- Home
- Fortinet
- Fortinet Network Security Expert
- NSE5_FNC_AD_7.6
- NSE5_FNC_AD_7.6 - Fortinet NSE 5 - FortiNAC-F 7.6 Administrator
Fortinet NSE5_FNC_AD_7.6 Fortinet NSE 5 - FortiNAC-F 7.6 Administrator Exam Practice Test
Fortinet NSE 5 - FortiNAC-F 7.6 Administrator Questions and Answers
Refer to the exhibits.
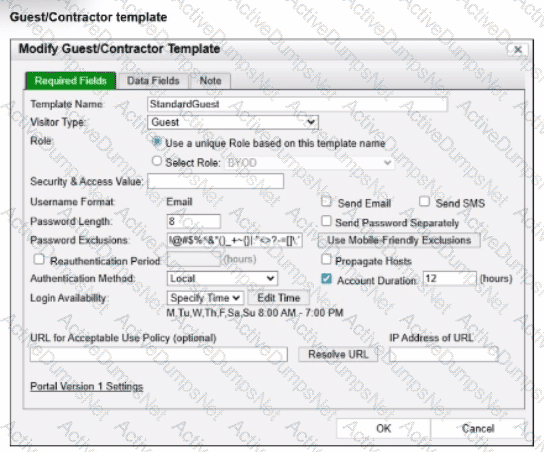
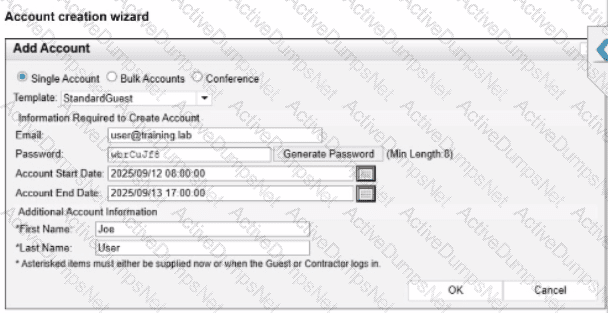
Based on the given configurations and settings, on which date and time would a guest account created at 8:00 AM on 2025/09/12 expire?
Options:
2025/09/12 at 8:00 PM
2025/09/12 at 7:00 PM
2025/09/12 at 17:00:00
2025/09/13 at 17:00:00
Answer:
DExplanation:
Questions no:22
Verified Answer: D
Comprehensive and Detailed 250 to 300 words each Explanation with Exact Matched Extract from FortiNAC-F Administrator library and documentation for current versions (including F 7.2, 7.4, and 7.6) documents:
In FortiNAC-F, the expiration of a guest or contractor account is determined by the configuration settings within theAccount Creation Wizardand the associatedGuest/Contractor Template. While a template can define a default "Account Duration" (as seen in the 12-hour setting in the second exhibit), theAccount Creation Wizardallows an administrator to manually specify or override the start and end parameters for a specific user session.
According to theFortiNAC-F Administration Guideregarding guest management, theAccount End Datefield in the creation wizard is the definitive timestamp for when the account object will be disabled or deleted from the system. In the provided exhibit (Account Creation Wizard), the administrator has explicitly set theAccount Start Dateto2025/09/12 08:00:00and theAccount End Dateto2025/09/13 17:00:00.
Even though the template indicates an "Account Duration" of 12 hours, this value typically serves as a pre-populated default. When a manual date and time are entered into the wizard, those specific values take precedence for that individual account. The account will remain active and valid until5:00 PM (17:00:00)on the following day,2025/09/13. It is also important to note the "Login Availability" from the template (8:00 AM - 7:00 PM); while the accountexistsuntil the 13th at 17:00:00, the user would only be able to authenticate during the active hours defined by the login schedule on both days.
"When creating an account, the administrator can select a template to provide default settings. However, specific values such as theAccount End Datecan be modified within theAccount Creation Wizard. The date and time specified in the 'Account End Date' field determines the absolute expiration of the account. Once this time is reached, the account is moved to an expired state and the user's network access is revoked." —FortiNAC-F Administration Guide: Guest and Contractor Account Management.
