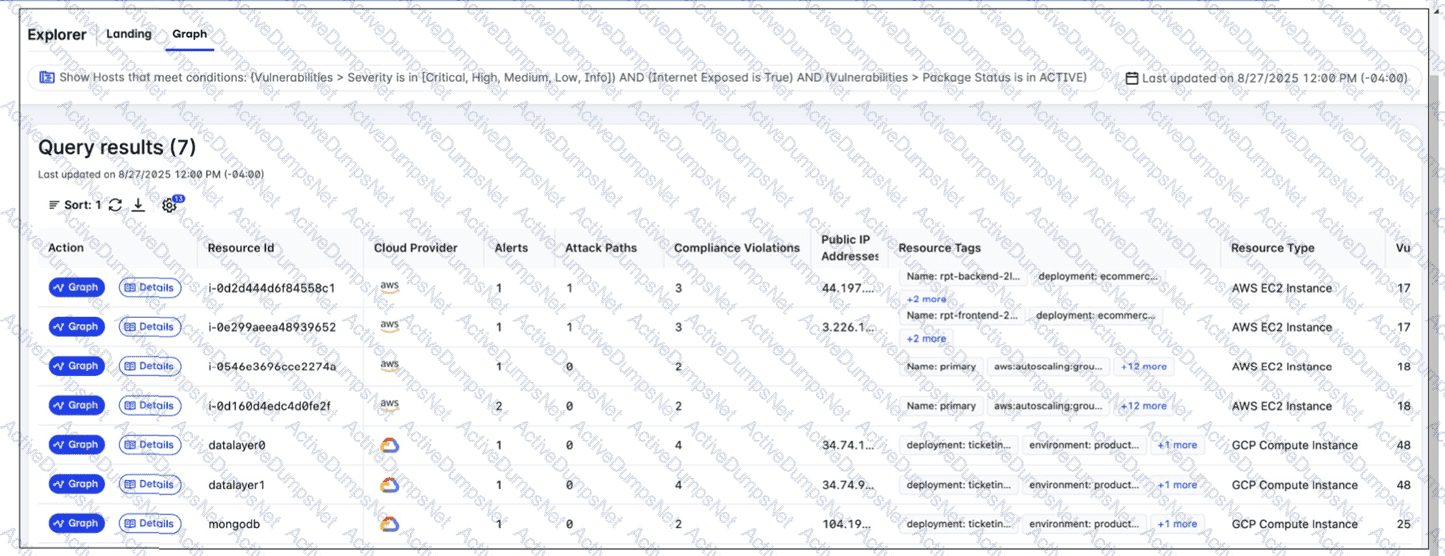
A FortiCNAPP administrator used the FortiCNAPP Explorer to reveal all hosts exposed to the internet that are running active packages with vulnerabilities of all severity levels. Why do only the first two results have an attack path? (Choose one answer)
You must add an Amazon Web Services (AWS) network access list (NACL) rule to allow SSH traffic to a subnet for temporary testing purposes. When you review the current inbound and outbound NACL rules, you notice that the rules with number 5 deny SSH and telnet traffic to the subnet.
What can you do to allow SSH traffic?
An administrator implements FortiWeb ingress controller to protect containerized web applications in an AWS Elastic Kubernetes Service (EKS) cluster.
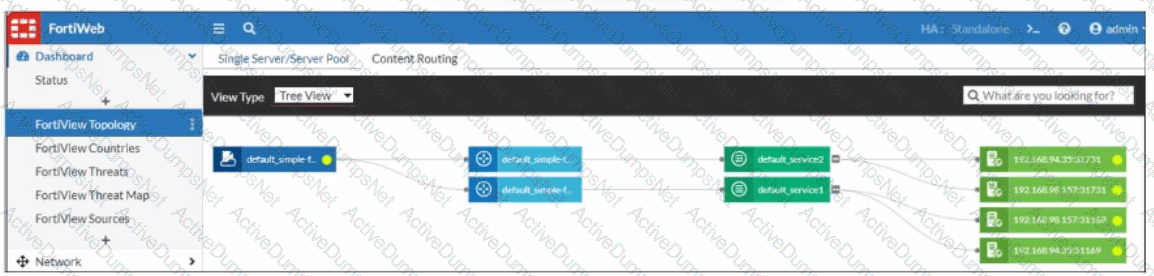
What can you conclude about the topology shown in FortiView?
An administrator is looking for a solution that can provide insight into users and data stored in major SaaS applications in the multicloud environment. Which product should the administrator deploy to have secure access to SaaS applications? (Choose one answer)
