Fortinet FCP_FML_AD-7.4 FCP - FortiMail 7.4 Administrator Exam Practice Test
FCP - FortiMail 7.4 Administrator Questions and Answers
A mail user wants the ability to subscribe or publish to and from their FortiMail calendar using Thunderbird as their mail user agent (MUA). What information does this mail user need from their webmail User Preferences section?
Refer to the exhibit, which displays a history log entry.
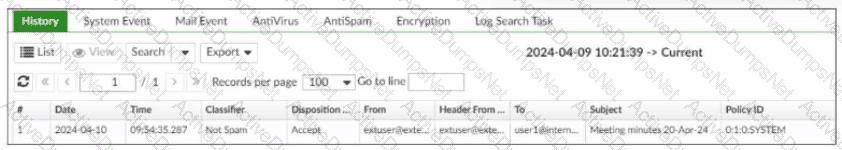
In the Policy ID column, why isthe last policy ID value SYSTEM?
While testing outbound MTA functionality, an administrator discovers that all outbound email is being processed using policy ID l: 2:0: SYSTEM. What are two possible reasons why the third policy ID value is o? (Choose two.)
Refer to the exhibit which shows a command prompt output of a telnet command.
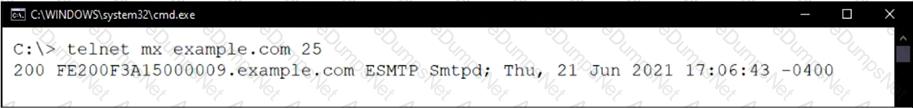
Which configuration change must you make to prevent the banner from displaying the FortiMail serial number?
When configuring a FortiMail HA group consisting of different models, which two statements are true? (Choose two.)
Refer to the exhibit, which shows a partial antispam profile configuration.
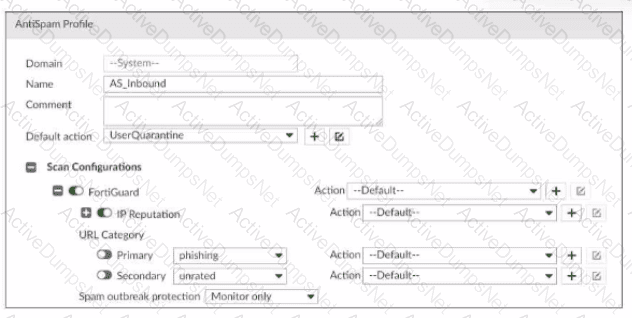
What will happen to an email that triggers Spam outbreak protection?
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs werenotgenerated because of any outbound email sent from their organization.
Which FortiMail antispam technique can the administrator use to prevent this scenario?
Refer to the exhibit which shows a detailed history log view.
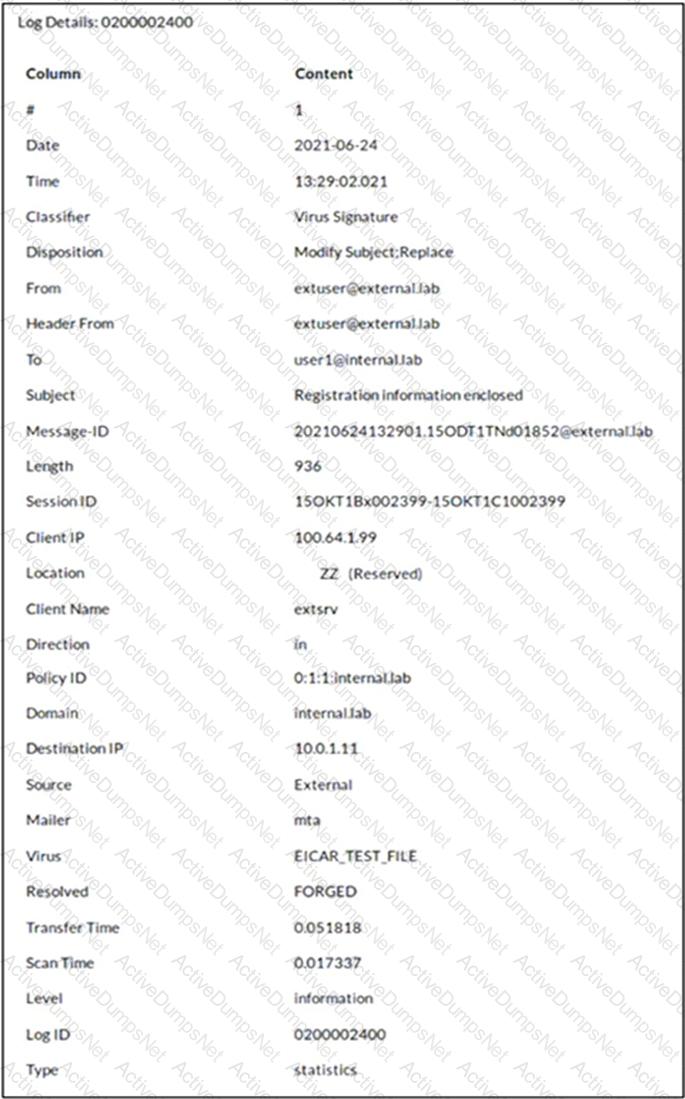
Which two actions did FortiMail take on this email message? (Choose two.)