Which two requirements must be met to set up an N+1 HA cluster? (Choose two.)
Options:
A FortiNAC-F manager
A FortiNAC-F device designated as a secondary
A dedicated VLAN for primary and secondary synchronization
At least two FortiNAC-F devices designated as primary
Answer:
A, BExplanation:
TheN+1 High Availability (HA)architecture was introduced in FortiNAC-F version 7.6 to provide a more scalable and flexible redundancy model compared to the traditional 1+1 active/passive setup. In an N+1 configuration, a single secondary (standby) appliance can provide coverage for multiple primary (active) Control and Application (CA) appliances.
To set up an N+1 HA cluster, there are two fundamental structural requirements:
A FortiNAC-F Manager (FortiNAC-M):Unlike standard 1+1 HA, which can be configured directly between two CAs, N+1 management is centralized. The FortiNAC-M acts as the orchestrator that manages the failover groups, monitors the health of the primaries, and coordinates the promotion of the secondary server if a primary fails.
A FortiNAC-F device designated as a Secondary:The cluster must have one appliance explicitly configured with theSecondary failover role. This device remains in a standby state, receiving database replications from all N primaries in its group until it is called upon to take over the functions of a failed unit.
While a cluster can support multiple primaries (D), it does not strictly require "at least two" to function as an N+1 group; it simply requires N primaries (where N ≥ 1). Additionally, N+1 is typically a Layer 3 managed solution via the Manager, meaning it does not mandate a "dedicated VLAN" for synchronization like some Layer 2 HA deployments.
"In FortiNAC-F 7.6,FortiNAC-Mfunctions as a manager to manage the N+1 Failover Groups... enabling N+M high availability for CAs. To create an N+1 Failover group, you should add thesecondary CAto the FortiNAC-M first, then add the primary CAs. The secondary CA is designed to take over the functionality of any single failed primary component." —FortiNAC-F 7.6.0 N+1 Failover Reference Manual.
An administrator wants FortiNAC-F to return a group of user-defined RADIUS attributes in RADIUS responses.
Which condition must be true to achieve this?
Options:
The requesting device must support RFC 5176.
Inbound RADIUS requests must contain the Calling-Station-ID attribute.
The device models in the inventory view must be configured for proxy-based authentication.
RADIUS accounting must be enabled on the FortiNAC-F RADIUS server configuration.
Answer:
BExplanation:
In FortiNAC-F, theRADIUS Attribute Groupsfeature allows administrators to return customized RADIUS attributes (such as specific VLAN IDs, filter IDs, or vendor-specific attributes) in anAccess-Acceptpacket sent back to a network device. This is particularly useful for supporting "Generic RADIUS" devices that are not natively supported but can be managed using standard AVPairs.
According to theFortiNAC-F Generic RADIUS Wired Cookbookand theRADIUS Attribute Groups sectionof the Administration Guide, there is one critical prerequisite for this feature to function: theinbound RADIUS request must contain the Calling-Station-ID attribute. The Calling-Station-ID typically contains theMAC addressof the connecting endpoint. Because FortiNAC-F is a host-centric system, it uses the MAC address as the unique identifier to look up the host record, evaluate the associated Network Access Policy, and determine which Logical Network (and thus which Attribute Group) should be applied. If the incoming request lacks this attribute, FortiNAC-F cannot reliably identify the host and, as a safety mechanism, willnot include any user-defined RADIUS attributesin the response. This ensures that unauthorized or unidentifiable devices do not receive privileged access through misapplied attributes.
"Configure a set of attributes that must be included in the RADIUS Access-Accept packet returned by FortiNAC...Requirement: Inbound RADIUS request must contain Calling-Station-Id. Otherwise, FortiNAC will not include the RADIUS attributes.This attribute is used to identify the host and its current state within the FortiNAC database." —FortiNAC-F 7.6.0 Generic RADIUS Wired Cookbook: Configure RADIUS Attribute Groups.
An administrator wants to build device profiling rules based on network traffic, but the network session view is not populated with any records.
Which two settings can be enabled to gather network session information? (Choose two.)
