Fortinet FCSS_EFW_AD-7.6 Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator Exam Practice Test
Fortinet NSE 7 - Enterprise Firewall 7.6 Administrator Questions and Answers
A company's users on an IPsec VPN between FortiGate A and B have experienced intermittent issues since implementing VXLAN. The administrator suspects that packets exceeding the 1500-byte default MTU are causing the problems.
In which situation would adjusting the interface’s maximum MTU value help resolve issues caused by protocols that add extra headers to IP packets?
Which two statements about IKEv2 are true if an administrator decides to implement IKEv2 in the VPN topology? (Choose two.)
Refer to the exhibit, which shows the VDOM section of a FortiGate device.
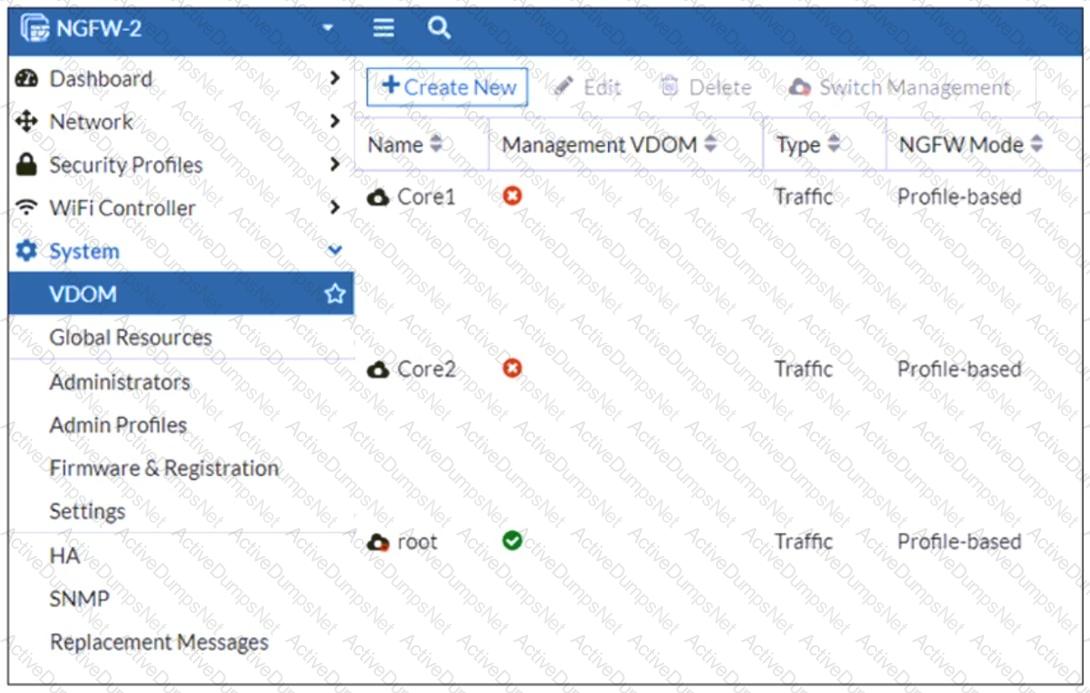
An administrator discovers that webfilter stopped working in Core1 and Core2 after a maintenance window.
Which two reasons could explain why webfilter stopped working? (Choose two.)
A company that acquired multiple branches across different countries needs to install new FortiGate devices on each of those branches. However, the IT staff lacks sufficient knowledge to implement the initial configuration on the FortiGate devices.
Which three approaches can the company take to successfully deploy advanced initial configurations on remote branches? (Choose three.)
Refer to the exhibit.
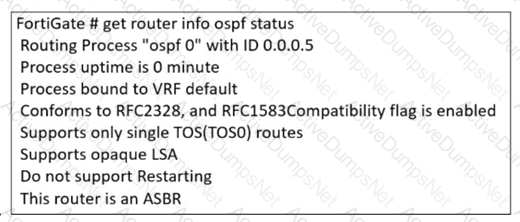
The partial output of an OSPF command is shown. You are checking the OSPF status of a FortiGate device when you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
Refer to the exhibit.
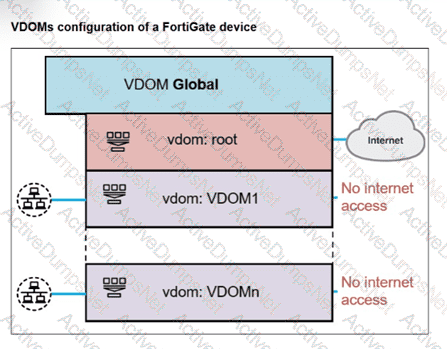
A FortiGate segmented into VDOMs is shown. You must ensure effective and accelerated internet access for all of the VDOMs in this enterprise network. How can you achieve this? (Choose one answer)
Refer to the exhibit, which shows a physical topology and a traffic log.