Refer to the exhibit, which shows a few lines of FortiMail logs.
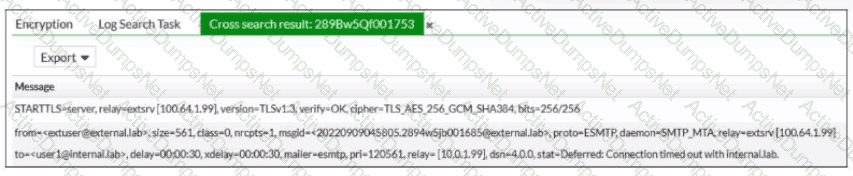
Based on these log entries, which two statements describe the operational status of this FortiMail device? (Choose two.)
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
Refer to the exhibit, which displays an access control rule.
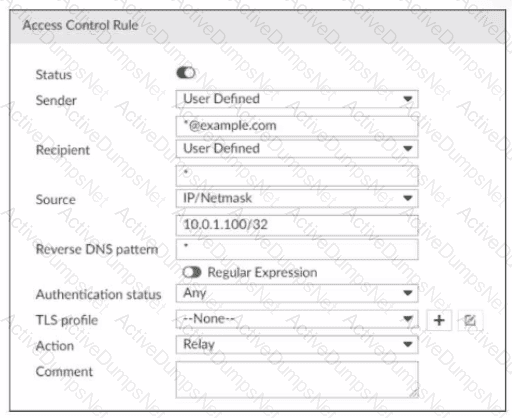
What are two expected behaviors for this access control rule? (Choose two.)
Refer to the exhibits showing SMTP limits (Session Profile — SMTP Limits), and domain settings (Domain Settings, andDomain Settings — Other) of a FortiMail device.
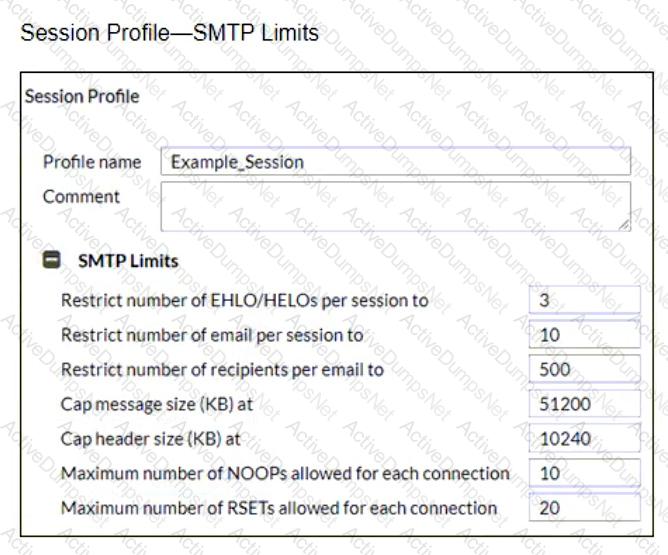