Options:
Network traffic polling on any modeled infrastructure device
Firewall session polling on modeled FortiGate devices
Netflow setting on the FortiNAC-F interfaces
Layer 3 polling on the infrastructure devices
Answer:
B, CExplanation:
In FortiNAC-F, theNetwork Sessionsview provides a real-time and historical log of traffic flows, including source/destination IP addresses, ports, and protocols. This data is essential for buildingDevice Profiling Rulesthat rely on "Traffic Patterns" or "Network Footprints" to identify devices (e.g., an IP camera communicating with its specific NVR). If the network session view is empty, the system is not receiving the necessary flow or session data from the network infrastructure.
According to theFortiNAC-F Administration Guide, there are two primary methods to populate this view:
NetFlow/sFlow/IPFIX (C):FortiNAC-F can act as a flow collector. By enablingNetFlowsettings on the FortiNAC-F service interface (port2/eth1) and configuring your switches or routers to export flow data to the FortiNAC IP, the system can parse these packets and record sessions.
Firewall Session Polling (B):For environments with FortiGate firewalls, FortiNAC-F can proactively poll the FortiGate via theREST APIto retrieve its current session table. This is particularly useful as it provides session visibility without requiring the overhead of configuring NetFlow on every access layer switch.
Settings likeLayer 3 Polling(D) only provide ARP table mappings (IP to MAC correlation) and do not provide the detailed flow information required for the session view.
"TheNetwork Sessionsview displays information regarding active and inactive network traffic sessions... To populate this view, FortiNAC must receive data through one of the following methods: •NetFlow/sFlow Support: Configure network devices to send flow data to the FortiNAC service interface. •Firewall Session Polling: Enable session polling on modeled FortiGate devices to retrieve session information via API. These records are then used by the Device Profiler to match rules based on traffic patterns." —FortiNAC-F Administration Guide: Network Sessions and Flow Data Collection.
Refer to the exhibit.
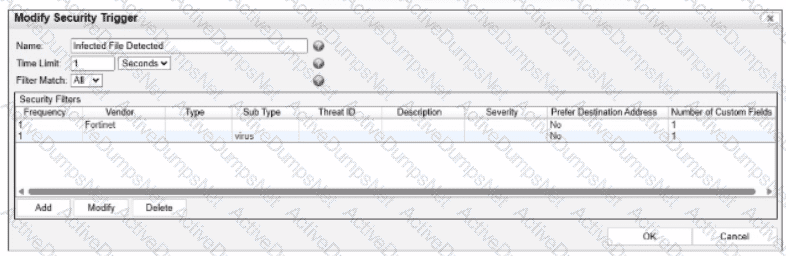
What would FortiNAC-F generate if only one of the security fitters is satisfied?
Options:
A normal alarm
A security event
A security alarm
A normal event
Answer:
DExplanation:
In FortiNAC-F,Security Triggersare used to identify specific security-related activities based on incoming data such as Syslog messages or SNMP traps from external security devices (like a FortiGate or an IDS). These triggers act as a filtering mechanism to determine if an incoming notification should be escalated from a standard system event to aSecurity Event.
According to theFortiNAC-F Administrator Guideand relevant training materials for versions 7.2 and 7.4, theFilter Matchsetting is the critical logic gate for this process. As seen in the exhibit, the "Filter Match" configuration is set to"All". This means that for the Security Trigger named "Infected File Detected" to "fire" and generate a Security Event or a subsequent Security Alarm,every single filterlisted in the Security Filters table must be satisfied simultaneously by the incoming data.
In the provided exhibit, there are two filters: one looking for the Vendor"Fortinet"and another looking for the Sub Type"virus". If only one of these filters is satisfied (for example, a message from Fortinet that does not contain the "virus" subtype), the logic for the Security Trigger is not met. Consequently, FortiNAC-F does not escalate the notification. Instead, it processes theincoming data as aNormal Event, which is recorded in the Event Log but does not trigger the automated security response workflows associated with security alarms.
