Fortinet FCP_FGT_AD-7.6 FortiGate 7.6 Administrator FCP_FGT_AD-7.6 Exam Practice Test
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 Questions and Answers
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
You have configured the below commands on a FortiGate.
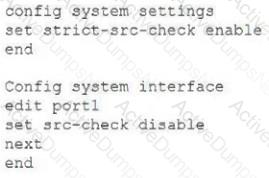
What would be the impact of this configuration on FortiGate?
An administrator wanted to configure an IPS sensor to block traffic that triggers a signature set number of times during a specific time period.
How can the administrator achieve the objective?
Refer to the exhibit.
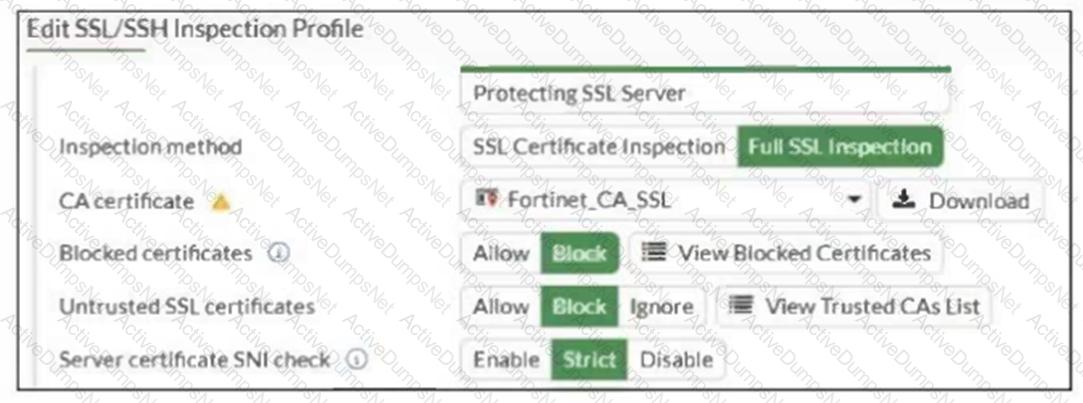
What would be the impact of these settings on the Server certificate SNI check configuration on FortiGate?
Refer to the exhibits.
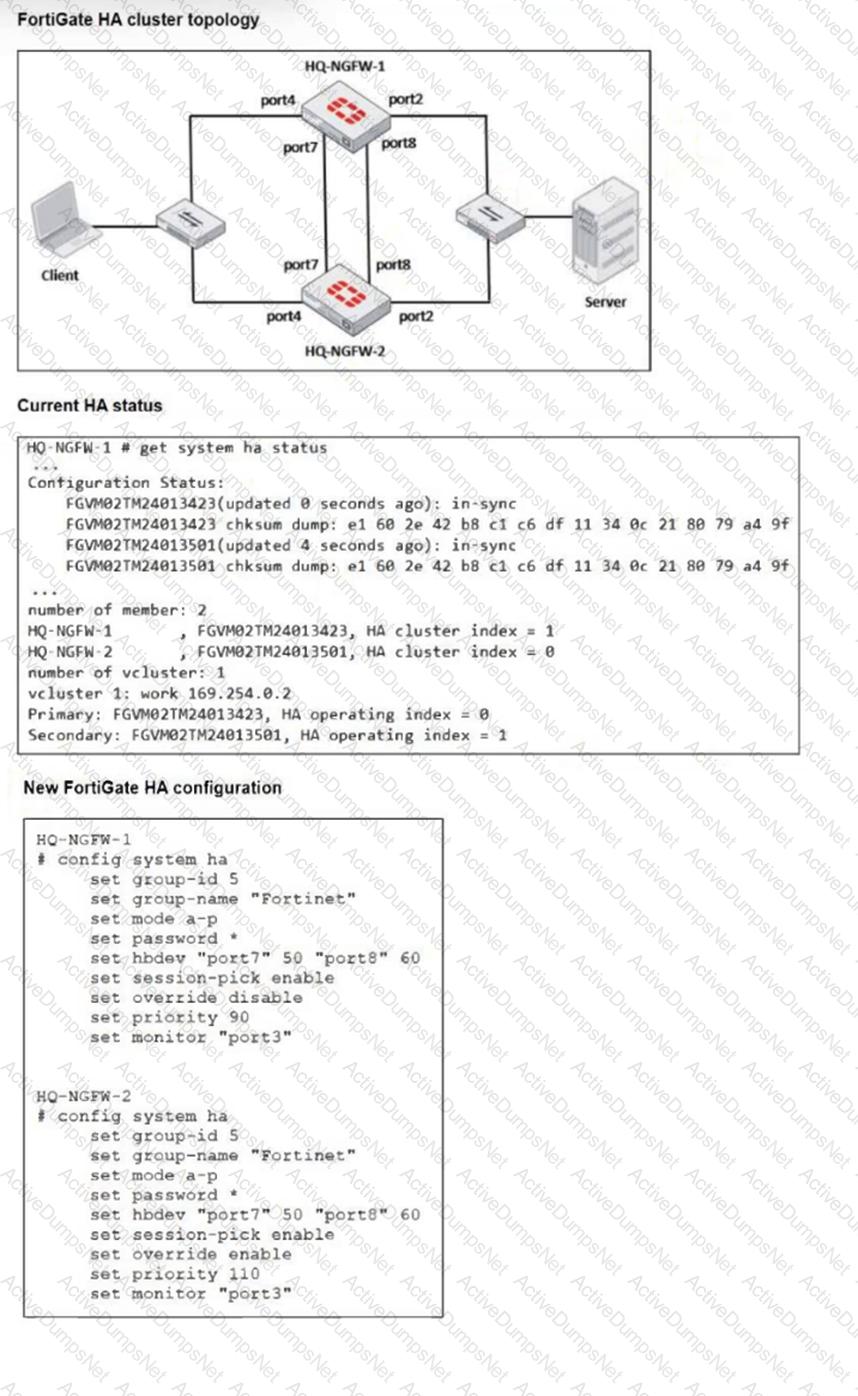
Based on the current HA status, an administrator updates the override and priority parameters on HQ-NGFW-1 and HQ-NGFW-2 as shown in the exhibit.
What would be the expected outcome in the HA cluster?
What is the primary FortiGate election process when the HA override setting is enabled?
Refer to the exhibit, which shows an SD-WAN zone configuration on the FortiGate GUI.
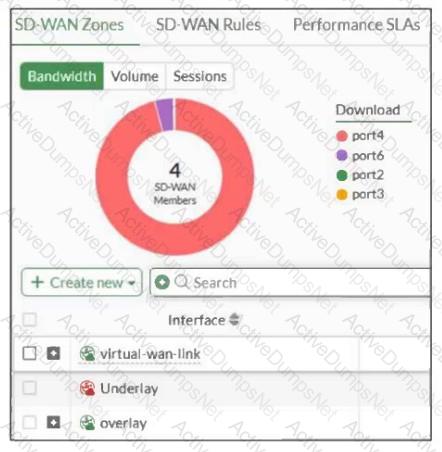
Based on the exhibit, which statement is true?