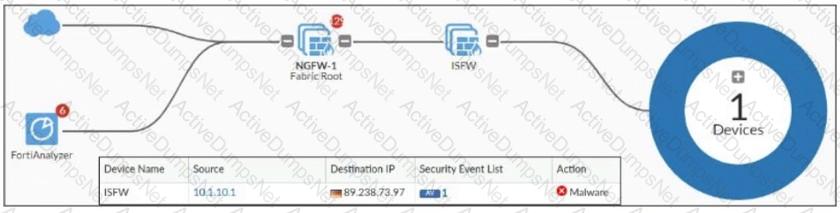
The administrator is checking on FortiAnalyzer traffic from the device with IP address 10.1.10.1, located behind the FortiGate ISFW device.
The firewall policy in on the ISFW device does not have UTM enabled and the administrator is surprised to see a log with the action Malware, as shown in the exhibit.
What are the two reasons FortiAnalyzer would display this log? (Choose two.)
A FortiGate device with UTM profiles is reaching the resource limits, and the administrator expects the traffic in the enterprise network to increase.
The administrator has received an additional FortiGate of the same model.
Which two protocols should the administrator use to integrate the additional FortiGate device into this enterprise network? (Choose two.)
Refer to the exhibit, which shows an OSPF network.
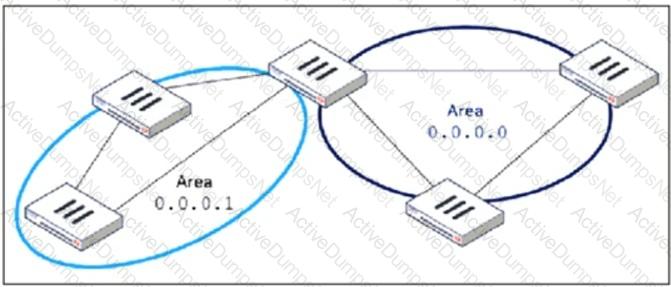
Which configuration must the administrator apply to optimize the OSPF database?
Refer to the exhibits.
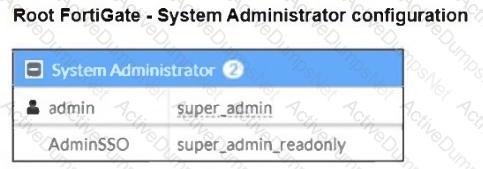
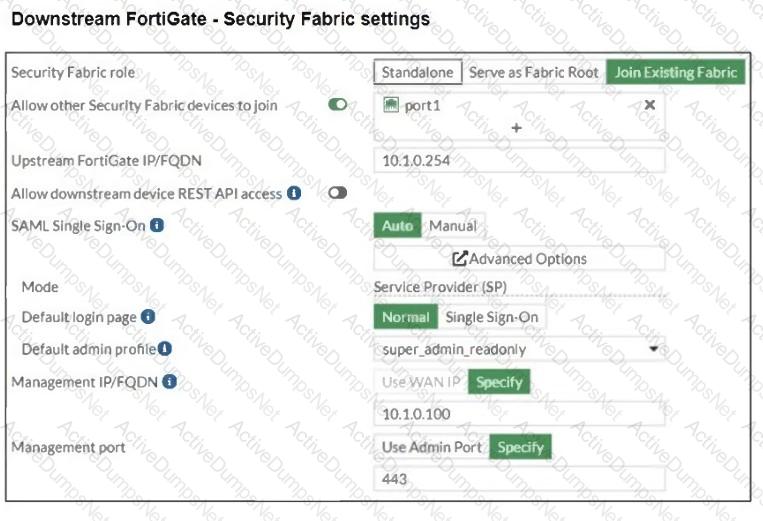
The Administrators section of a root FortiGate device and the Security Fabric Settings section of a downstream FortiGate device are shown.
When prompted to sign in with Security Fabric in the downstream FortiGate device, a user enters the AdminSSO credentials.
What is the next status for the user?
Refer to the exhibit, which shows a revision history window in the FortiManager device layer.
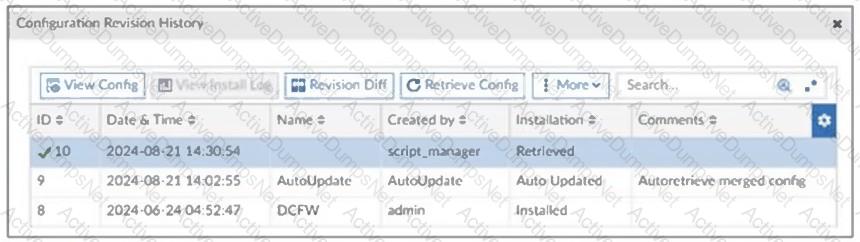
The IT team is trying to identify the administrator responsible for the most recent update in the FortiGate device database.
Which conclusion can you draw about this scenario?
An administrator must minimize CPU and RAM use on a FortiGate firewall while also enabling essential security features, such as web filtering and application control for HTTPS traffic.
Which SSL inspection setting helps reduce system load while also enabling security features, such as web filtering and application control for encrypted HTTPS traffic?
Why does the ISDB block layers 3 and 4 of the OSI model when applying content filtering? (Choose two.)
An administrator is extensively using VXLAN on FortiGate.
Which specialized acceleration hardware does FortiGate need to improve its performance?