"The Filter Match option defines the logic used when multiple filters are defined. If'All'is selected, then all filter criteria must be met in order for the trigger to fire and aSecurity Eventto be generated. If the criteria are not met, the incoming data is processed as anormal event. If'Any'is selected, the trigger fires if at least one of the filters matches." —FortiNAC-F Administration Guide: Security Triggers Section.
When creating a device profiling rule, what are two advantages of registering the device in the host view? (Choose two.)
Options:
The devices can be managed as a generic SNMP device.
The devices will have connection logs.
The devices can be associated with a user.
The devices can be polled for connection status.
Answer:
B, CExplanation:
In FortiNAC-F, theDevice Profileris a rule-based engine that evaluates unknown "rogue" devices and classifies them based on fingerprints and behavior. When a profiling rule matches a device, the administrator can configure the rule to automatically register that device. The registration process can place the device record in two primary locations: theTopology View(as a device) or theHost View(as a registered host).
According to theFortiNAC-F Administration Guide, registering a device in theHost Viewprovides significant advantages for identity management and historical tracking. First, the devices can beassociated with a user (C). In the FortiNAC database architecture, the Host View is the primary repository for endpoint identity; placing a profiled device here allows the system to link that hardware (MAC address) to a specific user account, whether that user is an employee, guest, or a system-level "owner". This association is essential for Role-Based Access Control (RBAC) and for tracking accountability across the network fabric.
Second, devices registered in the Host View will haveconnection logs (B). FortiNAC-F maintains a detailed operational history for all host records, including every instance of the device connecting to or disconnecting from a port, its IP address assignments, and the specific policies applied during each session. These logs are invaluable for troubleshooting connectivity issues and for security forensic audits, as they provide a clear timeline of the device's lifecycle on the network. In contrast, devices managed only in the Topology View are typically treated as infrastructure components where the focus is on device availability rather than individual session history.
"Devices that are registered and associated with a user are placed in theHost Viewand removed from the Profiled Devices window... Placing a device in the Host View allows for the tracking ofconnection historyand the association of the device with a specificidentity or user recordwithin the FortiNAC database." —FortiNAC-F Administration Guide: Device Profiler How it Works.
A healthcare organization is integrating FortiNAC-F with its existing MDM. Communication is failing between the systems.
What could be a probable cause?
Options:
Security Fabric traffic is failing
SSH communication is failing
REST API communication is failing
SOAP API communication is failing
Answer:
CExplanation:
The integration between FortiNAC-F and Mobile Device Management (MDM) platforms (such as Microsoft Intune, VMware Workspace ONE, or Jamf) is a critical component for providing visibility into mobile assets that do not connect directly to the managed infrastructure via standard wired or wireless protocols.
According to theFortiNAC-F MDM Integration Guide, the communication between the FortiNAC-F appliance and the MDM server is handled throughREST APIcalls. FortiNAC-F acts as an API client, periodically polling the MDM server to retrieve device metadata, compliance status, and ownership information. If communication is failing, it is most likely because the API credentials (Client ID/Secret) are incorrect, the MDM's API endpoint is unreachable from the FortiNAC-F service port, or the SSL certificate presented by the MDM is not trusted by the FortiNAC-F root store.
While SSH (B) is used for switch CLI management and the Security Fabric (A) uses proprietary protocols for FortiGate synchronization, neither is the primary vehicle for MDM data exchange. SOAP API (D) is an older protocol that has been largely replaced by REST in modern FortiNAC integrations.
"FortiNAC integrates with MDM systems by utilizingREST APIcommunication to query the MDM database for device information. To establish this link, administrators must configure the MDM Service Connector with the appropriateAPI URLand authentication credentials. If the 'Test Connection' fails, verify that the FortiNAC can reach the MDM provider via theREST APIport (usually HTTPS 443)." —FortiNAC-F Administration Guide: MDM Integration and Troubleshooting.
An administrator wants to create a conference manager administrator account but would like to limit the number of conference accounts that can be generated to 30.
Which statement about conference accounts is true?
Options:
In FortiNAC-F, conference accounts can be limited by multiples of 25, so the conference administrator could create 50 accounts.
The administrator can set a maximum of 30 conference accounts in the administrative profile for the conference manager.