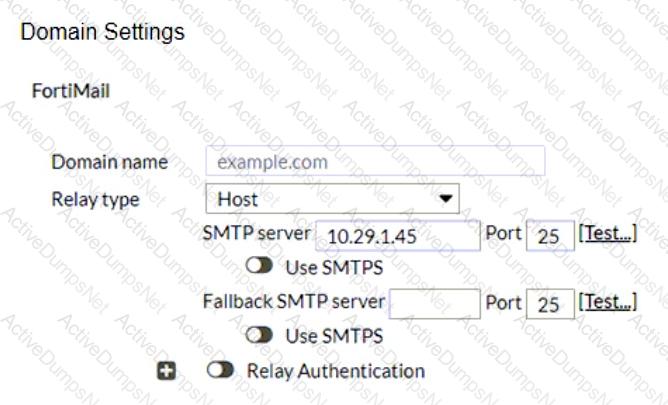
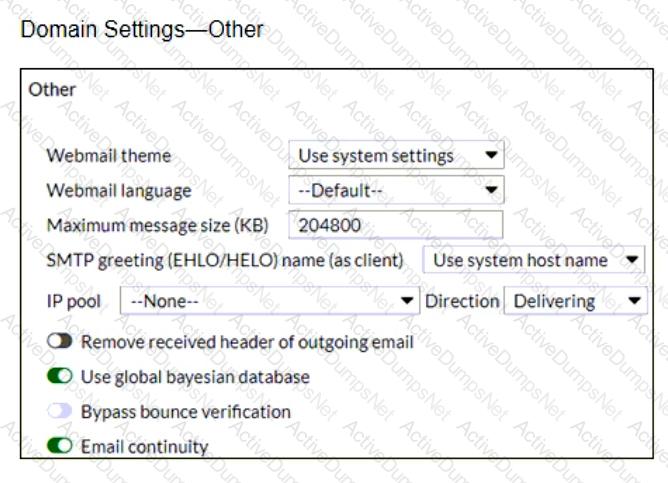
Which message size limit in KB will the FortiMail apply to outbound email?
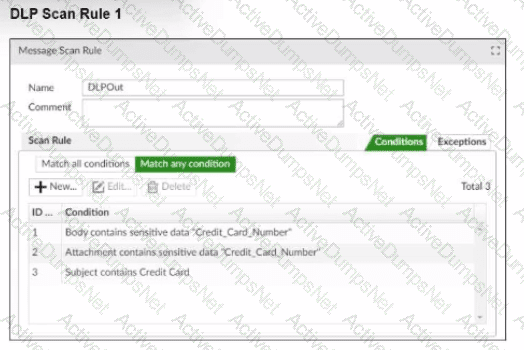

Refer to the exhibits, which shows a DLP scan profile configuration (DLP Scan Rule 1 and DLP Scan Rule 2) from a FortiMail device.
Which two message types will trigger this DLP scan rule? (Choose two.)
Refer to the exhibit, which shows a topology diagram of two separate email domains.
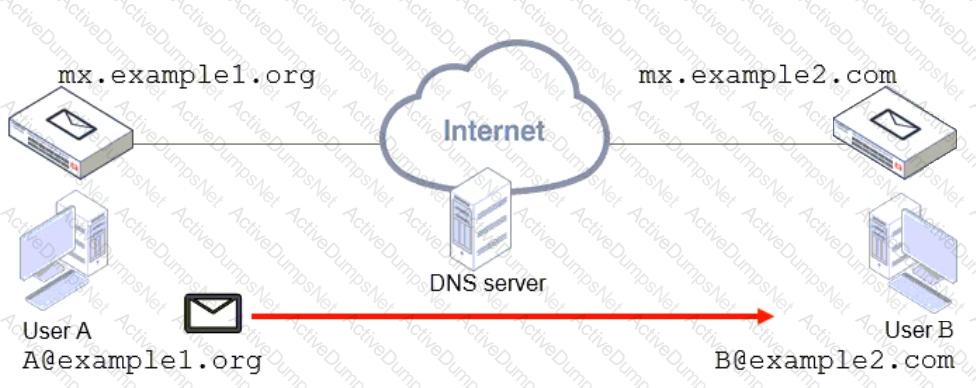
Which two statements correctly describe how an email message is delivered from User A to User B? (Choose two.)