The IT department discovered during the last network migration that all zero phase selectors in phase 2 IPsec configurations impacted network operations.
What are two valid approaches to prevent this during future migrations? (Choose two.)
An administrator must standardize the deployment of FortiGate devices across branches with consistent interface roles and policy packages using FortiManager.
What is the recommended best practice for interface assignment in this scenario?
Refer to the exhibit.
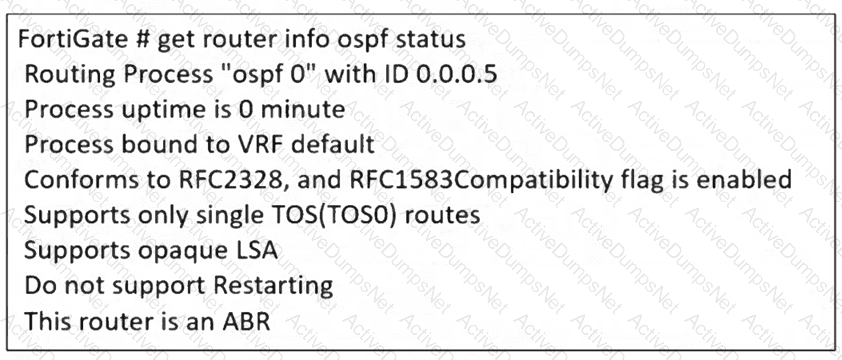
The partial output of an OSPF command is shown. While checking the OSPF status of FortiGate, you receive the output shown in the exhibit. Based on the output, which two statements about FortiGate are correct? (Choose two answers)
Refer to the exhibit.
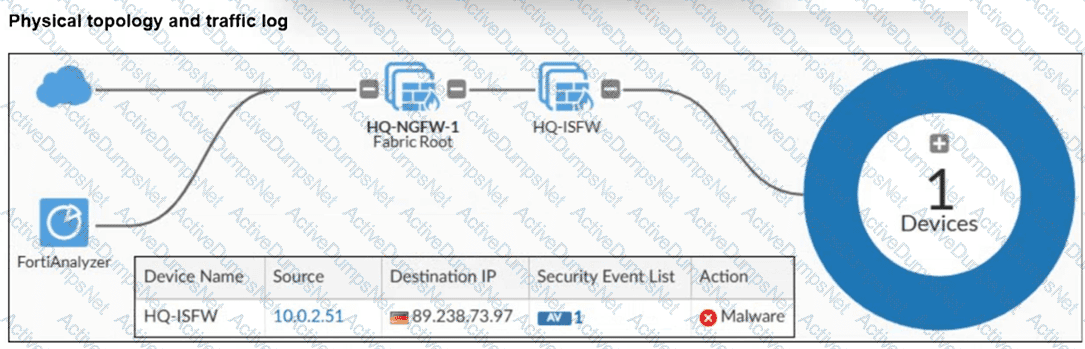
A physical topology along with a traffic log is shown. You are using FortiAnalyzer to monitor traffic from the device with IP address 10.0.2.51, which is located behind the FortiGate internal segmentation firewall (ISFW) device. Unified threat management (UTM) is not enabled in the firewall policy on the HQ-ISFW device, and you are surprised to see a log with the action Malware, as shown in the exhibit. What are two reasons why FortiAnalyzer would display this log? (Choose two answers)
Refer to the exhibit, which shows a command output.

FortiGate_A and FortiGate_B are members of an FGSP cluster in an enterprise network.
While testing the cluster using the ping command, the administrator monitors packet loss and found that the session output on FortiGate_B is as shown in the exhibit.
What could be the cause of this output on FortiGate_B?

 FGSP allows session-aware load balancing between multiple FortiGate units without requiring them to be in an HA (High Availability) cluster.
FGSP allows session-aware load balancing between multiple FortiGate units without requiring them to be in an HA (High Availability) cluster. With external load balancers, incoming traffic is evenly distributed across multiple FortiGate devices.
With external load balancers, incoming traffic is evenly distributed across multiple FortiGate devices. This approach is useful for scaling out traffic handling capacity while ensuring that sessions remain synchronized between firewalls.
This approach is useful for scaling out traffic handling capacity while ensuring that sessions remain synchronized between firewalls. FGSP is effective when stateful failover is required but without the constraints of traditional HA.
FGSP is effective when stateful failover is required but without the constraints of traditional HA. FGCP active-active mode enables multiple FortiGate devices to share traffic loads, increasing throughput and efficiency.
FGCP active-active mode enables multiple FortiGate devices to share traffic loads, increasing throughput and efficiency. Active-active mode is suitable for balancing UTM processing across multiple FortiGates, making it ideal when resource limits are a concern.
Active-active mode is suitable for balancing UTM processing across multiple FortiGates, making it ideal when resource limits are a concern. Using switches ensures redundancy and avoids single points of failure in the network.
Using switches ensures redundancy and avoids single points of failure in the network. This mode is commonly used in enterprise networks where both scalability and redundancy are required.
This mode is commonly used in enterprise networks where both scalability and redundancy are required.