The conference account limit is defined in the onboarding conference portal.
Conference account limits are defined in the conference guest and contractor template.
Answer:
BExplanation:
In FortiNAC-F, theConference Manageris a specialized administrative role designed for delegated administration, often used by receptionists or event organizers to create temporary guest accounts. To maintain security and prevent the over-provisioning of credentials, FortiNAC-F allows for granular restrictions on these accounts.
According to theFortiNAC-F Administration GuideregardingAdministrative Profiles, when an administrator creates a profile for a Conference Manager, they can define specific "Account Limits." Under the profile settings (located inSystem > Settings > Admin Profiles), there is a field specifically for"Max Accounts."By entering "30" into this field, the administrator ensures that any user assigned to this profile cannot exceed 30 active conference accounts at any given time.
This setting is distinct from the Portal configuration or the Guest templates. While templates define thetypeof account (e.g., duration and access level), theAdministrative Profiledefines thecapabilities and limitationsof the person creating those accounts. This ensures that even if a guest template allows for unlimited registrations, the specific administrator is physically restricted by the system from generating more than the allotted 30.
"Administrative Profiles define what an administrator can see and do within the system. For delegated administration roles like the Conference Manager, the'Max Accounts'field in the Administrative Profile is used to specify the maximum number of accounts the user is permitted to create. Once this limit is reached, the user will be unable to generate additional accounts until existing ones expire or are deleted." —FortiNAC-F Administration Guide: Administrative Profiles and Delegated Administration.
During an evaluation of state-based enforcement, an administrator discovers that ports that should not be under enforcement have been added to enforcement groups.
In which view would the administrator be able to identify who added the ports to the groups?
(Selected)
Options:
The Admin Auditing view
The Event Management view
The Port Changes view
The Security Events view
Answer:
AExplanation:
In FortiNAC-F, accountability and forensic tracking of configuration changes are managed through theAdmin Auditingfunctionality. When an administrator performs an action that modifies the system state—such as creating a policy, changing a device's status, or adding a switch port to anEnforcement Group—the system generates an audit record. This record is essential for troubleshooting scenarios where unauthorized or accidental configuration changes have occurred, leading to unintended network behavior.
TheAdmin Auditingview (found underLogs > Admin Auditing) provides a comprehensive log of the "Who, What, and When" for every administrative session. Each entry includes the username of the administrator, the source IP address from which they accessed the FortiNAC-F console, a precise timestamp, and a detailed description of the modification. In the scenario described, where ports have been incorrectly added to enforcement groups, the Admin Auditing view allows a supervisor to filter by the specific "Port" or "Group" object to identify exactly which administrator executed the command.
In contrast, theEvent Managementview (B) is designed to monitor system and network events, such as RADIUS authentications, host connections, and SNMP trap arrivals. While it tracks system activity, it does not typically log the manual configuration changes performed by admins. ThePort Changesview (C) tracks the operational history of a port (such as VLAN assignment changes and host movements) but does not attribute the administrative assignment of the port to a group. Finally, theSecurity Eventsview (D) is dedicated to alerts triggered by security rules and external threat feeds.
"Admin Auditing displays a record of all modifications made to the FortiNAC-F system by an administrator. This view includes the administrator's name, the date and time of the change, and a description of the action taken. It is the primary resource for determining which administrative user performed a specific configuration change, such as modifying port group memberships or altering policy settings." —FortiNAC-F Administration Guide: Logging and Auditing Section.
Unlock NSE5_FNC_AD_7.6 Features
- NSE5_FNC_AD_7.6 All Real Exam Questions
- NSE5_FNC_AD_7.6 Exam easy to use and print PDF format
- Download Free NSE5_FNC_AD_7.6 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
Questions & Answers PDF Demo
- NSE5_FNC_AD_7.6 All Real Exam Questions
- NSE5_FNC_AD_7.6 Exam easy to use and print PDF format
- Download Free NSE5_FNC_AD_7.6 Demo (Try before Buy)
- Free Frequent Updates
- 100% Passing Guarantee by Activedumpsnet