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when there is no inbound traffic.
Which DPD mode on FortiGate meets this requirement?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements about the requirements of connected physical interfaces on FortiGate are true? (Choose two.)
Which two statements are correct when FortiGate enters conserve mode? (Choose two.)
Which three statements explain a flow-based antivirus profile? (Choose three.)
Which two statements are true about an HA cluster? (Choose two.)
Refer to the exhibit.
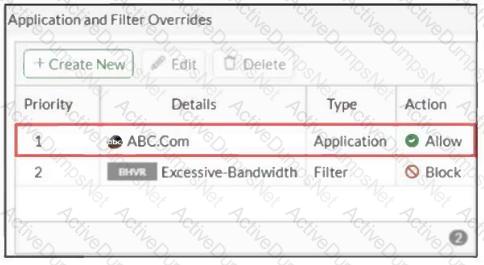
An administrator has configured an Application Overrides for the ABC.Com application signature and set the Action to Allow. This application control profile is then applied to a firewall policy that is scanning all outbound traffic. Logging is enabled in the firewall policy. To test the configuration, the administrator accessed the ABC.Com web site several times.
Why are there no logs generated under security logs for ABC.Com?
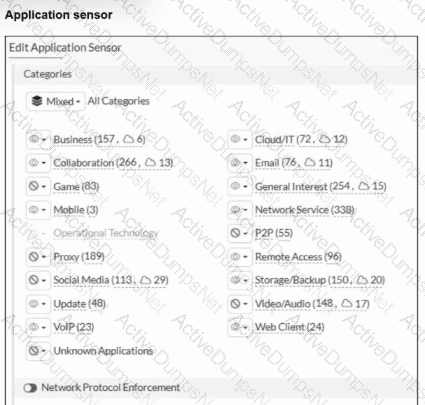
Refer to the exhibits.
You have implemented the application sensor and the corresponding firewall policy as shown in the exhibits.
Which two factors can you observe from these configurations? (Choose two.)
